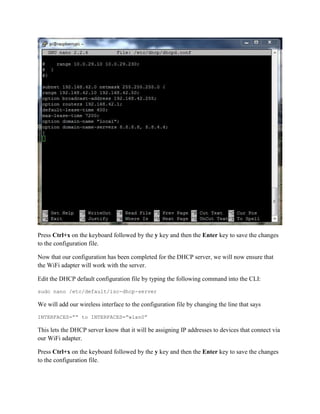
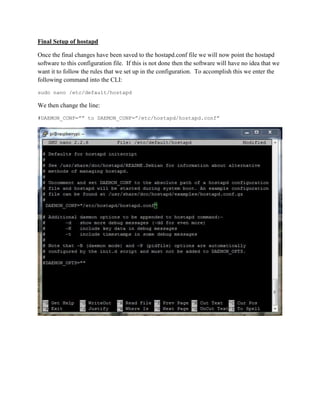
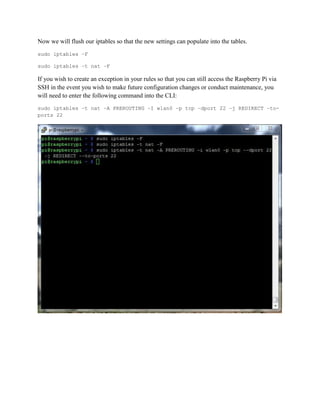
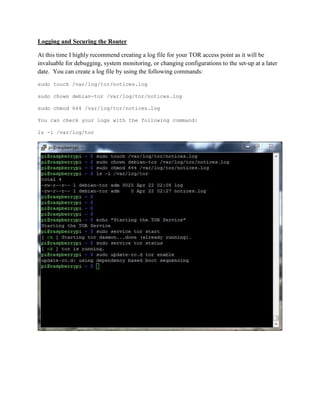
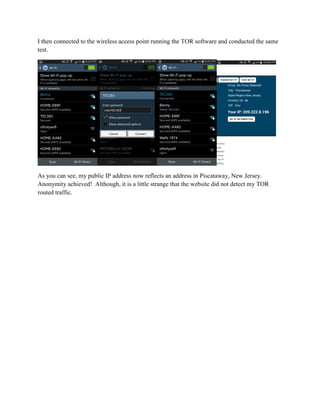
This document provides instructions for creating a wireless access point on a Raspberry Pi that routes all internet traffic through the TOR anonymity network. It involves installing an operating system on the Pi, configuring software like hostapd and dhcpd, and setting up network address translation. The access point is given a static IP and broadcasts an SSID of "TEC383" with WPA2 encryption. All configurations are saved so the access point will restart automatically with these settings.