Embed presentation
Downloaded 10 times




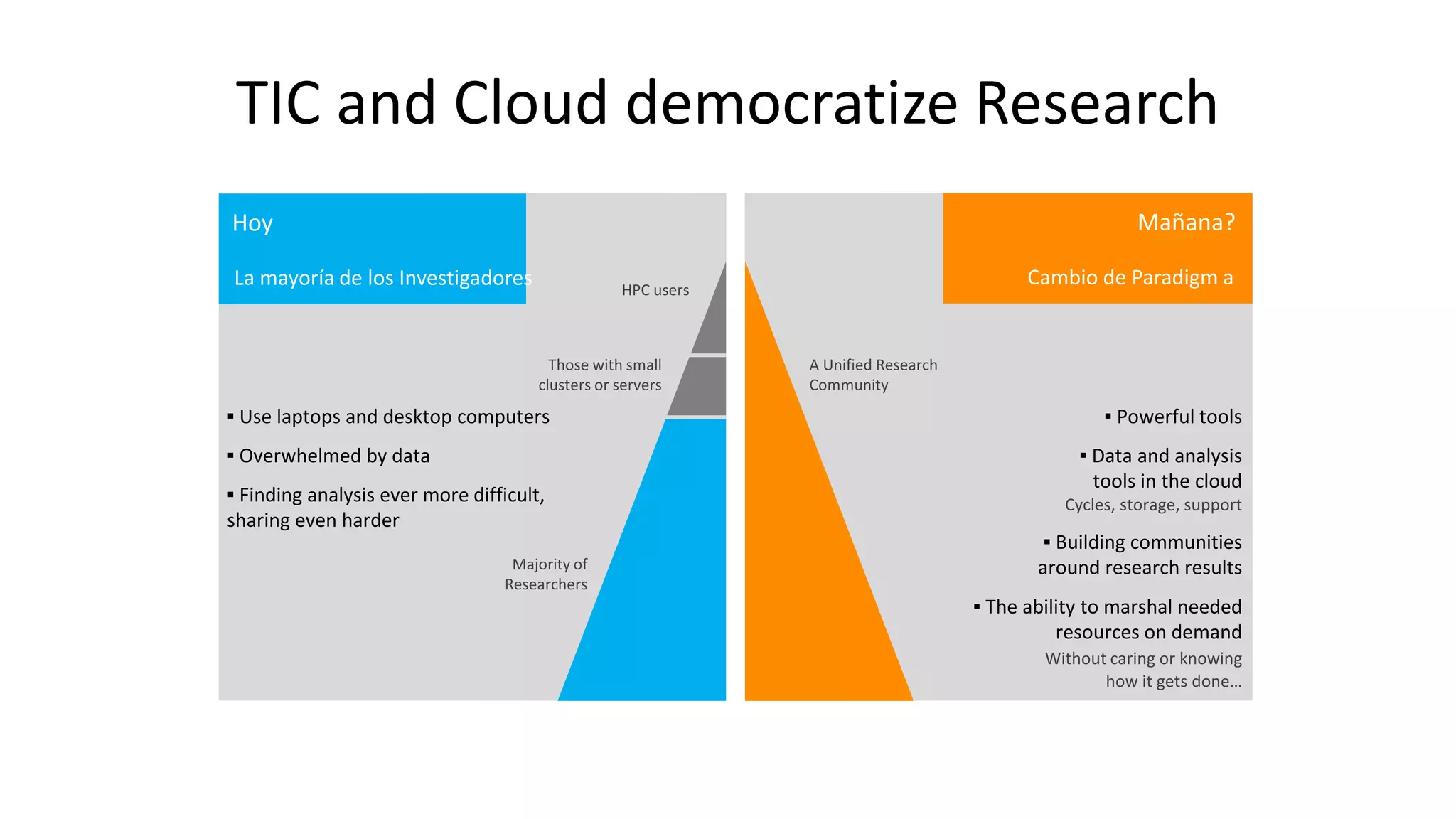


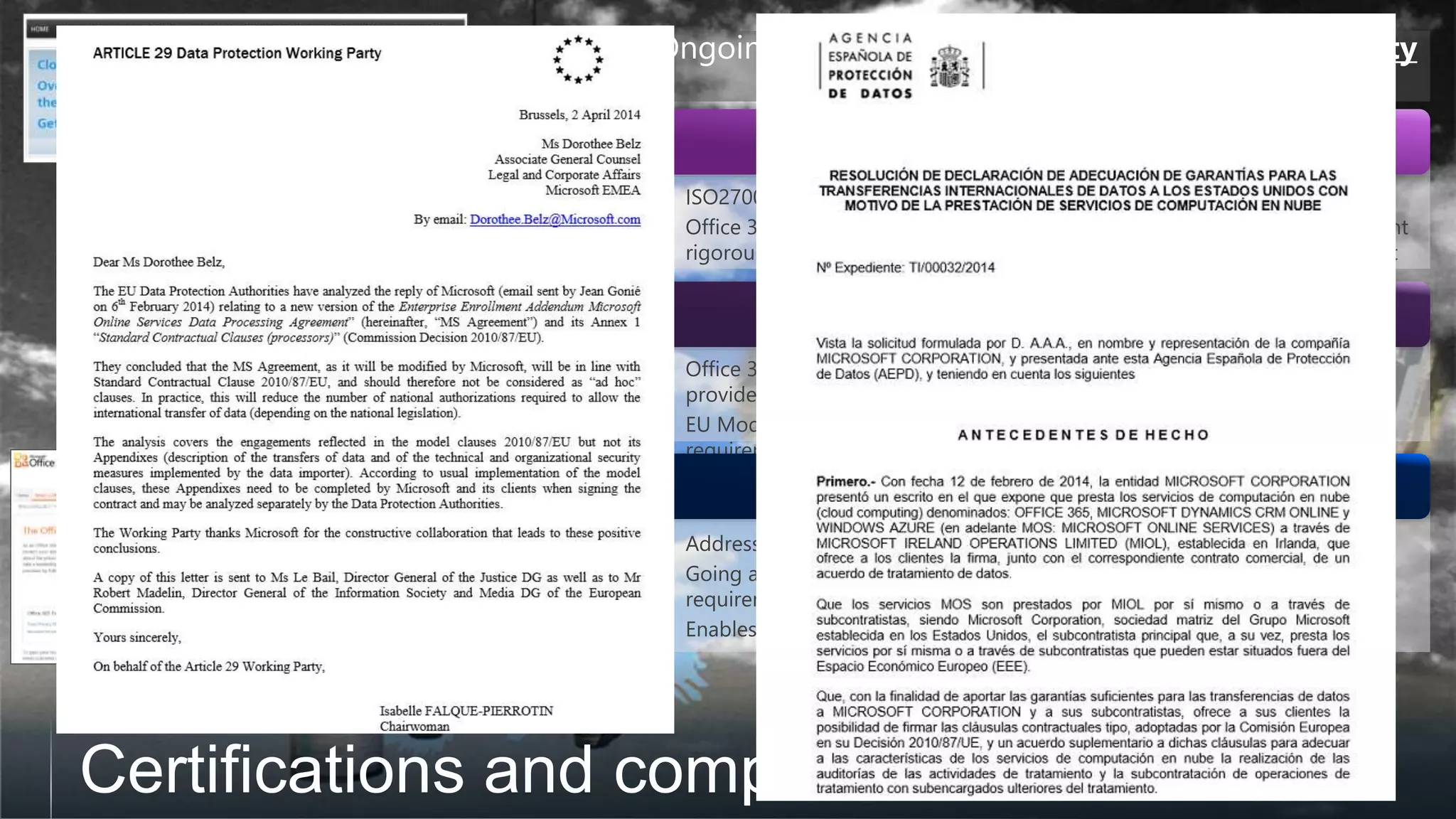

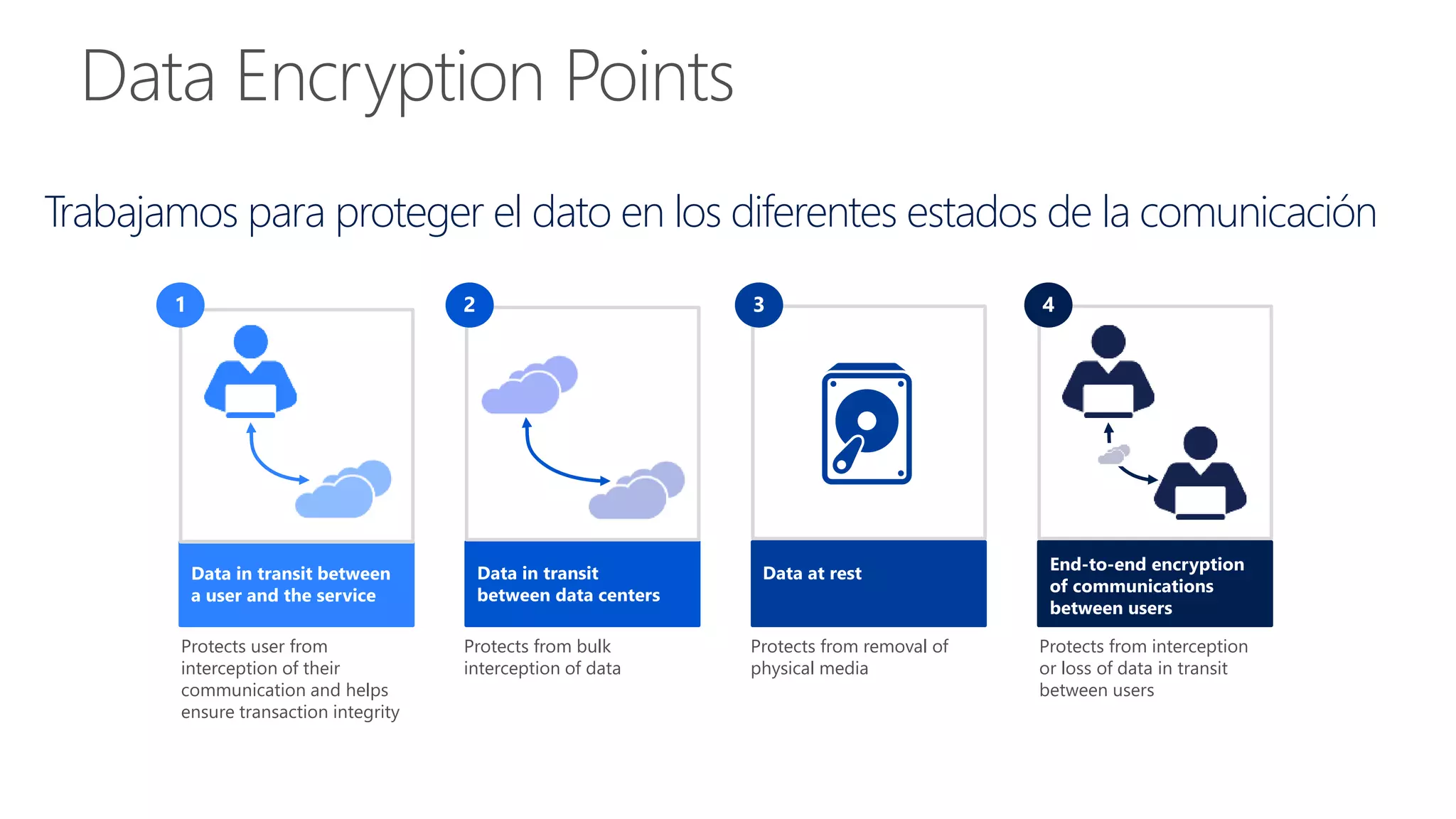


This document discusses cybersecurity and cloud computing. It summarizes that Microsoft is addressing privacy, security, and customer data handling with Office 365. Microsoft is signing EU Model Clauses with all customers and implementing rigorous ISO27001 security controls to enable customers to comply with local regulations. The document also notes Microsoft is aggressively rolling out encryption of customer content between data centers and implementing Perfect Forward Secrecy to protect user communications from interception.












