This document presents a project to develop a secure mobile messaging application using identity-based encryption (IBE). The goals of the project are to demonstrate that elliptic curve cryptography is viable on mobile devices, implement security in a user-friendly way with transparent encryption, and design the system to be modular and extensible. The document provides background on IBE and related concepts. It then reviews related work on secure messaging applications and their limitations. The design and implementation of the proposed mobile messaging application are described, covering authentication, IBE parameter retrieval, message encryption and decryption. Finally, the document discusses the user experience, application performance, and concludes with areas for future work.









![9
domestic surveillance, and any electronic communications acquired because of limitationson the NSA's
ability to filter communications. They are interested in any communication if it is deemed to contain
usable intelligence,informationoncriminal activity, athreatof harmto people orproperty, isencrypted,
or isbelieved tocontainanyinformationrelevanttocybersecurity. That’sright. Simplythe factthatdata
isencrypted(all HTTPStrafficwouldfallinthiscategory) isjustificationenoughforthe NSAto have alook.
The NSA isempoweredtoretain thisdataforup to five years. Goodthingour governmentisasystemof
checks-and-balancesandthere’sprobablysomeone incharge of keepingthe NSA inline. Right? Wrong.
The discretionastowhoisactuallytargetedunderthe NSA'sforeignsurveillancepowersliesdirectlywith
itsownanalysts,withoutrecoursetocourtsorsuperiors. Oh,andif theyweren’tabletocollectitontheir
own, the NSA has the power to compel telephone and internet companies to turn over the
communicationsof anyindividual identifiedbythe NSA.[43]
Don’t look for private industry to protect your privacy either. Take Google for example. Many of their
services are encrypted usingSSL. They offer two step verification when accessing your Google account.
They even ensure that you are protected from rogue employees and contractors with their strict
contractual confidentiality agreements. However, though this might keep your data safe from some
prying eyes, they have prying eyes of their own! Google utilizes automated systems that analyze your
data on theirsystemsincludingemails,deviceinformation,loginformation,locationinformation,unique
application numbers, local storage, cookies and anonymous identifiers. The technical information they
gatherismostlyusedto improveexistingservicesand developnewones. The otherinformationcollected
isusedinamore invasivemanner:enabling “tailoredcontent”and“personallyrelevantproductfeatures”
such as customized search results and targeted advertising. They don’t keep all this sensitive data to
themselves either. They provide your personal information to their affiliates and “other trusted
businesses or persons” for external processing. They also share aggregated,non-personally identifiable
information publicly and with publishers, advertisers and other websites. Theywill also leave you high-
and-dryif youshouldhave arun-inwithlaw enforcement. They will giveupyourpersonal information to
“companies,organizationsorindividualsoutsideof Google”to“meetanyapplicablelaw,regulation,legal
process or enforceable governmental request”, leaving you vulnerable to law enforcement requests or
civil subpoenas. Don’tthinkthat deletingyourdata from theirserviceswill protectyou. Even afteryou
delete informationfromtheirservices, they“maynotimmediatelydelete residualcopiesfromouractive
servers”andthey may noteverremove the informationfrom theirbackupsystems. [34,61]
Yahoo participates in the EU Safe Harbor program for protecting personal data. However, like Google,
they have limitations when it comes to personal data retention. When you request your account be
deletedordeactivated yourinformationwillremainontheirsystemforanother90days. Evenonce your
account informationisdeleted,anyof your personal informationthatwas archived may remaininback-
up storage for“some periodof time”afteryour deletionrequest.[62,65]
Both Google and Yahoo (and most other services) provide opt-out ability for some of the more invasive
data collectionpractices.
1.1 SECURITY ISSUES IN MOBILE NETWORKS
Inadditiontothe securityconcernsmentioned above,mobilenetworkshave someunique securityissues
of theirown. In many distributedsystems,nodesare responsible forrelayingmessagestoothernodes.
Because nodes may have access to messages meant for other nodes there is the possibility that
malevolent nodes can passively eavesdrop on communication between other nodes. Denial-of-Service](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-10-320.jpg)
![10
(DoS) and flow disruption(the delaying, dropping,or falsifying of relay packets) attacks are also easy in
schemes where many of the nodes are inter-connected. Mobile ad-hoc networking is a type of
communication taking place in unpredictable and dynamic environments. These types of systems are
susceptible to signaling attacks, or transmitting false routing info, which can bring down the network.
Some schemes utilize mobile agents, or software programs that can travel from system to system to
perform tasks on behalf of a user. For example, a mobile agent could be tasked with visiting several
differentwebsitestofindandcompare pricesof items. These agents mustbe able tooperateinuntrusted
environments. Mobiledevicesthemselves have resourceconstraintssuchaslimited memory,processing
power, and batterylife. Thiscan limitthe amountof computationthatcan be performedorthe level of
communicationbetweendevices. Tradeoffs existbetweenbandwidthcapabilities,rangecapabilities,and
powerconsumption. Resourceexhaustion(transmittingexcessive packetstodrainthe batteriesofanode
device) canbe a significantissue. Designchoiceshave alarge impactonthe securityof mobile networks.
For example, in Peer-to-Peer (P2P) systems, decentralized systems are likely to be better suited for
handingDoS attacks,while semi-centralizedsystemswouldbe bettersuitedforhandlingauthentication.
Some systems are designedwith authentication and non-reputabilityas a primary concern. This means
that undercourt order the systemcan reveal private informationtogovernmentandlegal authoritiesby
cooperatingtoprovide akeyescrowservice.[2,5]
1.2 STATE OF THE ART
Messagingapplications allowyouto sendshort messagesand share images and video virtuallyinstantly
with your friends, family, co-workers and loved ones via your computer, tablet or mobile phone. Most
popular instant messaging apps are easy to use but communication is generally sent over insecure
channels. Accordingtothe ElectronicFrontierFoundation (EFF) mostbig-namemessagingservicesfail to
provide adequate securityfor their users. Security often comes at the cost of usability. Everyday users
mayhave trouble installing andconfiguringsecure applications,verifyingotherusers’ authenticity,setting
up accounts, or usingthe applications correctly. Forexample,Pidginallowssecure communicationviaa
plugincalled‘Off-The-Record’whichworksverywell,butonlyan advanceduser wouldbe able to install
andconfigure the plugin. In2011, about400 millionmobile deviceswereshippedandthere werearound
600,000 apps available for these devices. A big driving force for the attacks on mobile devices, and the
same reason that mobile securityneedstobe stressed,isthat the value of mobile paymenttransactions
isprojectedtoreach over$600 billionthisyear. [15, 44, 66, 67]
Next I review three of the most popular messaging apps being used today and their security
characteristics. I chose to lookat WhatsApp,Hangouts,andSnapChat because Ifeel theybestexemplify
the currentstate of the art. Below isachart fromthe ElectronicFrontierFoundation’swebsite. It’scalled
the Secure MessagingScorecardanditshows thesecurityprotectionsprovidedbymessaging applications.
As youcan see,these three appsdidnotscore verywell.](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-11-320.jpg)
![11
FIGURE 2 - EXCERPT FROM THE ELECTRONIC FRONTIER FOUNDATION'S SECURE MESSAGING SCORECARD
WhatsApp is an instant messaging application developed by WhatsApp, Inc. It is available on all major
mobile platforms including iPhone, Android, and Windows Phone. The company was founded by two
former Yahoo! Engineers in 2009 and was eventually acquiredby Facebook in February of 2014. There
are 500 million registered (350 million active) WhatsApp users. WhatsApp is so incredibly popular
because itiseasy to use,cheaperthantext(SMS) messaging(especiallyinternationally),costsonly$0.99
per year, and has no ads. Until 2012, all of WhatsApp messages were sent in plaintext. Though it has
since begun encrypting messages it still does not score highly (2 out of 7 points) on the EFF's secure
messaging scorecard. The app lost points because WhatsApp has access to the keys that messages are
encryptedwith,userscan'tverify otheruser'sidentities(noauthentication),pastmessagesare notsecure
if the encryption keys are stolen (no forward secrecy), the application source code is not open to
independent review, and its security design is not properly documented. Since the acquisition by
Facebook, WhatsApp has taken more interest in security. In November 2014 they entered into a
partnershipwith OpenWhisperSystemstoprovide end-to-endencryptionbyincorporatingthe protocol
usedintheirTextSecure application. [45,68]
Hangouts is Google’s mobile messaging offering. Its instant messaging feature is incorporated into the
Gmail web-basedemailsystemand the Hangouts mobilemessagingappisavailableonAndroidand more
recently on Apple devices. The Hangouts app offers live video and voice conversations in addition to
messaging. In 2013 Google reported its Google+ services had reached 540 million active users. All
messagesinHangoutsare sent overencrypted HTTPS connectionwith128-bit encryption,usingTLS1.2.
However, like WhatsApp, Hangouts only scored 2 out of 7 points on the EFF scorecard. Keep in mind
Google’sPrivacyPolicymentionedearlier. [46, 47, 69]
SnapChatisaphotoandvideomessagingappcreatedby StanfordUniversitystudents EvanSpiegel,Bobby
Murphy,and Reggie Brown. The mainfeature of the applicationisthatphotosand videossentare auto-
destroyed within 10 seconds, removed from both the recipient’s device and SnapChat’s servers. The](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-12-320.jpg)
![12
service boasts 100 million active users who send 700 million photos and videos daily. However, their
premise is a little flawed. According to their official Privacy Policy, they “can’t guarantee that messages
will be deletedwithinaspecifictimeframe.Andevenafterwe’vedeletedmessagedatafromourservers,
that same data may remain in backup for a limited period of time. We also sometimes receive requests
from law enforcement requiring us by law to suspend our ordinaryserver-deletionpractices for specific
information. Finally, of course, as with any digital information, there may be ways to access messages
while still intemporarystorage onrecipients’devicesor,forensically,evenaftertheyare deleted.”
In additiontobeingunable to do goodon theirmainpremise,theyalsoletcompanies “use cookies,web
beacons, and other technologies” to collect your personal information including unique device
information (device identifiers, manufacturer,and operatingsystem), your IP address, the web browser
you are using and the pages you are viewing with it, the links you are clicking, and how much time you
spenddoingit. Theyuse thisinformationto “analyze andtrack data, determine the popularityof certain
content,and betterunderstandyouronline activity.” Theyalsosell thisinformationtoothercompanies
to use in targeted advertising. The kicker: “Snapchat does not currently respond to do-not-track signals
that may be sentfromyour device.”
Justlike the twoapplicationsreviewedpreviously,theappthatistrustedtoprivatelymanageclosetoone
billionphotosandvideoseverydayonlymanagedtoscore 2 pointsonthe EFF scorecard. In a breachof
their systems in October 2014 members of a hacker forum claimed to have collected at least 100,000
Snapchat photos. They were able to do this because the service uses very elementary encryption that
would take a good hacker just a few-hours to reverse-engineer and find the key. This would be bad
enoughif eachuser hadtheirown unique keys,butbecause theyusedasingle universalkey,once itwas
exposed the attacker would be able to decrypt everything in the system. Despite such massive security
breachesbeingacommonheadlinetosee onthe news,take Targetand Home Depotforexample,people
don’t seem to mind as long as they get their free identity protection!. To quote an expert in the field:
"These types of breaches will definitelystop people from using Snapchat … until they have a really cool
picture to share." [48 - 50, 70]
1.3 PROJECTGOALS
If securitycan be made simple,secure applicationswouldbe more readilyadoptedbyalargernumberof
users who might not otherwise be willing to deal with the headache, frustration, and tedium of current
securitymeasures. Tothatend,I propose the constructionof asecure messagingapplicationforAndroid
devices. Thisimplementationisbuiltontopof the XMPPstandardasthe instantmessagingandpresence
protocol and Identity-BasedEncryption(IBE) asthe securitymechanism. The majorgoal of thisproject is
to achieve a high level of security without distracting the user with confusing and error prone security
configuration.
The paperstarts witha reviewof the currentstate of the art, some of the outstandingsecurityproblems
that exist in mobile messaging, and a review of some common solutions to these problems. In chapter
two I do a quick review of the concepts involved in this paper such as mobile messaging,encryption,
ellipticcurvesandbilineargroups, andidentity-basedencryption. Ithenjustifymychoicesof the Android
operatingsystem,the XMPPmessagingprotocol,IBEandthe JPBClibrary. Inchapterthree Ireviewsome
of the relatedworkinsecure messagingapplications. In the fourth chapterI describe mysecure mobile
messaging app and provide the details in its implementation. I review the user experience and](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-13-320.jpg)

![14
CHAPTER 2 – BACKGROUNDCONCEPTS (IBE, ECC, AND THE
PBC LIBRARY)
In an Identity-Based Encryption (IBE) scheme,the public key of a user may be an arbitrary string like an
email addressorotheridentifier. Messagesare encryptedusingacombinationof the systemmasterkey
and the id of the recipient. Usersmustgo to a trustedparty and prove theiridentityinordertoobtaina
private keywhichwill allow himtodecrypt messages. Thistrustedpartyis knownas the Key Generation
Server (KGS). During system setup, the KGS creates a master public keyand public parameters. [19, 27,
30, 59, 60]
FIGURE 3 - IDENTITY-BASED ENCRYPTION (IBE)
2.1 HISTORY OF IBE
The concept of Identity-BasedEncryption (IBE) was first proposed by Adi Shamir, famous co-inventor of
the RSA algorithm (among others), in 1984. Shamir introduced the concept of IBE as an approach to
simplifypublickeyandcertificatemanagementinaPublicKeyInfrastructure (PKI). InanIBEsystemauser
can sendan encryptedmessagetoanotherpartysimplybyknowingtheiridentityaswell asasetof global
parameters, eliminatingthe needtodistribute aseparate publickeyforeach userin the system.
Althoughthe concept initially received alotof interest,itwasn'tuntil several yearslaterthat Bonehand
Franklinintroducedthe firstIdentity-BasedEncryptionscheme usinggroupswithefficientlycomputable
bilinearmaps.The original Bonehand Franklinresultusedthe random oracle heuristicto prove security
under the Bilinear Diffe-Hellman assumption and a significant open question was whether the random](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-15-320.jpg)
![15
oracle model couldbe removed. Bonehand Franklinimplementedthe firstfunctional IBEscheme inthe
random oracle model (in 2001) and it was perfected by world-renowned cryptographers at Stanford
UniversityunderUSDefense fundedresearchprograms. Theirimplementationcame tobe knownasthe
StanfordPairingBasedCryptography(PBC) library.
Followingthe breakthroughresultof Bonehand Franklin,there hasbeensignificantprogressinrealizing
IBE in the standard model. First, Canetti, Halevi, and Katz proved security without the random oracle
heuristic,butundera weaker “Selective-ID"model where the attackermustdeclare the identity thathe
will attack before even seeing the system's public parameters. Boneh and Boyen then provided an
efficient selectively secure scheme. Subsequently, Boneh and Boyen and Waters gave fully secure
solutions in the standard model. The Waters scheme provided an efficient and provably fully secure
system in the standard model under the decisional Bilinear Diffie-Hellman assumption; however, one
drawback was that the publicparametersconsistedof O(λ) group elementsforsecurityparameterλ. [7,
21, 27, 59, 60]
There hasbeensignificantworkonIBEsince then. Boldyreva,Goyal,andKumarcame upwithan efficient
revocation scheme for IBE in 2008. Brent Waters came up with the first Hierarchical IBE (HIBE) scheme
and an IBE systemwithshortparametersin 2009. De Caro, Iovino,Persiano realizedthe firstAnonymous
HIBE protocol in 2010. [21, 28, 31]
2.2 ELLIPTIC CURVES
An elliptic curve is one formed by an equation of the form y2 = x3 + ax + b over a finite field of prime
orderq (x, y ∈ q)
FIGURE 4 - ELLIPTIC CURVE Y2
= X3
– 3X + 3
Elliptic Curve Cryptography (ECC) is dependent on the Bilinear Diffie-Hellman (BDH) problem being hard
to solve. A problem being ‘hard to solve’ means that the result of mathematical operations are fast to
compute, but hard to reverse. For the BDH problem, this means findinggxy
given g and the values of gx](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-16-320.jpg)
![16
andgy
. As of 2006, the most efficientsolutionstothe BDHprobleminvolvesolving the discretelogarithm
problem (DLP); find x given g and gx
. Maps are also central to ECC. Maps are classified as one-way
functions, meaning it is easy to calculate their result given a pair of operands but hard to calculate the
inverse. The pairings take place using two groups, an additive group and multiplicative group, over the
same prime orderq. The additive groupisimplementedusingagroupof pointsonan ellipticcurve. The
multiplicativegroupisa subsetof a multiplicative group of points overafinite field. Thissubgroupmust
have the followingthree properties:bilinearity,non-degeneracy,andcomputability. Thismapisreferred
to asa “bilinearpairing.” These mapsare derivedfromeitherthe Weil(pronouncedvay)orTate pairings.
Of these two, Tate pairingis typicallyfaster. Computationallyefficientonesare basedon bilinearmaps.
Map isa functionpairingelementsfromone grouptoanotherof the same prime orderwherethe discrete
logarithmproblemishardinthe firstgroup. Forexample,given:
Pair(a ∙ X, b ∙ Y)= Pair(b ∙ X, a ∙ Y)
Calculatinga∙ X iseasy,and finding agivenX anda ∙ X,ishard.
2.3 IDENTITY-BASED ENCRYPTION
There are four major algorithms or steps performed in Identity-Based Encryption: Setup, KeyGen,
EncryptionandDecryption.
Setup:Performedbythe KeyGenerationServer. Createsmasterpublicandprivate keypairbased
on initializationparameters.
Key Generation:Performedbythe KeyGenerationServer. Generates andreturns users’private
keyswhenrequestedaftertheyhave authenticatedthemselvestothe KGS.
Encryption: Performedbythe users. Usingthe recipientsIDalongwiththe masterpublickey,the
userencryptsthe message andsendsitto the recipient.
Decryption: Performed by the users. Using their private key,the receiving user can decrypt the
encryptedmessage.
For more in-depth informationon bilinear pairing and identity-based encryption, see Baek et al’s paper
“A Survey of Identity-Based Cryptography,” Youngblood’s “An Introduction to Identity-Based
Cryptography,”andLee et al’s“Secure KeyIssuinginID-BasedCryptography”[30,59, 60]
2.4 REVIEW OF ALGORITHMS AND THEIR CLASSIFICATIONS
The security strength of an IBE system is determined by the underlying algorithm, which, in turn, is
determined by the bit-length of the parameters. Depending on system requirements, different curves
and initializationparametersmightbe chosen.
Here is a summary of pairings available in PBC cryptosystems. ‘Type a’ is considered the fastest pairing
and goodforcryptosystemswhere groupelementsize isnotcritical. Itutilizesthe supersingularcurve y2
= x3 + x over a group order Solinas prime. ‘Type dn’ pairing is good for cryptosystems when group
elementsmust be as short as possible. It uses the MNT method to generate curves. ‘Type e’ pairing is
considered to not be useful butrequiresonlymodulararithmetictoimplement.‘Type f’pairingis useful
for insuringagainstfuture finite fielddiscrete logalgorithmimprovements. The curve is foundusingthe](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-17-320.jpg)
![17
Paulo Barreto method. ‘Type gn’ pairing uses Freeman-Scottalgorithmto generate curves. It is slower
than embeddingdegree 12 pairings. No good use for this pairinghas beenfound. Some cryptosystems
need the curve order to be a specific number, e.g. N = p q where p and q are large primes so that N is
hard to factorize. With ‘Type a1’ pairing, a suitable pairing can be found by using the same curve as for
type a pairings. Belowisatable of pairings andtheirattributes fromthe StanfordPBCLibrary.
Type Base Field Size
(bits)
k Dlog security
(bits)
a 512 2 1024
dn n 6 6n
e 1024 1 1024
f 160 12 1920
gn n 10 10n
a1 1024 2 2048
TABLE 1 - PAIRING TYPES (PBC)
There is one particular curve classification that is of particular importance in PBC, supersingular curves.
Supersingularcurvesare of the formy2
= x3
+ x. As of 2007 there are no known weaknessesfor(carefully
selected) supersingularcurves.
Identity-BasedEncryptionisreferencedinseveralInternetEngineeringTaskForce (IETF) draft standards;
RFC 5091 - Identity-BasedCryptographyStandard(IBCS) #1: SupersingularCurve Implementationsof the
BF and BB1 Cryptosystems, and RFC 5408 - Identity-Based Encryption Architecture and Supporting Data
Structures,amongothers. [16, 17, 22]
2.5 OTHER INTERESTING THINGSABOUTIBE
Identity-BasedEncryptionhaspotentialapplicationsinasecure machine tomachine(M2M) scheme inan
Internet-of-Things (IoT). Identity-based proxy re-encryption schemes can be derived from existing IBE
schemes. ProxyRe-Encryption(PRE) hasmanypractical applicationslikeemailforwarding,distributedfile
systems, andDigital RightsManagement (DRM).
In Fuzzy IBE, users’ keys and ciphertexts are associatedwith multiple descriptive attributes,ex. a user’s
identityandtime. A user’skey can decrypt a particular ciphertextonlyif some numberof attributes(so
called“error-tolerance”)matchbetweentheciphertextandthe key. The collusion-resistance propertyof
FuzzyIBE givessystems protectionfromuserswhohave beenrevoked. Attribute-BasedEncryption(ABE)
isan encryptionscheme thatis derivedfromFuzzyIBEandallowsthe authoritytospecifymore advanced
decryptionpolicies. ABEisusefulinDisruption-TolerantNetworks(DTNs)andforsecuring medical records
(or similarlysensitive documents) onmobile devices.[7,9,16, 17, 23, 25, 28]
2.6 NOTABLE IMPLEMENTATIONS
Boneh and Franklin developed a C++-based IBE implementation published under an MIT-style license
commonly referred to as the “Stanford IBE System”. In 1988 Shamus Software developed a C++-based
cryptographic library called “MIRACL” which follows Boneh and Franklin's IBE scheme. It is currently
licensed to hundreds of leading companies in the United States, Brazil, Britain, Germany, France,
Switzerland, South Africa and Australia. Its cryptographic runtimes can be found in chips, operating
systemsandsoftware applicationsinindustriesrangingfromdefense andintelligence tofinancialservices
and software as a service companies. In 2003 the Hewlett Packard Lab in Bristol UK developed a](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-18-320.jpg)
![18
healthcare informationsystembuiltonIBE. In 2004, Voltage securitydevelopedanIBE implementation
that providespluginsforMicrosoftOffice,Hotmail,andYahoo.[6,7, 9, 58 - 60]
2.7 PROS AND CONS
The major issues with IBE are the key escrow and key revocation problems. The key escrow problem
states that, because the Key Generating Server has access to all private keys in the system, it’s possible
for them to decrypt any ciphertext in the system and forge any entity’s signatures. There have been
several proposedsolutionstothis problem. One solutioninvolvesusing multiple KGSs,where eachKGS
onlyhas one piece of the key information andthisneedstobe combinedwithpiecesfromotherKGSsto
get a complete key. Another solution involves trusted third-party mediators that help a user decrypt
messages. The keyrevocationproblemdealswithhowtoefficientlyrevoke usersfromthe systemaswell
as howtopreventrevokedusersfrom colludingwithvalidusers toreadencryptedmessages. A technique
that could solve bothkeyescrow and revocationproblemsisusinga threshold(e.g.timeout) technique,
where keys expire after a given length of time and so users are forced to periodically renew their keys.
One major drawback to either solution is that they involve additional infrastructure which makes the
systems more complex and therefore you lose some of the advantages you have over a PKI scheme.
Another drawback of Elliptic Curve Cryptography is that it can be significantly slower than the modular
exponentiation usedby RSA. It has been shownto be 10x slower at moderate securitylevels and up to
nearly 20 times slower at high security levels. The inefficiency is due to the fact that the pairing
computationsinvolvedare roughly20timesslower.[16– 18, 21, 26 – 30, 59]
The majoradvantage of Identity-BasedEncryption overotherencryptionschemes isthatit is certificate-
less. It doesn’trequire acomplex keymanagementinfrastructure like PublicKeyEncryption (PKE) does,
eliminatingthe storage andcomputingoverhead of storing,verifying,andrevokingcertificates. Usersin
an IBE systemdo not needto pre-share secrets. This lendsitself well tomobile anddistributedsystems
where devices need to be able to find, authenticate, and transact with each other without a central
authority. Significantlysmallercryptographicparameters,includingsmall publicandprivate keys,canbe
used in ECC than in other competitive public-key cryptographic systems such as the popular RSA
cryptosystembutwithequivalentlevelsof security. Whenusingschemeswithasmall numberof pairing
calculations(someof whichcanbe eliminatedduringrepeated operationswiththesame user),the system
can be computationally less intensive (light-weight). These restrictionsare critical to preserve power in
small, resource-constrained devices as the power to transmit one bit in a typical wireless sensor is
equivalent to approx. 2,090 clock cycles of execution on a microcontroller. IBE is becoming more well
supported as it becomes standardized, notably the IEEE 1363.3 standard for Identity Based Encryption
and IETF draftstandardsRFC 5091, and RFC 5408. [3, 18, 19, 22, 25, 29, 30, 59]
2.8 WHY WASIBE CHOSEN?
I chose to use Identity-Based Encryption in my secure mobile messaging application for many reasons.
Firstand foremost,Idon’tknowof anyotherinstantmessagingscheme thatusesIBEsoit wouldgive me
a chance to develop a proof-of-concept. Also, there has not been much work on Elliptic Curve
CryptographyonmobiledevicessoIwasinterestedtoseehow well ECCwouldperformonmodernmobile
phones. There are also manytechnical considerationsthatmade IBE an attractive choice for my system.
Because encryption is based on users’ identities there is no need to set up and manage a certificate
managementinfrastructure. The lowimplementationoverhead allowsfora systemthatcan be modular
and extensible. This makes it easy to add IBE as a security layer on top of an existing system. Certain
schemes offer short ciphertexts and public parameters which is ideal for messaging systems and for](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-19-320.jpg)


![21
that they believe to be secure. Because there is no central authority in OTR, users are responsible for
authenticating each other. This authentication can happen ‘out-of-band’ by verifying each other’s
fingerprint(the hashof auser’spublickey) inperson,overthe phone,etc.,orbyusingthe secret-sharing
popup window. In this window, the instigating user enters a question or phrase that they are sure only
the other party would know the response to. If the recipient enters the correct response, the users are
authenticated and secure messaging is initiated. In practice, new users tend to have issuesfiguring out
how to use this secret sharing window. A big limitation of this form of authentication is that it doesn’t
allowforthe authenticationof userswhohave nothadany priorcontact. [12, 32, 33]
3.2 Secure Instant Messagingand Presence Protocol (SIMPP)
The Secure Instant Messaging and Presence Protocol (SIMPP) is an XMPP-compliant protocol createdin
2007 by Yang, Kuo,Ahn, and Lee and basedon the open-source jabberdproject. Itisan implementation
of RFC 2778, draftedin2000, whichdefinesstandardfor presence andinstantmessagingservices. SIMPP
is adapted from the Instant Messaging Key Exchange (IMKE) protocol created by Mannan and van
Oorschot to ensure the confidentiality, integrity and authentication of client-server and client-client
communications. SIMPP improves upon RSA-based IMKE by using Elliptic Curve Cryptography to speed
up public-key cryptographic functions. Their main objective was to increase the security of instant
messaging systems by making them more practical and more readily adoptable. They aim to do this by
reducingthe computational overheadimposedonthese systems due tothe security mechanisms.
SIMPP isconfiguredwith twosystemparameters:ellipticcurve E : y2 = x3 + ax + b and base pointG =
(xG, yG) of prime ordern > 2160. Usingthese parameters,the servergeneratesforitself apublic/private
keypair and sharesits publickeywithall usersin the system. This keyis usedby the clientsto generate
theirmaster keys. Their systemhas three phases:registration,client-servercommunication,andclient-
client communication. In the registrationphase,the client submits their ID and public key to the server
(R1). The serverrespondswiththese credentials,alongwitharandomstring, encryptedwiththe master
key (R2). The user responds with the random string signed with their private key, and, if valid, is then
registeredonthe server(R3).
FIGURE 5 - SIMPP PHASE 1: REGISTRATION
The client-server communication phase is the phase where the client authenticates with the server to
loginto the system. The clientauthenticateshimself bygeneratingasymmetricsessionkeyitwishesto](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-22-320.jpg)
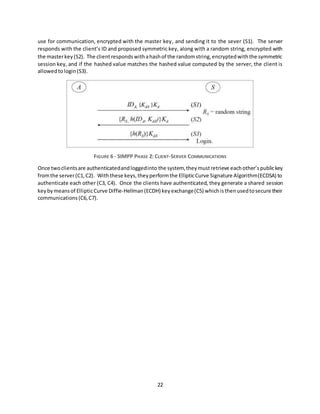
![23
FIGURE 7 - SIMPP PHASE 3: CLIENT-CLIENT COMMUNICATION
FIGURE 8 - SIMPP PROTOCOL: KEY TERMS
The creators of SIMPP chose to use the MIRACL cryptographic SDK as their library of cryptographic
functions. Fromthislibrarytheyuse 128-bit AESfor symmetricencryption,andECCover a prime fieldof
224 and160 bitson the serverandclientsrespectivelyforasymmetricencryption.
The main drawback of this system is that it relies on a Public-Key Infrastructure (PKI) to distribute keys
each time a new pair of clients wish to communicate. This adds unwanted overhead and complexity to
the system. [3]](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-24-320.jpg)
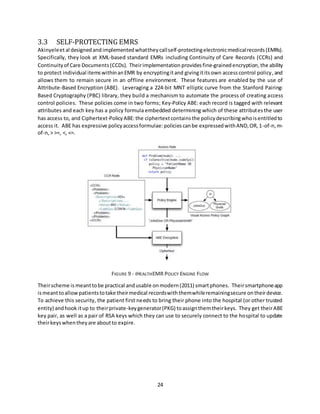
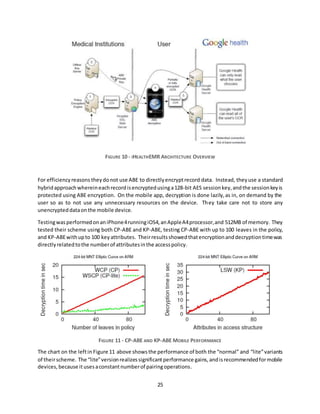
![26
Using an out-of-band key exchange process gives the system additional security, but also makes the
system less practical outside of a scheme where the user needs to physically interact with a central
authority. Their implementation of a secure EMR system is elegant and well executed,and, while their
systemhas acceptable performance on a fourthgenerationiPhone,itwouldlikelyrealize improvements
inuser experience onamodernmobile device. [7]
3.4 JXTA-OVERLAY
JXTA-Overlay is an implementation of a security layer on top of the Java P2P framework JXTA (a.k.a.
juxtapose) by Arnedo-Morenoetal. The JXTA specificationprovidesaset of openprotocolsthat enable
the creationand deploymentof P2P networks,enablingP2Papplicationstodiscoverandobserve peers,
communicate and offer and access resources within the network. JXTA-Overlay is based on JXTA and
enables the creation of Java-based end-user applications. The goal of their security layer is to provide
securitywhile beingtransparenttothe underlyingframework. Theyalsowantedit to be extensibleand
easilyadaptedtodifferentcryptomodules. Withtheirsystem, thiscanbe achievedmostlybyextension
and withlittle modificationtothe original code base.
The major security entities involved in the JXTA-Overlay framework are the SecurityManager and the
CryptoManager. Because theydesignedthe CryptoManagerina modularfashion,itessentiallyactsas a
proxy for any cryptographic module you wish to plug in, potentiallyeven one based on Elliptic Curve
Cryptography. In their implementation, security is provided by TLS utilizing X.509 certificates, JCE
keystores,and128-160 bit sessionidentifiers(SIDs),inadditionto a challenge-response protocol.
FIGURE 12 - JXTA-OVERLAY LOGIN SEQUENCE
The roles in the JXTA network are end-users, clients, peers, brokers, a central database, and
administrators. The framework is divided into 3 layers: the client layer, broker layer, and control layer,
much like a traditional MVCframework. Clientpeersare protectedagainstimpersonationbyextending
the Discoverprimitivesandfunctionswithbrokerauthentication. A secure loginprimitive isprovidedto
protect username and password from eavesdroppers. They also implement a basic method for key
distributionbetweengroupmembers,once theyhave beengrantedaccessto the JXTA-Overlaynetwork
by the broker.](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-27-320.jpg)
![27
InJXTA-Overlay, keydistribution isinvisibletothe end-usersandtheyneednotconcern themselvesabout
how the keydistributionmechanismworks. Thismakesthe systemmore user-friendlyandtherefore its
use and implementation less error-prone. The proposed framework is completely modular and can be
adapted to different scenarios, including different types of credentials or cryptographic modules.
Performance of the system is likely highly dependent upon the type of cryptographic functions used in
the CryptoManagermodule. The onlyreal issue isthat itreliesoncertificatesanda certificate authority
to manage those certificates.[14]
3.5 TEXTSECURE (AXOLOTL)
TextSecure isasecure messagingappforAndroiddevelopedby WhisperSystems,whosegoal istocreate
“simple andeasy-to-use toolsforsecure mobilecommunicationandsecure mobilestorage.” Inaddition
to a private textandchat app, theyalsofeature anapp that allows private calling. WhisperSystems was
acquired by Twitter in late 2011, who very generously made some of the Whisper Systems software
available under an open-source license (GPLv3). This new project is known as “Open Whisper Systems”
and has beenunderactive developmentbythe open-source community. TextSecure hasreceivedpraise
by whistleblowerEdwardSnowden.
TextSecure’sprotocol consistsof several phases: registration,sending/receivinga firstmessage,sending
a follow-up message,and sending a reply. When a new session is created to exchange messages, three
main cryptographic building blocks are applied: a key/secret exchange protocol, a key update and
management protocol (the so-called axolotl ratchet), which updates the encryption and MAC keys for
everyoutgoingmessage,anda stateful authenticatedencryptionscheme. Keyexchange is essentiallya
triple Diffie-Hellman(DH) keyexchange usinglong-termandephemeral secretkeys. Thisisthe onlystep
in the protocol flowthat usesthe long-termkeys. The keymanagementprotocol providesbothforward
secrecy (which roughly means that past sessions remain secure even if the long-term key of a party is
corrupted) and future secrecy (in which a leak of keys to an eavesdropper will be “healed” by the
introductionof newDH ratchetkeys). Messagesare encryptedusingAESincounter mode andsent over
JSON/REST.
For push messaging, TextSecure relies on a central server to relay messages to the intended recipient.
Parties communicate with the central server via REST using HTTPS. The central authority’s certificate is
self-signed, and the certificate of the signing CA is hard-coded in the TextSecure app. Actual message
deliveryisperformedviaGoogle CloudMessaging(GCM),whichbasically actsasa routerformessages.
Version 2 of the TextSecure messaging protocol uses the no header keysvariation of the axolotl ratchet
and protobuf records. The protocol can detect replay,reorder,and deletion of messages. It allowsthe
decryption of out-of-order messages with minimal reduction in forward secrecy. It also does not leak
metadata, such as identities or sequence numbers, in cleartext. The scheme guarantees deniability as
well asthe confidentialityandauthenticityof the exchangedmessages. Everynew messageisencrypted
usinga new key and all messagesare encryptedlocally aswell asintransit.
In additiontoits reliance ona central authority, one issue withTextSecure isthatit onlypartiallyutilizes
its MAC image space. TextSecure uses HMAC-SHA-256 to calculate MACs but does not transmit the
complete output,onlythe first 64 of the 256 bit MAC. NIST recommends a MAC lengthof 80 bitswhen
used for key confirmation. TextSecure is also vulnerable to an attack known as an Unknown Key-Share](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-28-320.jpg)
![28
Attack (UKS). FirstdescribedbyDiffie etal, if such an attack is mountedagainst Pa, thenPa sharesa key
withPb,however, Pb believestheyshare akeywithPe != Pa.
FIGURE 13 - UKS ATTACK ON TEXTSECURE
Frosch etal provide asolutiontothe UKS attack intheirpaper ‘How Secure isTextSecure?’
Another issue with TextSecure is that it requires two parties to initially authenticate by comparing
fingerprintsusinganout-of-bandchannel,forexample,aphonecall oranin-personmeeting. Eventhough
they do make the manual process fairly easy by allowing the two parties to scan Quick Response (QR)
codesoneach other’sphones,it isstill inconvenientandinsome casesimpossible forthe communicating
partiestomeetinperson.[34, 42, 57, 64]
3.6 CRYPTO-BOOK
Modernsocial networkingsitesutilizecross-siteauthenticationprotocolssuchasOAuthandOpenID. One
of the down-sidesof theseprotocolsisthatauser’sonlineactivitycanbe easilytracked,presentingarisk
to online privacy. Toaddressthisissue, JohnMaheswaran,DavidIsaacWolinsky,andBryanFord created
Crypto-Book in2013. The conceptof the projectisto buildaprivacy-preservingcryptographiclayeratop
existing social network identities. It does this via third-party key servers that convert social network
identities into public/private key pairs on demand. This results in unique pseudonyms that are
untraceable backto the owneryetcan resistanonymousabuse.
Crypto-Bookutilizeskeyservers(which couldbe runbythe social networkingsitesorindependently) that
existina cloudtheycall “anytrust”. Usersobtaintheirprivate keybyauthenticatingwitheachof the key
serversviaOAuth(overanSSLconnection). Eachkeyservergeneratesonlyone partof the user’sprivate
key; the user’s client machine (or potentially some trusted proxy) combines these key parts into the
complete private key. Tosupportthis,the creators chose the DSA keyformat because DSA keyssupport
easy key splittingand combining. DSA keys operate in a group G of order p and are of the form Y = gx
mod p, where Y isthe publickeyand xisthe private key. The keysare furtherdividedintoepochs,where
the key server’s master secret is valid only during a given epoch, and gets randomly reinitializedin each
successive epoch. The scheme remainssecure aslongasat leastone of these serversremainshonest.](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-29-320.jpg)
![29
FIGURE 14 - CRYPTO-BOOK'S ANYTRUST ARCHITECTURE
Crypto-Bookemploys RSA-basedringsignaturestoauthenticateanonymouslytothird-partywebsitesand
serviceswithoutrevealing Personally-Identifiable Information(PII)sothatuserscannotbe tracked. A ring
signature proves that one of the “ring members” signed a message but does not reveal which one. To
protect clientsfrombeingtrackedby maliciousservers,clientsare assumedtobe connectingto the key
serversoverananonymitynetworksuchasTor.
FIGURE 15 – CRYPTO-BOOK ANONYMOUS KEY RETRIEVAL
Asa proof-of-concept,they builtanimplementationof theirschemewhichtheydubbedBlackBox. Black
Box allowsuserstosignfilesdeniablyusingringsignatures. A possiblethreatto the Crypto-Bookscheme
involvesthirdpartysitescolluding inanattempttode-anonymizeanduniquelyidentifyusersusingsome
formof cross-site correlationattack. Overall,Crypto-Bookisaveryintriguingproject,withexcellentdata
securityoptionsfromachoice of cryptographicimplementation(RSA,DSA,orevenIBE),andusers’privacy
iswell protectedwiththe combinationof ringsignaturesandananonymitynetwork. [39]](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-30-320.jpg)
![31
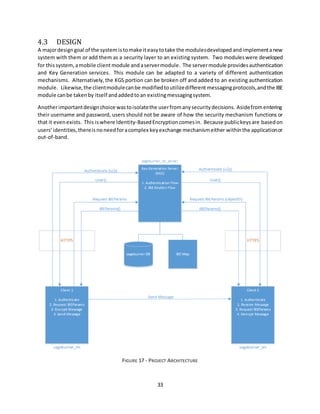
CHAPTER 4 – PROJECT DESIGN AND IMPLEMENTATION
4.1 PROJECT OVERVIEW
The goal of this projectis to developamobile messagingappthat is exceptionallysecure yetsimpleand
intuitive to use. Messages will be protected whensent over the wire as well as at rest, and will not be
persistedonusers’devicesoronthe servers. To be user-friendly,the securitymechanismisdesignedto
be transparent and seamless. I leveraged the Android Bootstrap framework to develop a secure
messaging app for the Android operating system that uses Identity-Based Encryption based on elliptic
curves from the Stanford PBC library. The system will provide encryption to protect the user’s data,
authenticationsothatuserscanbe sure of otherusers’identities,deniabilitysothatanythingauserdoes
cannot be heldagainstthem,and forwardsecrecy so that if a userlosescontrol of theirprivate keys,no
previousconversationiscompromised. The application isintendedto be useful to anyonewhowouldlike
to share their personal, financial, business, and health information with the assurance that it is secure.
[71]
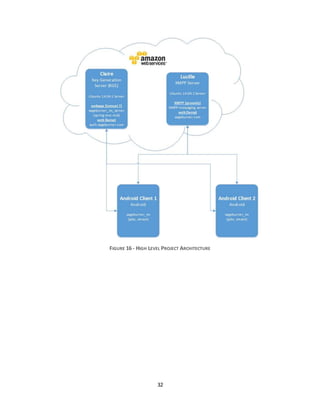
4.2 PROJECTARCHITECTURE
I chose to leverage cloud services to implement the messaging system. Cloud services provide fast
provisioning,reliability,lowmaintenance,andlow costs. I use AmazonWeb Services tohost my project
infrastructure. In particular, I leverage the Amazon Elastic Compute Cloud (EC2) and Route 53 services.
Amazon EC2 runs virtual server instances. One basic server instance can be used for free and other
instancescanbe usedandpaid forbythe hourof runtime. Route 53providesscalableandhighlyavailable
DomainName System(DNS) services.The name (Route 53) is a reference to TCP or UDP port 53, where
DNS serverrequestsare addressed.[72]
The implementationconsistsof twoserversand,fordevelopmentandtesting,twoAndroidsmartphones.
One serveracts as the IBE KeyGenerationServer(KGS) anduserauthenticationserver. The otherserver
providesthe XMPPmessagingservice. The smartphonesrunthe secure messagingclientapplication.
On the KGS serverI am runningthe Ubuntu Linux Serveroperatingsystem (UbuntuServer14.04.01), the
Apache Tomcat Application Server (Tomcat 7), the Apache Web Server (Apache 2.4.7) and the MySQL
database server from the LAMP software package, which stands for Linux-Apache-MySQL-PHP. The
Apache WebServerisconfiguredforHTTPS sothatall authenticationrequeststothe serverare protected.
On the XMPP Serverinstance I am running Ubuntu Linux Server14.04.01 and the ProsodyXMPP Server.
Thisserveralsohoststhe projectwebsite sageburner.com.[73- 78]
The mobile devices used in the system were the Samsung Galaxy Nexus and Samsung Galaxy Note 3
smartphones. The Galaxy Nexus smartphone (2011) runs on Android 4.3 and has a dual-core 1.2 GHz
Cortex-A9processorwith1GB of RAM. The Galaxy Note 3 (2013) runs the Android4.4 operatingsystem
and has a quad-core 2.3 GHz Krait400 processorandhas 3 GB of RAM.](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-32-320.jpg)



![38
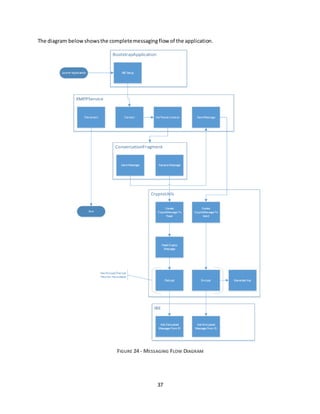
4.4 IMPLEMENTATION DETAILS
There are two maincomponentsinthe implementationof the system;aserverapplicationmodulecalled
the sageburner_im_server and a client application called sageburner_im. The sageburner_im_server
module runs on the Key GenerationServer. This applicationis writtenin Java and is built on top of the
Spring application framework running on Apache Tomcat 7 web application server. Its purpose is to
provide authenticationandIBE KeyGenservicestothe sageburner_imclientapplicationviaRESTful web
services. It utilizesthe JPBCand BouncyCastle librariesforencryption. Thismodule performsthe Setup
and KeyGenstepsfromthe IBEprotocol. [79]
The sageburner_im module runs on the users’ mobile devices. This module is also written in Java and
built on the Android Bootstrap application framework. This framework was chosen because it is well
supportedbythe Androiddevelopmentcommunityanditisdevelopedusingindustrystandardpractices
and proven design patterns. Along with user-interface templates, the framework comes with
authenticationandRESTservice componentsout-of-the-box. Thismodule providesthe securemessaging
clientforthe mobiledevices. ItwascompiledforAndroidAPI19(Android4.4KitKat) andutilizesthe JPBC
andBouncyCastle librariesforencryptionaswell asthe ‘asmack’XMPPclientlibraryforinstantmessaging
and presence services. Thismoduleperformsthe EncyptandDecryptstepsfromthe IBE protocol.
In the Key Generation Server module, authentication is handled by the LoginController. The controller
calls the LoginService, which fetches the user and validates the users’ passwords. To get the user
information,itreliesonthe UserDaoclassto retrieve the user informationfrom the database. The users’
passwords are validated with the help of the CryptoService, which compares the hash of the received
passwordto the hashedpasswordstoredinthe database.
FIGURE 25 - AUTHENTICATION SEQUENCE DIAGRAM](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-39-320.jpg)




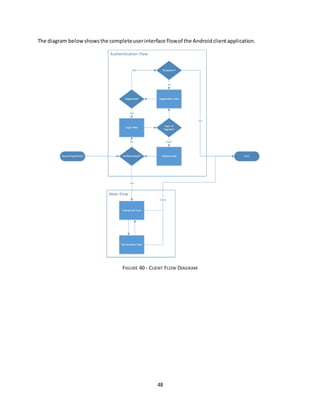

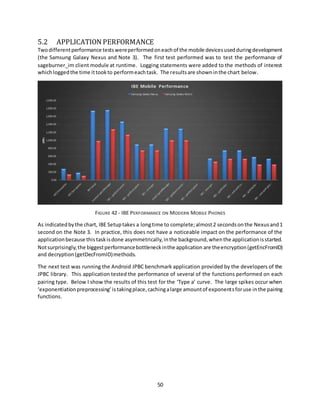
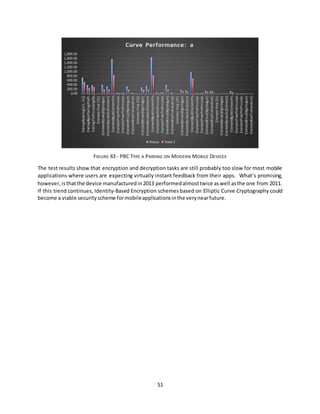


![54
REFERENCES
[1] A Secure Instant Messaging System. http://students.mimuw.edu.pl/SR/prace-mgr/wrzesinska/thesis6.html
[2] Masao Tanabe and Masaki Aida. 2008. Secure communicationmethodinmobile wireless networks. InProceedings o f
the 1st international conference on MOBILe Wireless MiddleWARE, OperatingSystems, andApplications
(MOBILWARE '08). ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering),
ICST, Brussels, Belgium, Belgium, Article 17, 6 pages.
[3] Chung-Huang Yang, Tzong-Yih Kuo, TaeNam Ahn, Chia-Pei Lee. 2007. DesignandImplementation ofa Secure Instant
Messaging Service basedonElliptic-Curve Cryptography. http://security.nknu.edu.tw/publications/200801JOC.pdf
[4] Chung-Huang Yang, Tzong-Yih Kuo. 2007. The DesignandImplementation ofa Secure Instant Messaging Key
Exchange Protocol. http://www.kc.org.tw/fleget/FileDownLoad.aspx?CDE=149
[5] James Walkerdine, Peter Phillips, andSimonLock. 2008. Architecting secure mobile P2Psystems. InProceedings of
the 1st international workshop onSoftware architectures andmobility(SAM'08). ACM, New York, NY, USA, 9-14.
DOI=10.1145/1370888.1370892 http://doi.acm.org/10.1145/1370888.1370892
[6] Joris Claessens, Bart Preneel, andJoos Vandewalle. 2003. (How)canmobileagents dosecure electronic transactions
on untrustedhosts? A surveyof the securityissues andthe current solutions. ACMTrans. Internet Technol. 3, 1
(February2003), 28-48. DOI=10.1145/643477.643479 http://doi.acm.org/10.1145/643477.643479
[7] JosephA. Akinyele, MatthewW. Pagano, Matthew D. Green, Christoph U. Lehmann, ZacharyN.J. Peterson, andAviel
D. Rubin. 2011. Securing electronic medical records using attribute-based encryptiononmobile devices. In
Proceedings of the 1st ACM workshoponSecurityandprivacyin smartphones and mobile devices (SPSM'11). ACM,
New York, NY, USA, 75-86. DOI=10.1145/2046614.2046628 http://doi.acm.org/10.1145/2046614.2046628
[8] ViganRaça, Betim Çiço, andMajlinda Fetaji. 2012. Management, communications andsecuritypolicyin mobile
database systems. InProceedings ofthe FifthBalkan Conference inInformatics (BCI '12). ACM, New York, NY, USA,
118-123. DOI=10.1145/2371316.2371339 http://doi.acm.org/10.1145/2371316.2371339
[9] Sven Heiberg, Peeter Laud, Sigurðr Másson, andClaus PoppLarsen. 2011. Secure mobile accessto homecare patients'
data. InProceedings of the 5th International Conference onTheoryandPractice of Electronic Governance (ICEGOV
'11), Elsa Estevez and Marijn Janssen(Eds.). ACM, New York, NY, USA, 363-364. DOI=10.1145/2072069.2072143
http://doi.acm.org/10.1145/2072069.2072143
[10] AndroidProgramming:The Big Nerd RanchGuide (BigNerdRanchGuides) Series:Big NerdRanchGuides. Paperback:
580 pages. Publisher:BigNerdRanch Guides;1 edition(April 7, 2013). ISBN-10:0321804333. ISBN-13:978-
0321804334.
[11] Abhijit Bose andKang G. Shin. 2006. Proactive securityfor mobile messaging networks. InProceedings of the 5th ACM
workshopon Wireless security(WiSe '06). ACM, New York, NY, USA, 95-104. DOI=10.1145/1161289.1161307
http://doi.acm.org/10.1145/1161289.1161307
[12] Nikita Borisov, IanGoldberg, andEric Brewer. 2004. Off-the-record communication, or, whynot to use PGP. In
Proceedings of the 2004 ACMworkshopon Privacyinthe electronic society(WPES '04). ACM, New York, NY, USA, 77-
84. DOI=10.1145/1029179.1029200 http://doi.acm.org/10.1145/1029179.1029200
[13] Benoît Libert, Jean-Jacques Quisquater, andMoti Yung. 2007. Forward-secure signatures in untrustedupdate
environments:efficient andgeneric constructions. In Proceedings of the 14th ACMconference onComputer and
communications security(CCS '07). ACM, New York, NY, USA, 266-275. DOI=10.1145/1315245.1315279
http://doi.acm.org/10.1145/1315245.1315279
[14] Joan Arnedo-Moreno, Keita Matsuo, LeonardBarolli, andFatos Xhafa. 2009. Securing a Java P2Pframework:the JXTA-
overlaycase. InProceedings of the 11th InternationalConference on Information Integration andWeb-based](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-55-320.jpg)
![55
Applications & Services (iiWAS'09). ACM, New York, NY, USA, 160-167. DOI=10.1145/1806338.1806373
http://doi.acm.org/10.1145/1806338.1806373
[15] Minzhe Guo, Prabir Bhattacharya, Ming Yang, Kai Qian, andLi Yang. 2013. Learning mobile securitywith android
securitylabware. In Proceeding of the 44th ACMtechnical symposiumon Computer science education (SIGCSE '13).
ACM, New York, NY, USA, 675-680. DOI=10.1145/2445196.2445394 http://doi.acm.org/10.1145/2445196.2445394
[16] Xinlei Wang, JianqingZhang, Eve Schooler andMihaela Ion,“Performance Evaluationof Attribute-BasedEncryption:
Toward Data Privacyinthe IoT,” IEEE InternationalConference on Communications (ICC), 2014.
http://csiflabs.cs.ucdavis.edu/~xlwang/public/icc_2014_wang.pdf
[17] S. Roy, M. Chuah, "Secure Data Retrieval Based onCiphertext PolicyAttribute-BasedEncryption (CP-ABE)Systemfor
the DTNs", LehighCSE TechnicalReport, May, 2009 http://www.cse.lehigh.edu/~chuah/publications/cpabe-
report09.pdf
[18] InternationalJournal ofNetworkSecurityVolume: 15, No:4 (July1, 2013) A Surveyon Attribute-basedEncryption
Schemes of Access Control inCloud Environments Cheng-Chi Lee, Pei-Shan Chung, andMin-ShiangHwang, Vol. 15,
No. 4, 2013, pp. 231-240 http://ijns.femto.com.tw/contents/ijns-v15-n4/ijns-2013-v15-n4-p231-240.pdf
[19] Fourth IACR Theoryof CryptographyConference TCC2007 February21-24 2007, KNAW Trippenhuis Amsterdam, The
Netherlands. Multi-AuthorityAttribute-BasedEncryption. Melissa Chase
http://cs.brown.edu/~mchase/papers/multiabe.pdf
[20] The Java Pairing-BasedCryptographyLibrary(JPBC) @inproceedings{ISCC:DecIov11,author = {Angelo{De Caro} and
VincenzoIovino},title = {jPBC:Java pairing basedcryptography},year = {2011},pages = {850-855},booktitle =
{Proceedings of the 16th IEEE Symposium onComputers and Communications, ISCC2011},address = {Kerkyra, Corfu,
Greece, June 28 - July1}publisher = {IEEE},url = {url{http://gas.dia.unisa.it/projects/jpbc/}},}
[21] Brent Waters. 2009. Dual System Encryption:RealizingFullySecure IBE andHIBE under Simple Assumptions. In
Proceedings of the 29th AnnualInternational CryptologyConference on Advances in Cryptology(CRYPTO '09), Shai
Halevi (Ed.). Springer-Verlag, Berlin, Heidelberg, 619-636. DOI=10.1007/978-3-642-03356-8_36
http://dx.doi.org/10.1007/978-3-642-03356-8_36
[22] JoonsangBaek and JianyingZhou. 2011. Compact identity-basedencryptionwithout strongsymmetric cipher. In
Proceedings of the 6th ACMSymposium onInformation, Computer andCommunications Security(ASIACCS '11). ACM,
New York, NY, USA, 61-70. DOI=10.1145/1966913.1966923 http://doi.acm.org/10.1145/1966913.1966923
[23] Song Luo, JianbinHu, and ZhongChen. 2010. New constructionof identity-basedproxyre-encryption. In Proceedings
of the tenthannual ACMworkshopon Digital rights management (DRM'10). ACM, New York, NY, USA, 47-50.
DOI=10.1145/1866870.1866880 http://doi.acm.org/10.1145/1866870.1866880
[24] Sherman S.M. Chow, YevgeniyDodis, Yannis Rouselakis, andBrent Waters. 2010. Practicalleakage-resilient identity-
basedencryptionfrom simple assumptions. InProceedings of the 17th ACMconference onComputer and
communications security(CCS '10). ACM, New York, NY, USA, 152-161. DOI=10.1145/1866307.1866325
http://doi.acm.org/10.1145/1866307.1866325
[25] B. S. Adiga, P. Balamuralidhar, M. A. Rajan, Ravishankara Shastry, andV. L. Shivraj. 2012. An identitybasedencryption
using elliptic curve cryptographyfor secure M2Mcommunication. InProceedings ofthe First InternationalConference
on Securityof Internet of Things (SecurIT '12). ACM, New York, NY, USA, 68-74. DOI=10.1145/2490428.2490438
http://doi.acm.org/10.1145/2490428.2490438
[26] Keita Emura, Akira Kanaoka, Satoshi Ohta, andTakeshi Takahashi. 2014. Buildingsecure andanonymous
communicationchannel:formal modelandits prototype implementation. InProceedings ofthe 29th Annual ACM
Symposium onAppliedComputing(SAC'14). ACM, New York, NY, USA, 1641-1648. DOI=10.1145/2554850.2554879
http://doi.acm.org/10.1145/2554850.2554879](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-56-320.jpg)
![56
[27] Vipul Goyal, Steve Lu, Amit Sahai, andBrent Waters. 2008. Black-box accountable authorityidentity-based
encryption. In Proceedings of the 15th ACMconference onComputer andcommunications security(CCS '08). ACM,
New York, NY, USA, 427-436. DOI=10.1145/1455770.1455824 http://doi.acm.org/10.1145/1455770.1455824
[28] Alexandra Boldyreva, Vipul Goyal, andVirendra Kumar. 2008. Identity-basedencryptionwithefficient revocation. In
Proceedings of the 15th ACMconference on Computer and communications security(CCS '08). ACM, New York, NY,
USA, 417-426. DOI=10.1145/1455770.1455823 http://doi.acm.org/10.1145/1455770.1455823
[29] Al-Riyami Certificateless Public KeyCryptography
[30] Byoungcheon Lee, Colin Boyd, Ed Dawson, KwangjoKim, JeongmoYang, andSeungjae Yoo. 2004. Secure keyissuing
in ID-basedcryptography. In Proceedings of the secondworkshoponAustralasianinformation security, Data Mining
and Web Intelligence, andSoftware Internationalisation - Volume 32 (ACSW Frontiers '04), J. Hogan, P. Montague, M.
Purvis, and C. Steketee (Eds.), Vol. 32. AustralianComputer Society, Inc., Darlinghurst, Australia, Australia, 69-74.
[31] AngeloDe Caro, VincenzoIovino, Giuseppe Persiano. FullySecure Anonymous HIBEandSecret-KeyAnonymous HIBE
with Short Ciphertexts. CryptologyePrint Archive, Report 2010/197, 2010. http://eprint.iacr.org/.
[32] Off-the-RecordMessaging Protocol version3. 2014. https://otr.cypherpunks.ca/Protocol-v3-4.0.0.html
[33] Ryan Stedman, Kayo Yoshida, andIanGoldberg. 2008. A user studyof off-the-record messaging. InProceedings of the
4th symposium onUsable privacyandsecurity(SOUPS'08). ACM, New York, NY, USA, 95-104.
DOI=10.1145/1408664.1408678 http://doi.acm.org/10.1145/1408664.1408678
[34] Matt Green. Matt Green:A Few Thoughts onCryptographic Engineering. 2014.
http://blog.cryptographyengineering.com/2014/08/whats-matter-with-pgp.html
[35] Vinnie Moscaritolo, GaryBelvin, Phil Zimmerman. Silent Circle Instant Messaging Protocol. Protocol Specifications.
Silent Circle Engineering. December 5, 2012. Version1.0.
[36] Neal Koblitz andAlfred Menezes. 2005. Pairing-Based cryptographyat high securitylevels. InProceedings of the 10th
international conference onCryptographyandCoding (IMA'05), NigelP. Smart (Ed.). Springer-Verlag, Berlin,
Heidelberg, 13-36. DOI=10.1007/11586821_2 http://dx.doi.org/10.1007/11586821_2
[37] B. Lynn, On the implementation of pairing-based cryptosystems. PhD thesis, StanfordUniversity, 2007.
[38] M. Ion, Securityof Publish/Subscribe Systems. PhD thesis, Universityof Trento, 2013. http://eprints-
phd.biblio.unitn.it/993/
[39] John Maheswaran, DavidIsaac Wolinsky, and Bryan Ford. 2013. Crypto-Book:an architecture for privacypreserving
online identities. In Proceedings of the Twelfth ACMWorkshoponHot Topics inNetworks (HotNets-XII). ACM, New
York, NY, USA, , Article 14 , 7 pages. DOI=10.1145/2535771.2535798 http://doi.acm.org/10.1145/2535771.2535798
[40] https://www.eff.org/secure-messaging-scorecard (last accessed February, 2015)
[41] http://www.entrepreneur.com/article/230335 (last accessed February, 2015)
[42] https://github.com/trevp/axolotl/wiki (last accessed February, 2015)
[43] GlennGreenwald. The topsecret rulesthat allow NSA to use US data without a warrant. June 20, 2013 18:59 EDT.
http://www.theguardian.com/world/2013/jun/20/fisa-court-nsa-without-warrant (last accessedFebruary, 2015)
[44] Stephanie Mlot. Only6 MessagingApps Are TrulySecure. November 5, 2014 11:25AM EST. pcmag.com
http://www.pcmag.com/article2/0,2817,2471658,00.asp (last accessed February, 2015)
[45] http://en.wikipedia.org/wiki/WhatsApp#Security (last accessedFebruary, 2015)
[46] https://support.google.com/a/answer/6046115?hl=en (last accessedFebruary, 2015)
[47] http://en.wikipedia.org/wiki/Google_Hangouts#Security (last accessedFebruary, 2015)](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-57-320.jpg)
![57
[48] http://www.reuters.com/article/2014/10/14/us-snapchat-future-security-idUSKCN0I32UJ20141014 (last accessed
February, 2015)
[49] https://www.snapchat.com/privacy (last accessedFebruary, 2015)
[50] http://en.wikipedia.org/wiki/Snapchat#Secure_messaging_scorecard (last accessed February, 2015)
[51] https://www.pidgin.im/about/ (last accessedFebruary, 2015)
[52] https://otr.cypherpunks.ca/index.php#docs (last accessedFebruary, 2015)
[53] https://www.aim.com/faq (last accessedFebruary, 2015)
[54] AOL Instant Messenger :Wikipedia http://en.wikipedia.org/wiki/AOL_Instant_Messenger#Security (last accessed
February, 2015)
[55] Skype Security- Encryption http://www.skype.com/en/security/#encryption (last accessedFebruary, 2015)
[56] Skype Has A SecurityProblem With LeakingChats :Forbes.com
http://www.forbes.com/sites/ianmorris/2014/08/14/skype-has-a-security-problem-with-leaking-chats/ (last accessed
February, 2015)
[57] TextSecure - ProtocolV2 :github.comhttps://github.com/WhisperSystems/TextSecure/wiki/ProtocolV2 (last accessed
February, 2015)
[58] http://www.voltage.com/company/awards-recognition/(last accessedFebruary, 2015)
[59] JoonsangBaek, JanNewmarch, Reihaneh Safavi-Naini, andWillySusilo. A Surveyof Identity-BasedCryptography
www.jan.newmarch.name/publications/auug_id_survey.pdf
[60] Carl Youngblood. An Introductionto Identity-basedCryptography. March 2005.
https://courses.cs.washington.edu/courses/csep590/06wi/finalprojects/youngblood_csep590tu_final_paper.pdf
[61] Google Privacy& Terms. https://www.google.com/intl/en/policies/privacy/ (last accessedFebruary, 2015)
[62] Yahoo PrivacyCenter. https://info.yahoo.com/privacy/us/yahoo/details.html (last accessedFebruary, 2015)
[63] The Pairing-BasedCryptographyLibrary. https://crypto.stanford.edu/pbc/(last accessedSeptember, 2014)
[64] TilmanFrosch, Christian Mainka, Christoph Bader, FlorianBergsma, Jörg Schwenk, and ThorstenHolz. 2014. How
Secure is TextSecure? Horst Görtz Institute for IT Security, Ruhr UniversityBochum.
https://eprint.iacr.org/2014/904.pdf
[65] export.gov/safeharbor (last accessedFebruary, 2015)
[66] eff.org (last accessedFebruary, 2015)
[67] otr.cypherpunks.ca (last accessed February, 2015)
[68] whatsapp.com (last accessed February, 2015)
[69] google.com/hangouts/(last accessedFebruary, 2015)
[70] snapchat.com(last accessedFebruary, 2015)
[71] androidbootstrap.com (last accessed February, 2015)
[72] aws.amazon.com (last accessedFebruary, 2015)
[73] www.ubuntu.com(last accessedFebruary, 2015)
[74] http://tomcat.apache.org/ (last accessedFebruary, 2015)
[75] http://httpd.apache.org/(last accessedFebruary, 2015)
[76] http://dev.mysql.com/(last accessedFebruary, 2015)
[77] prosody.im (last accessedFebruary, 2015)
[78] http://sageburner.com (last accessedFebruary, 2015)
[79] spring.io (last accessedFebruary, 2015)](https://image.slidesharecdn.com/e486111b-a840-4aad-aa87-084ba8d17113-150426193001-conversion-gate02/85/Ryan_Holt_MS_Thesis_Project-58-320.jpg)