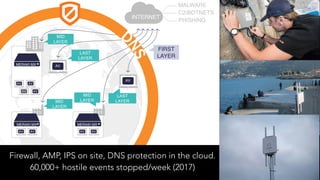
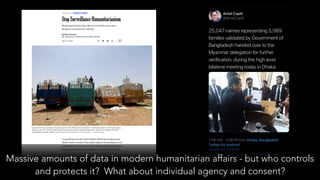
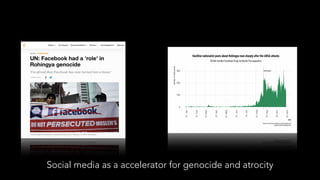
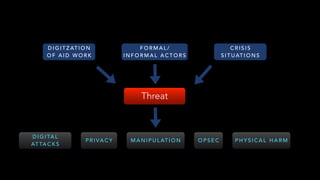
The document discusses the evolution of refugee connectivity and the importance of cybersecurity for vulnerable populations in crisis situations. It highlights the historical deployment of hastily formed networks in response to disasters and the increasing significance of communication technologies for refugees, particularly during the 2015 European migration crisis. It emphasizes the need for digital dignity in humanitarian aid and the protection of personal data while addressing cybersecurity threats faced by humanitarian agencies.






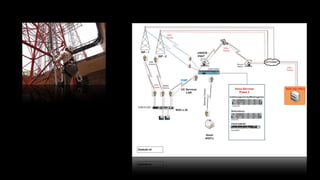











![“The ongoing threat [to humanitarian operations related to Syria] is
advanced, persistent, and unlike anything most NetHope NGO members
have dealt with to date.”
(Bharania, 2015)](https://image.slidesharecdn.com/refugeesconnectivitydignity-190823181656/85/Refugees-connectivity-dignity-21-320.jpg)