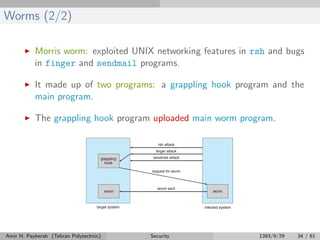
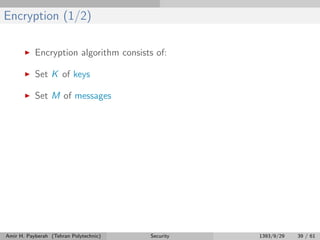
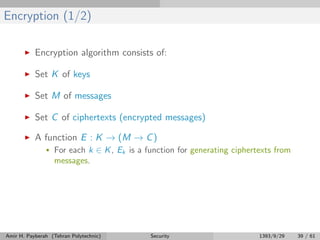
The document discusses various security threats to computer systems, including breaches of confidentiality, integrity, availability, and denial of service. It describes common attack methods like masquerading, replay attacks, and man-in-the-middle attacks. Specific threats discussed in more detail include Trojan horses, trap doors, logic bombs, stack and buffer overflows, and viruses. Security needs to be implemented at the physical, human, operating system, and network levels to be effective.