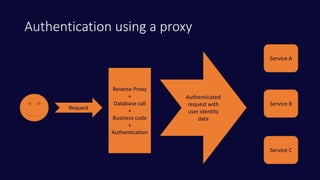
The document discusses various challenges in the microservice architecture, including issues related to authentication, communication, and configuration. It emphasizes the importance of a robust system for managing services and highlights tools such as message brokers and event sourcing that can aid in this process. The author also advocates for a developer-centric approach to architecture, encouraging agility and innovation in software design.