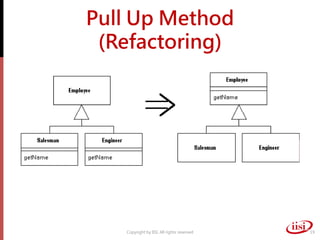
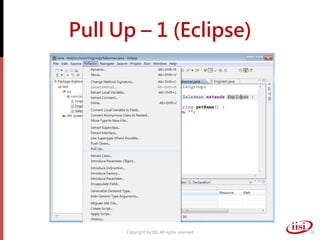
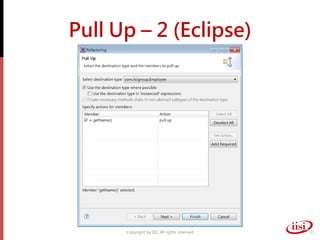
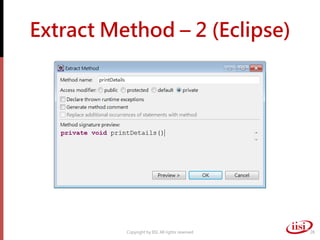
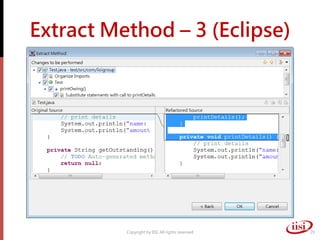
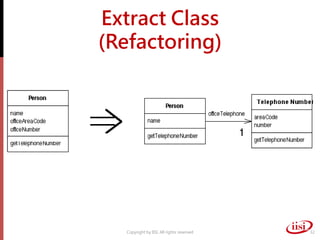
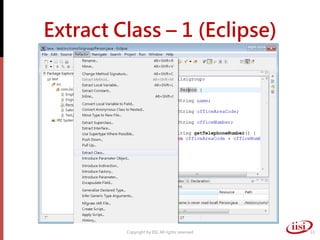
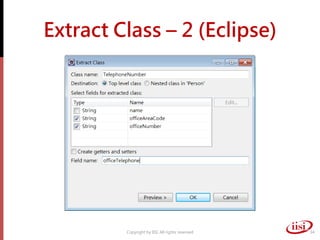
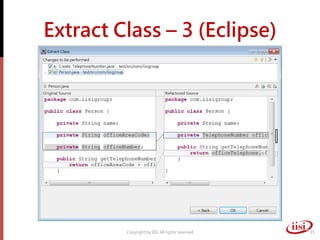
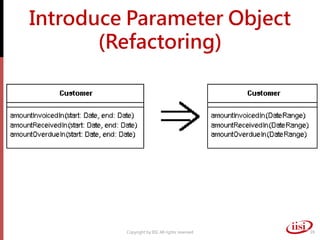
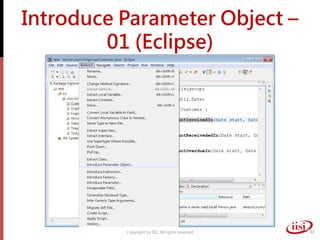
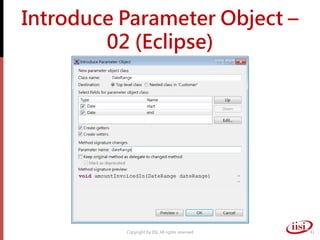
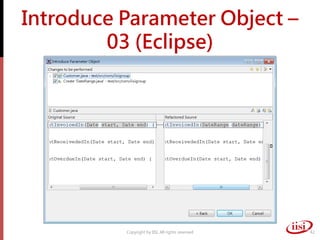
The document discusses refactoring and improving existing code. It describes how the Eclipse IDE has been refactored and improved over multiple versions from 1.0 to 3.7. It also discusses common code smells like duplicated code, long methods, large classes, and long parameter lists that indicate needs for refactoring. Various refactoring techniques are presented, such as extracting methods, extracting classes, replacing parameters with method calls, and introducing parameter objects. The importance of unit testing during refactoring is also emphasized.