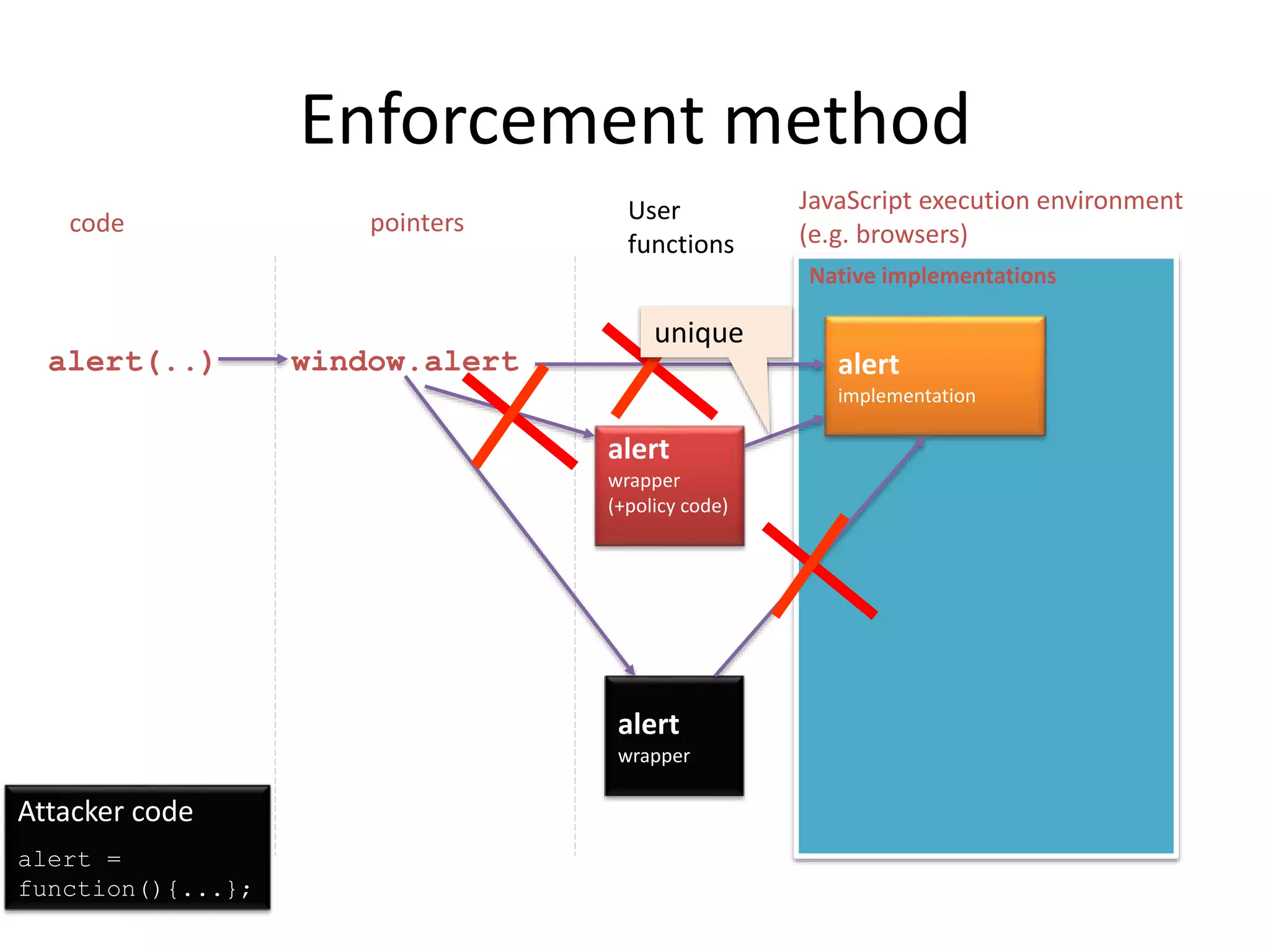
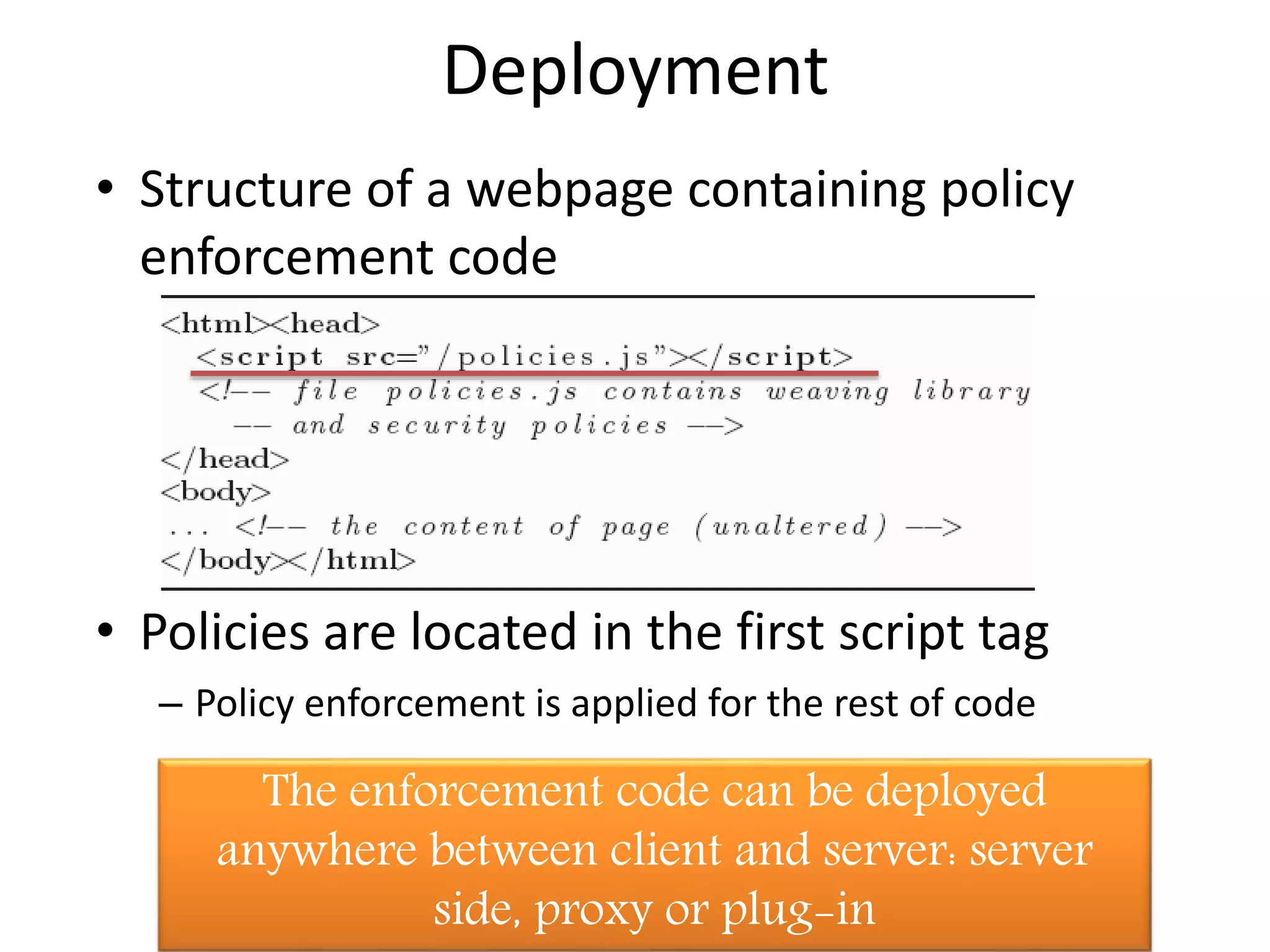
The document discusses a method for enhancing the security of JavaScript through self-protecting mechanisms, aiming to address vulnerabilities from injected (untrusted) JavaScript code, such as cross-site scripting (XSS) attacks. It outlines an approach that incorporates security policies directly into JavaScript code without requiring browser modifications, allowing original code to remain unchanged while ensuring safe execution. Future work includes developing the framework further and creating a policy language for better authoring of security policies.





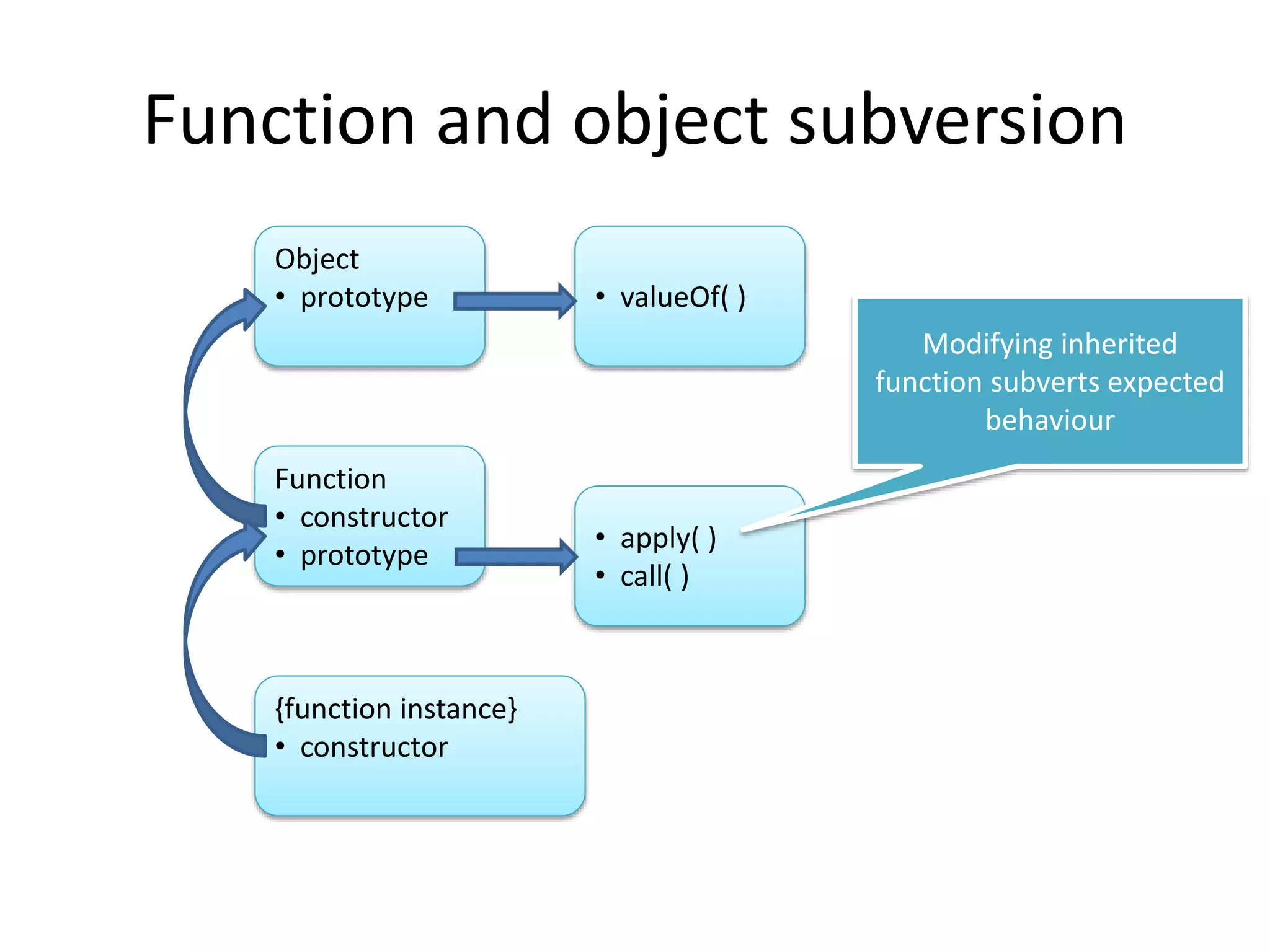



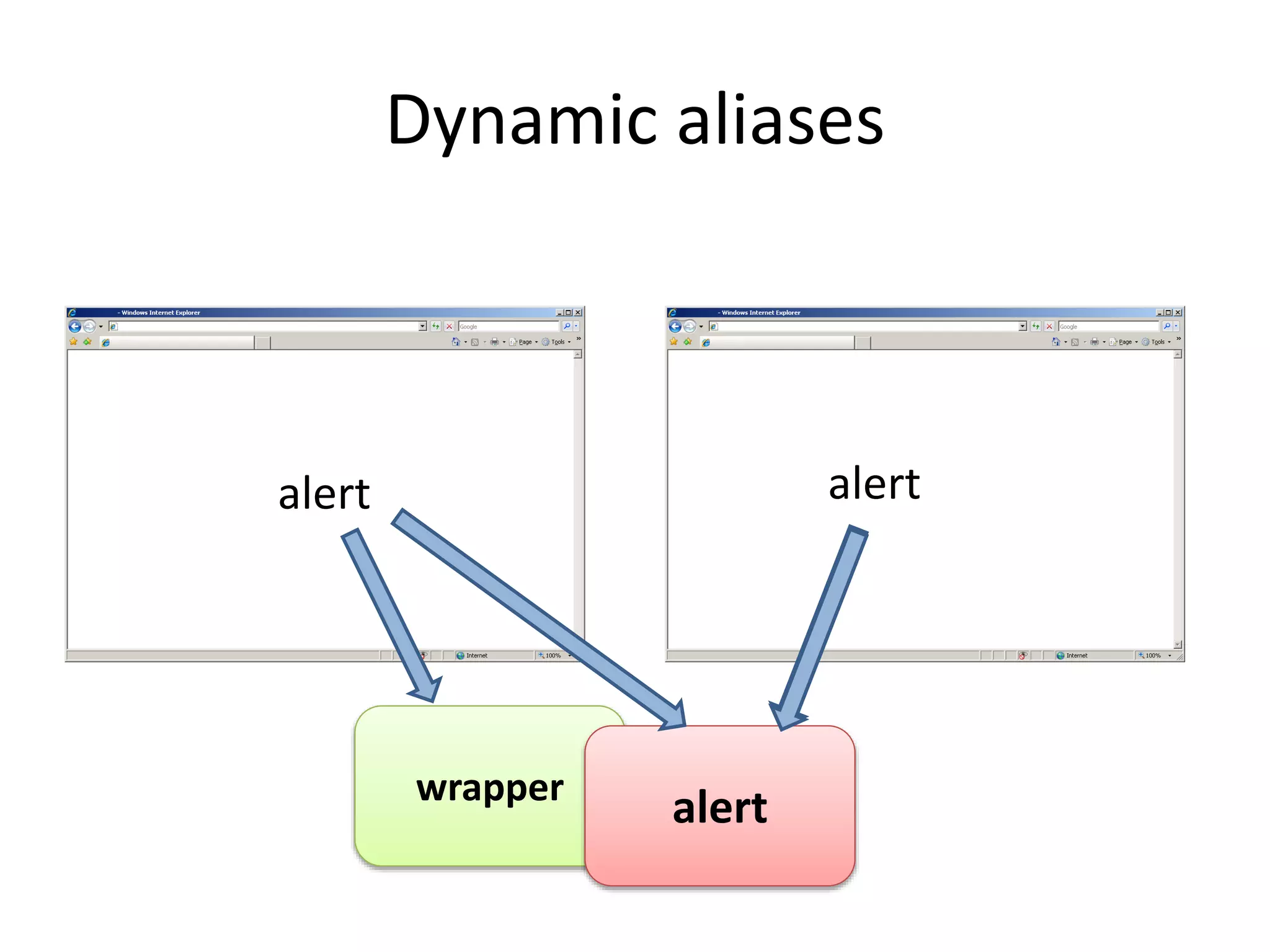
![Caller subversion (built-ins)
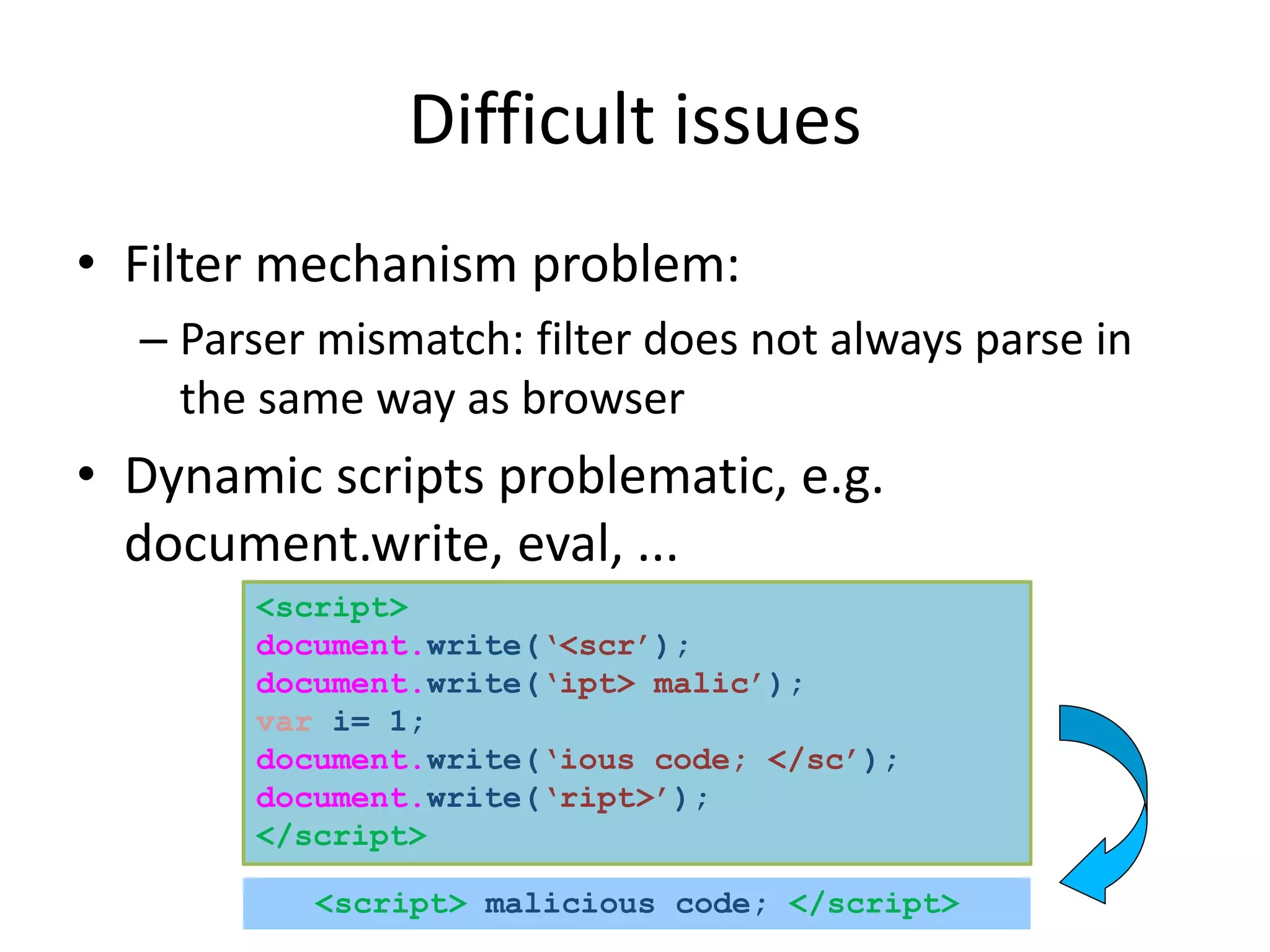
• Example of call by design:
[1,2,3].map(function(){})
• Takes function as an argument
• Can not be reliably wrapped – not a problem
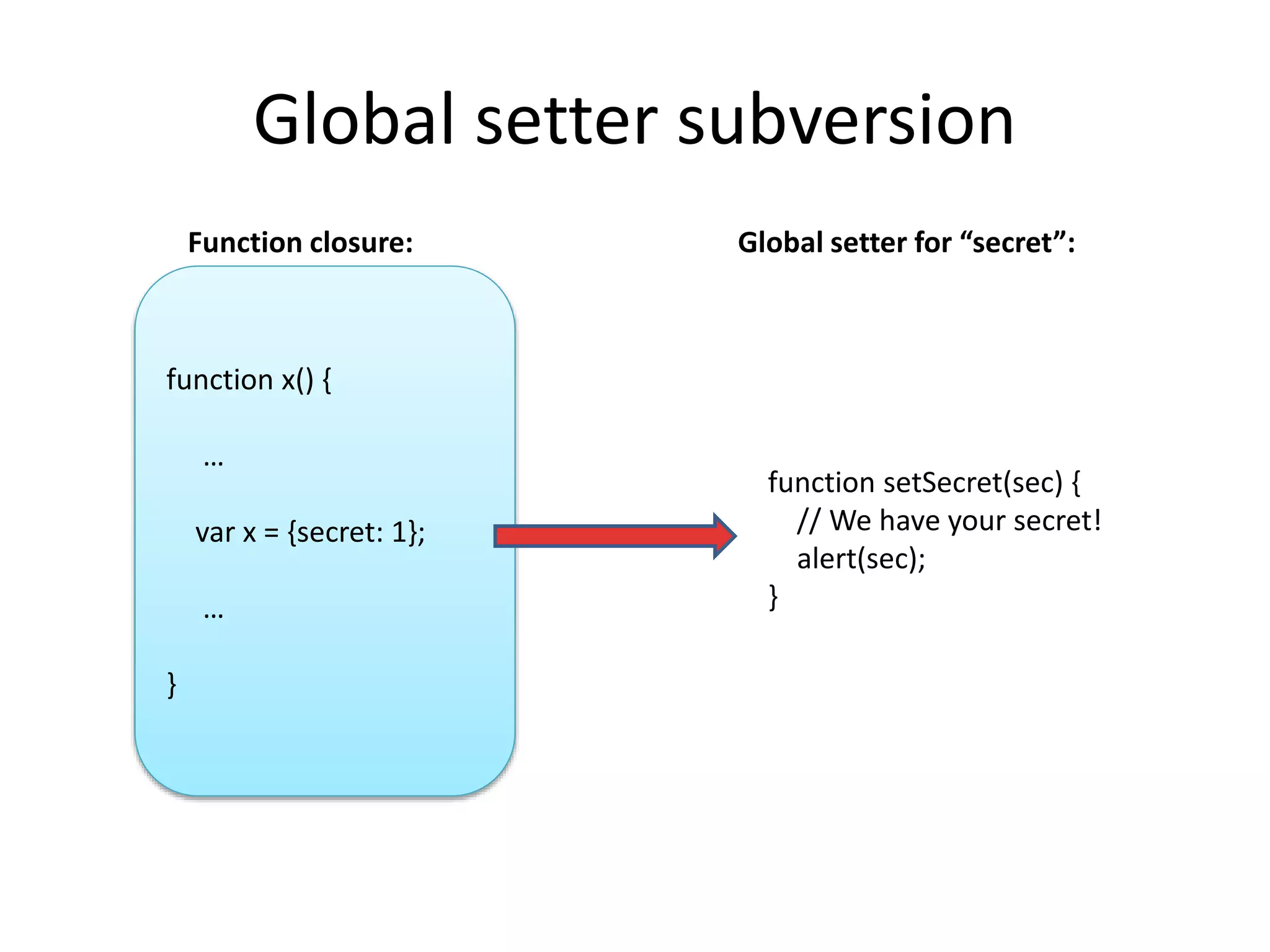
• Example of implicit call
obj.toString = function x(){return alert= x.caller}
alert(obj)
• Alert will execute the function which will restore alert
• Need to know an upper bound on potential implicit calls
• Remove any user defined functions on affected properties](https://image.slidesharecdn.com/safewrappers-jonasphu-140826120517-phpapp02/75/Safe-Wrappers-and-Sane-Policies-for-Self-Protecting-JavaScript-19-2048.jpg)


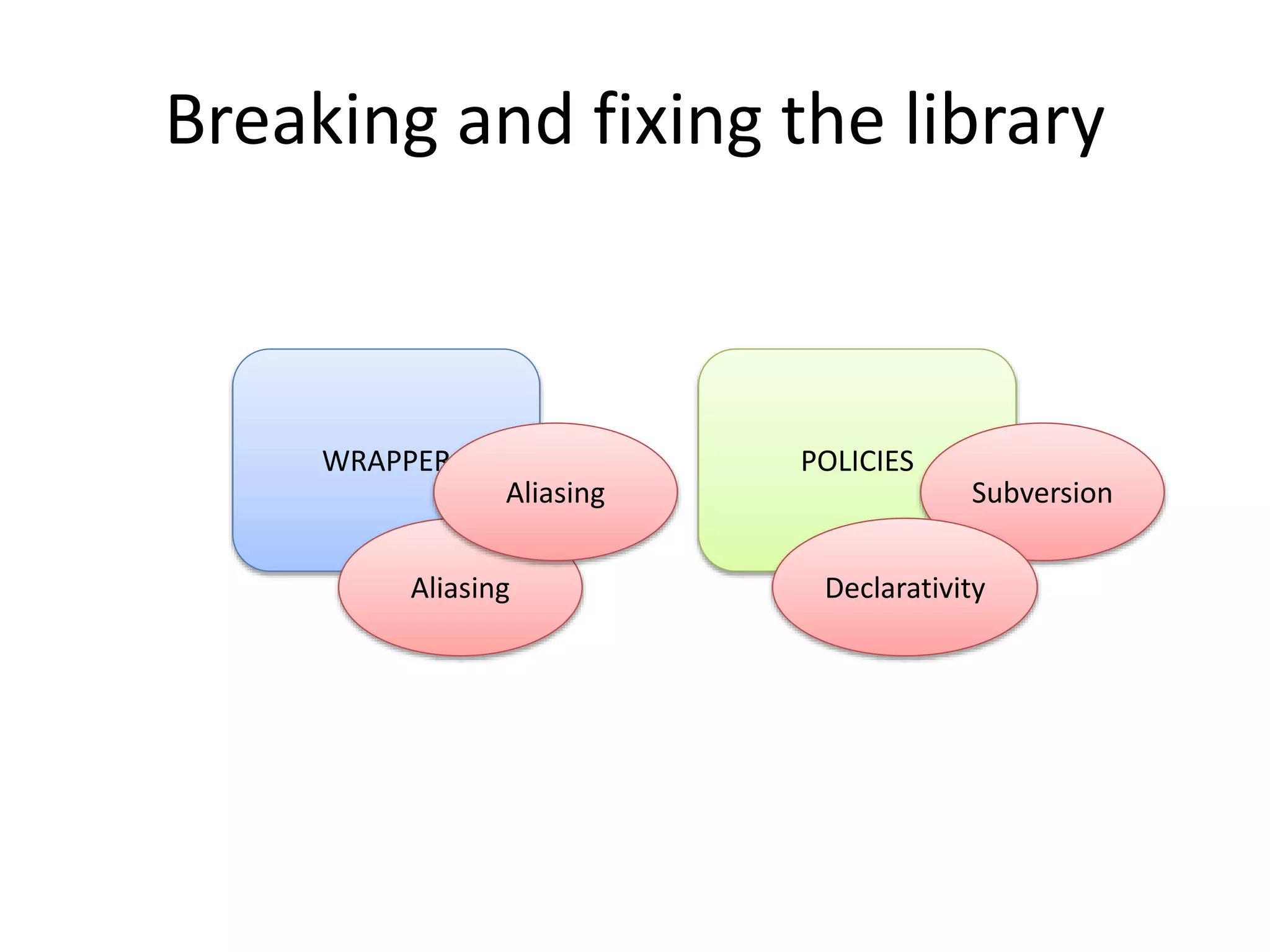
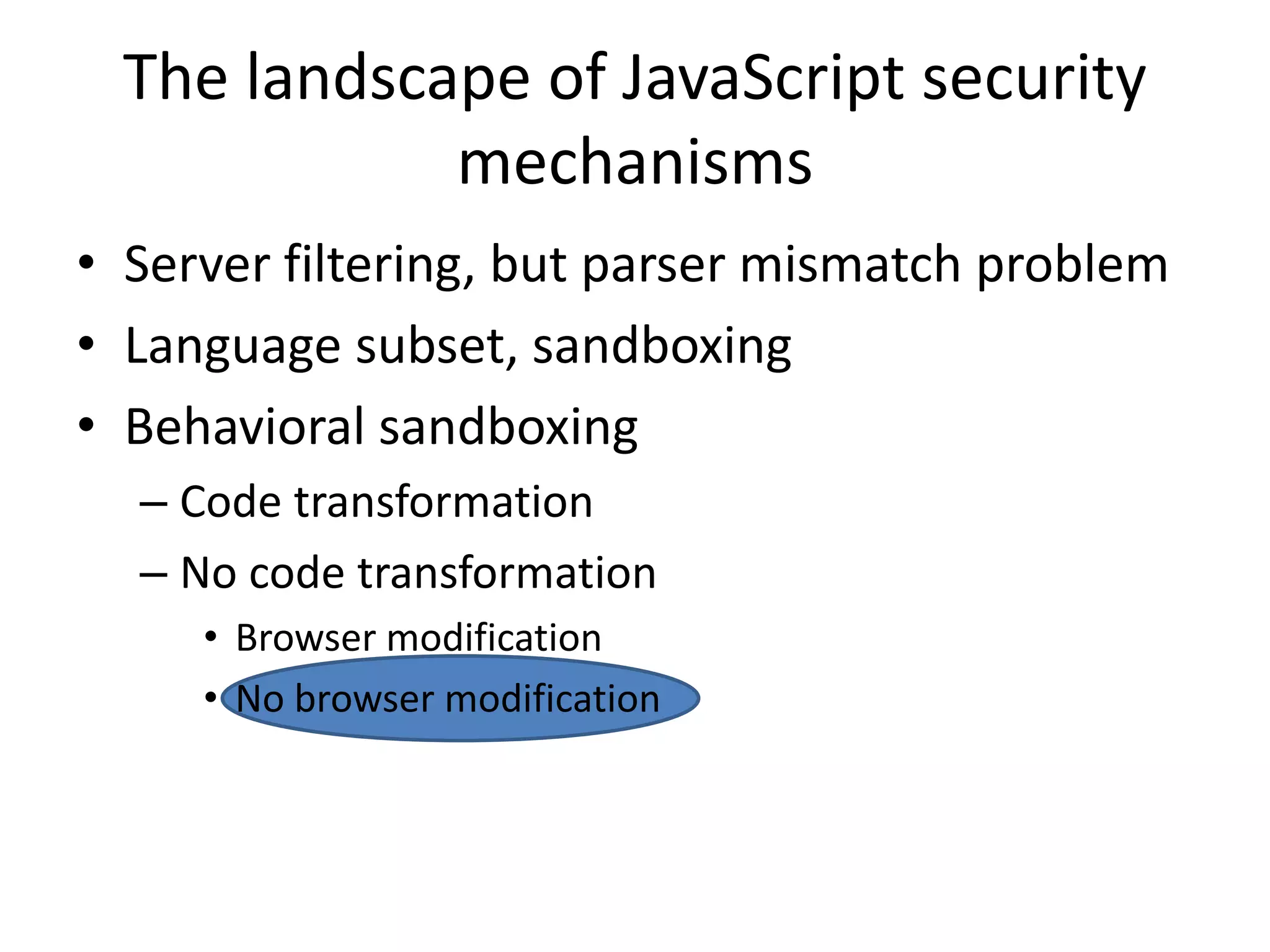
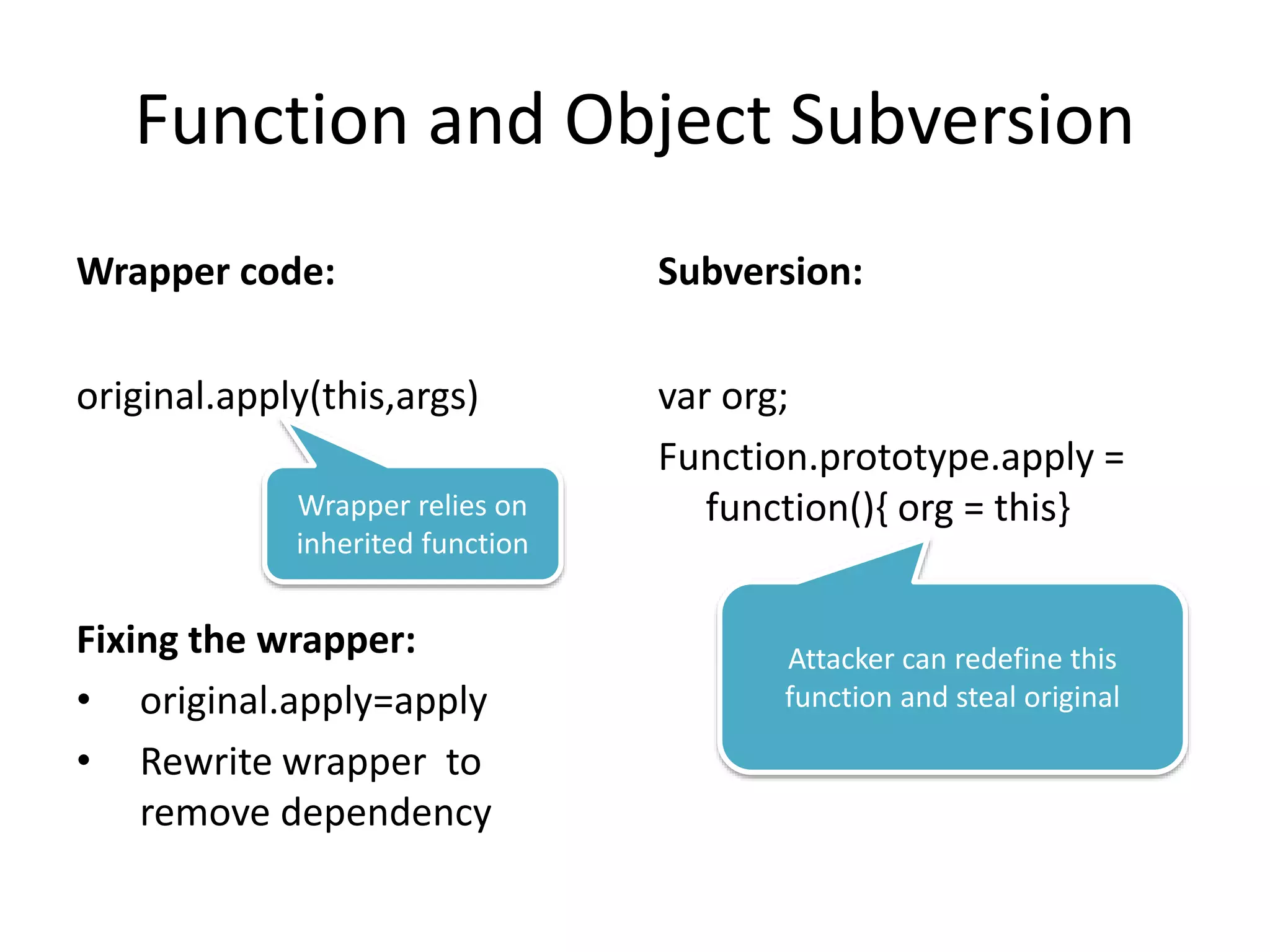
![Function and Object Subversion for
Policies
Policy code
var whitelist = {"good.com":true }
if(whitelist[address.substr(...))])
Policy expects
certain behavior
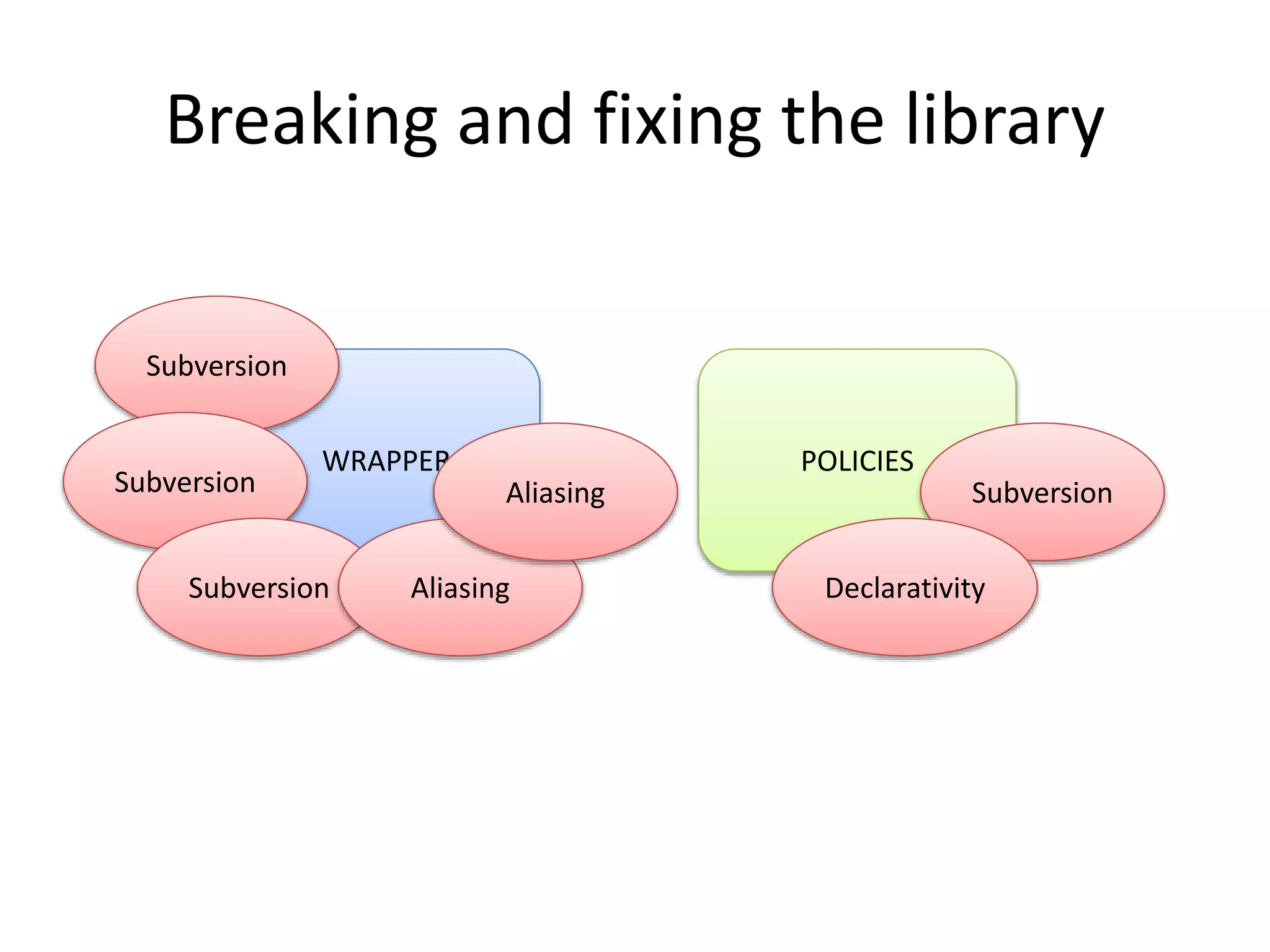
Fixing subversion
• hasOwnProperty()
• Use “safe” objects…
Subversion
Object.prototype[‘evil.com’]= true
String.prototype.substr =
function() { return ‘good.com’; }
The policy writer should not have
to remember this…
Attacker can easily
change the expected
behavior](https://image.slidesharecdn.com/safewrappers-jonasphu-140826120517-phpapp02/75/Safe-Wrappers-and-Sane-Policies-for-Self-Protecting-JavaScript-27-2048.jpg)

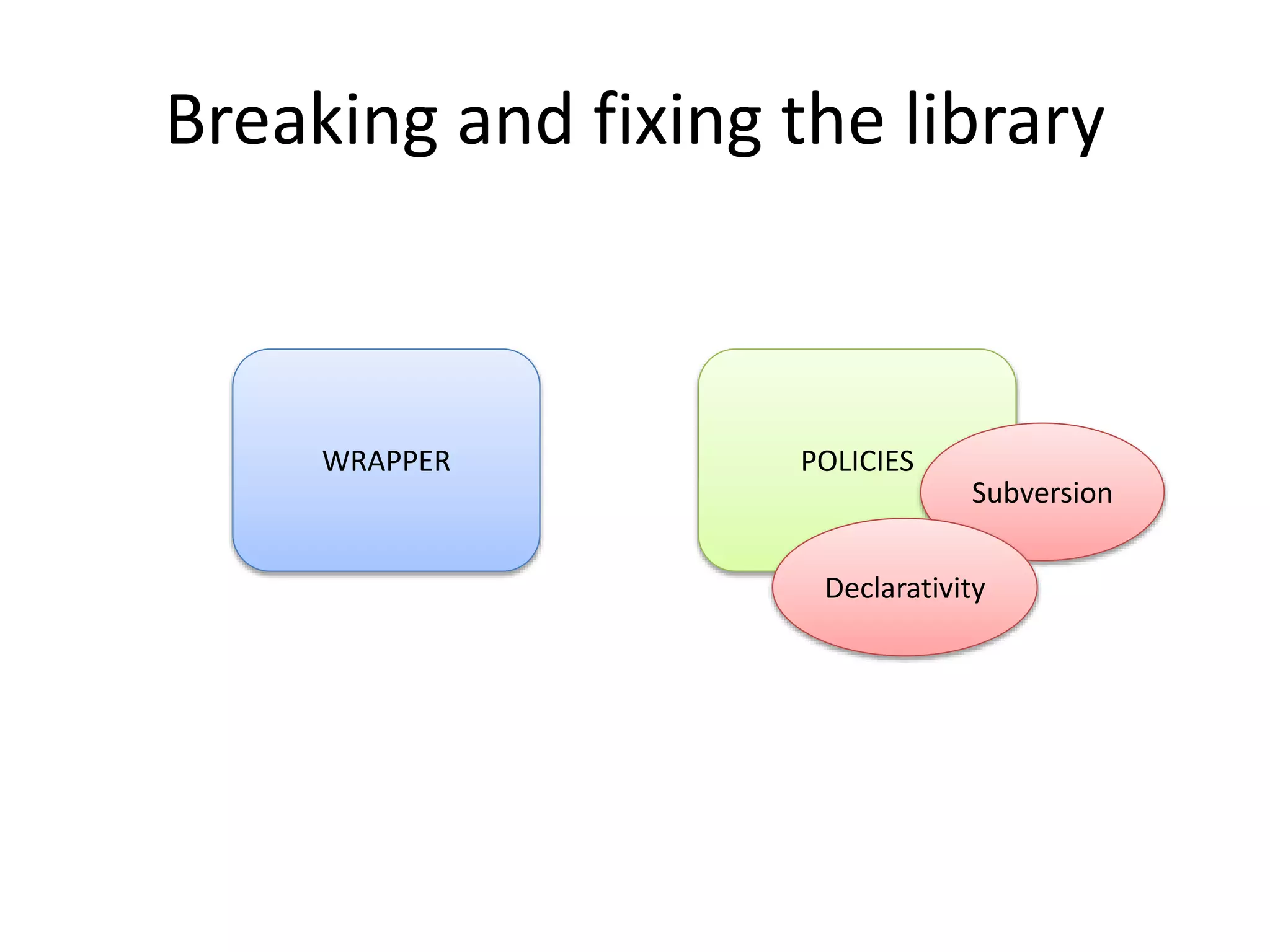
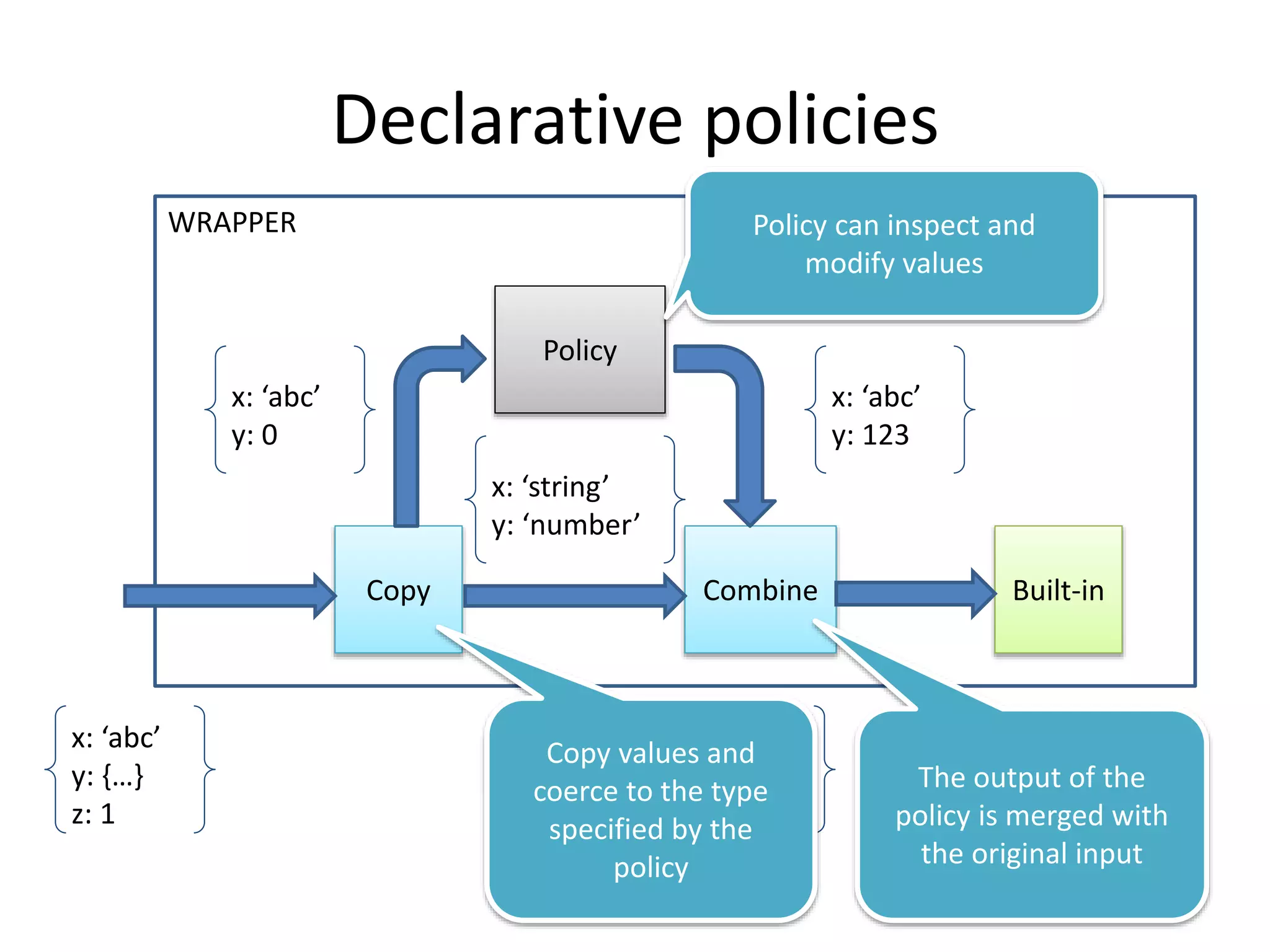
![Non-declarative vs. declarative policies
Policy code
if (whitelist[address])
img.src = address;
Fixing problem
Policy declare which types it
expects in a type language and
monitor enforces it
Attack
x = {toString: function() {
this.toString=
function()’bad.com’;
return ‘good.com’;
}
}
Policy code expect
address to be a string
Attacker can pass a statefull
object that pretends to be a
good string, but then
changes into a bad string](https://image.slidesharecdn.com/safewrappers-jonasphu-140826120517-phpapp02/75/Safe-Wrappers-and-Sane-Policies-for-Self-Protecting-JavaScript-30-2048.jpg)