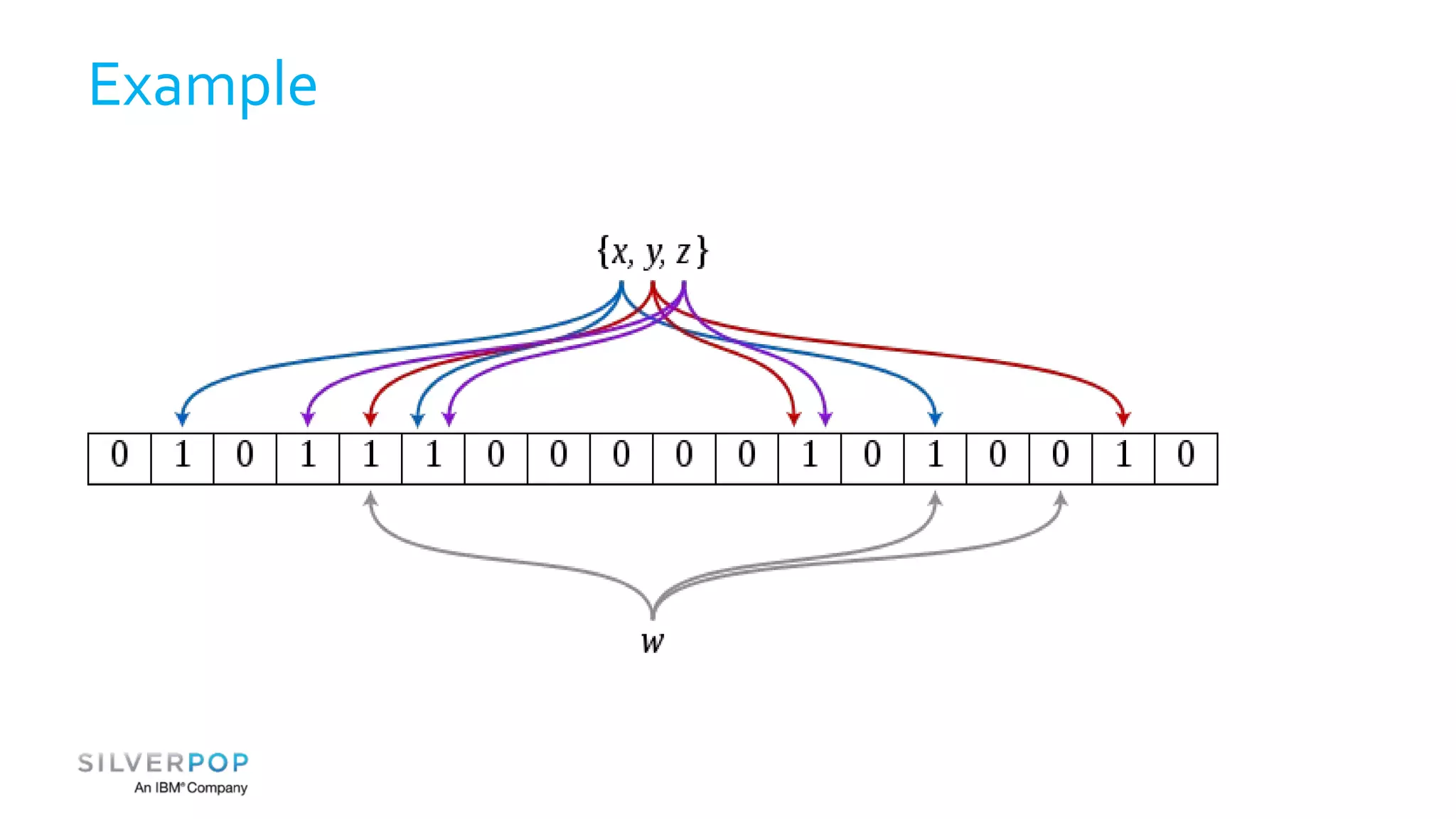
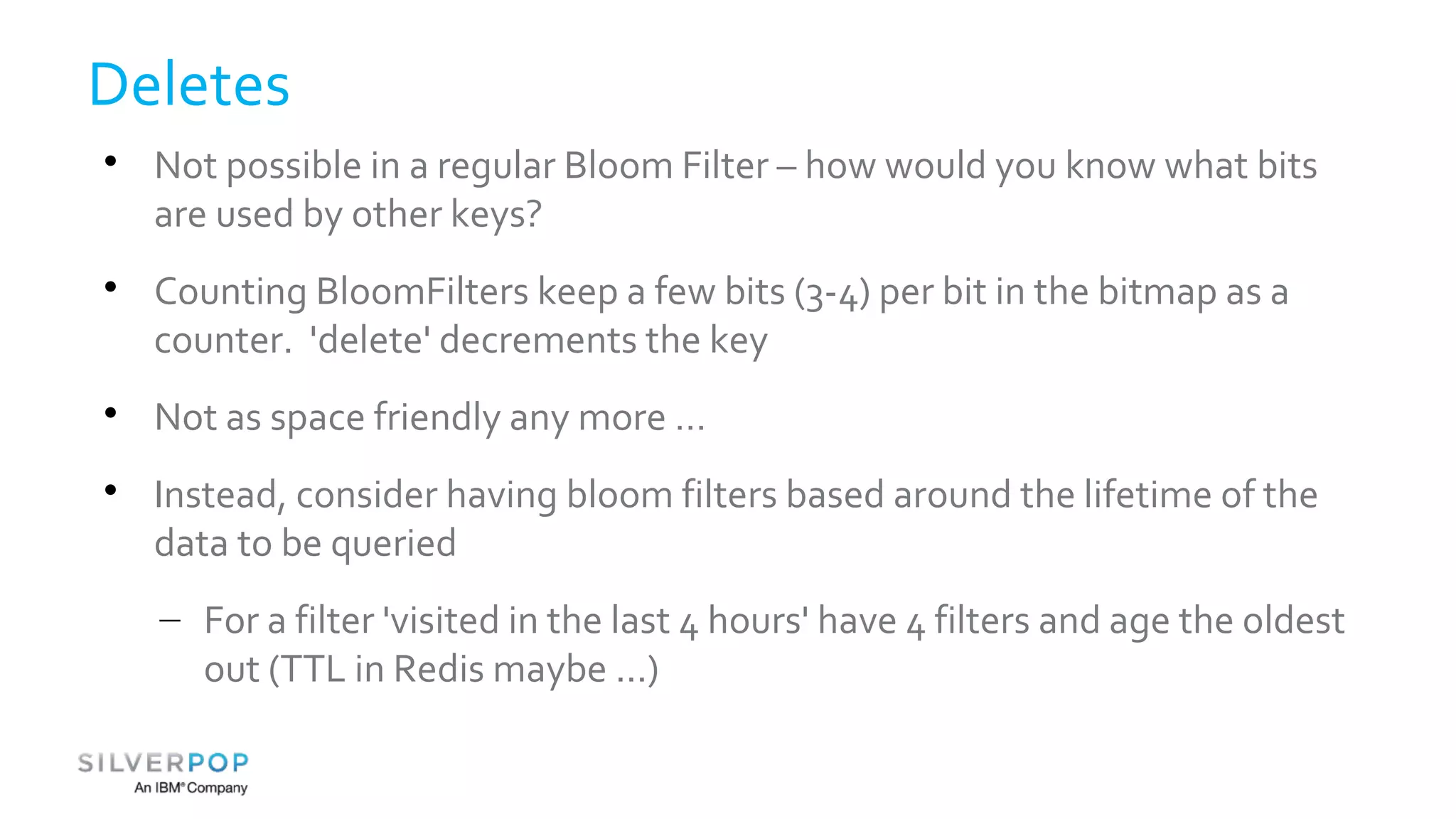
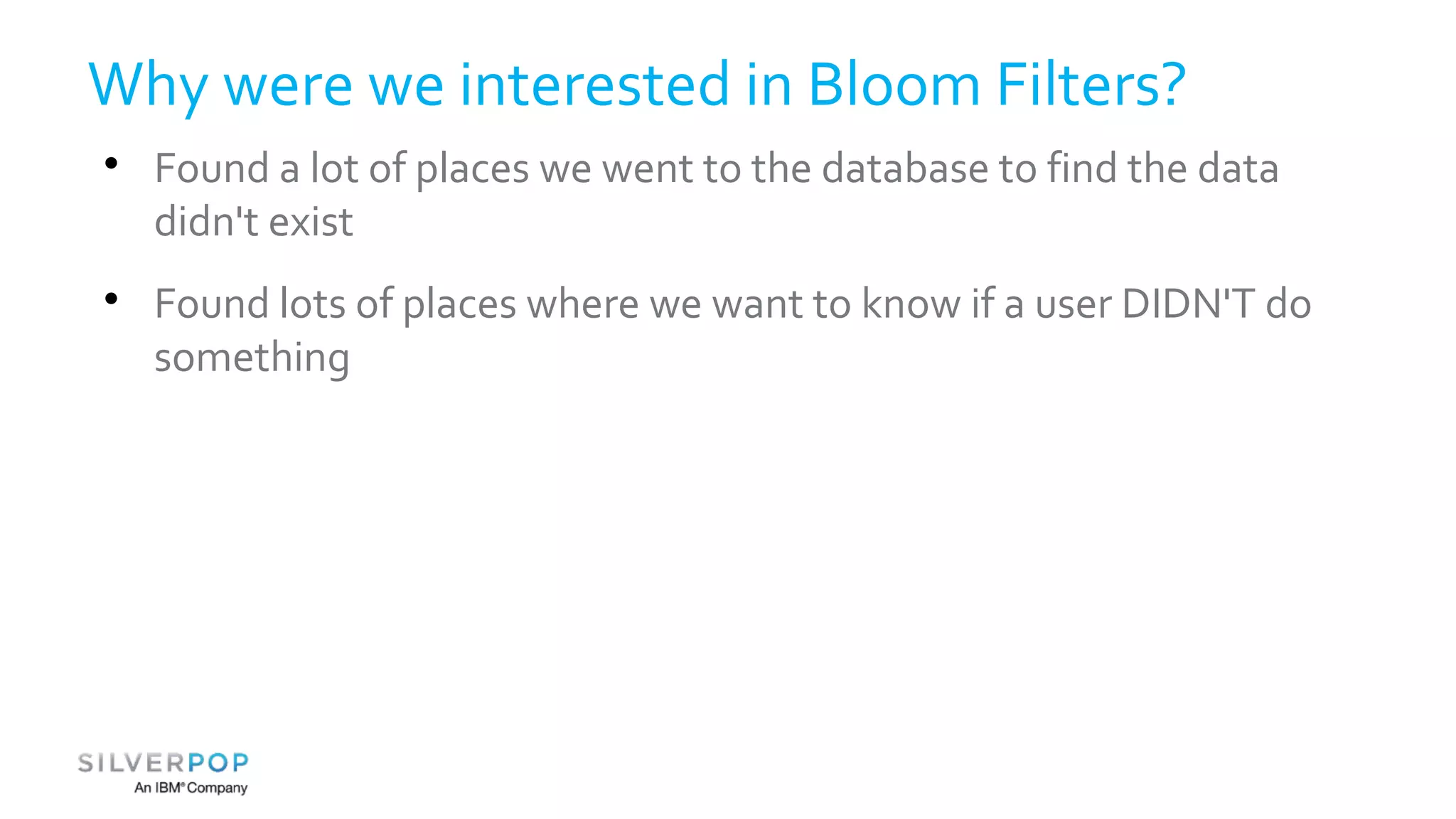
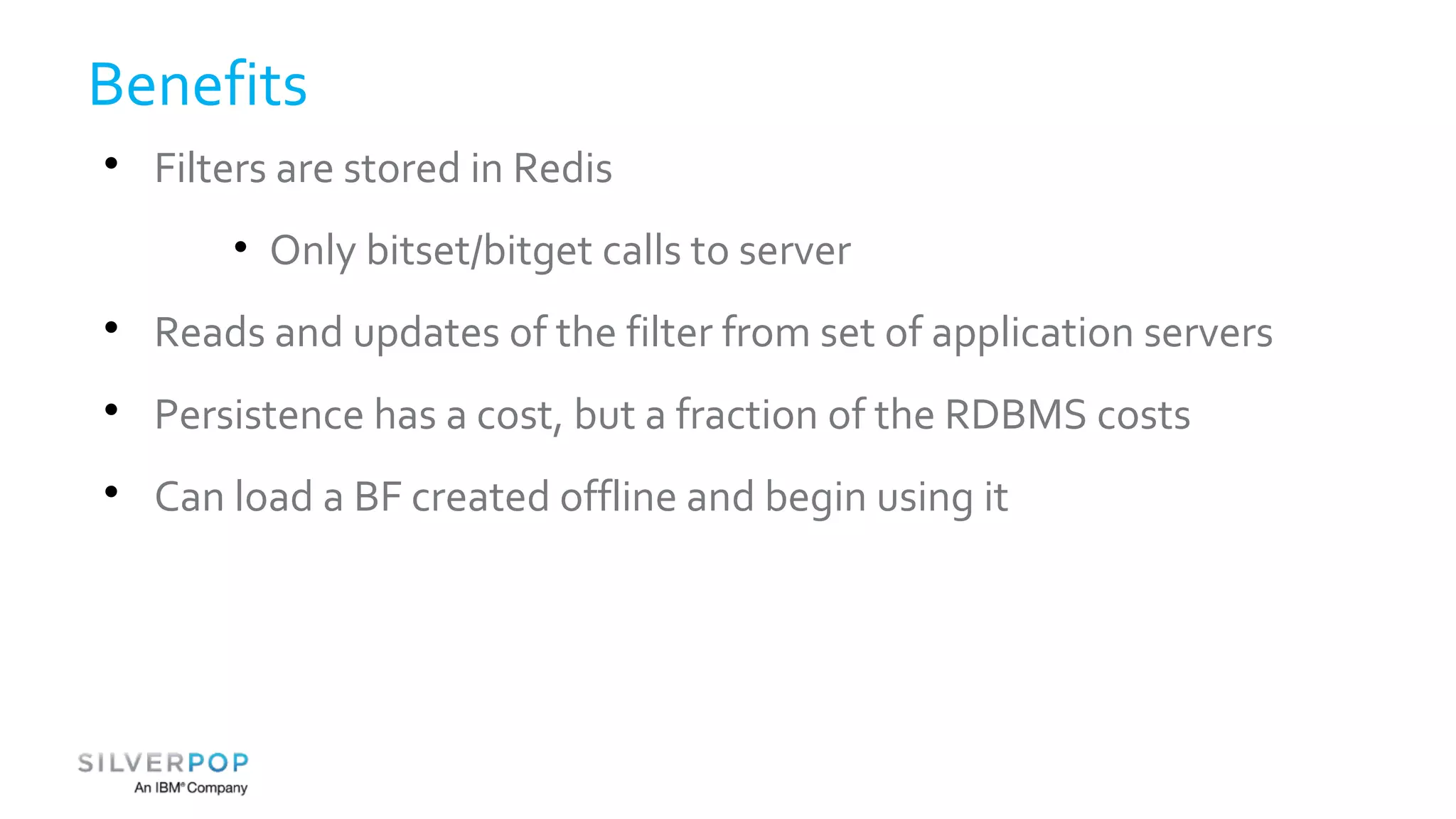
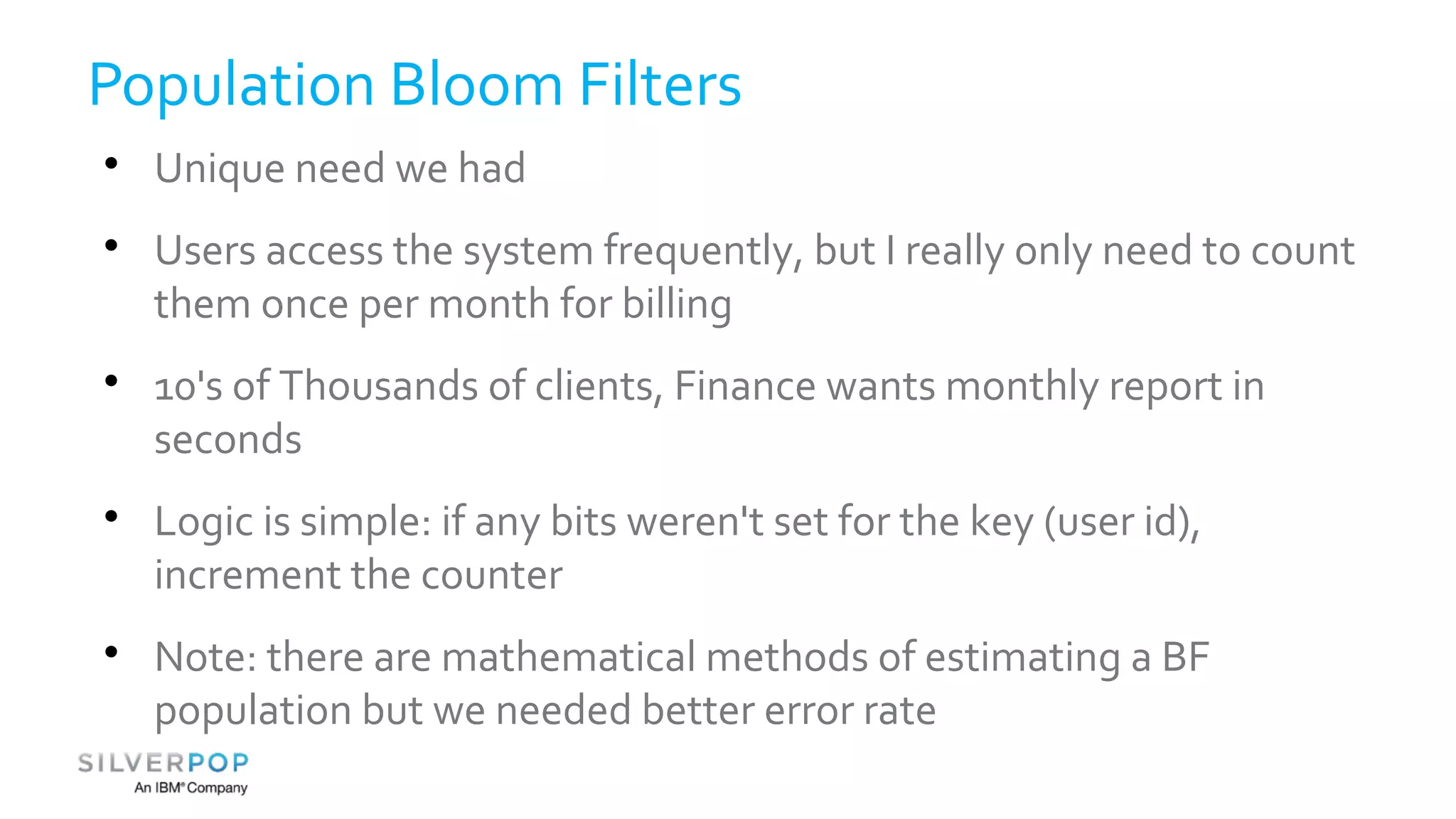
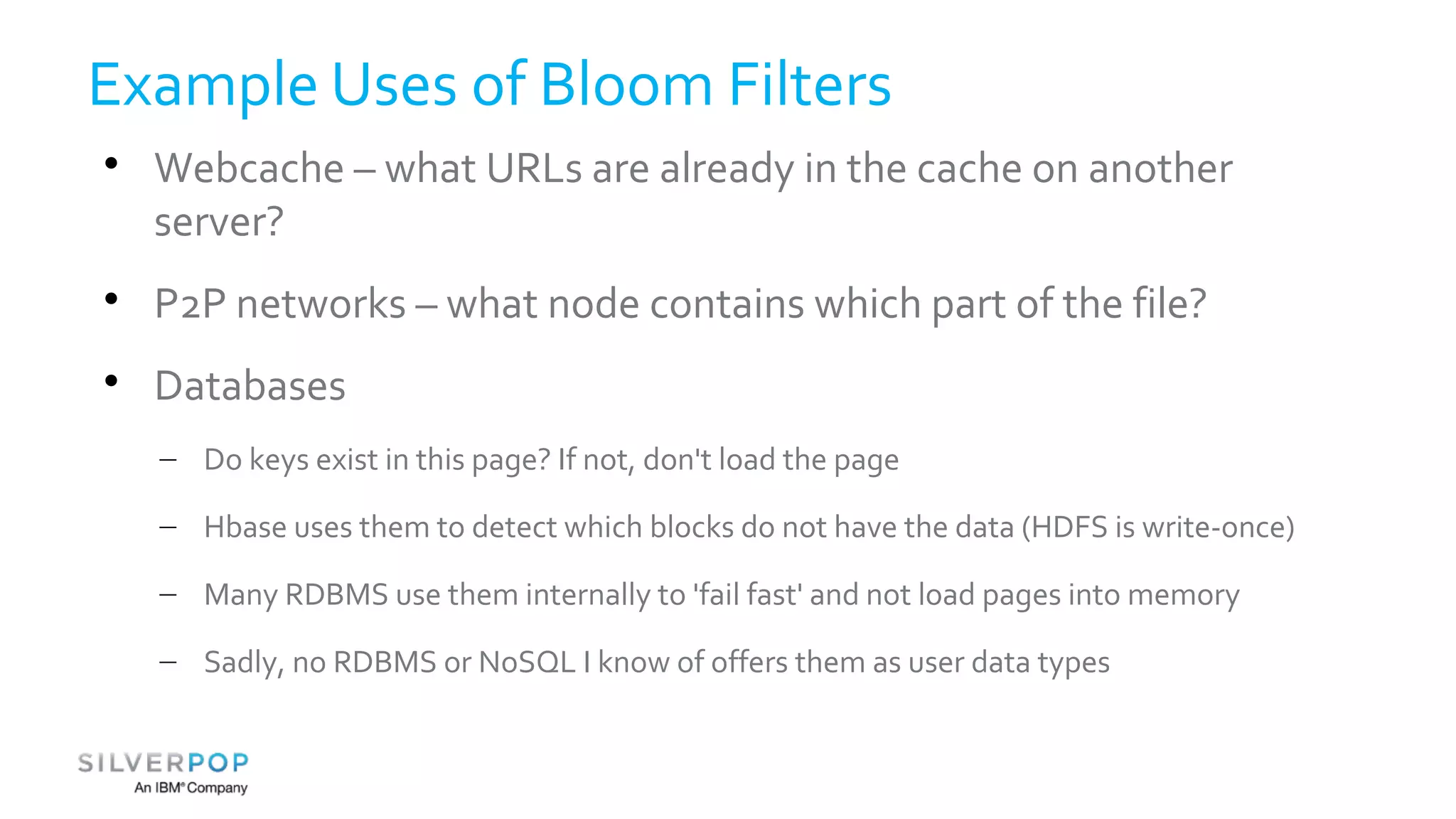
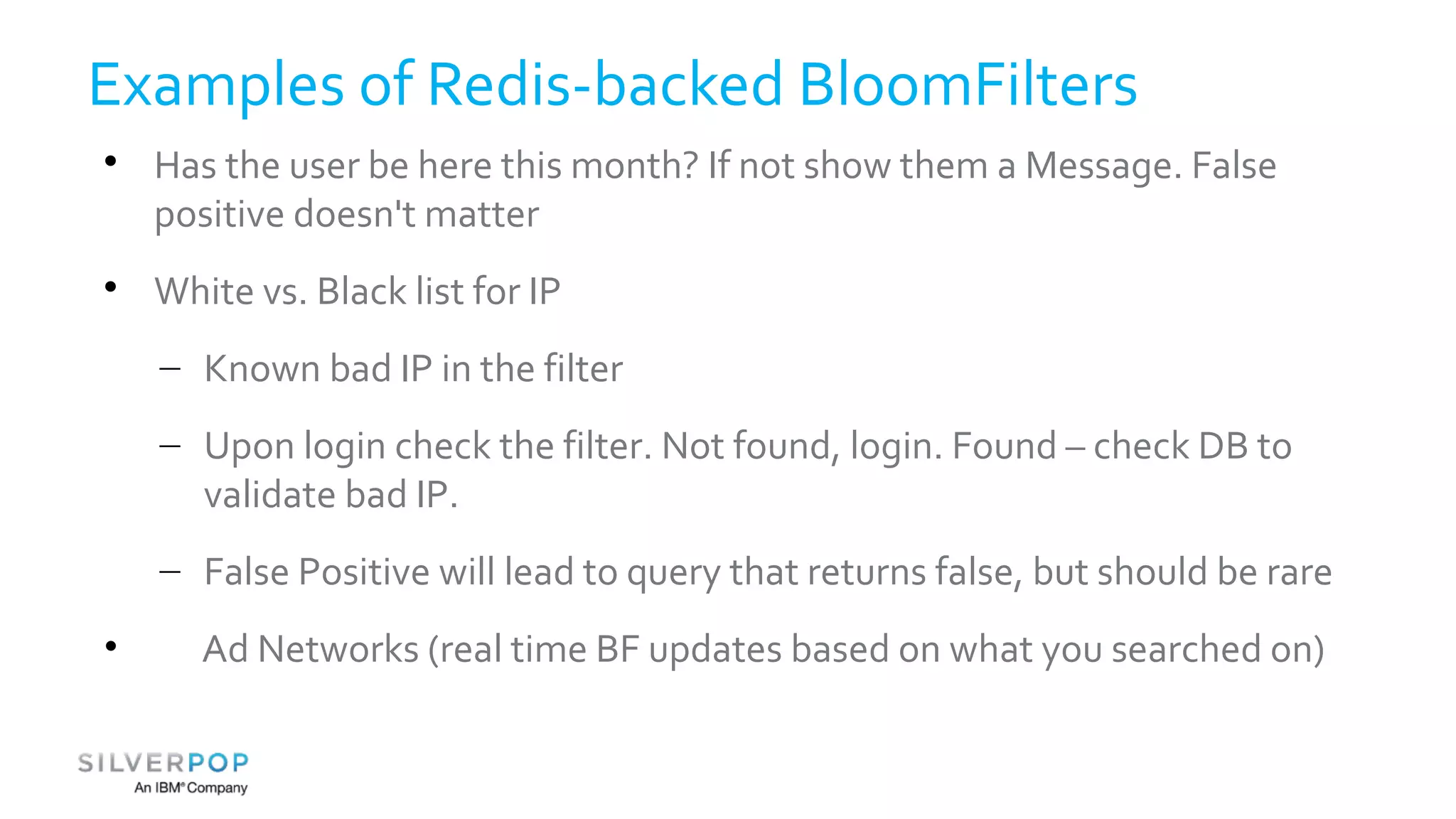
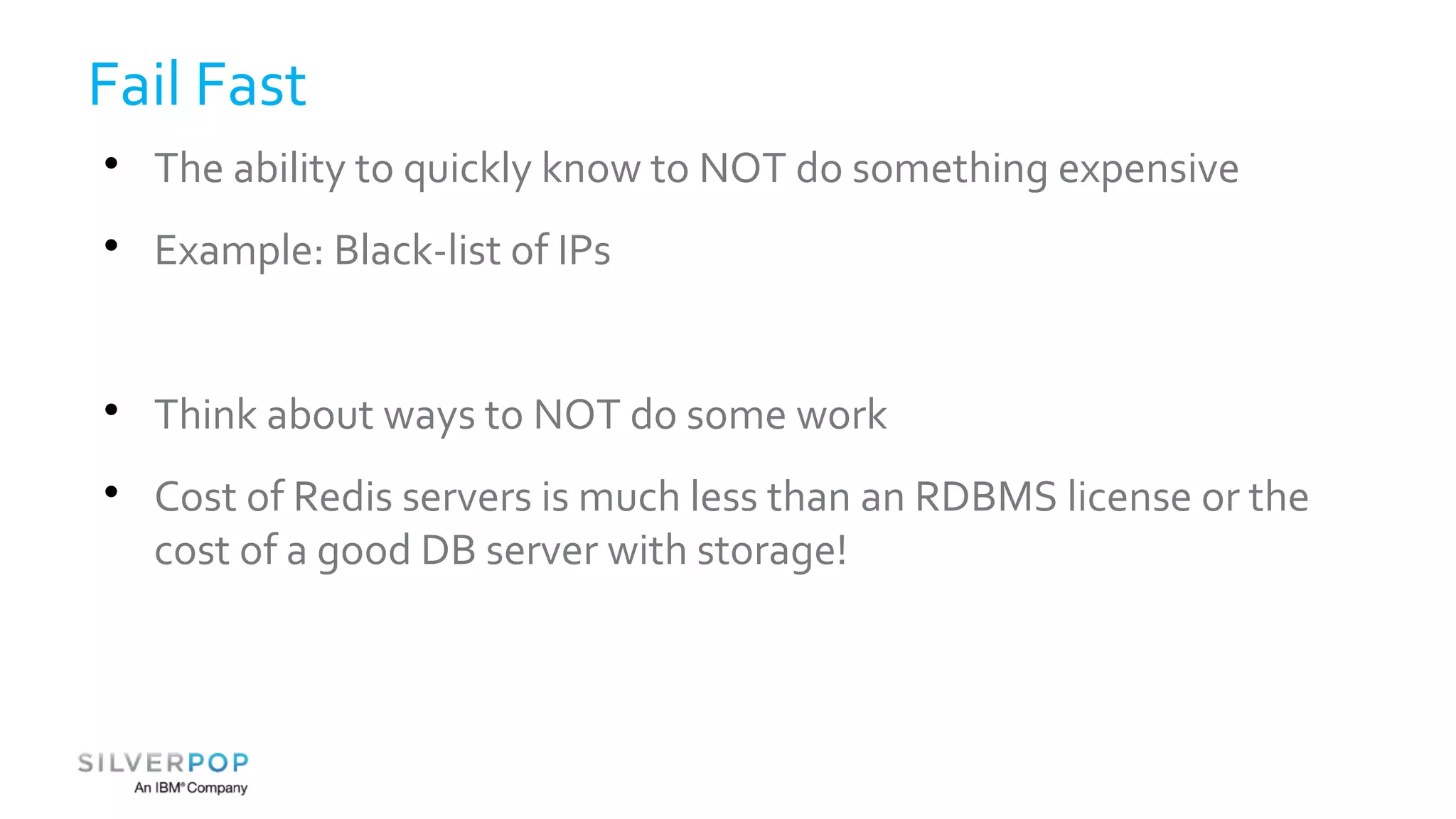
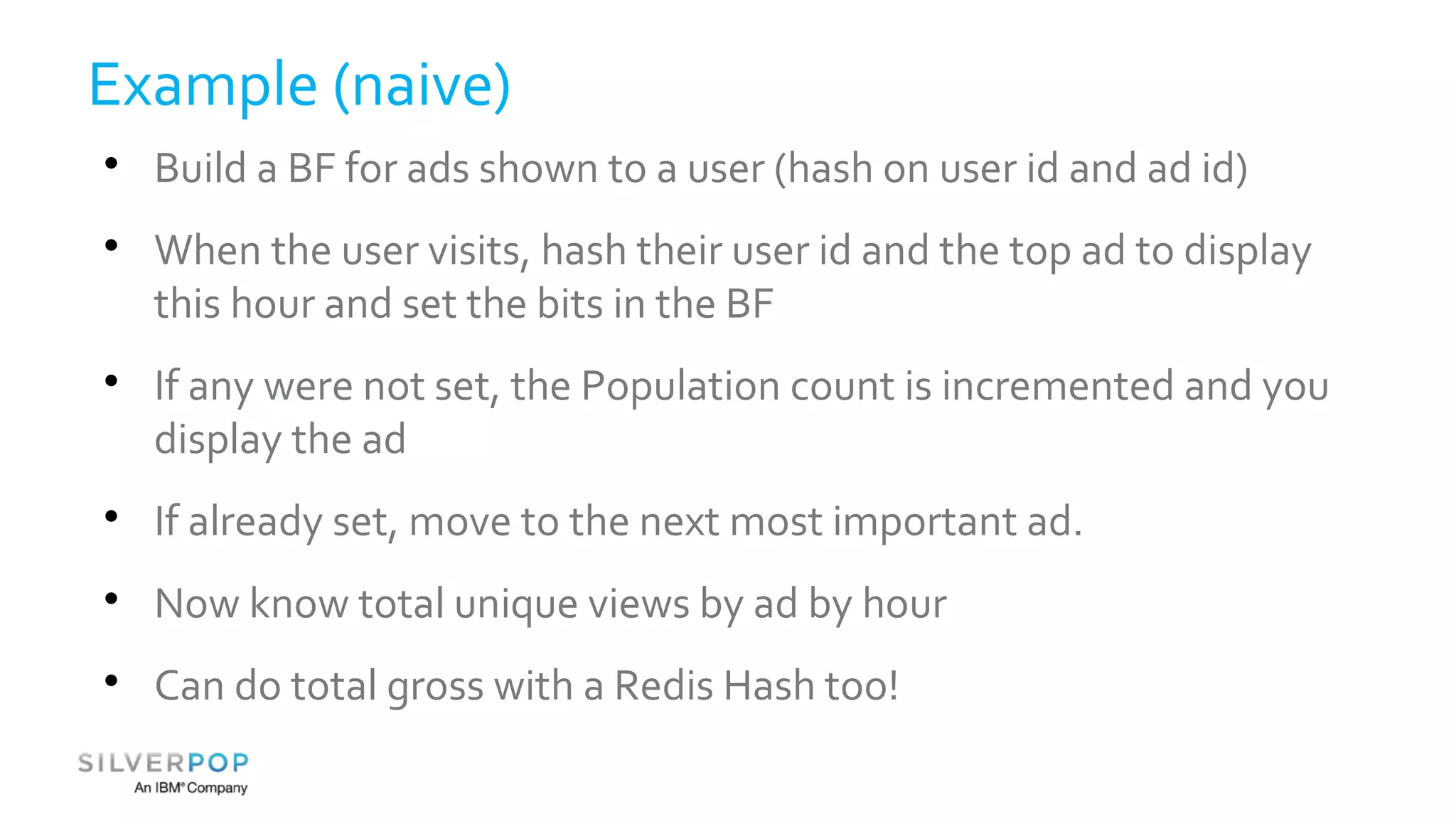
This document discusses using Redis to enable failing fast with Bloom filters. It provides an overview of Redis as a data structure server and key-value cache, as well as Bloom filters as a space-efficient probabilistic data structure for membership testing. By storing Bloom filters in Redis, they can be made updatable and persistent while avoiding the high costs of updating and querying large Bloom filters stored in databases. Examples are given where Redis-backed Bloom filters can be used to optimize queries and decide whether expensive operations need to be performed.