Presant
•
0 likes•292 views
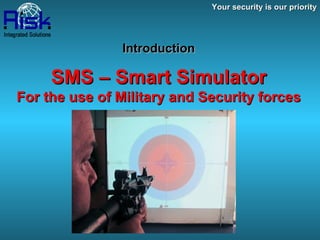
The document describes an SMS (Smart Simulator) system that provides simulated firearms training for military and security forces using a laser, camera, projector, and software. The SMS system allows up to 4 trainees to conduct motion, technical, tactical, and video drills on a projected firing range from 1-20 meters without live ammunition for training purposes under friendly control and monitoring of operations and data.
Report
Share
Report
Share
Recommended
Safe system-flyer

This innovative new system is now available from Dukane.
You can see a video on it here :
http://www.slideshare.net/DukaneAVMarketing/cnn-features-safe-system
For more information contact:
Delia Valdez
Dukane Customer Service Representative
Phone: 800-676-2485
Fax: (630) 584-5156
Email; avsales@dukane.com
Website: www.Dukane.com/AV
Dukane AV
2900 Dukane Drive
St. Charles, IL 60174
Info on Dukane’s Classroom/Audience Reponse system can be found at :
Convey Website: www.conveyclassrooms.com
Recommended
Safe system-flyer

This innovative new system is now available from Dukane.
You can see a video on it here :
http://www.slideshare.net/DukaneAVMarketing/cnn-features-safe-system
For more information contact:
Delia Valdez
Dukane Customer Service Representative
Phone: 800-676-2485
Fax: (630) 584-5156
Email; avsales@dukane.com
Website: www.Dukane.com/AV
Dukane AV
2900 Dukane Drive
St. Charles, IL 60174
Info on Dukane’s Classroom/Audience Reponse system can be found at :
Convey Website: www.conveyclassrooms.com
Security threats to mobile multimedia applications camera based attacks on mo...

Security threats to mobile multimedia applications camera based attacks on mo...JPINFOTECH JAYAPRAKASH
The Places of Our Lives: Visiting Patterns and Automatic Labeling from Longitudinal Smartphone Data
ABSTRACT:
The location tracking functionality of modern mobile devices provides unprecedented opportunity to the understanding of individual mobility in daily life. Instead of studying raw geographic coordinates, we are interested in understanding human mobility patterns based on sequences of place visits which encode, at a coarse resolution, most daily activities. This paper presents a study on place characterization in people’s everyday life based on data recorded continuously by smartphones. First, we study human mobility from sequences of place visits, including visiting patterns on different place categories. Second, we address the problem of automatic place labeling from smartphone data without using any geo-location information. Our study on a large-scale data collected from 114 smartphone users over 18 months confirm many intuitions, and also reveals findings regarding both regularly and novelty trends in visiting patterns. Considering the problem of place labeling with 10 place categories, we show that frequently visited places can be recognized reliably (over 80 percent) while it is much more challenging to recognize infrequent places.
8 WAYS TO PROTECT THE DATA IN YOUR OFFICE: #3 Trust in your office solutions

Not all devices offer the same level of protection for your networks or the data that exits in your office.
PLN9 Surveillance

PLN9 SurveillancePLN9 Security Services
Total security solutions for Manned Guarding & Electronic Security with Tyco.
Manned Guarding, Event Management, Industrial Security, Mall Security, Hotel Security, Building Management.
Electronic Security- Distributor of Tyco Fire Products & Tyco Security Products.
ICT Security with Automation

ICT Smart Building Solution is an integrated solution of Security and Automation.
Cybersecurity Applied to Embedded Systems, Fundamentals of Embedded Systems a...

An embedded system is a microprocessor-based computer hardware system with software designed to perform dedicated functions, either as an independent system or as a part of a large system. The core is an integrated circuit designed to perform real-time operation calculations.
Embedded systems use tailored operating systems or language platforms, especially where a real-time operating environment must be provided. With higher-level chip functions (such as those in SoCs), designers increasingly decide that systems are usually fast enough and can withstand subtle changes in response time, so real-time methods are suitable. In these cases, a streamlined version of the Linux operating system is usually deployed
Ways to prevent cyber-attacks on embedded systems:
Expect firmware to be updated regularly
integration with third-party security management systems
Secure communication
Limit access to embedded systems to a need-to-use basis
Tonex offers "Cybersecurity Applied to Embedded Systems, Cybersecurity Training"
Learn about the basics of embedded systems and network security applications to illustrate unique vulnerabilities that are commonly exploited. Methods and techniques to consider cyber security measures in the entire system life cycle and acquisition process.
Learn About:
Risk assessment methodologies
Failure analysis and using defensive tools to mitigate cyber risk and vulnerabilities
Weapon systems, missiles, smart weapons
Network Enabled Weapons (NEW)
UAVs, Communications systems
Industrial control systems
medical devices, robotics, smart grid
SCADA, Intelligent Electronic Devices (IED), PLCs
Learning Objectives:
Examining how to fit cybersecurity in embedded systems
Fundamentals of cybersecurity
Fundamentals of Embedded Systems
Fundamentals of embedded system product design cycle, project management, design for production, V&V and O&M
Embedded Systems Security Requirements
Fundamentals of hardware and firmware analysis and design in embedded design
Vulnerabilities in embedded systems
Embedded hardware and firmware analysis
Foundation knowledge of cyber security threats, risks, mitigation strategies applied to embedded systems
And many more..
Audience
Product/process designers and engineers
Developers working with embedded systems
Information security professionals
Application developers
Course Outline
Cybersecurity 101
Introduction to Embedded Systems
Embedded System Vulnerability Analysis
Exploiting Real Time Operating Systems
Securing Embedded Systems Interfaces and Protocols
Cybersecurity Attacks and Best Mitigation Practices for Embedded Systems
Case Study and Workshop
Learn More:
https://www.tonex.com/cybersecurity-applied-to-embedded-systems-cybersecurity-training/
Internettrendsv1 150526193103-lva1-app6892

KPCB’s Mary Meeker presents the 2015 Internet Trends report, 20 years after the inaugural “The Internet Report” was first published in 1995. Since then, the number of Internet users has risen from 35 million in 1995 to more than 2.8 billion today. The 2015 report looks at key Internet trends globally – while still healthy Internet user and smartphone subscription growth continue to slow, Internet engagement continues to rise led by consumers spending more time on their mobile devices, where they can be connected 24/7. Mobile advertising still has headroom to expand and new innovations around ad formats and buy buttons should prove compelling for consumers and businesses.
Chinese Trademark Violations

As it stands today, the Chinese are copying every possible brand and trademark, some with license but most of them just by inserting minor changes in the brands name and logo.
More Related Content
What's hot
Security threats to mobile multimedia applications camera based attacks on mo...

Security threats to mobile multimedia applications camera based attacks on mo...JPINFOTECH JAYAPRAKASH
The Places of Our Lives: Visiting Patterns and Automatic Labeling from Longitudinal Smartphone Data
ABSTRACT:
The location tracking functionality of modern mobile devices provides unprecedented opportunity to the understanding of individual mobility in daily life. Instead of studying raw geographic coordinates, we are interested in understanding human mobility patterns based on sequences of place visits which encode, at a coarse resolution, most daily activities. This paper presents a study on place characterization in people’s everyday life based on data recorded continuously by smartphones. First, we study human mobility from sequences of place visits, including visiting patterns on different place categories. Second, we address the problem of automatic place labeling from smartphone data without using any geo-location information. Our study on a large-scale data collected from 114 smartphone users over 18 months confirm many intuitions, and also reveals findings regarding both regularly and novelty trends in visiting patterns. Considering the problem of place labeling with 10 place categories, we show that frequently visited places can be recognized reliably (over 80 percent) while it is much more challenging to recognize infrequent places.
8 WAYS TO PROTECT THE DATA IN YOUR OFFICE: #3 Trust in your office solutions

Not all devices offer the same level of protection for your networks or the data that exits in your office.
PLN9 Surveillance

PLN9 SurveillancePLN9 Security Services
Total security solutions for Manned Guarding & Electronic Security with Tyco.
Manned Guarding, Event Management, Industrial Security, Mall Security, Hotel Security, Building Management.
Electronic Security- Distributor of Tyco Fire Products & Tyco Security Products.
ICT Security with Automation

ICT Smart Building Solution is an integrated solution of Security and Automation.
Cybersecurity Applied to Embedded Systems, Fundamentals of Embedded Systems a...

An embedded system is a microprocessor-based computer hardware system with software designed to perform dedicated functions, either as an independent system or as a part of a large system. The core is an integrated circuit designed to perform real-time operation calculations.
Embedded systems use tailored operating systems or language platforms, especially where a real-time operating environment must be provided. With higher-level chip functions (such as those in SoCs), designers increasingly decide that systems are usually fast enough and can withstand subtle changes in response time, so real-time methods are suitable. In these cases, a streamlined version of the Linux operating system is usually deployed
Ways to prevent cyber-attacks on embedded systems:
Expect firmware to be updated regularly
integration with third-party security management systems
Secure communication
Limit access to embedded systems to a need-to-use basis
Tonex offers "Cybersecurity Applied to Embedded Systems, Cybersecurity Training"
Learn about the basics of embedded systems and network security applications to illustrate unique vulnerabilities that are commonly exploited. Methods and techniques to consider cyber security measures in the entire system life cycle and acquisition process.
Learn About:
Risk assessment methodologies
Failure analysis and using defensive tools to mitigate cyber risk and vulnerabilities
Weapon systems, missiles, smart weapons
Network Enabled Weapons (NEW)
UAVs, Communications systems
Industrial control systems
medical devices, robotics, smart grid
SCADA, Intelligent Electronic Devices (IED), PLCs
Learning Objectives:
Examining how to fit cybersecurity in embedded systems
Fundamentals of cybersecurity
Fundamentals of Embedded Systems
Fundamentals of embedded system product design cycle, project management, design for production, V&V and O&M
Embedded Systems Security Requirements
Fundamentals of hardware and firmware analysis and design in embedded design
Vulnerabilities in embedded systems
Embedded hardware and firmware analysis
Foundation knowledge of cyber security threats, risks, mitigation strategies applied to embedded systems
And many more..
Audience
Product/process designers and engineers
Developers working with embedded systems
Information security professionals
Application developers
Course Outline
Cybersecurity 101
Introduction to Embedded Systems
Embedded System Vulnerability Analysis
Exploiting Real Time Operating Systems
Securing Embedded Systems Interfaces and Protocols
Cybersecurity Attacks and Best Mitigation Practices for Embedded Systems
Case Study and Workshop
Learn More:
https://www.tonex.com/cybersecurity-applied-to-embedded-systems-cybersecurity-training/
What's hot (12)
Security threats to mobile multimedia applications camera based attacks on mo...

Security threats to mobile multimedia applications camera based attacks on mo...
Vutlan presentation 09.2015 EN - Shamal Abeyrathne

Vutlan presentation 09.2015 EN - Shamal Abeyrathne
8 WAYS TO PROTECT THE DATA IN YOUR OFFICE: #3 Trust in your office solutions

8 WAYS TO PROTECT THE DATA IN YOUR OFFICE: #3 Trust in your office solutions
Cybersecurity Applied to Embedded Systems, Fundamentals of Embedded Systems a...

Cybersecurity Applied to Embedded Systems, Fundamentals of Embedded Systems a...
Intrusion Detection & Electronic Surveillance For Security

Intrusion Detection & Electronic Surveillance For Security
Viewers also liked
Internettrendsv1 150526193103-lva1-app6892

KPCB’s Mary Meeker presents the 2015 Internet Trends report, 20 years after the inaugural “The Internet Report” was first published in 1995. Since then, the number of Internet users has risen from 35 million in 1995 to more than 2.8 billion today. The 2015 report looks at key Internet trends globally – while still healthy Internet user and smartphone subscription growth continue to slow, Internet engagement continues to rise led by consumers spending more time on their mobile devices, where they can be connected 24/7. Mobile advertising still has headroom to expand and new innovations around ad formats and buy buttons should prove compelling for consumers and businesses.
Chinese Trademark Violations

As it stands today, the Chinese are copying every possible brand and trademark, some with license but most of them just by inserting minor changes in the brands name and logo.
Space Efficient Kitchens 

Those kitchen were specially designed for small apartments in congested big cities where every meter counts.
DGP Woodworks

We provide the off-site availability of quality wood products for residential and commercial construction projects.
Our products include:
• Door / Window Frames & Shutters
• Wardrobe Frames & Shutters
• Architraves and Skirting
• Hardwood Flooring
• Cabinetry
• Staircases
• Pergolas
• Balconies
• Home Products
The Stockholm Metro

Stockholm's metro, referred to, sometimes, as "The world's longest gallery", is an amazing example of unification of urban life and art.
Viewers also liked (20)
Karavīru dienasgrāmatas Otrajā pasaules karā: faktoloģisks fiksējums un 'dvēs...

Karavīru dienasgrāmatas Otrajā pasaules karā: faktoloģisks fiksējums un 'dvēs...
Развертывание и управление CMS Drupal в Microsoft Azure

Развертывание и управление CMS Drupal в Microsoft Azure
Similar to Presant
AMI Security 101 - Smart Grid Security East 2011

This is the slide deck from the Smart Grid Security East 2011 pre-conference workshop (www.smartgridsecurityeast.com)
Kith Infotech

We Serve Industry since last 14 years,having 3000+ satisfied customers and offer world class products atcompetitive price.
Huneed-Cisco Perimeter Security Solution Guide

Perimeter security solution guide created between Huneed and Cisco
CCTV Surveillance System Including Sensor For Infrastructure Protection

CCTV Surveillance System Including Sensor For Infrastructure ProtectionNeometrix_Engineering_Pvt_Ltd
The IPS (Infrastructure protection system)- Perimeter Security & Intrusion Detection System along with integrated Security Surveillance System. This IPS comprises of following Sub Systems:-
(i) Perimeter intrusion Detection System (PIDS)
(ii) PIDS Software and Sensors ( Vibration, Proximity, beam etc.)
(iii) Network IP camera
(iv) Common Accessories
(v) Cable – Outdoor UV Protected
(vi) AC Power Supply
(vii) IT System
(viii) IT Accessories
(ix) Power Accessories
(x) Site Accessories
(xi) Switches
(xii) Video Management System (VMS)
(xiii) Command & Control Software
(xiv) UPS
Study of campus network security

this is latest seminar topic which can be taken up and can future improve to make even better
Keeping up with the security features

As we discovered in our whitepaper, “The Human Face of The Global Security Industry,” ( https://bit.ly/2RicjfR ) the prevalence of electronic security has undoubtedly increased over the past couple of years. One of the contributing factors for this change was the decreasing cost of hardware and software resources. With rising crime rates, citizens and security service providers have collaboratively worked towards creating a safer environment. Amidst all the transformations in electronic security, one might be curious to understand what goes on behind the scenes during the remote guarding process.
CCTV solutions and trends about security settings

This is part of a large project to design trends and future needs. In this sub-project has been analyzed methodologies, value and rule of targets in order to create a continuum between assessment plan, project and heterogeneous rules defined by Facility Manager, IT Manager and Security Manager.
The journey to ICS - Extended 

This presentation was given at BSides Las Vegas 2015.
The modern times that we live in, the gentle shift that we are making towards the Internet of Things (IoT) is slowly but surely getting a grip on our day to day lives. The same goes for securing our Industrial Control Systems (ICS). We see that the demand for ICS security is raising and governmental regulations are being established and implement. However, this also means that the need for ICS security professionals is raising as well. More and more security professionals/firms are starting to perform security assessments such as penetration testing on an ICS level. Two years ago I got the question if I was up for the challenge, converting myself from a ‘normal’ security professional to a ICS specific security professional.
The purpose of this talk would be to provide a starting point for security professionals that want to make the shift towards ICS Security, just like I did two years ago. While the term starting point might be a bit misleading, the goal would be to provide an ICS 001 talk instead in contrast to an ICS 101 talk.
Similar to Presant (20)
CCTV Surveillance System Including Sensor For Infrastructure Protection

CCTV Surveillance System Including Sensor For Infrastructure Protection
More from riskis
More from riskis (20)
Recently uploaded
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
ODC, Data Fabric and Architecture User Group

Let's dive deeper into the world of ODC! Ricardo Alves (OutSystems) will join us to tell all about the new Data Fabric. After that, Sezen de Bruijn (OutSystems) will get into the details on how to best design a sturdy architecture within ODC.
When stars align: studies in data quality, knowledge graphs, and machine lear...

Keynote at DQMLKG workshop at the 21st European Semantic Web Conference 2024
Connector Corner: Automate dynamic content and events by pushing a button

Here is something new! In our next Connector Corner webinar, we will demonstrate how you can use a single workflow to:
Create a campaign using Mailchimp with merge tags/fields
Send an interactive Slack channel message (using buttons)
Have the message received by managers and peers along with a test email for review
But there’s more:
In a second workflow supporting the same use case, you’ll see:
Your campaign sent to target colleagues for approval
If the “Approve” button is clicked, a Jira/Zendesk ticket is created for the marketing design team
But—if the “Reject” button is pushed, colleagues will be alerted via Slack message
Join us to learn more about this new, human-in-the-loop capability, brought to you by Integration Service connectors.
And...
Speakers:
Akshay Agnihotri, Product Manager
Charlie Greenberg, Host
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head of Product, Amazon Games
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on the notifications, alerts, and approval requests using Slack for Bonterra Impact Management. The solutions covered in this webinar can also be deployed for Microsoft Teams.
Interested in deploying notification automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
"Impact of front-end architecture on development cost", Viktor Turskyi

I have heard many times that architecture is not important for the front-end. Also, many times I have seen how developers implement features on the front-end just following the standard rules for a framework and think that this is enough to successfully launch the project, and then the project fails. How to prevent this and what approach to choose? I have launched dozens of complex projects and during the talk we will analyze which approaches have worked for me and which have not.
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

As AI technology is pushing into IT I was wondering myself, as an “infrastructure container kubernetes guy”, how get this fancy AI technology get managed from an infrastructure operational view? Is it possible to apply our lovely cloud native principals as well? What benefit’s both technologies could bring to each other?
Let me take this questions and provide you a short journey through existing deployment models and use cases for AI software. On practical examples, we discuss what cloud/on-premise strategy we may need for applying it to our own infrastructure to get it to work from an enterprise perspective. I want to give an overview about infrastructure requirements and technologies, what could be beneficial or limiting your AI use cases in an enterprise environment. An interactive Demo will give you some insides, what approaches I got already working for real.
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

The IoT and OT threat landscape report has been prepared by the Threat Research Team at Sectrio using data from Sectrio, cyber threat intelligence farming facilities spread across over 85 cities around the world. In addition, Sectrio also runs AI-based advanced threat and payload engagement facilities that serve as sinks to attract and engage sophisticated threat actors, and newer malware including new variants and latent threats that are at an earlier stage of development.
The latest edition of the OT/ICS and IoT security Threat Landscape Report 2024 also covers:
State of global ICS asset and network exposure
Sectoral targets and attacks as well as the cost of ransom
Global APT activity, AI usage, actor and tactic profiles, and implications
Rise in volumes of AI-powered cyberattacks
Major cyber events in 2024
Malware and malicious payload trends
Cyberattack types and targets
Vulnerability exploit attempts on CVEs
Attacks on counties – USA
Expansion of bot farms – how, where, and why
In-depth analysis of the cyber threat landscape across North America, South America, Europe, APAC, and the Middle East
Why are attacks on smart factories rising?
Cyber risk predictions
Axis of attacks – Europe
Systemic attacks in the Middle East
Download the full report from here:
https://sectrio.com/resources/ot-threat-landscape-reports/sectrio-releases-ot-ics-and-iot-security-threat-landscape-report-2024/
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

91mobiles recently conducted a Smart TV Buyer Insights Survey in which we asked over 3,000 respondents about the TV they own, aspects they look at on a new TV, and their TV buying preferences.
Knowledge engineering: from people to machines and back

Keynote at the 21st European Semantic Web Conference
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
UiPath Test Automation using UiPath Test Suite series, part 3

Welcome to UiPath Test Automation using UiPath Test Suite series part 3. In this session, we will cover desktop automation along with UI automation.
Topics covered:
UI automation Introduction,
UI automation Sample
Desktop automation flow
Pradeep Chinnala, Senior Consultant Automation Developer @WonderBotz and UiPath MVP
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
Recently uploaded (20)
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
When stars align: studies in data quality, knowledge graphs, and machine lear...

When stars align: studies in data quality, knowledge graphs, and machine lear...
Connector Corner: Automate dynamic content and events by pushing a button

Connector Corner: Automate dynamic content and events by pushing a button
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
"Impact of front-end architecture on development cost", Viktor Turskyi

"Impact of front-end architecture on development cost", Viktor Turskyi
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

State of ICS and IoT Cyber Threat Landscape Report 2024 preview
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf
Knowledge engineering: from people to machines and back

Knowledge engineering: from people to machines and back
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
UiPath Test Automation using UiPath Test Suite series, part 3

UiPath Test Automation using UiPath Test Suite series, part 3
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Presant
- 1. Your security is our priority Introduction SMS – Smart Simulator For the use of Military and Security forces
- 2. Your security is our priority System Parts Camera + basis Laser + batteries Barrel connector Trigger micro switch Computer software and speakers Projector with camera
- 3. Your security is our priority Laptop Projector screen / wall Cables Speakers Projector + IR camera Training range 1-20 m. System Configuration
- 4. Your security is our priority System calibration and weapon zeroing System calculate average hit point and software process the calibration
- 5. Your security is our priority Friendly control on operation and data
- 6. Your security is our priority 1-4 trainees
- 7. Your security is our priority On motion drills
- 8. Your security is our priority Technical drills
- 9. Your security is our priority Tactical drills
- 10. Your security is our priority Graphic firing range drills
- 11. Your security is our priority Video realistic drills
- 12. Your security is our priority SMS – allow firing training to every end user