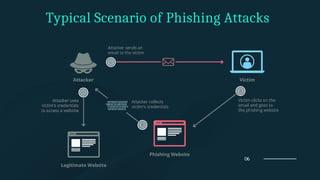
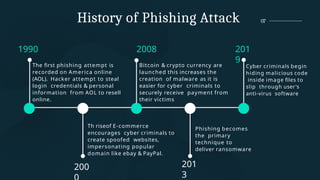
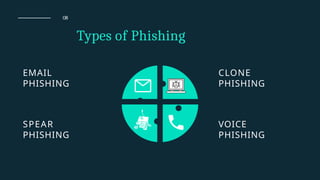
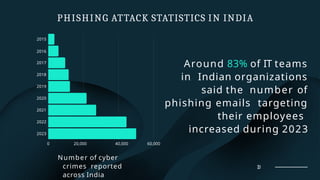
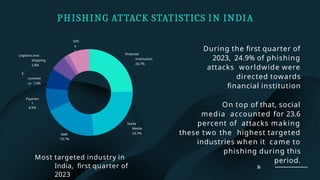
The document discusses phishing, a social engineering attack aimed at stealing user data by impersonating trustworthy entities. It covers the history, types of phishing attacks, and statistics related to phishing incidents in India, highlighting the significant rise in such attacks in recent years, especially targeting financial institutions and social media. Preventive measures and legal implications associated with phishing are also outlined, emphasizing a multi-faceted approach to reduce its prevalence.