Embed presentation
Download to read offline









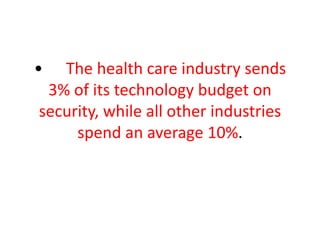

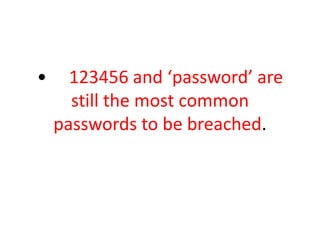




The document summarizes key points from a symposium on rethinking compliance. Some memorable quotes from speakers include that on average 205 days pass before a data security breach is discovered, that staff training should focus more on teaching people to rethink rather than just teaching the law, and that encryption alone is not enough to ensure security and that additional safeguards are needed. The document also lists common topics discussed at the symposium like information privacy, security risk analysis, training, and breach response.














