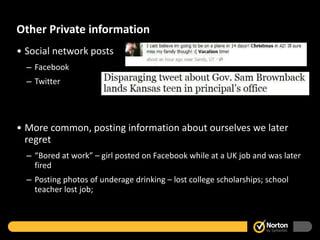
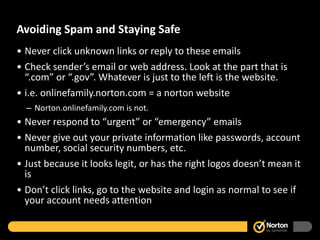
The document provides tips for staying safe online, including using strong and unique passwords, maintaining privacy settings on social media, protecting devices, recognizing and avoiding spam emails and links, spotting signs of malware infection, and dealing with cyberbullying. Some key recommendations are using complex passwords not related to personal information, logging out of devices when not in use, only downloading files and clicking links from trusted sources, and getting help from adults if witnessing cyberbullying.