Poster-A4
•
0 likes•90 views
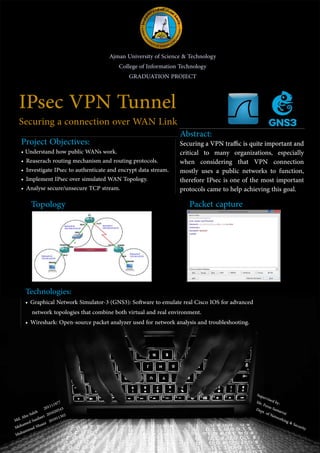
This document outlines a graduation project to understand how public WANs work, research routing protocols and IPsec, implement an IPsec VPN over a simulated WAN topology, and analyze secure and unsecure TCP streams. The project will use GNS3 to emulate Cisco IOS and create a graphical network simulator combining virtual and real environments, along with Wireshark for network analysis and troubleshooting. The abstract indicates that securing VPN tunnels is important for organizations using public networks, and that IPsec is a key protocol for achieving security goals when connecting over WAN links.
Report
Share
Report
Share
Download to read offline
Recommended
A secure scheme against power exhausting

HEAD OFFICE (CHENNAI):
JP INFOTECH,
Old No. 31, New No: 86, 1st Floor, 1st Avenue,
Ashok Nagar (Ashok Pillar),
Chennai – 83.
Landmark: Next to Kotak Mahendra Bank / Bharath Scans
MOBILE: (0)9952649690
LANDLINE: (044) 43012642
E-MAIL: jpinfotechprojects@gmail.com
PUDUCHERRY / PONDICHERRY OFFICE:
JP INFOTECH,
#45, Kamaraj Salai, Thattanchavady,
Pondy-Tindivanam High Road,
Puducherry/Pondicherry – 605009.
Landmark: Opp. To Thattanchavady Industrial Estate and Next to VVP Nagar Arch.
MOBILE: (0)9952649690 / (0) 8608600246
LANDLINE: (0413)4300535
E-MAIL: jpinfotechprojects@gmail.com
Detection and localization of multiple spoofing attacks in

REAL TIME PROJECTS
IEEE BASED PROJECTS
EMBEDDED SYSTEMS
PAPER PUBLICATIONS
MATLAB PROJECTS
targetjsolutions@gmail.com
(0)9611582234, (0)9945657526
Network Simulation Tools Projects

MAJOR USES OF NETWORK SIMULATION TOOLS
INNOVATIVE TOPICS IN SIMULATION TOOLS
SIGNIFICANCE OF NETWORK SIMULATION TOOLS
Recommended
A secure scheme against power exhausting

HEAD OFFICE (CHENNAI):
JP INFOTECH,
Old No. 31, New No: 86, 1st Floor, 1st Avenue,
Ashok Nagar (Ashok Pillar),
Chennai – 83.
Landmark: Next to Kotak Mahendra Bank / Bharath Scans
MOBILE: (0)9952649690
LANDLINE: (044) 43012642
E-MAIL: jpinfotechprojects@gmail.com
PUDUCHERRY / PONDICHERRY OFFICE:
JP INFOTECH,
#45, Kamaraj Salai, Thattanchavady,
Pondy-Tindivanam High Road,
Puducherry/Pondicherry – 605009.
Landmark: Opp. To Thattanchavady Industrial Estate and Next to VVP Nagar Arch.
MOBILE: (0)9952649690 / (0) 8608600246
LANDLINE: (0413)4300535
E-MAIL: jpinfotechprojects@gmail.com
Detection and localization of multiple spoofing attacks in

REAL TIME PROJECTS
IEEE BASED PROJECTS
EMBEDDED SYSTEMS
PAPER PUBLICATIONS
MATLAB PROJECTS
targetjsolutions@gmail.com
(0)9611582234, (0)9945657526
Network Simulation Tools Projects

MAJOR USES OF NETWORK SIMULATION TOOLS
INNOVATIVE TOPICS IN SIMULATION TOOLS
SIGNIFICANCE OF NETWORK SIMULATION TOOLS
36

For further details contact:
N.RAJASEKARAN B.E M.S 9841091117,9840103301.
IMPULSE TECHNOLOGIES,
Old No 251, New No 304,
2nd Floor,
Arcot road ,
Vadapalani ,
Chennai-26.
www.impulse.net.in
Email: ieeeprojects@yahoo.com/ imbpulse@gmail.com
PhD Thesis NS2 Projects

KEY NOTES ON MANET ATTACKS
PARAMETERS OF THESIS WRITING
SIGNIFICANCE OF WSN ATTACKS
52

For further details contact:
N.RAJASEKARAN B.E M.S 9841091117,9840103301.
IMPULSE TECHNOLOGIES,
Old No 251, New No 304,
2nd Floor,
Arcot road ,
Vadapalani ,
Chennai-26.
www.impulse.net.in
Email: ieeeprojects@yahoo.com/ imbpulse@gmail.com
Postgraduate Projects in NS2

FOREMOST CONCEPTS IN NS2 PROJECTS
SIGNIFICANT COMPONENTS IN NS2 PROJECTS
VALUABLE APPLICATIONS IN NS2 PROJECTS
Kracking WPA2

This paper performs an in-depth analysis of the functionality of WPA2 and the Key Reinstallation Attack, announced in early November. Both forms of the attack, the 4-way handshake and the group key exploit are explained in brief detail so as to fasciliate an understanding of the processes involveds, leading into a discussion on the potential implications that this will have on a few connected areas such as BYOD policies, IoT and the Android ecosystem. A test is also conducted on an Android Phone which proves the testing mechanisms provided, and that without updated security patches for both clients and access points, the exploit is a threat.
How to hack wireless internet connections using aircrack-ng

I use this presentation slide on the "Presentation Progrm" organized by Diploma-Acme Engineering College.
Blackhole Attack Network Project Topics

Top 5 Blackhole Prevention Methods
Notable Modules in Blackhole Attack Network Projects
Fundamental Types of Blackhole Attack Network Projects
Network Engineering Projects in NS3

PROMINENT FEATURES IN NS3 PROJECTS
NOTABLE PACKETS IN NS3 PROJECTS
SIGNIFICANT FIELDS IN NS3 PROJECTS
containing byzantine failures with control zones

At Softroniics we provide job oriented training for freshers in IT sector. We are providing IEEE project guidance and Final year project guidance. We are Pioneers in all leading technologies like Android, Java, .NET, PHP, Python, Embedded Systems, Matlab, NS2, VLSI, Modelsim, Tanner, Xilinx etc. We are specializiling in technologies like Big Data, Cloud Computing, Internet Of Things (iOT), Data Mining, Networking, Information Security, Image Processing and many other. We are providing long term and short term internship also. We are also providing IEEE project support at Calicut, Thrissur and Palakkad. For more details contact 9037291113, 7907435072
More Related Content
What's hot
36

For further details contact:
N.RAJASEKARAN B.E M.S 9841091117,9840103301.
IMPULSE TECHNOLOGIES,
Old No 251, New No 304,
2nd Floor,
Arcot road ,
Vadapalani ,
Chennai-26.
www.impulse.net.in
Email: ieeeprojects@yahoo.com/ imbpulse@gmail.com
PhD Thesis NS2 Projects

KEY NOTES ON MANET ATTACKS
PARAMETERS OF THESIS WRITING
SIGNIFICANCE OF WSN ATTACKS
52

For further details contact:
N.RAJASEKARAN B.E M.S 9841091117,9840103301.
IMPULSE TECHNOLOGIES,
Old No 251, New No 304,
2nd Floor,
Arcot road ,
Vadapalani ,
Chennai-26.
www.impulse.net.in
Email: ieeeprojects@yahoo.com/ imbpulse@gmail.com
Postgraduate Projects in NS2

FOREMOST CONCEPTS IN NS2 PROJECTS
SIGNIFICANT COMPONENTS IN NS2 PROJECTS
VALUABLE APPLICATIONS IN NS2 PROJECTS
Kracking WPA2

This paper performs an in-depth analysis of the functionality of WPA2 and the Key Reinstallation Attack, announced in early November. Both forms of the attack, the 4-way handshake and the group key exploit are explained in brief detail so as to fasciliate an understanding of the processes involveds, leading into a discussion on the potential implications that this will have on a few connected areas such as BYOD policies, IoT and the Android ecosystem. A test is also conducted on an Android Phone which proves the testing mechanisms provided, and that without updated security patches for both clients and access points, the exploit is a threat.
How to hack wireless internet connections using aircrack-ng

I use this presentation slide on the "Presentation Progrm" organized by Diploma-Acme Engineering College.
Blackhole Attack Network Project Topics

Top 5 Blackhole Prevention Methods
Notable Modules in Blackhole Attack Network Projects
Fundamental Types of Blackhole Attack Network Projects
Network Engineering Projects in NS3

PROMINENT FEATURES IN NS3 PROJECTS
NOTABLE PACKETS IN NS3 PROJECTS
SIGNIFICANT FIELDS IN NS3 PROJECTS
containing byzantine failures with control zones

At Softroniics we provide job oriented training for freshers in IT sector. We are providing IEEE project guidance and Final year project guidance. We are Pioneers in all leading technologies like Android, Java, .NET, PHP, Python, Embedded Systems, Matlab, NS2, VLSI, Modelsim, Tanner, Xilinx etc. We are specializiling in technologies like Big Data, Cloud Computing, Internet Of Things (iOT), Data Mining, Networking, Information Security, Image Processing and many other. We are providing long term and short term internship also. We are also providing IEEE project support at Calicut, Thrissur and Palakkad. For more details contact 9037291113, 7907435072
What's hot (18)
Wifi Security, or Descending into Depression and Drink

Wifi Security, or Descending into Depression and Drink
How to hack wireless internet connections using aircrack-ng

How to hack wireless internet connections using aircrack-ng
Dotnet detection and localization of multiple spoofing attackers in wireless...

Dotnet detection and localization of multiple spoofing attackers in wireless...
Viewers also liked
Teaching staff concerns about academic integrity

Presentation for the International Conference Plagiarism across Europe and Beyond.
12-13 June 2013
How to Effectively Communicate this Holiday Season with Stress in the Air

How to Effectively Communicate this Holiday Season with Stress in the AirThe Happiness Alliance - home of the Happiness Index
How to Effectively Communicate this Holiday Season with Stress in the Air is a tool in the Happiness Alliance @happycounts.org for your happiness, your communty's happiness and, through our work of listening and being heard, our nation's happiness. It includes four steps for talking and four steps for listening. Viewers also liked (14)
How to Effectively Communicate this Holiday Season with Stress in the Air

How to Effectively Communicate this Holiday Season with Stress in the Air
Similar to Poster-A4
Evaluation of mininet WiFi integration via ns-3

Mininet is a Linux-based network emulator that
is particularly widely used for Software Defined Network experiments,
due to its in-built support for OpenFlow switches.
However, Mininet currently lacks support for wireless links. A
recent work has addressed this limitation by using the realtime
feature of ns-3 to integrate the IEEE 802.11 channel
emulation feature with Mininet, which we refer to as Mininetns3-
WiFi. While this approach has great potential to serve as
an experimental platform, in particular for Software Defined
Wireless Networks, it has not been extensively evaluated in terms
of experiment result accuracy and fidelity. This is critical for any
system that integrates simulation with real-time components. In
this paper, we present a detailed evaluation of the fidelity of
experimental results of Mininet-ns3-WiFi. We further present
a reliable and low cost method that gives an experimenter an
indicator about the fidelity and trustworthiness of the results.
5G Core Network - ZTE 5g Cloude ServCore

5G Core Network - ZTE 5g Cloude ServCore
Presented by Zhijun Li
Botprobe - Reducing network threat intelligence big data 

Adrian Winckles,Cyber Lead & Director, Cyber Security & Networking Research Group https://dssitsec.eu
IRJET- A Survey of Working on Virtual Private Networks

https://www.irjet.net/archives/V6/i9/IRJET-V6I9203.pdf
IoT meets Big Data

ข้อมูล IoT จากอุปกรณ์มีปริมาณมาก และมีความไดนามิกต่อเนื่องตลอดเวลา มีหลายมิติ ทำอย่างไร จึงจะประมวผลได้เร็วและตอบสนองแบบทันทีทันได้ โดยใช้เครื่องมือ Streaming processing and bigdata analytics
Security Issues of 802.11b

Seminar Paper on Security Issues of 802.11b based on IEEE Whitepaper by Boland, H. and Mousavi, H., Carleton University, Ottawa, Ont., Canada, IEEE Canadian Conference on Electrical and Computer Engineering, 2-5 May 2004
International Journal of Engineering Research and Development (IJERD)

International Journal of Engineering Research and Development is an international premier peer reviewed open access engineering and technology journal promoting the discovery, innovation, advancement and dissemination of basic and transitional knowledge in engineering, technology and related disciplines.
summer training report on Computer network and Cisco packet tracer 

In this report... we study the concept of computer network designing with practical implementation
DCCN 2016 - Tutorial 2 - 4G for SmartGrid ecosystem

DCCN Tutorial C4: Implementation of 4G
cellular communication within the SmartGrid
ecosystem
Major presentation

This project aims at cracking the Wi-Fi security(WEP,WPA-personal).It basically includes
intrusion in a BSS(Basic Service Set),monitoring the traffic in air, manipulate SSIDs, get details
of clients on a particular SSID, sniffing the packets to & from them to Access point, creating a
false access point, detect hidden SSIDs etc.
Long term goal of the project (part of the project which will be implemented in next semester) is
that once the security is breached and we are able to communicate with the victim we will try to
take over the control of the victim’s system and try to manipulate the data in his system.
11172017 SafeAssign Originality Reporthttpswilmu.blac.docx

11/17/2017 SafeAssign Originality Report
https://wilmu.blackboard.com/webapps/mdb-sa-bb_bb60/originalityReport?attemptId=010cac5b-661a-4bb4-992e-f7813b0d363c&includeDeleted=true… 1/4
DEPT.SSC.SAFEASSIGN.... - SSC TUTORING - SAFEASSIGN FA2017
Draft SafeAssignment 13
Sushma Poreddy on Fri, Nov 17 2017, 11:21 AM
34% highest match
Submission ID: 010cac5b-661a-4bb4-992e-f7813b0d363c
Citations (8/8)
Running head: 1 WAN TECHNOLOGIES 1 WAN TECHNOLOGIES 5
WAN Technology Name Institution
2 POINT-TO-POINT WAN PROTOCOL IT IS ONE OF THE MOST COMMON
TYPES OF WAN CONNECTION THAT IS NOW BEING USED AROUND THE
Word Count: 677
Attachment ID: 188558880
week-4.docx
34%
1 Another student's paper
2 Another student's paper
3 Another student's paper
4 Another student's paper
5 http://netcert.tripod.com/ccna/wan/wan.html
6 Another student's paper
7 Another student's paper
8 Another student's paper
http://safeassign.blackboard.com/
https://wilmu.blackboard.com/webapps/mdb-sa-bb_bb60/originalityReportPrint?course_id=_448739_1&paperId=188558880&&attemptId=010cac5b-661a-4bb4-992e-f7813b0d363c&course_id=_448739_1
https://help.blackboard.com/SafeAssign
http://netcert.tripod.com/ccna/wan/wan.html
11/17/2017 SafeAssign Originality Report
https://wilmu.blackboard.com/webapps/mdb-sa-bb_bb60/originalityReport?attemptId=010cac5b-661a-4bb4-992e-f7813b0d363c&includeDeleted=true… 2/4
WORLD TODAY. It is often used for connecting LANs to various WAN service
providers. It is also employed by many organizations to connect LAN segments in their
network (Suo, Wan, Zou, & Liu, 2012). 2 THE POINT-TO-POINT CONNECTION
BETWEEN A LAN TO WAN IS ALSO SOMETIMES REFERRED TO AS A
LEASED LINE CONNECTION DUE TO THE FACT THAT THESE LINES ARE
USUALLY LEASED FROM A SPECIFIC CARRIER MOSTLY FROM A
TELEPHONE COMPANY OR SERIAL CONNECTION.
This type of connection is dedicated for use by the company that leases the lines. This typ
of protocol helps us in establishing host-to-network and router-to-router connections ove
asynchronous and synchronous circuits that have inbuilt security features. The point-to-
point WAN protocol has the capability of working with various network layer protocols
such as ARA, IP and IPX. A good example of point-to-point connection is when we
establish a connection to our Internet Service Provider (ISP) by using a modem (Suo,
Wan, Zou, & Liu, 2012). 2 THIS TYPE OF CONNECTION BETWEEN US AND
THE ISP LEADS TO ESTABLISHMENT OF TWO POINTS ON THE NETWORK
Therefore, this means that the protocol that has been use here is what we call Point-to-
Point Protocol. 3 THERE ARE FOUR COMPONENTS IN THE PPP. These
components encompass; 4 LINK CONTROL PROTOCOL: Used when establishing,
testing and configuring the data link connection; HDLC: It is a method that is usually
used when datagrams over serial links need to be encapsulated; Data Encapsulations: It i
a method that is often employed in encapsulating the multi-protocol datagrams; Network
Cont ...
Swisscom Network Analytics Data Mesh Architecture - ETH Viscon - 10-2022.pdf

Swisscom Network Analytics at the VIScon Symposium 2022
Similar to Poster-A4 (20)
Botprobe - Reducing network threat intelligence big data 

Botprobe - Reducing network threat intelligence big data
IRJET- A Survey of Working on Virtual Private Networks

IRJET- A Survey of Working on Virtual Private Networks
International Journal of Engineering Research and Development (IJERD)

International Journal of Engineering Research and Development (IJERD)
summer training report on Computer network and Cisco packet tracer 

summer training report on Computer network and Cisco packet tracer
NETWORK INTRUSION DETECTION AND NODE RECOVERY USING DYNAMIC PATH ROUTING

NETWORK INTRUSION DETECTION AND NODE RECOVERY USING DYNAMIC PATH ROUTING
DCCN 2016 - Tutorial 2 - 4G for SmartGrid ecosystem

DCCN 2016 - Tutorial 2 - 4G for SmartGrid ecosystem
11172017 SafeAssign Originality Reporthttpswilmu.blac.docx

11172017 SafeAssign Originality Reporthttpswilmu.blac.docx
Swisscom Network Analytics Data Mesh Architecture - ETH Viscon - 10-2022.pdf

Swisscom Network Analytics Data Mesh Architecture - ETH Viscon - 10-2022.pdf