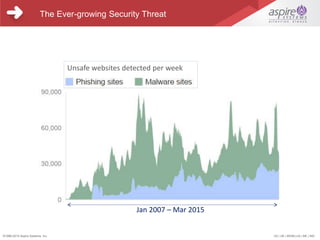
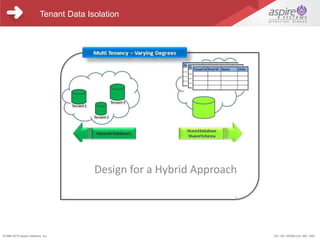
This document provides an overview and agenda for a webinar on security architecture best practices for SaaS applications. The webinar will cover the shared responsibility model for security between SaaS providers and infrastructure providers. It will discuss security considerations at different architecture layers, data isolation risks and mitigation plans, and OWASP top security threats. Speakers from Aspire Systems, a global technology services firm, will provide insights on these topics and take participant questions at the end.