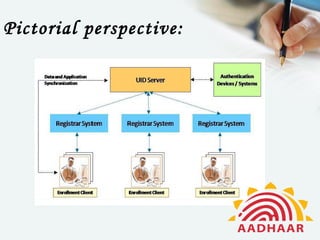
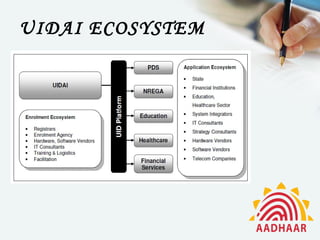
Aadhaar is a 12-digit unique identification number issued by UIDAI for Indian residents, aimed at reducing identity fraud and enhancing service access. The document discusses the projected benefits of Aadhaar, including streamlined identity verification and increased financial inclusion, while also highlighting potential risks such as hacking and corruption. Proposed security measures include strict information classification, encryption, and rigorous employee protocols to protect sensitive data.