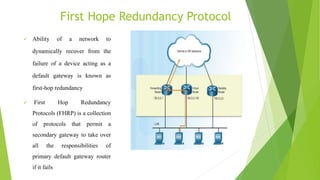
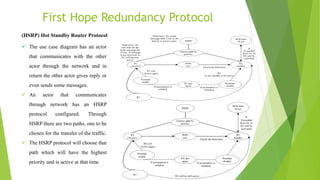
The document discusses network flow optimization through first hop redundancy protocols (FHRPs) like HSRP, VRRP, and GLBP, highlighting their role in minimizing packet loss and improving network reliability. It evaluates these protocols using GNS3 for simulation, comparing their performance metrics such as packet loss, CPU utilization, and authentication methods like MD5. The conclusion asserts that GLBP is superior in resource utilization and load balancing, with MD5 enhancing the security of FHRPs.







![Protocols Packet
Size
CPU
utilization (%)
Convergence
duration
[second]
Bandwidth
Utilization
[Kbps]
HSRP 100 0.69 8.056 0-1
VRRP 68 1.06 9.934 0-1
GLBP 108 0.54 7.344 0-1
Protocols Packet
Size
CPU
utilization (%)
Convergence
duration
[second]
Bandwidth
Utilization
[Kbps]
HSRP 100 1.78 3.564 0-3
VRRP 68 2.15 7.935 0-3
GLBP 108 1.62 2.983 0-3
COMPARISION RESULTS AND DISCUSSIONS
Comparison of HSRP, VRRP and GLBP by using
default values of hold time, priority, preempt and
‘Hello’ time
test was performed by setting priority value 215,
hold time to 6 seconds and rest to be the same. The
output we got from this test is shown](https://image.slidesharecdn.com/pptusman-240621061724-dd1110c0/85/PPT-network-protocol-First-hope-redundancy-protocol-pptx-12-320.jpg)







