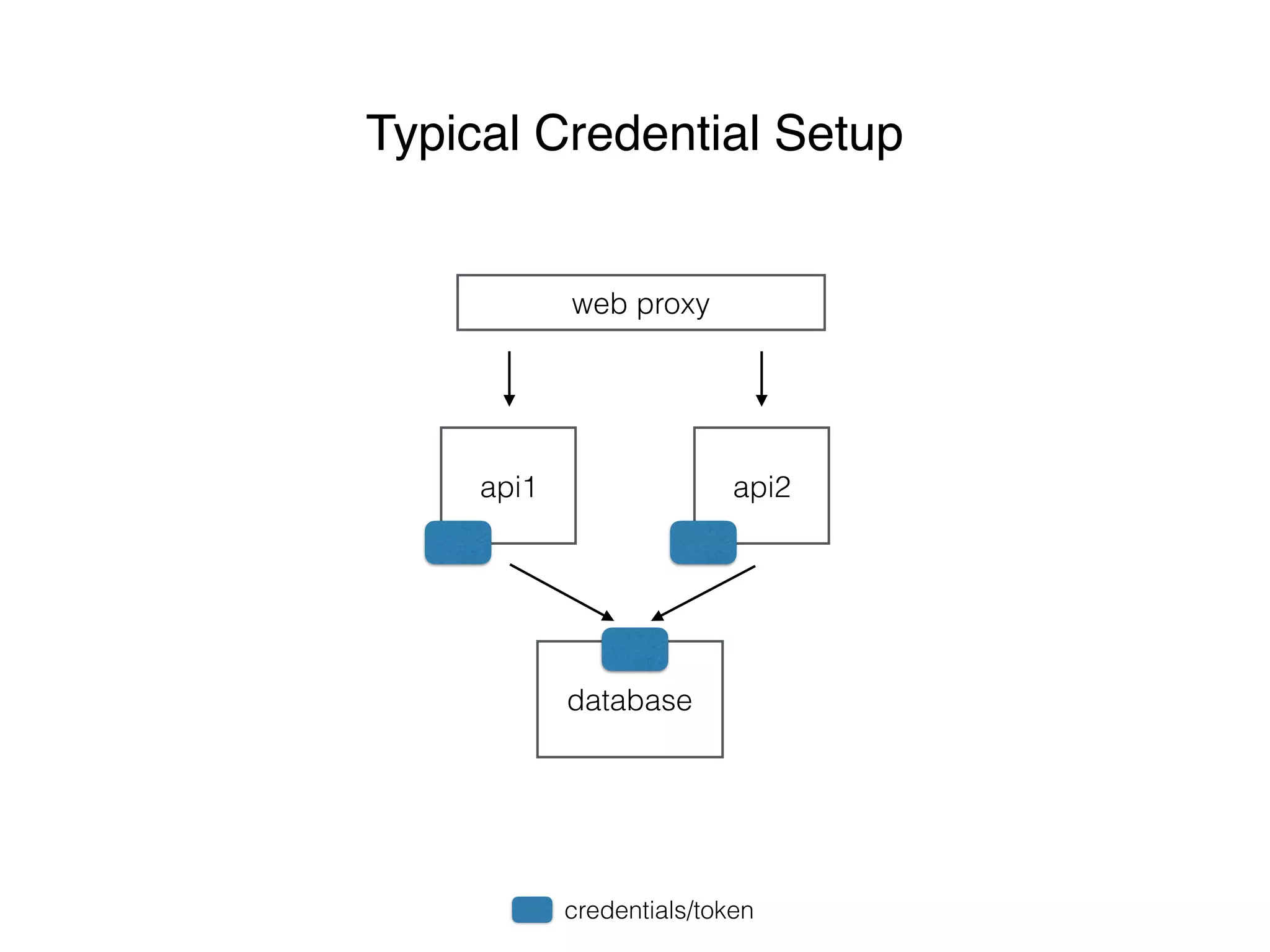
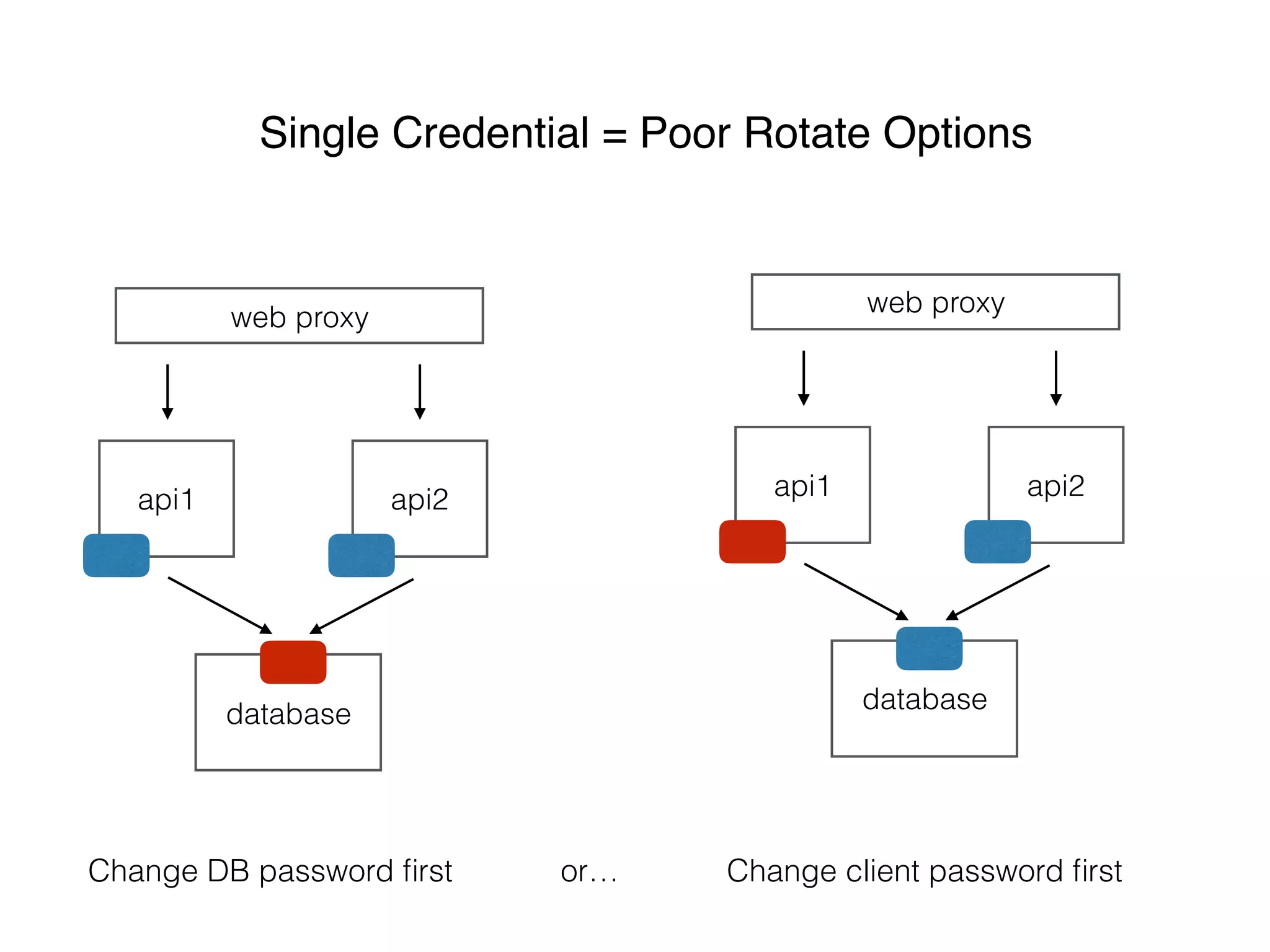
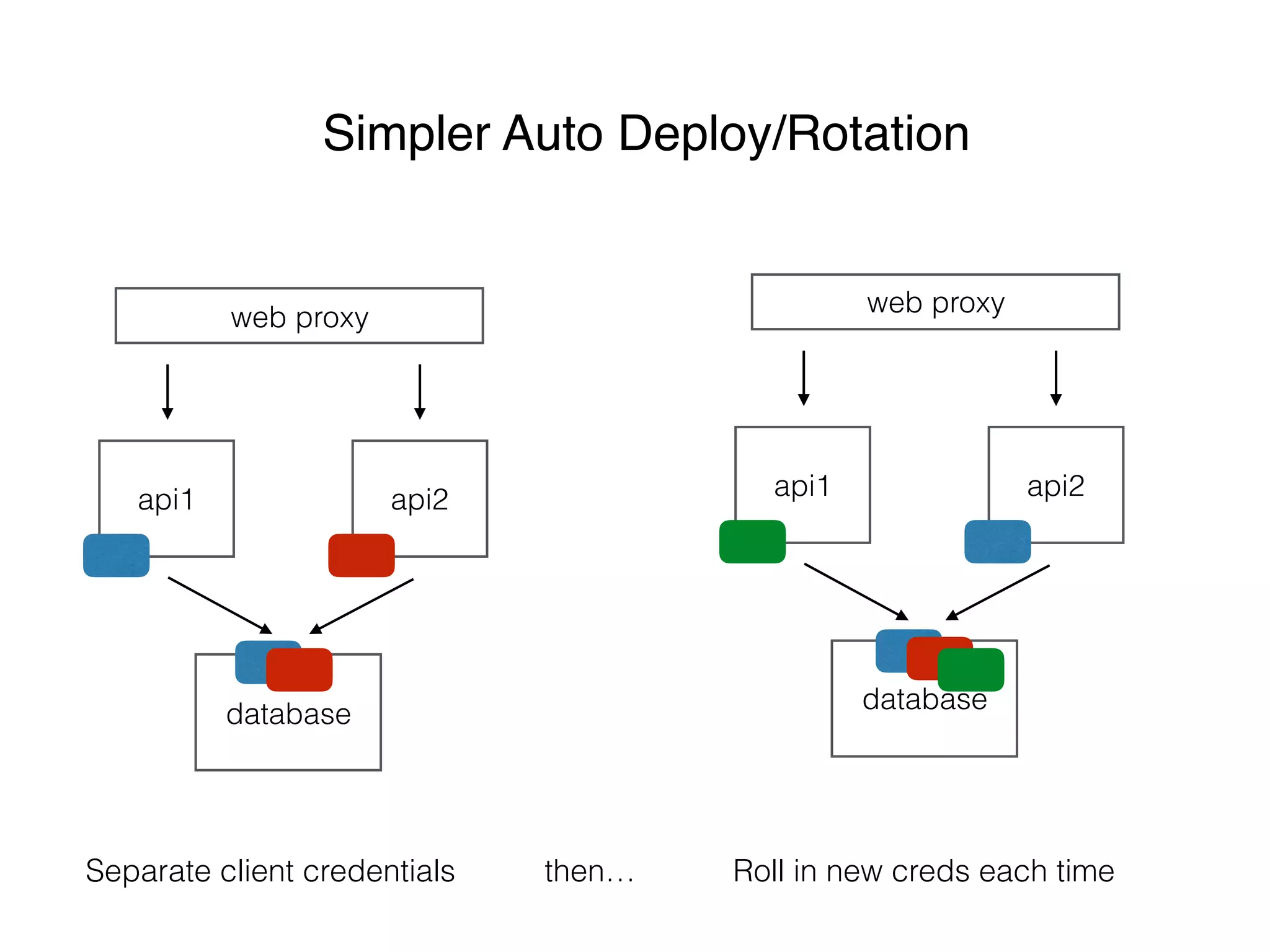
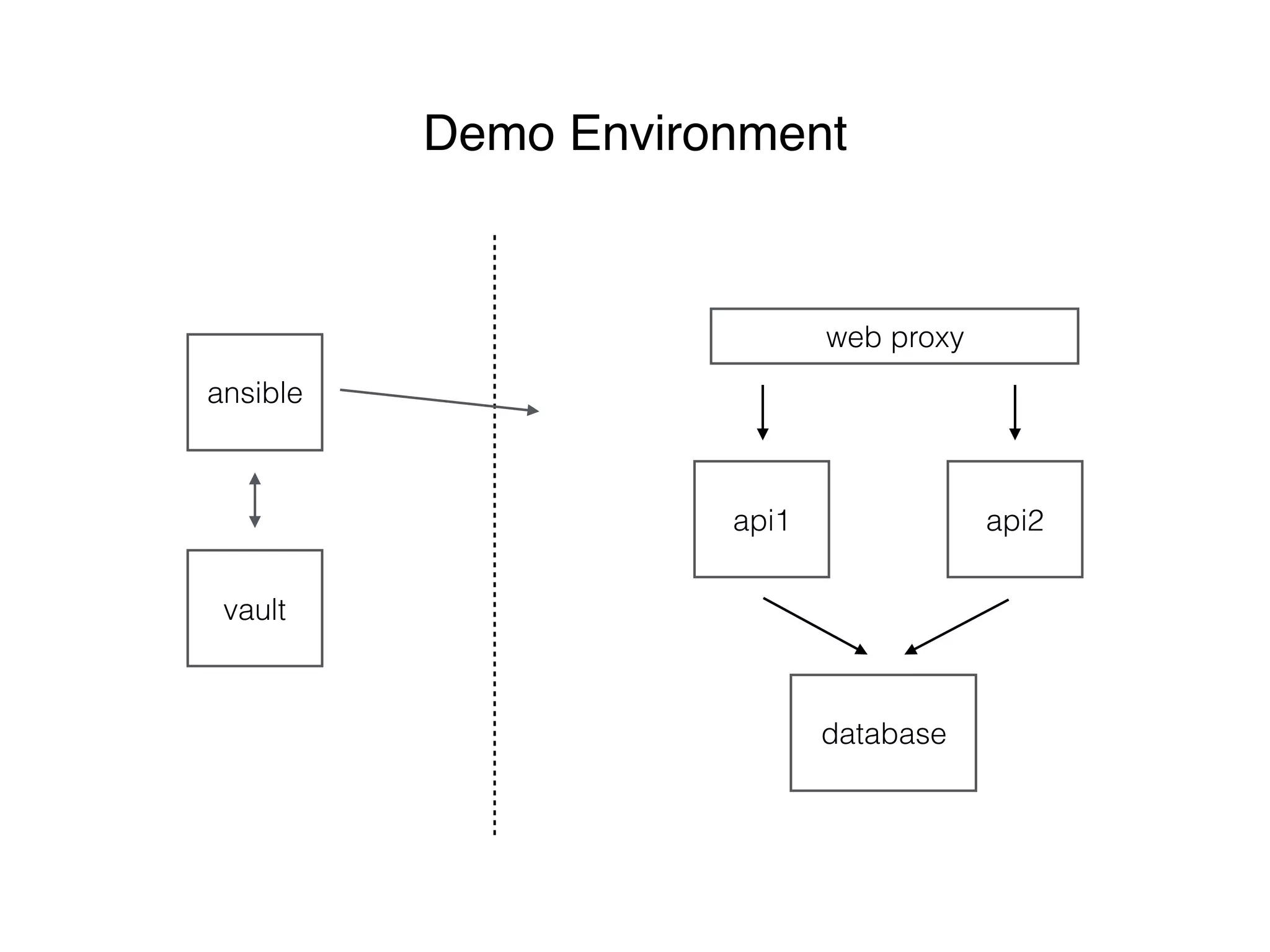
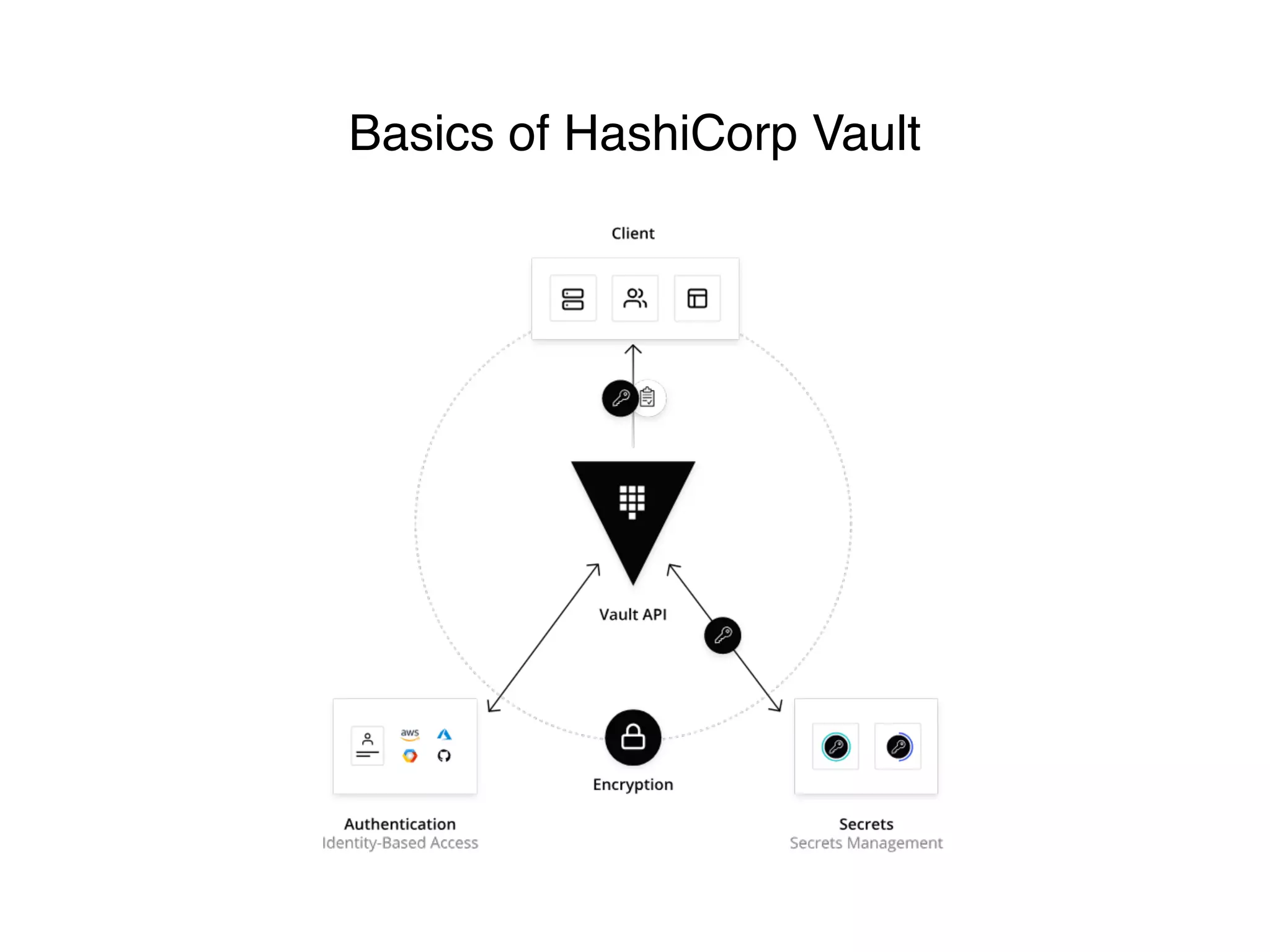
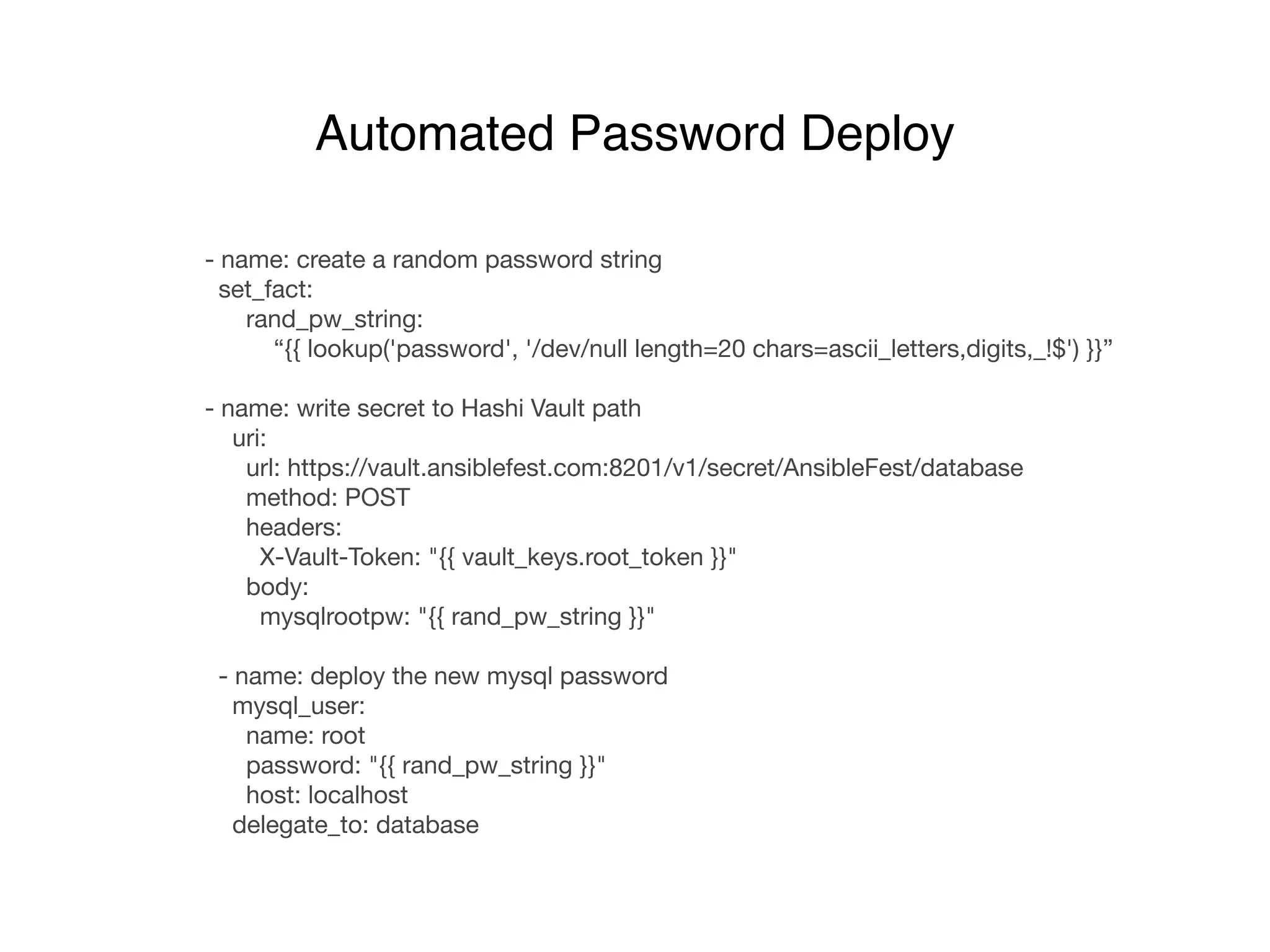
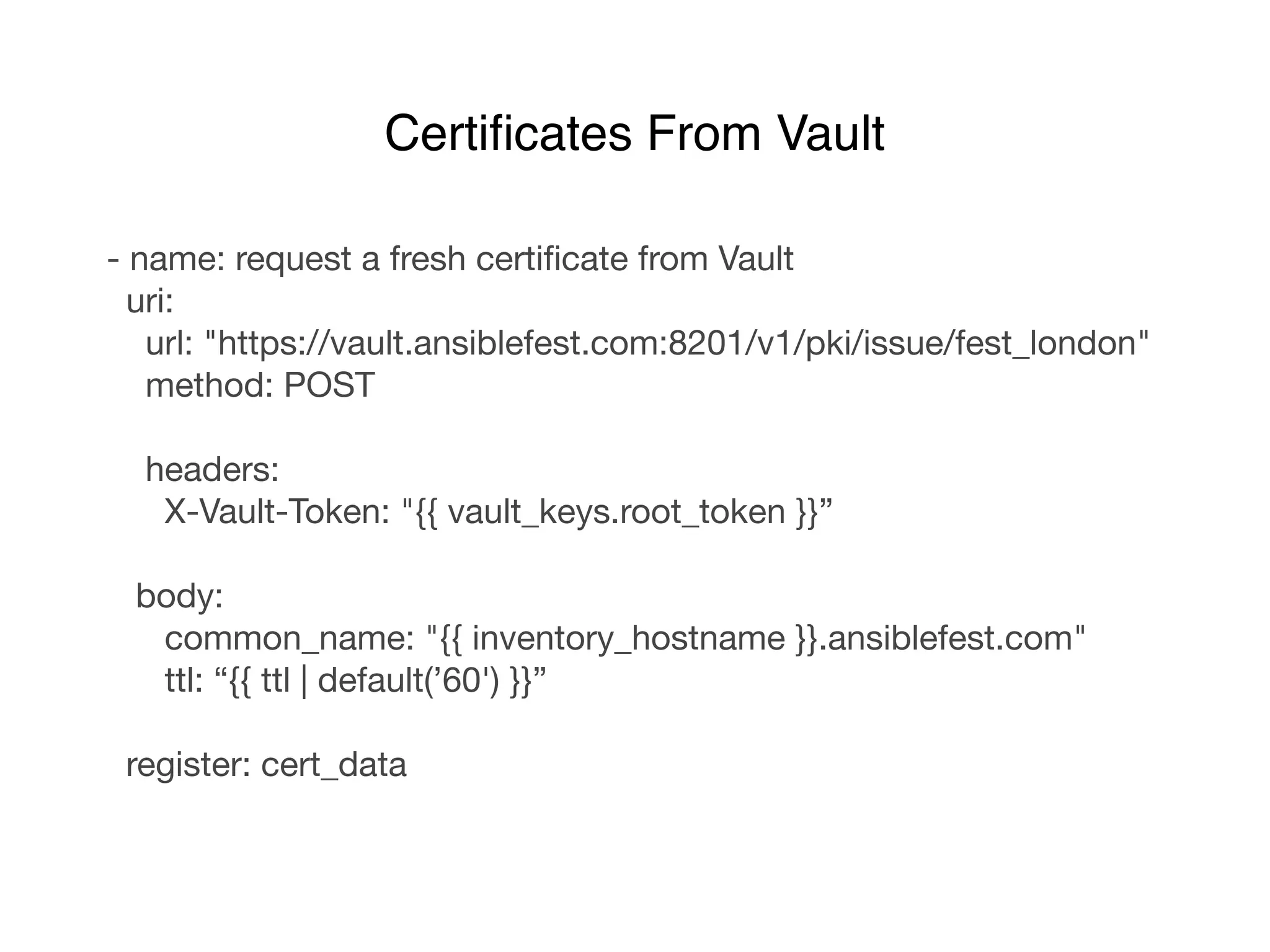
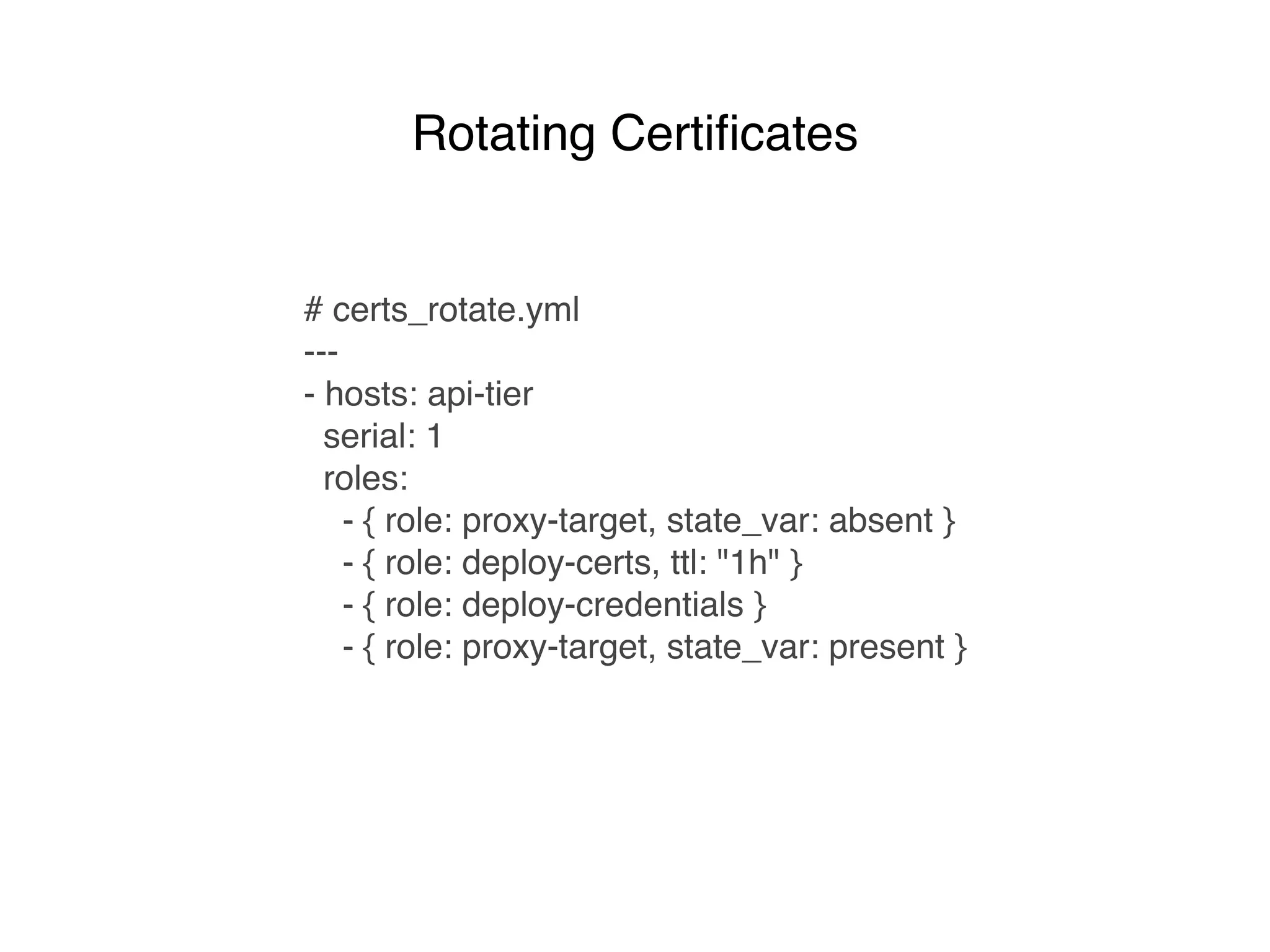
This document discusses managing shared secrets with Ansible. It describes using HashiCorp Vault to store secrets like passwords and SSL certificates centrally. It then shows how Ansible can be used to automate deploying secrets from Vault to applications and services, such as randomly generating database passwords stored in Vault and deploying them, and requesting and deploying rotated SSL certificates from Vault on an hourly schedule. The document advocates automating routine security tasks like credential rotation to improve security practices and free up time for developers and operators to work on more interesting problems.



![Security Best Practice
DevOps Reality
the
gumption*
gap
* initiative or courage: you haven’t the gumption to try [C18: originally Scottish]
The Gumption Gap](https://image.slidesharecdn.com/secretswithansible-181129192946/75/Secrets-with-Ansible-5-2048.jpg)