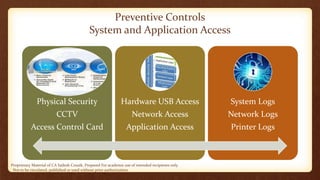
The document outlines key aspects of fraud prevention, including identifying potential threats and fraudster profiles, as well as discussing the motivators behind fraud and sector-specific vulnerabilities. It emphasizes the importance of preventive controls, continuous monitoring, and creating awareness within organizations. Additionally, it highlights analysis of fraud cases, profiles of fraudsters and victims, and the need for established processes in recruitment and vendor selection to mitigate risks.