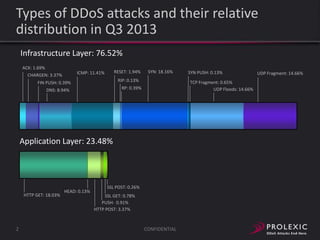
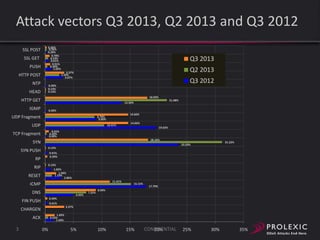
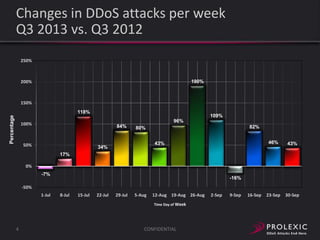
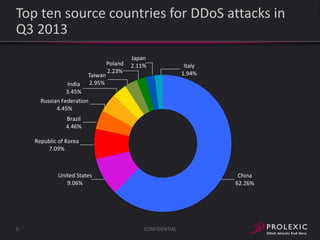
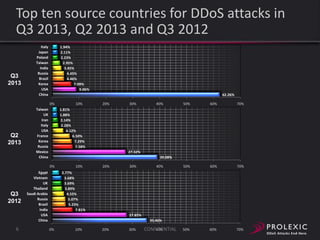
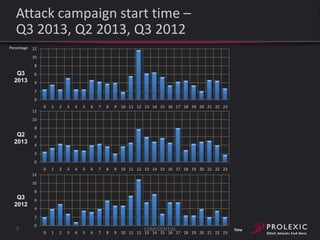
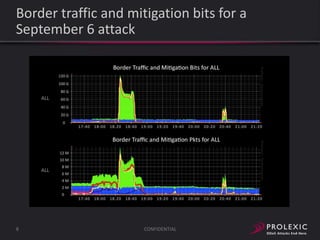
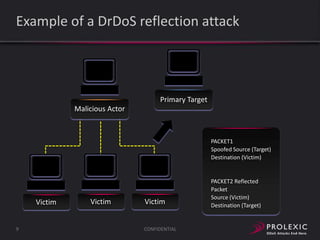
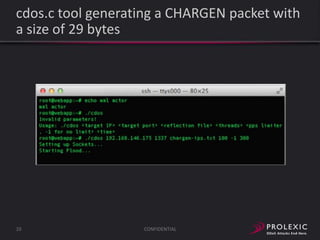
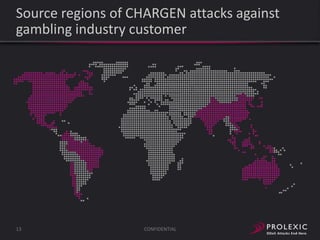
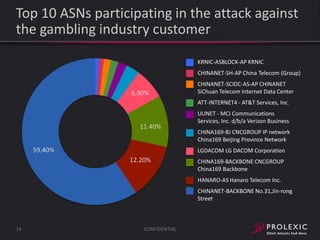
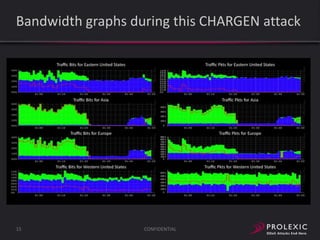
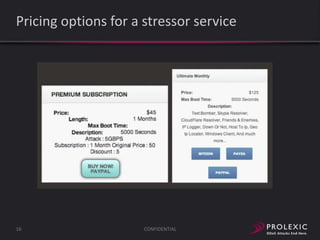
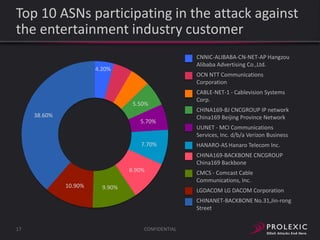
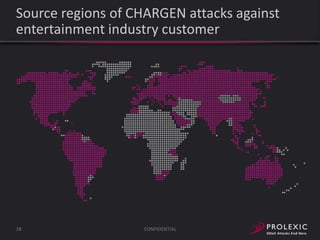
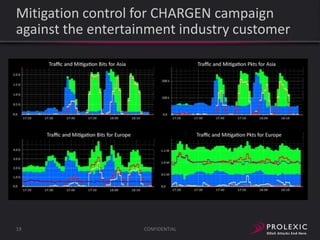
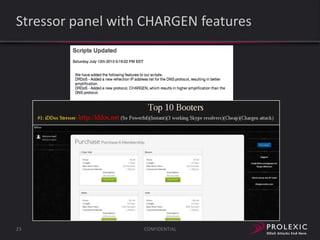
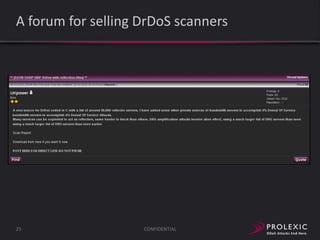
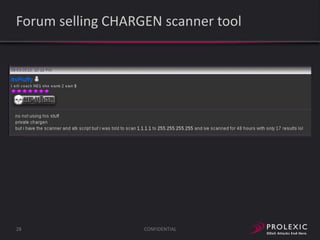
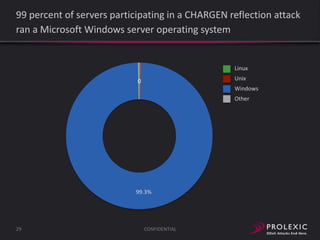
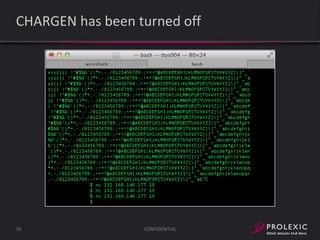
The document reports on distributed denial of service (DDoS) attack trends in Q3 2013. It finds that 76.52% of attacks targeted the infrastructure layer, with SYN floods being the most common at 18.16%. Application layer attacks made up 23.48% of attacks, led by HTTP GET floods at 18.03%. It analyzes attack vectors and source countries over time, finding that China was the top source country in Q3 2013 at 62.26%. Specific examples are also given of CHARGEN reflection attacks on gaming and entertainment industry customers.