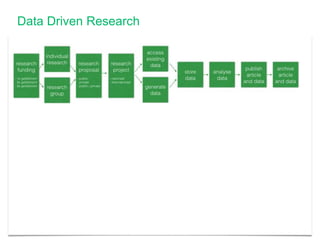
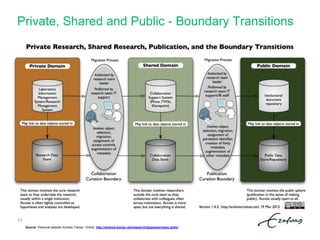
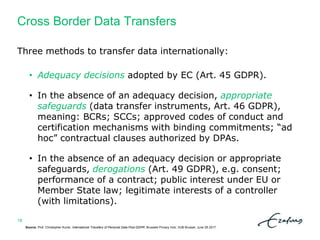
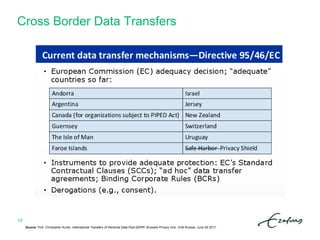
The document outlines a summer school itinerary focused on privacy and data protection in research, exploring rights and responsibilities, GDPR principles, and privacy-enhancing technologies. Key topics include the balance between researchers' interests and individual privacy rights, data protection impact assessments, and cross-border data transfer methods. It emphasizes the importance of compliance with legal standards while promoting ethical research practices.




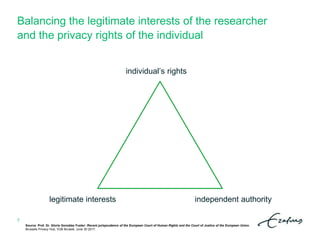
![Balancing the legitimate interests of the researcher
and the privacy rights of the individual
Source: Brendan Van Alsenoy (Belgian Privacy Commission), Balancing the interests of controllers and the rights of the data subject.
Brussels Privacy Hub, VUB Brussel, June 30 2017.
5
“The right to the protection of personal data is not an absolute
right; it must be considered in relation to its function in society
and be balanced against other fundamental rights,
in accordance with the principle of proportionality.”
Recital (4) GDPR
“processing is necessary for the purposes of the legitimate
interests pursued by the controller or by a third party, except
where such interests are overridden by the interests or
fundamental rights and freedoms of the data subject […]”
Article 6(1)f GDPR](https://image.slidesharecdn.com/summerschoolerasmusmcmdomingusjuly2017-170712152805/85/Privacy-and-Data-Protection-in-Research-5-320.jpg)