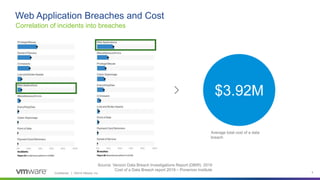
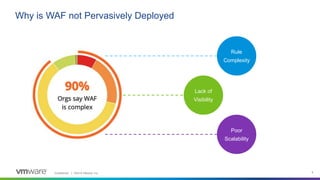
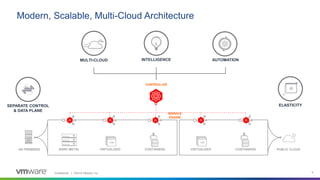
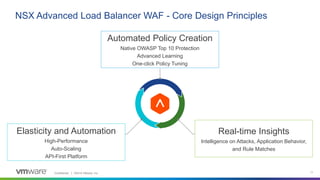
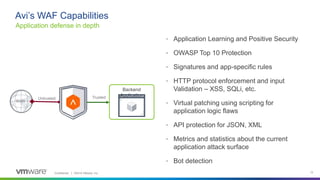
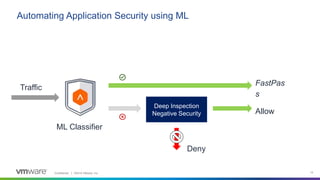
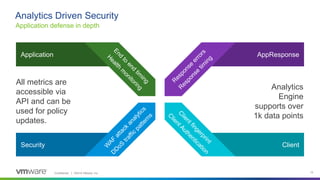
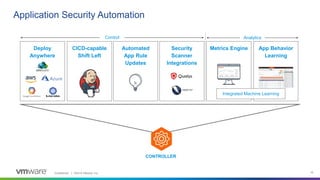
This webinar discusses how analytics-driven web application firewalls can help prevent threats. It covers why application security has become critical due to widespread data breaches. The webinar demonstrates NSX Advanced Load Balancer's web application firewall capabilities, including automated policy creation, advanced learning, and real-time insights. It also discusses a customer success story where NSX Advanced Load Balancer helped a lottery company reduce costs and simplify operations through elastic scaling and security analytics.