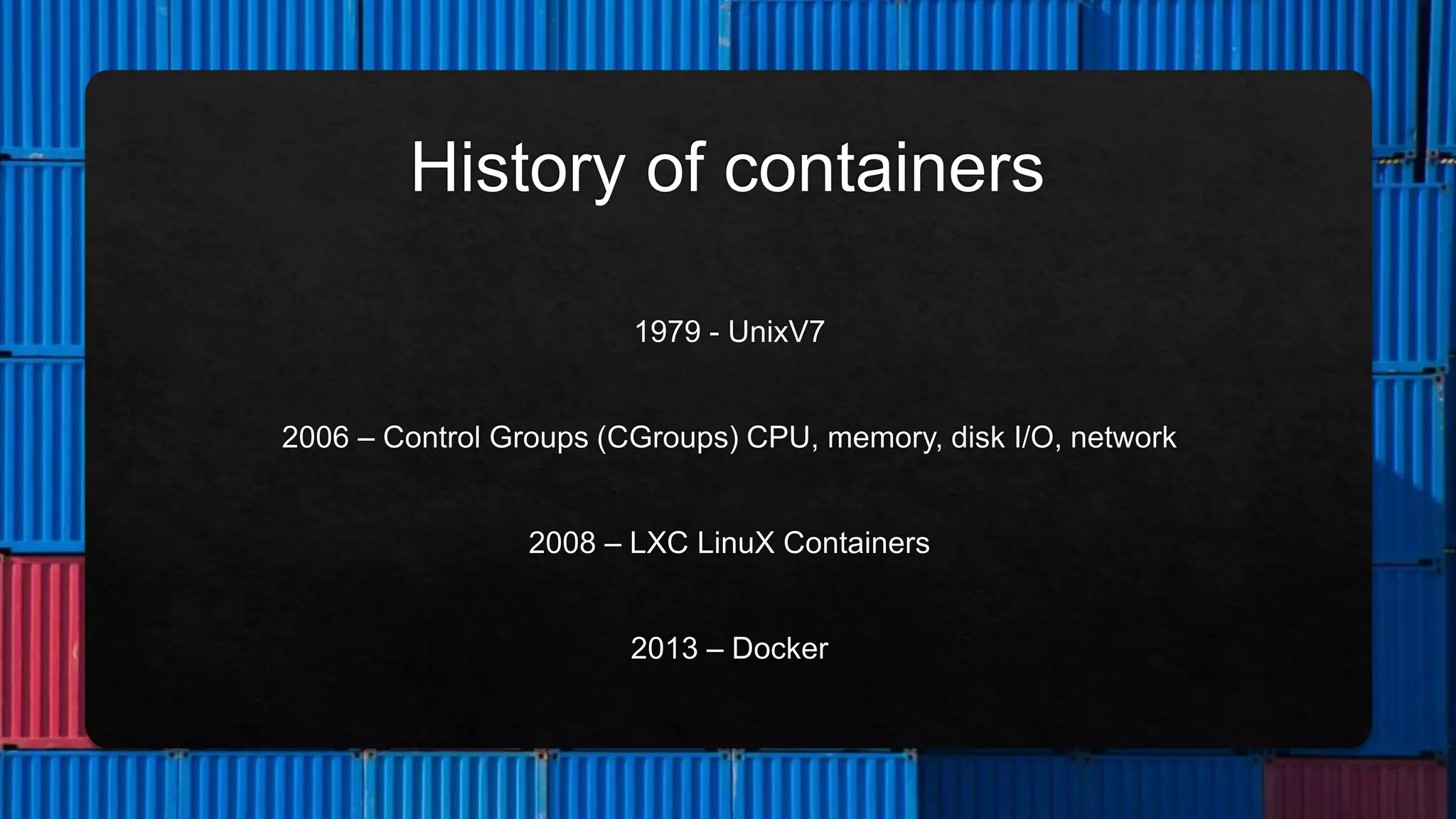
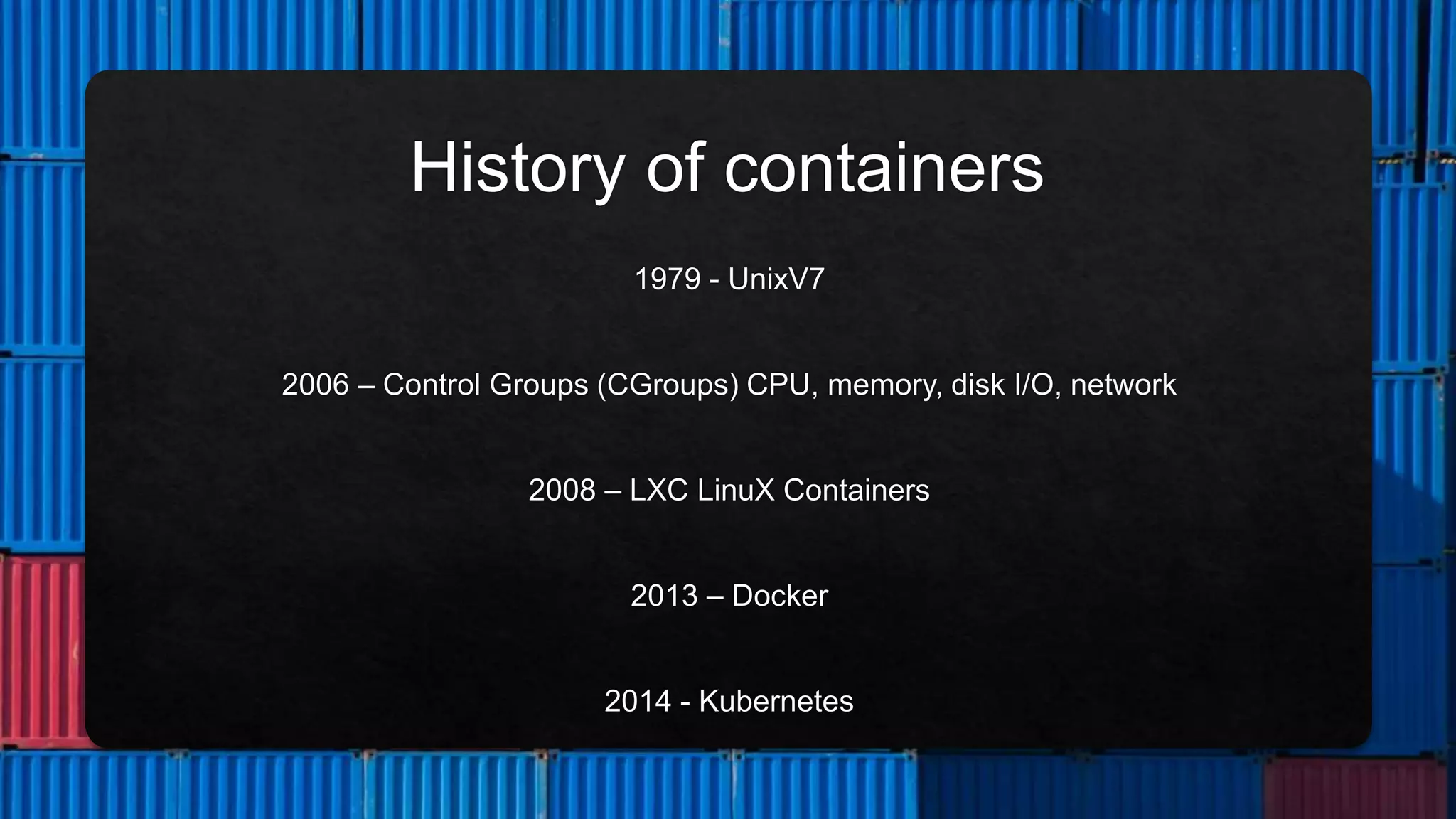
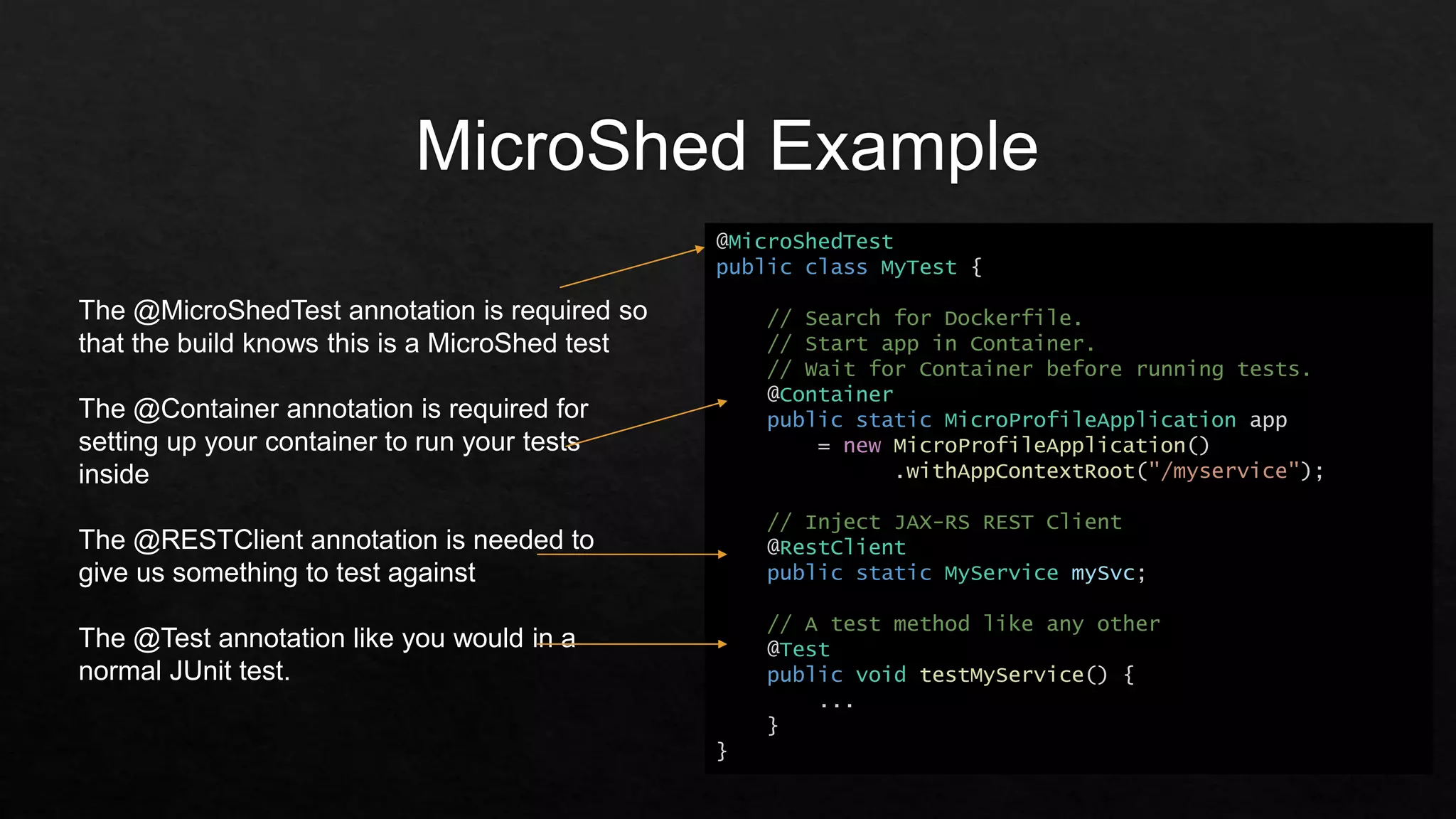
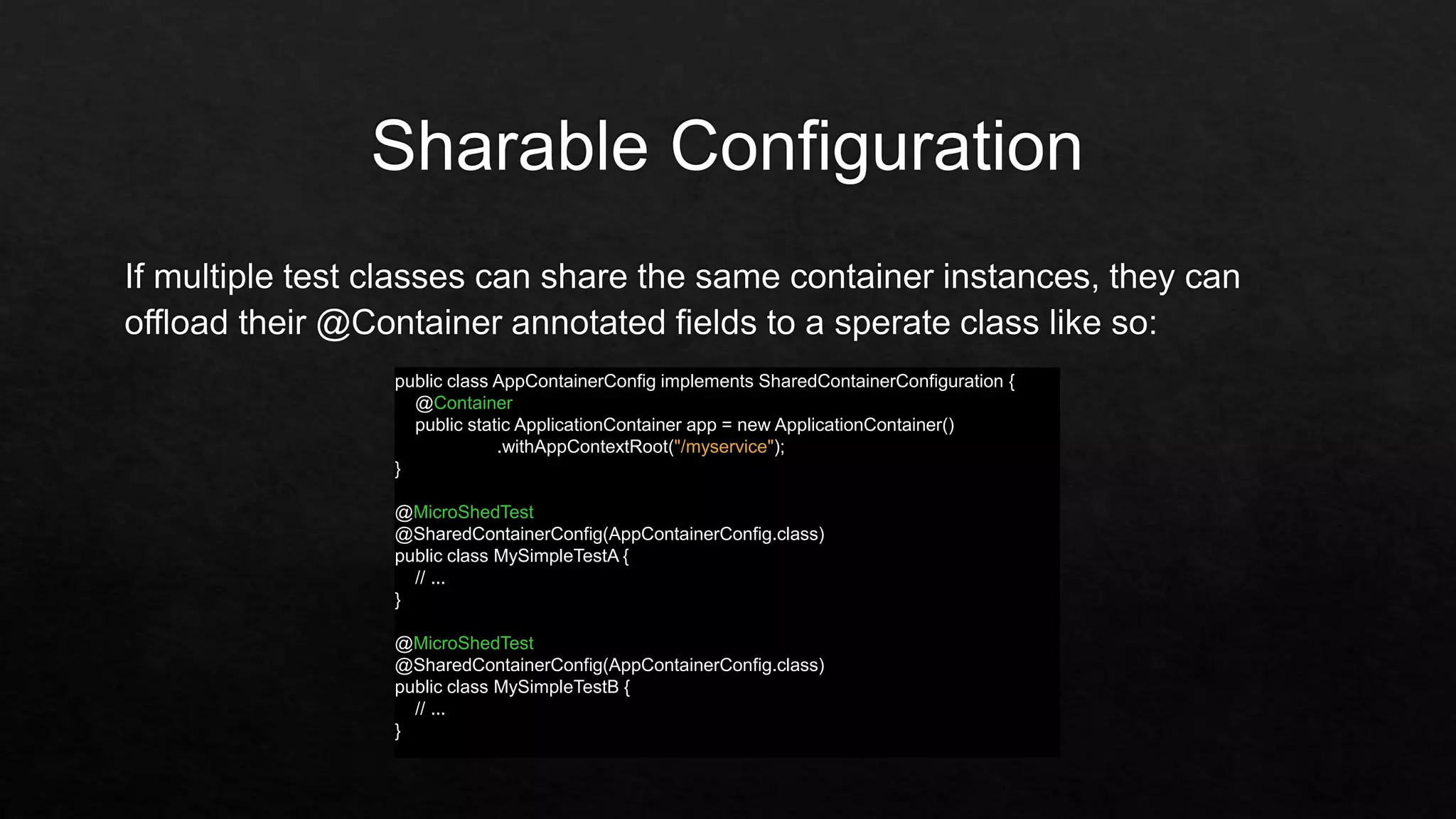
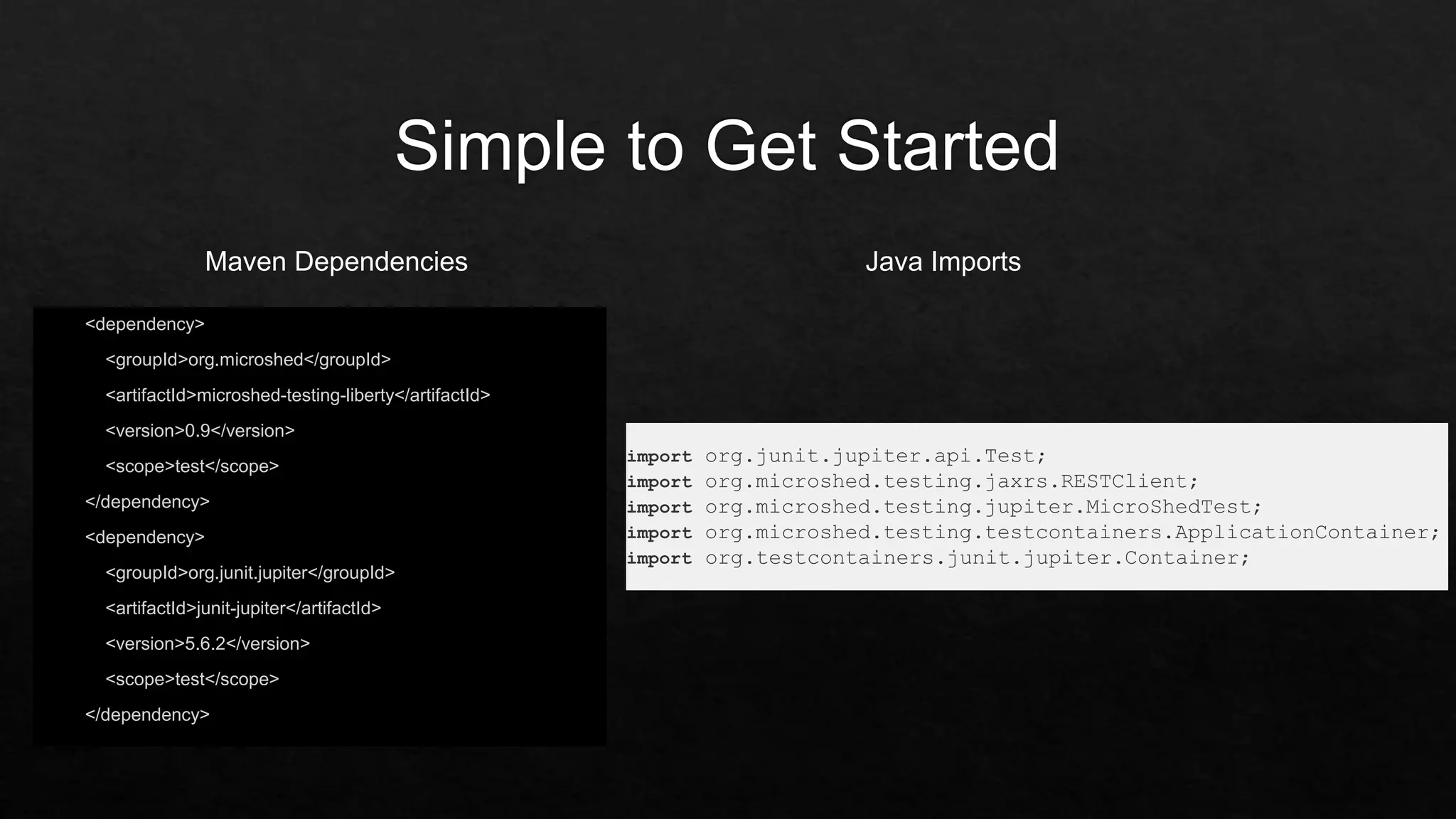
The document outlines the setup and structure for unit testing using the Microshed Testing framework with JUnit in a Docker container environment. It describes the necessary annotations, such as @microshedtest, @container, and @restclient, that facilitate the testing process. Additionally, it includes the required Maven dependencies and Java imports for proper configuration.