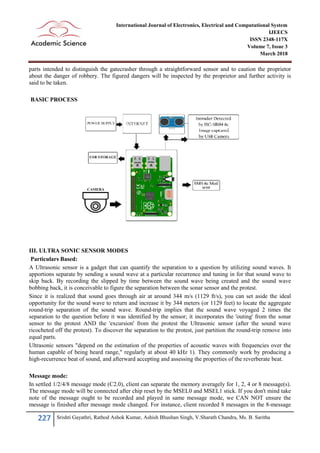
This document describes a home surveillance system that uses a Raspberry Pi connected to an ultrasonic sensor to detect intruders. The system is designed to monitor a home or shop for security purposes. When the ultrasonic sensor detects an intruder based on distance readings, it sends an alert message and photo to the owner. The system aims to automatically detect intruders, unlike CCTV which requires constant video review. It uses low-cost hardware and provides real-time alerts to help prevent crime.




![230 Srishti Gayathri, Rathod Ashok Kumar, Ashish Bhushan Singh, V.Sharath Chandra, Ms. B. Saritha
International Journal of Electronics, Electrical and Computational System
IJEECS
ISSN 2348-117X
Volume 7, Issue 3
March 2018
The Email is a substitute method for informing the proprietor about the guest, in light of the fact that the SMS
which is sent may not be conveyed to the proprietor's telephone because of system issues or Internet issues.
Henceforth Email is another most ideal method for advising. Consequently the code will be composed in the
capacity called "send_email" which will contain every one of the certifications, for example, the mail id from
which the message is to be sent, the secret word of that record and the mail id which ought to get the email
about the guest's essence. Before giving a mail id in the code, that mail id ought to be made, that is the mail id
ought to be enrolled with Gmail.
The picture with an instant message which ought to be sent to the proprietor through an Email ought to
likewise be indicated in the python code. It might be something like "Interloper Detected" with a picture
caught of the gatecrasher. Consequently along these lines the Owner is informed through two means about the
guest's quality.
V. CONCLUSIONS
Therefore we have outlined a brilliant observation framework fit for catching picture and transmitting to a cell
phone. It is beneficial as it offers dependability and protection on the two sides. Fundamental move can be
made in limited capacity to focus time on account of crisis conditions, for example, elderly individual falling
debilitated, military regions, brilliant homes, workplaces, businesses and so on.,
Once in a while, our choice to introduce video reconnaissance may frequently take after a disagreeable
occurrence. In the event that apparatus, assets are continually vanishing from your store, or any savagery has
influenced you to feel dangerous, you will need some expanded security. You presumably feel your house is
well protected prepared for break-ins and interlopers.
You keep your entryways and windows bolted and mull over who you've given an extra key or the code to
your carport way to however "That is sufficiently not". Observation framework will give you this true
serenity. A Surveillance framework that is suited to your correct needs will give ideal security and this won't
just enable you to examine wrongdoings, yet in addition to viably avert potential lawbreakers. In case of a
crisis, the framework will likewise help you to keep up an outline and call for help rapidly
VI. REFERENCES
[1] CCTV cameras: If they do not stop crime or catch criminals, what are they for?, Telegraph, Aug. 24, 2009.
[2] Steve Chapman, Do cameras stop crime?, Chi. Trib, Sept. 20, 2011; Do security cameras deter crime?, Homeland
Sec. News, Feb. 22, 2011.
[3] Charlie Savage, US doles out millions for street cameras, Bos. Globe, Aug. 12, 2007.
[4] For example, some opponents of cameras argue cameras don’t eliminate but merely displace crime. See generally
Sam Waples, e.al., Does CCTV Displace Crime?, 9 Criminology & Crim. Just. 207 (2009), abstract.
[5] Nick Taylor, Closed Circuit Television: The British Experience, 1999 Stan. Tech. L. Rev. 11, 1 (1999).
[6] B. Welsh & D. Farrington, “Crime Prevention Effects of Closed Circuit Television: A Systemic Review”, Home
Office Research, Development and Statistics Directorate (2002); see Noam Biale, “Expert Findings on Surveillence
Cameras: What Criminologists and Others Studying Surveillence Cameras Have Found”, ACLU at 3 (White Paper
based on major studies 2000-2008), available here.
[7] David Weisburd et. al., Effects of Closed-Circuit Television on Crime, 587 Annals Am. Acad. Pol. & Soc. Sci. 110,
133 (2003).](https://image.slidesharecdn.com/raspberypiiotindian-190326222518/85/Raspberypi-iot-indian-6-320.jpg)