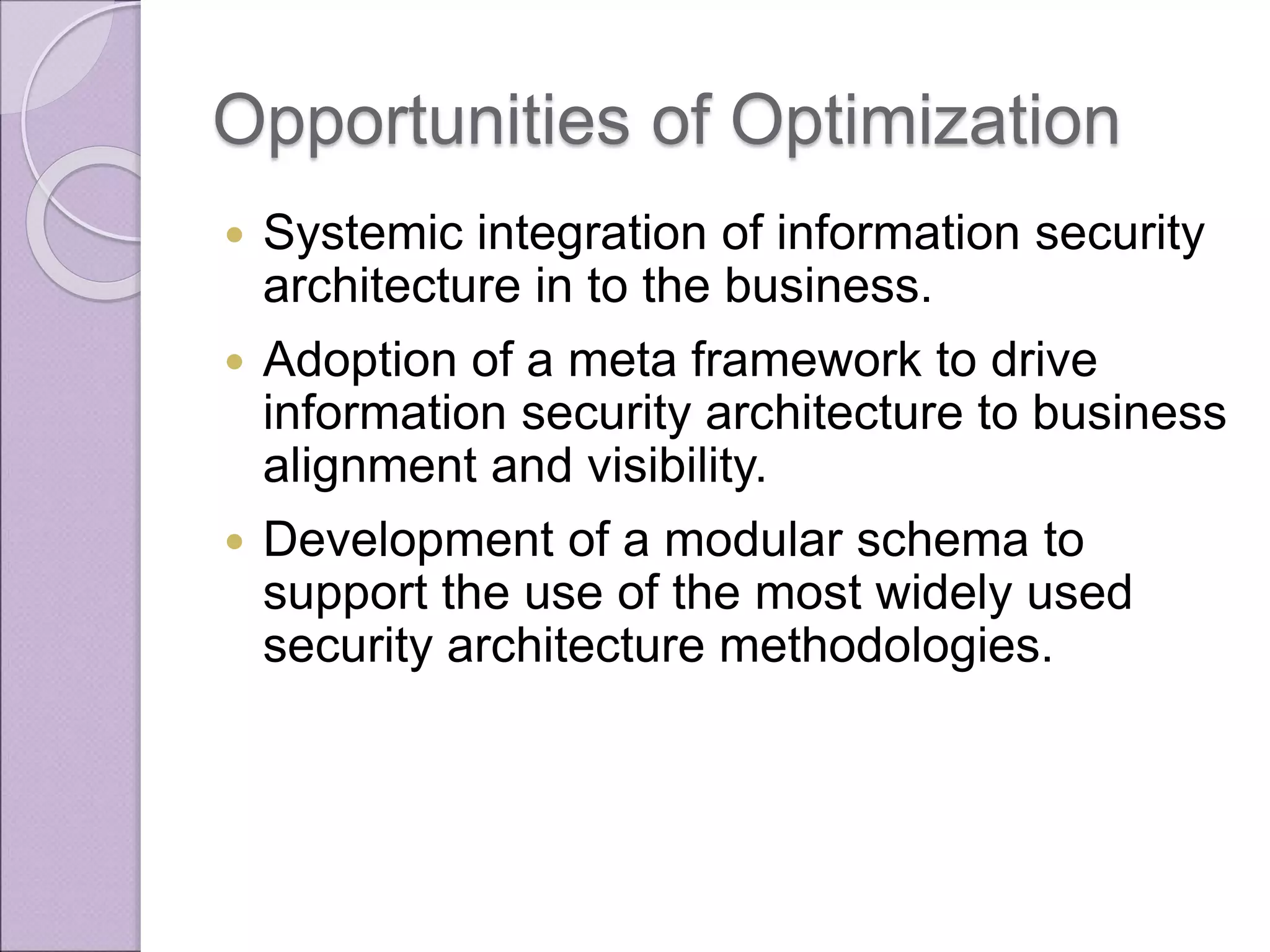
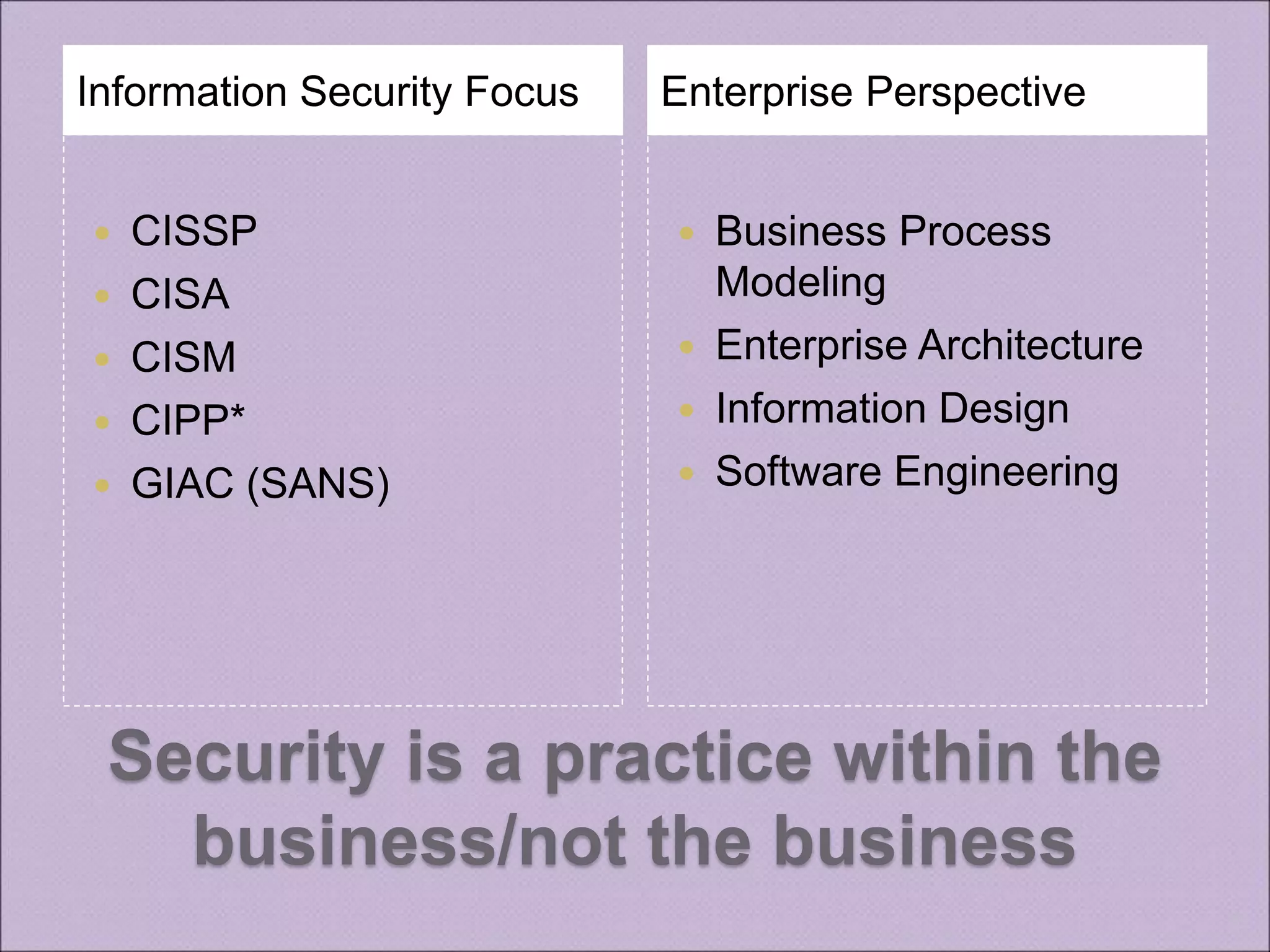
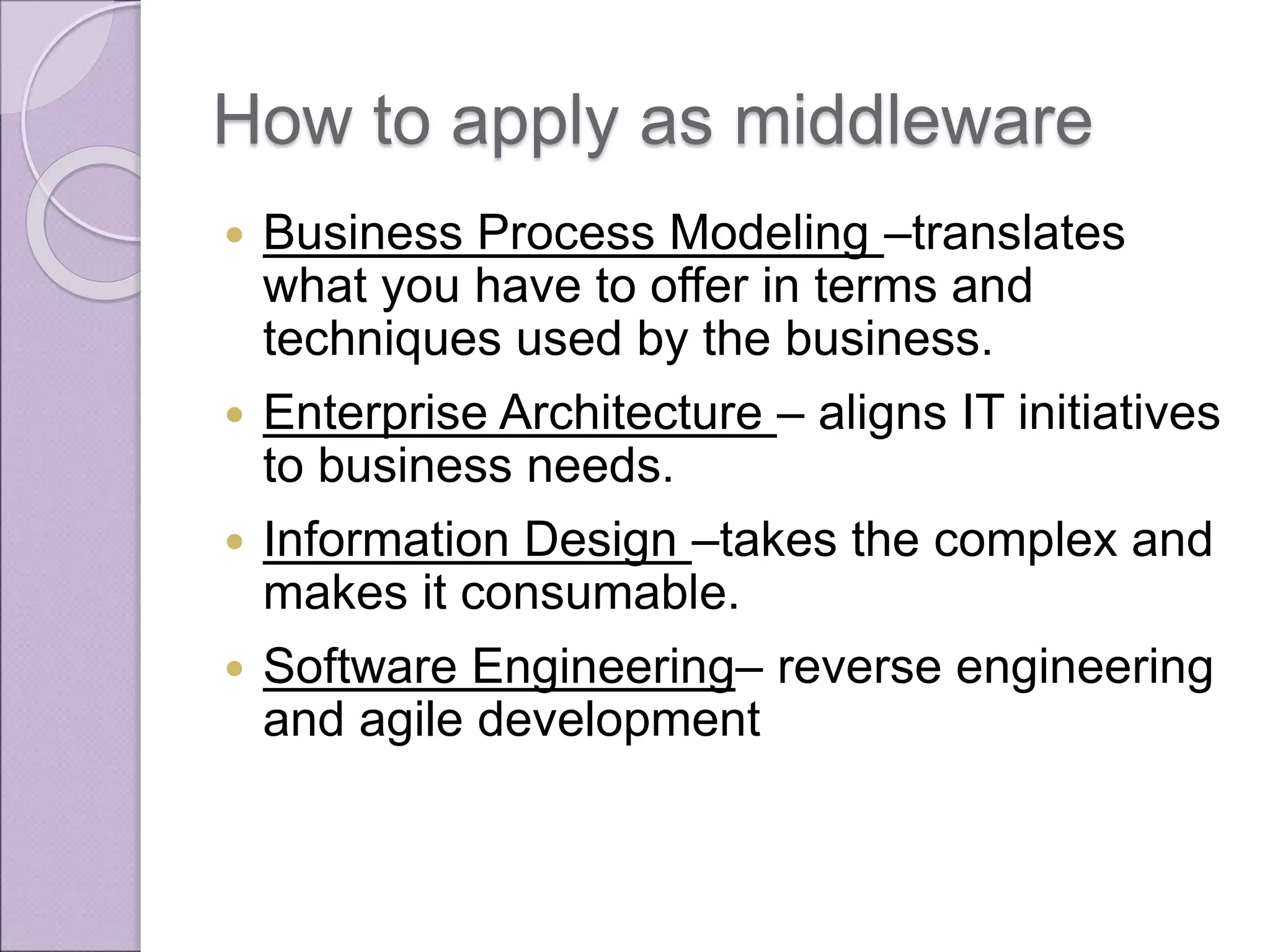
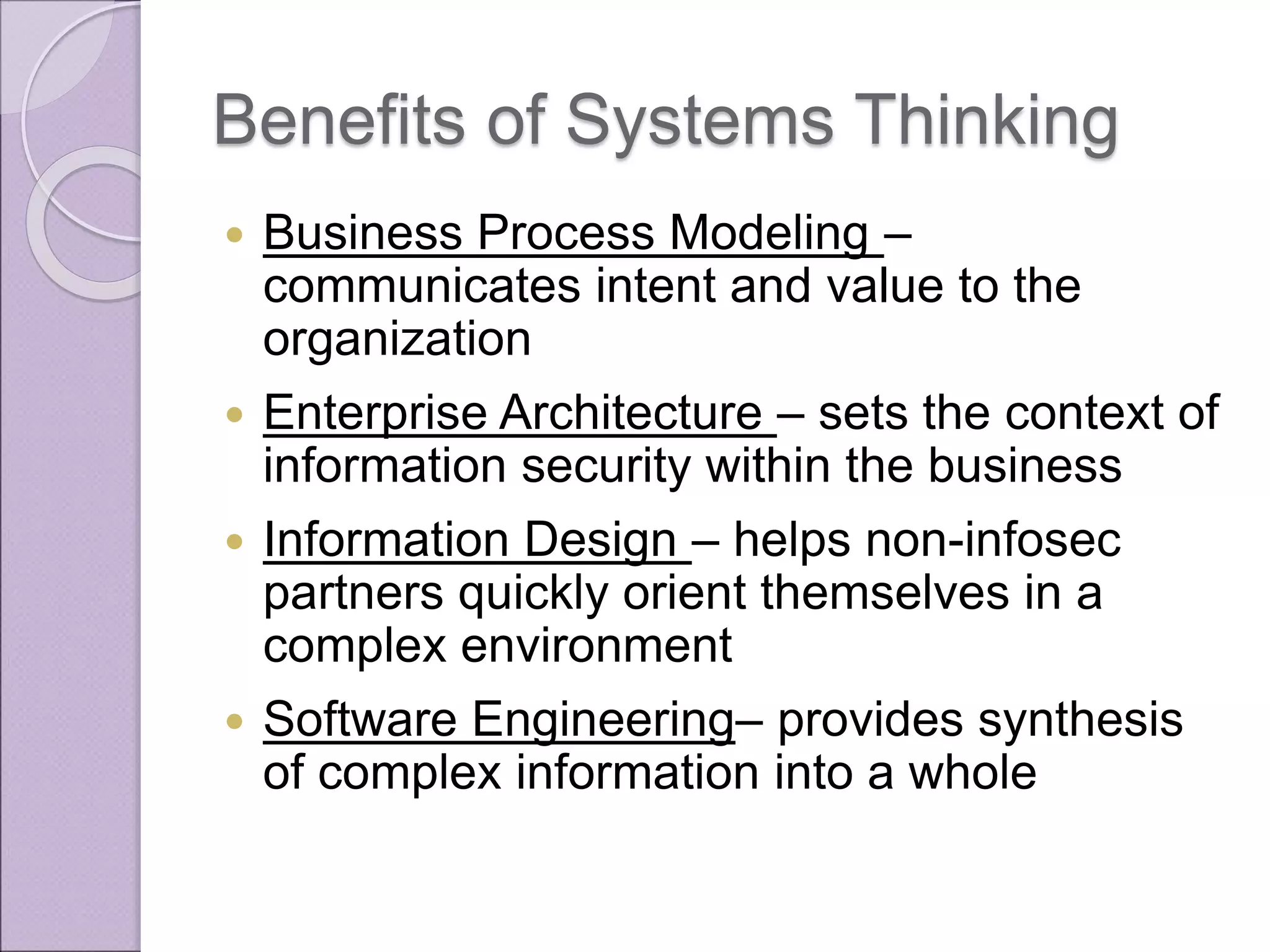
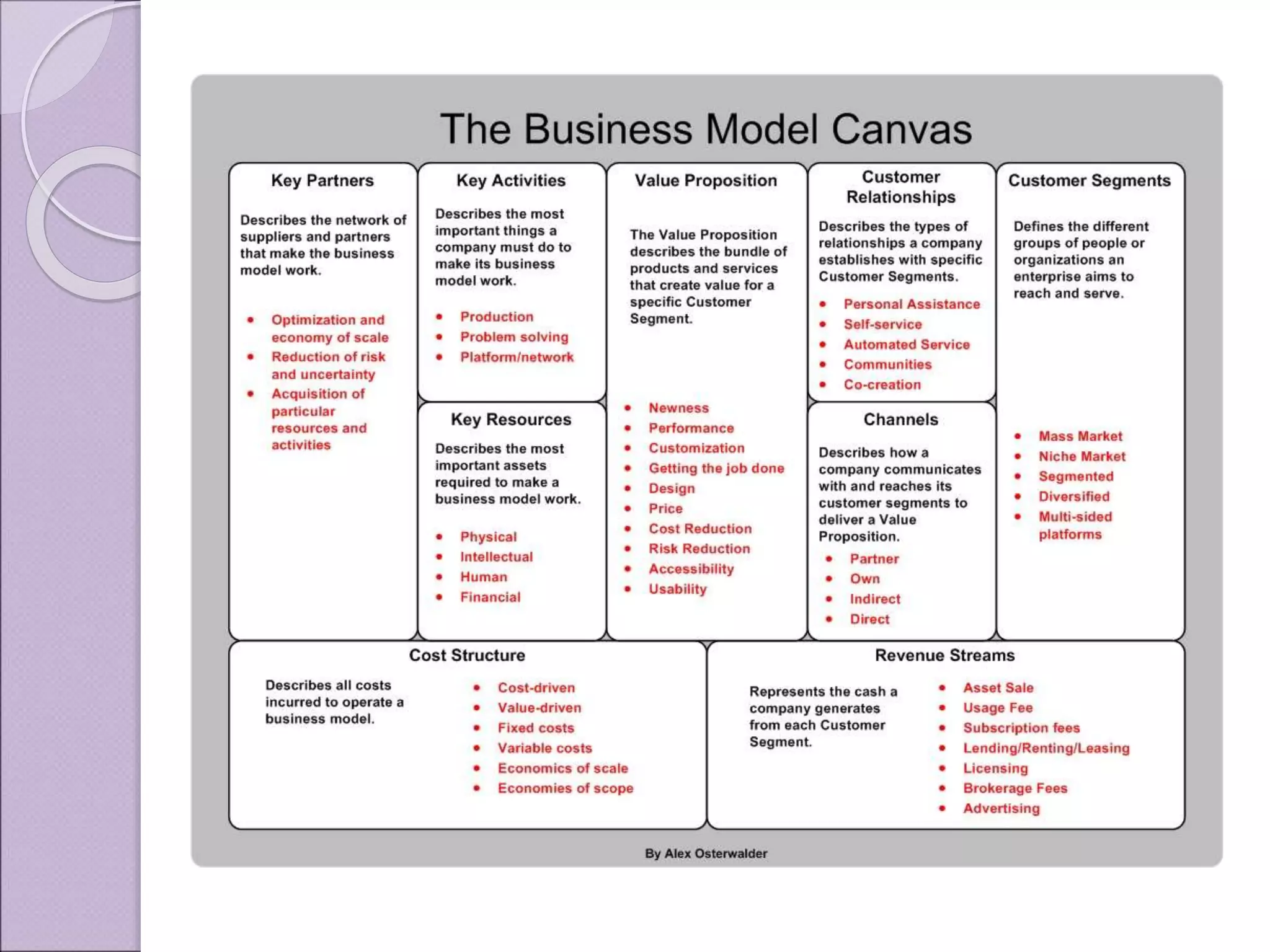
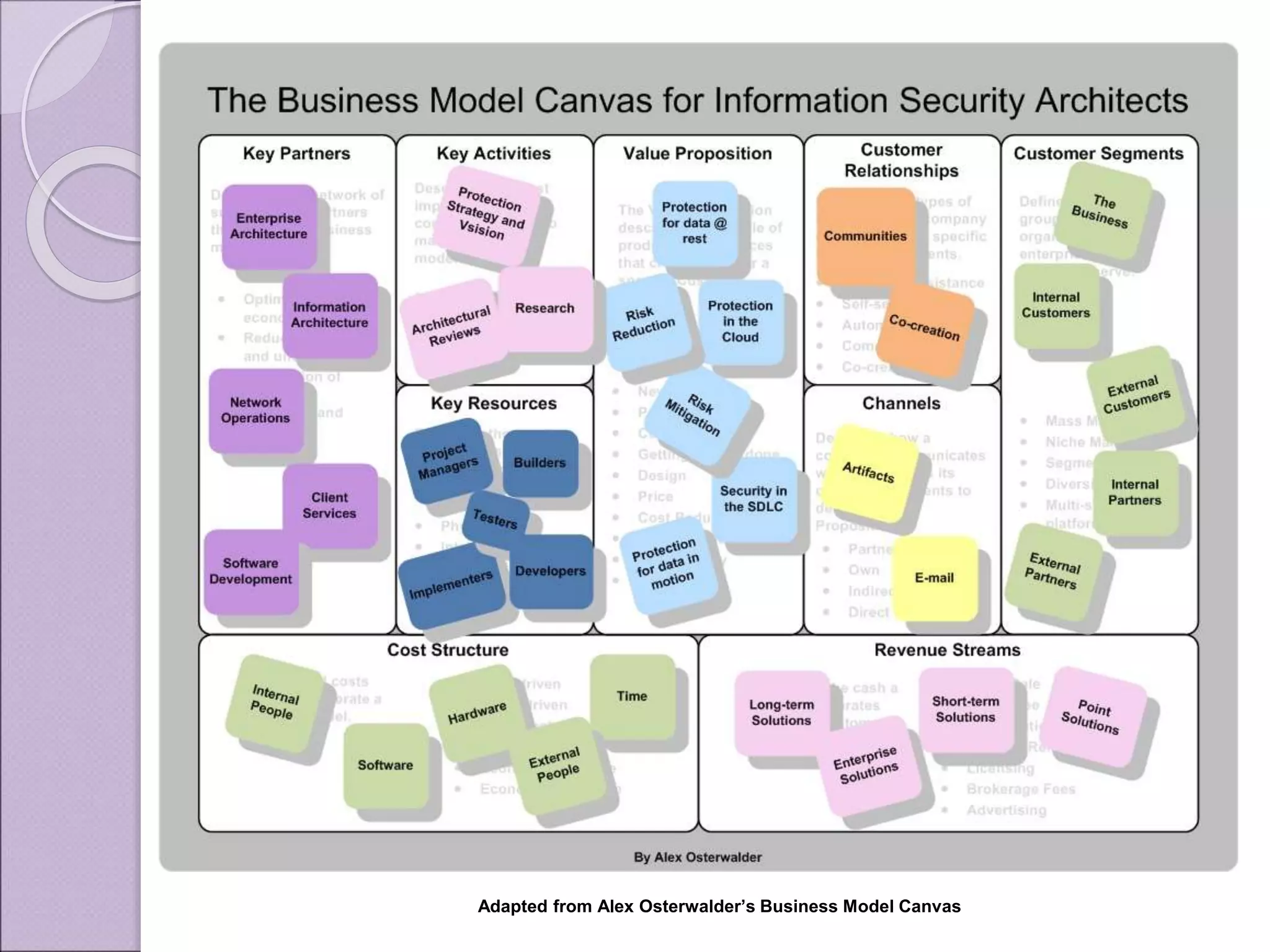
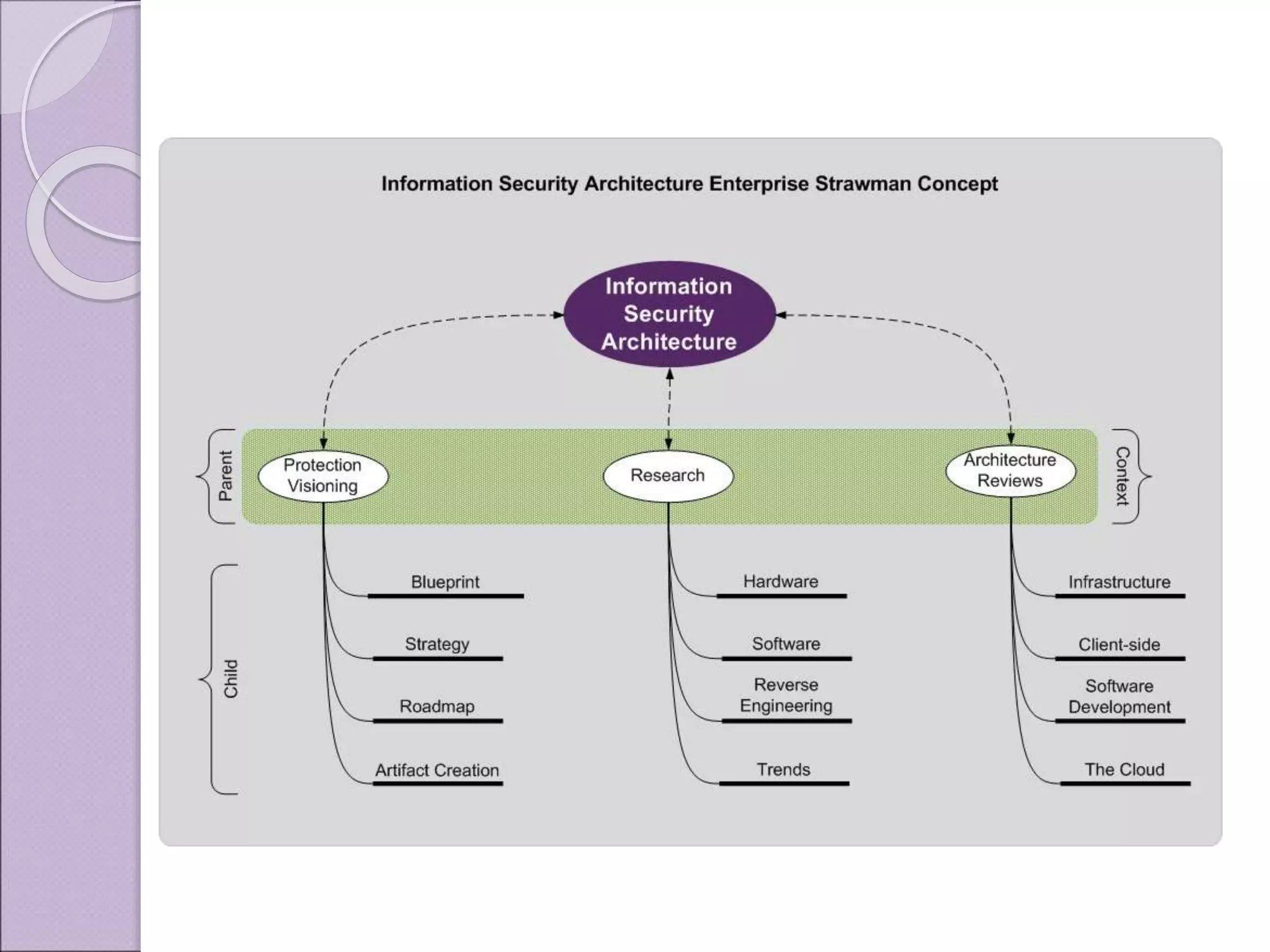
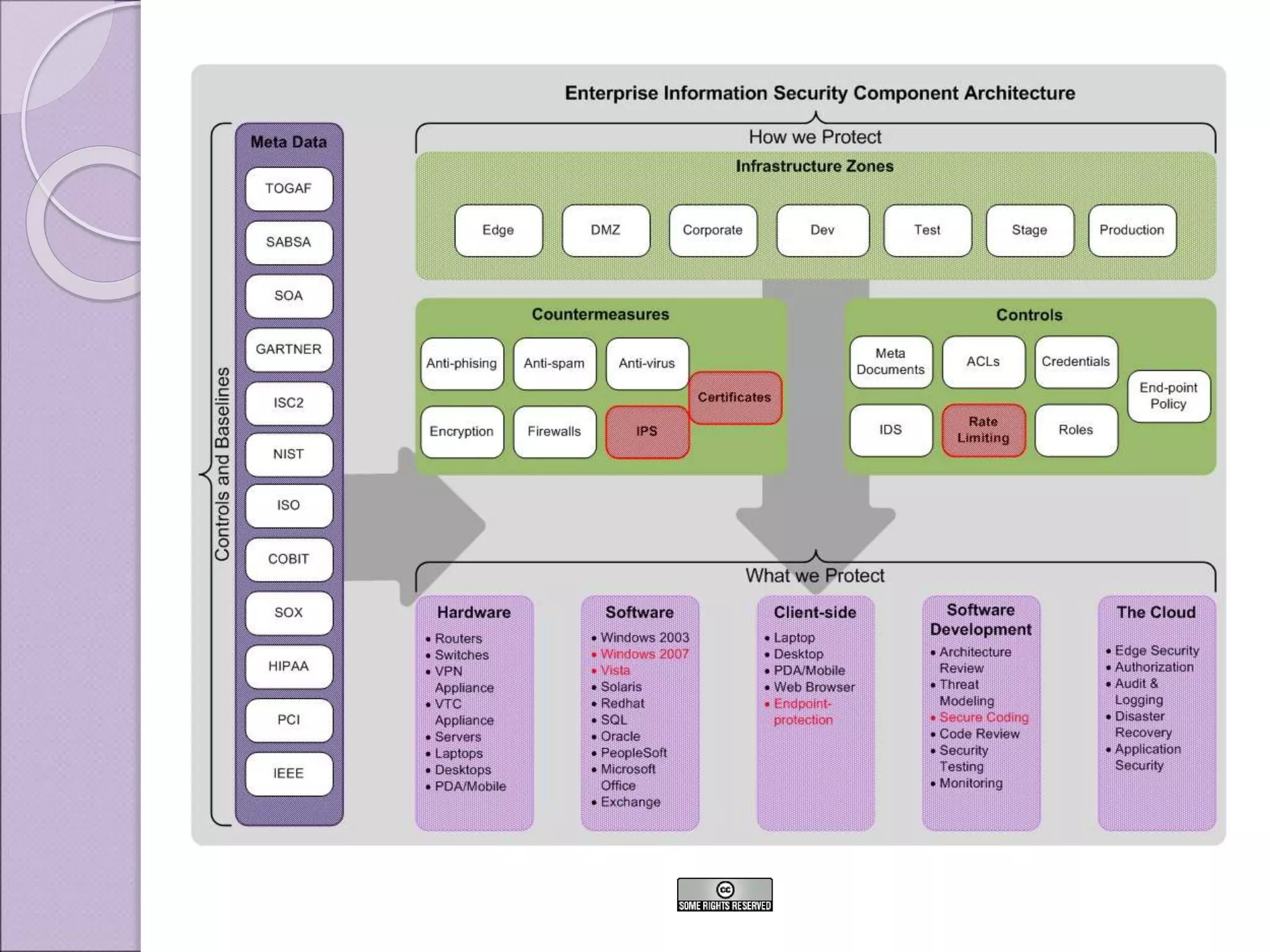
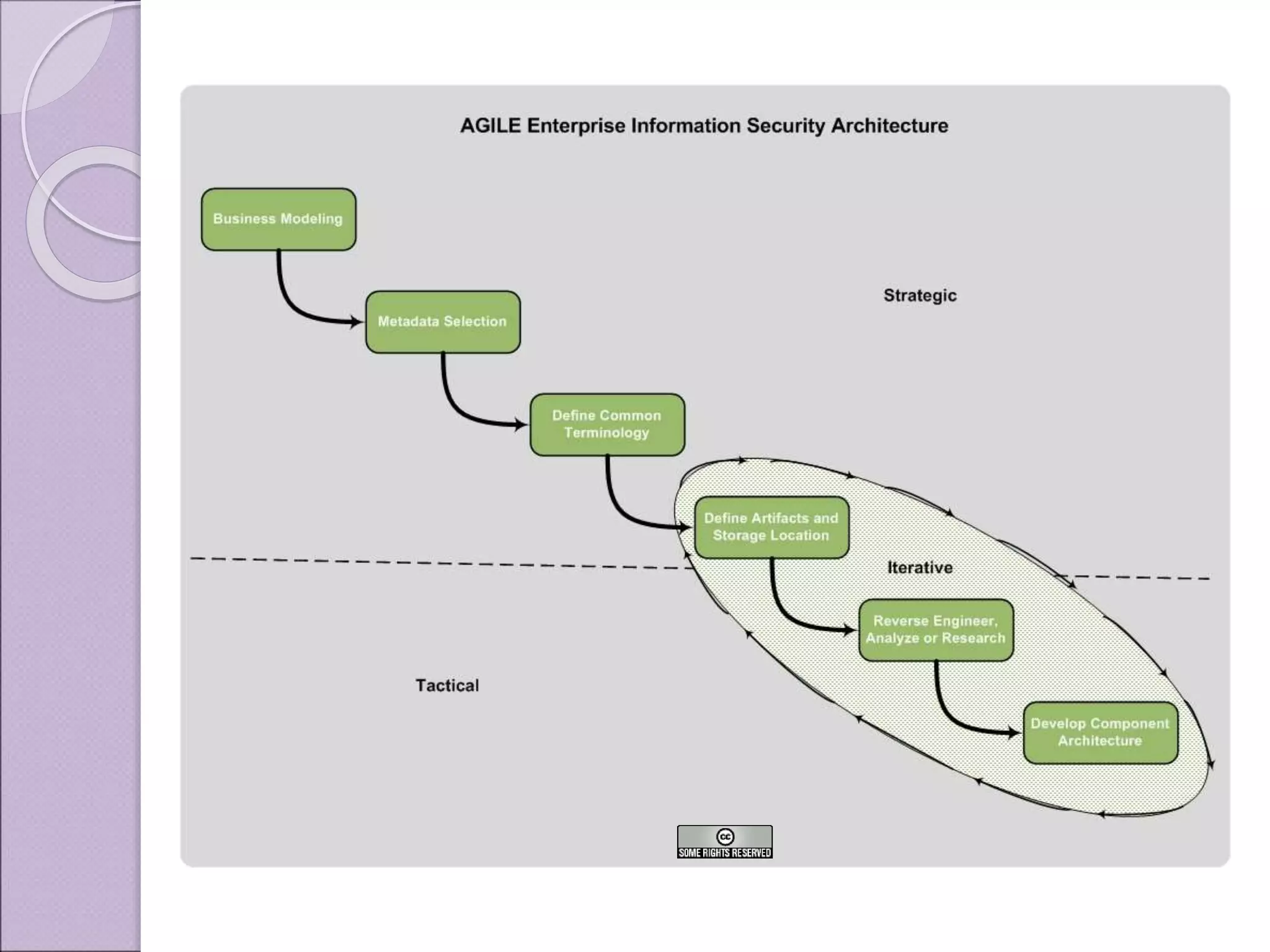
This document discusses improving enterprise information security architecture by taking a more business-focused systems thinking approach. It outlines the current state of security architecture, which can lack business alignment. The document proposes applying business modeling techniques, enterprise architecture, and information design to better integrate security as a practice within the business. This would involve developing a component-based security architecture using common artifacts and terminology to become more agile and contextualized to business needs.