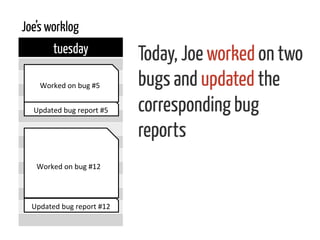
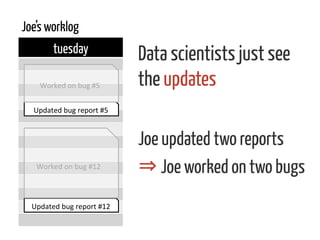
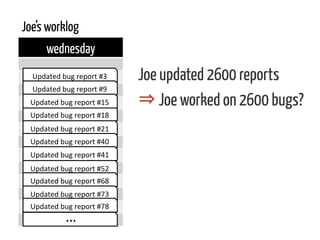
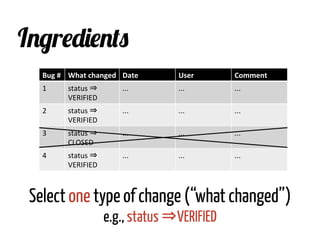
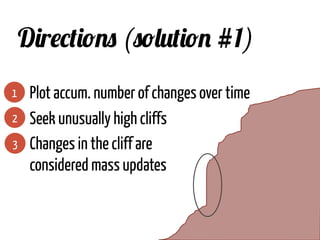
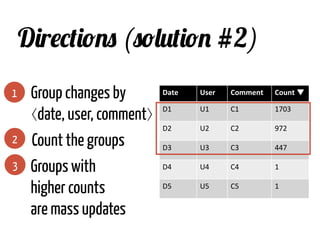
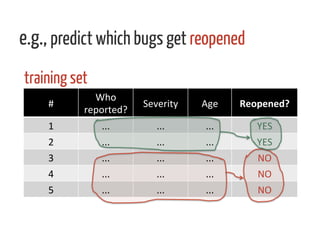
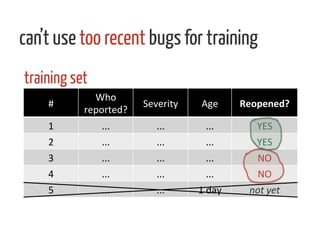
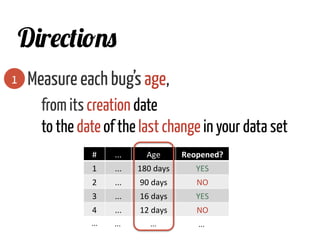
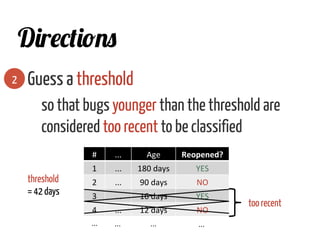
The document discusses strategies for cleaning up bug data, focusing on two main patterns: identifying mass updates in bug reports and determining which reports are too recent to be classified. It explains how to analyze changes in bug reports, discard irrelevant mass updates, and estimate the age and reliability of reports before further analysis. Proper data cleaning is emphasized as crucial for accurate insights into software quality.