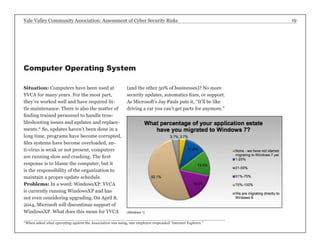
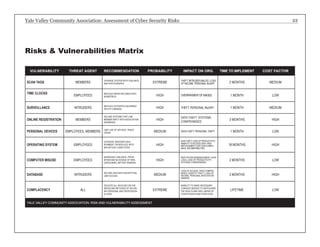
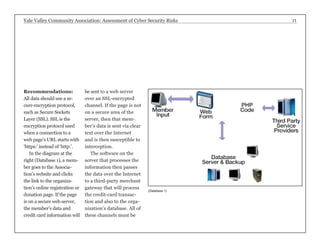
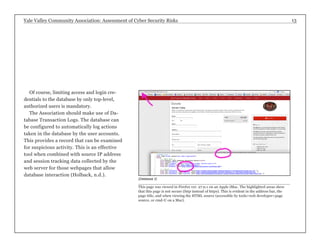
The report assesses the cyber security risks facing the Yale Valley Community Association (YVCA), a health and fitness organization with about 4,000 members. It identifies vulnerabilities in member access, employee time tracking, facility surveillance, online registration, and personal device usage, providing specific recommendations for improving security measures. The goal is to protect sensitive member data and ensure a secure environment amidst increasing threats of data breaches and identity theft.








![Yale Valley Community Association: Assessment of Cyber Security Risks 9
Re: [CVE-REQUEST] Foscam <= 11.37.2.48 path traversal vulnerability
From: Frederic BASSE (basse.fredericgmail.com)
Date: Wed Mar 13 2013 - 10:01:47 CDT
Messages sorted by: [ date ] [ thread ] [ subject ] [ author ]
CVE Assigned: CVE-2013-2560.
2013/3/2 Frederic BASSE <basse.fredericgmail.com>:
> [CVE-REQUEST] Foscam <= 11.37.2.48 path traversal vulnerability
> _______________________________________________________________________
> Summary:
> Foscam firmware <= 11.37.2.48 is prone to a path traversal
> vulnerability in the embedded web interface.
>
> The unauthenticated attacker can access to the entire filesystem and
> steal web & wifi credentials.
> _______________________________________________________________________
> Details:
>
> GET //../proc/kcore HTTP/1.0
>
>
> ____________________________________________________________________
> CVSS Version 2 Metrics:
> Access Vector: Network exploitable
> Access Complexity: Low
> Authentication: Not required to exploit
> Confidentiality Impact: Complete
> Availability Impact: Complete
> _______________________________________________________________________
> Disclosure Timeline:
> 2013-01-18 Vendor fixed the issue in fw 11.37.2.49; no security notice
> 2013-02-21 Vulnerability found
> 2013-03-01 Public advisory
> _______________________________________________________________________
> Solution:
> A new firmware is available on vendor’s site:
> http://www.foscam.com/down3.aspx
> _______________________________________________________________________
> References:
> http://code.google.com/p/bflt-utils/
> http://wiki.openipcam.com/
> _______________________________________________________________________
> Arnaud Calmejane - Frederic Basse
(Camera 2)
be hacked with the username “admin” and
no password. They further state that 99% of
the Foscam cameras noted above, were not
patched after the firmware update was re-leased
(Smith, 2013).
Researchers have found a way to exploit a
vulnerability in the camera’s Web interface
that can allow attackers to get a “snapshot”
of the camera’s memory.
This memory snapshot would contain the
admin username and password in clear text
and other information such as Wi-Fi cre-dentials
or details about devices on the local
network. (Constantin, 2013).](https://image.slidesharecdn.com/riskassessmentjeffmacharyas-140914144704-phpapp01/85/Risk-Assessment-Cybersecurity-Project-at-Utica-College-9-320.jpg)



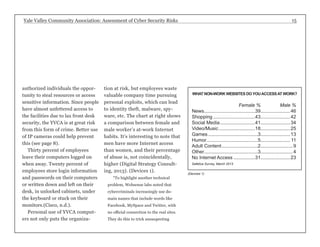

![Yale Valley Community Association: Assessment of Cyber Security Risks 17
Current Standards on Passwords
Example • SANS Institute • sans.org
Strong passwords
have the following characteristics:
• Contain at least three of the five following character
classes:
• Lower case characters
• Upper case characters
• Numbers
• Punctuation
• “Special” characters (e.g. @#$%^&*()_+|~-=`{}
[]:”;’<>/ etc)
• Contain at least fifteen alphanumeric characters.
Weak passwords
have the following characteristics:
• The password contains less than fifteen characters
• The password is a word found in a dictionary (En-glish
or foreign)
• The password is a common usage word such as:
• Names of family, pets, friends, co-workers, fantasy
characters, etc.
• Computer terms and names, commands, sites,
companies, hardware, software.
• The words “<Company Name>”, “<city>”, “<city,
abbrev.>” or any derivation.
• Birthdays and other personal information such as
addresses and phone numbers.
• Word or number patterns like aaabbb, qwerty, zyx-wvuts,
123321, etc.
• Any of the above spelled backwards.
• Any of the above preceded or followed by a digit
(e.g., secret1, 1secret)
(Devices 2)
(Devices 3)](https://image.slidesharecdn.com/riskassessmentjeffmacharyas-140914144704-phpapp01/85/Risk-Assessment-Cybersecurity-Project-at-Utica-College-17-320.jpg)