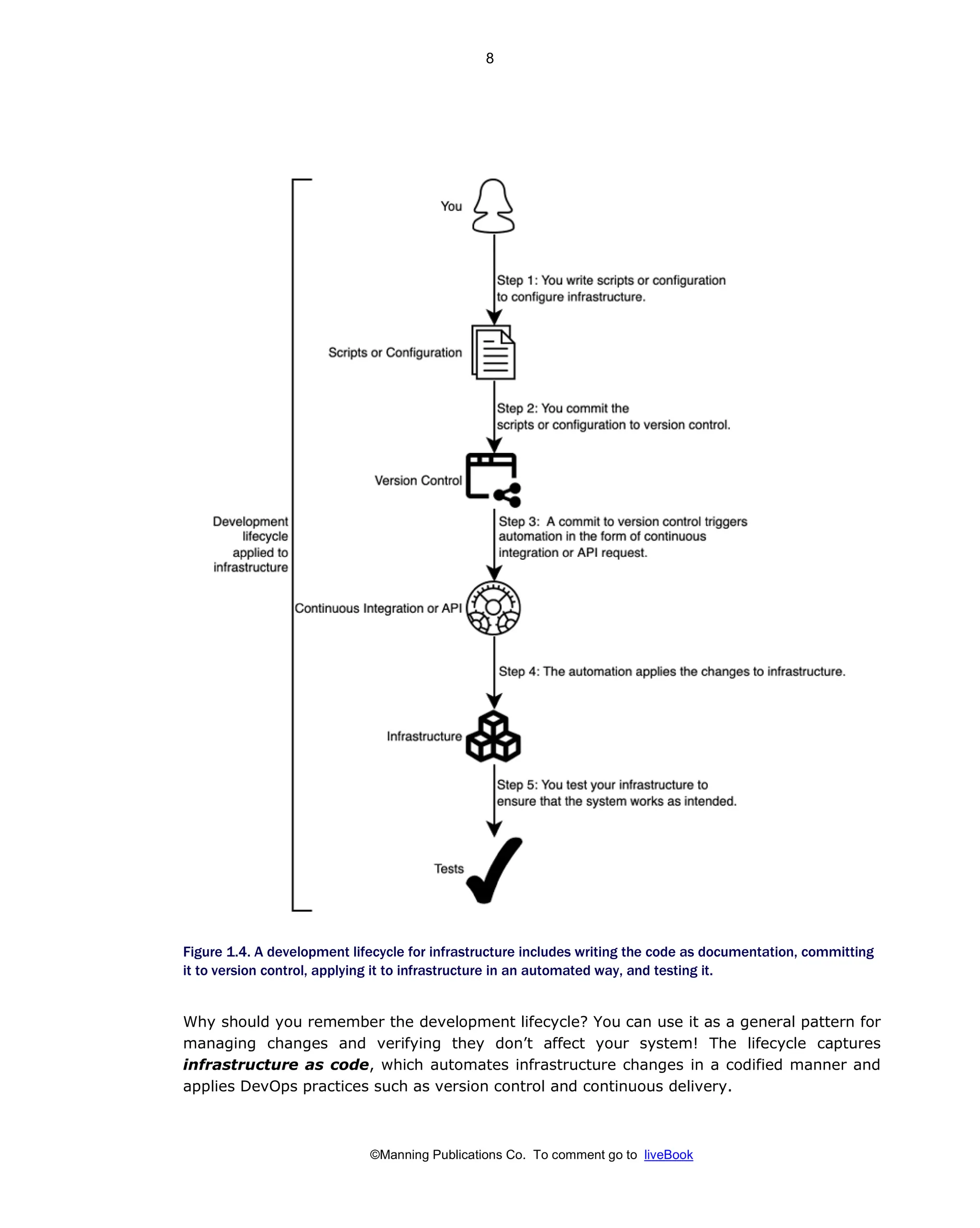
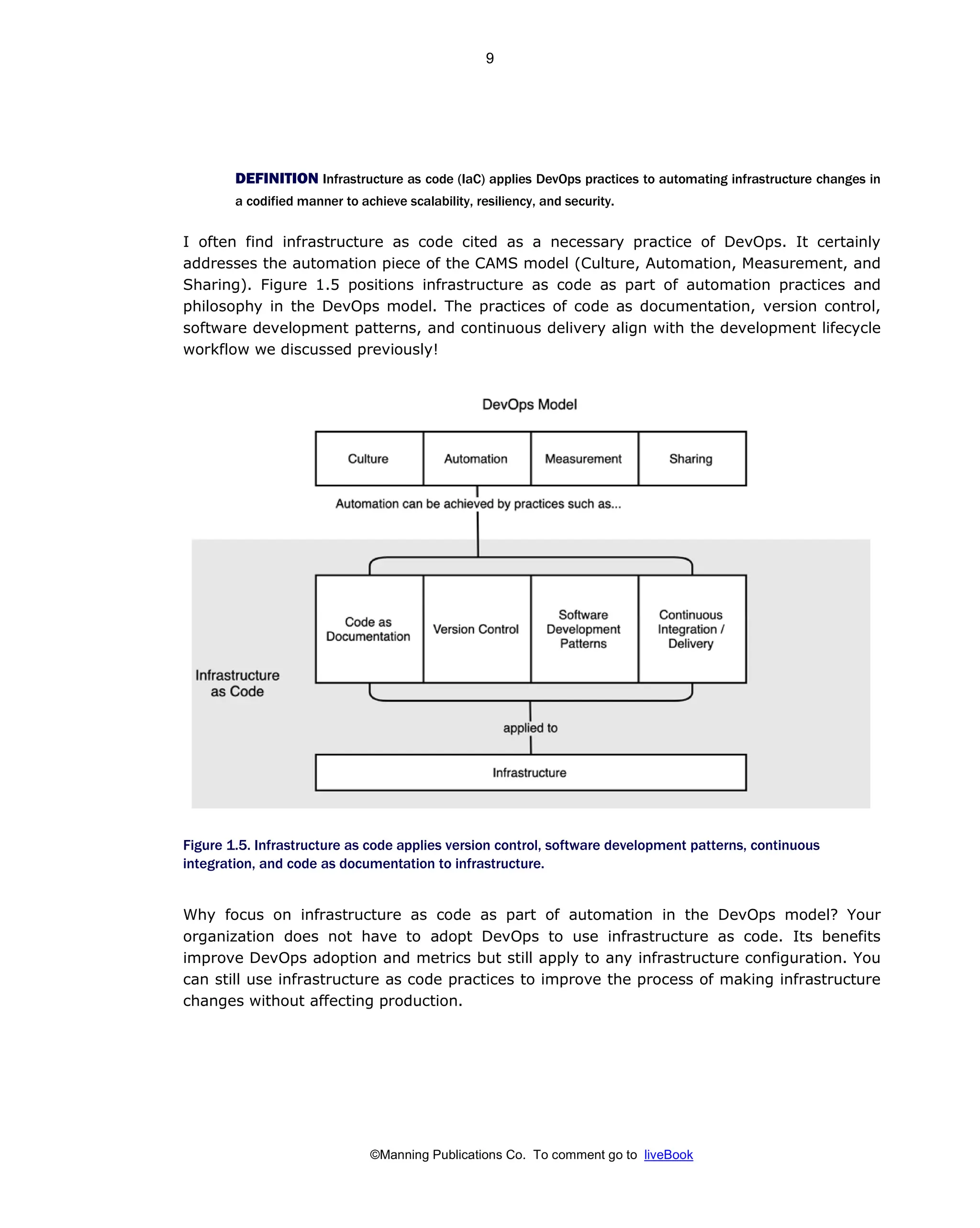
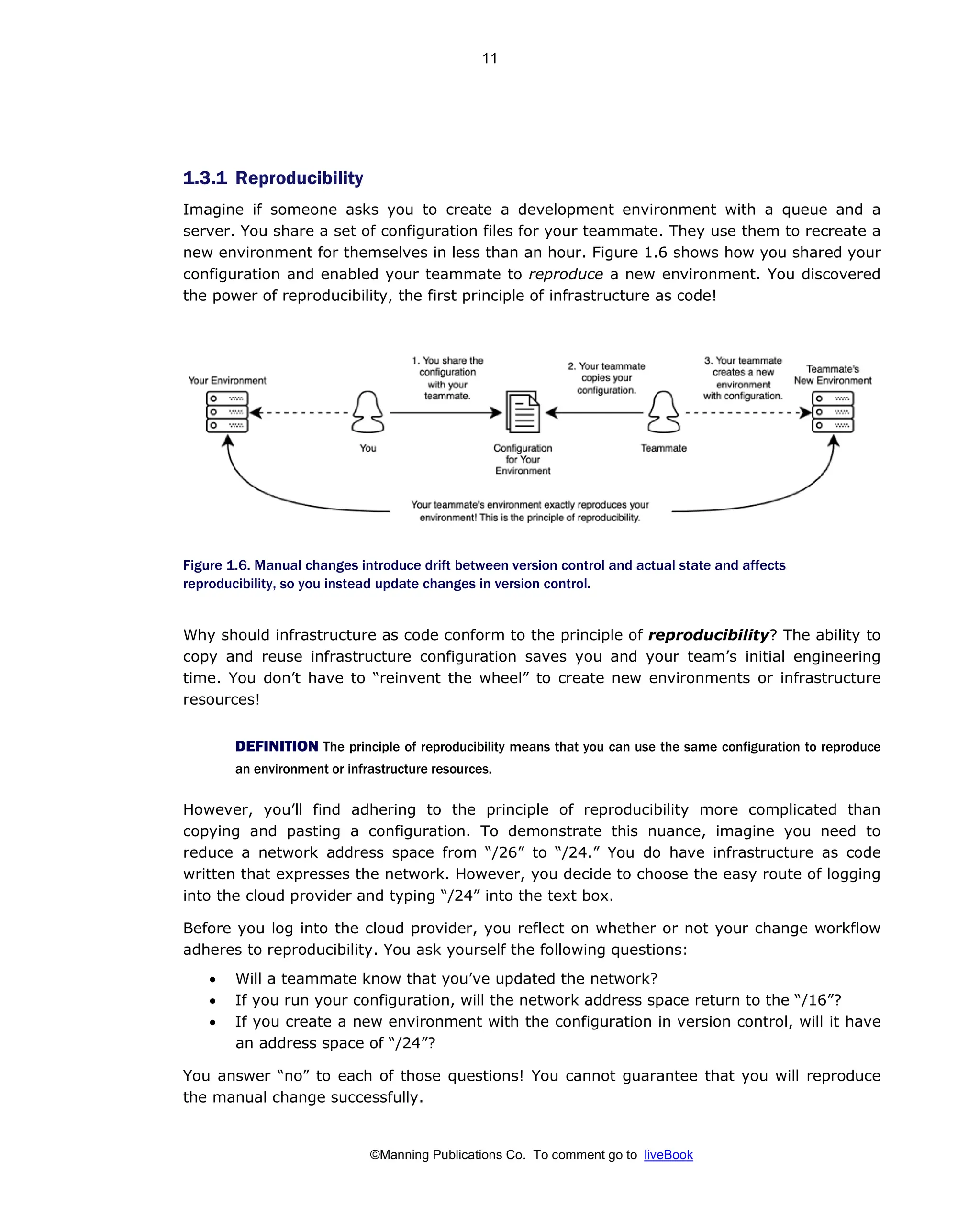
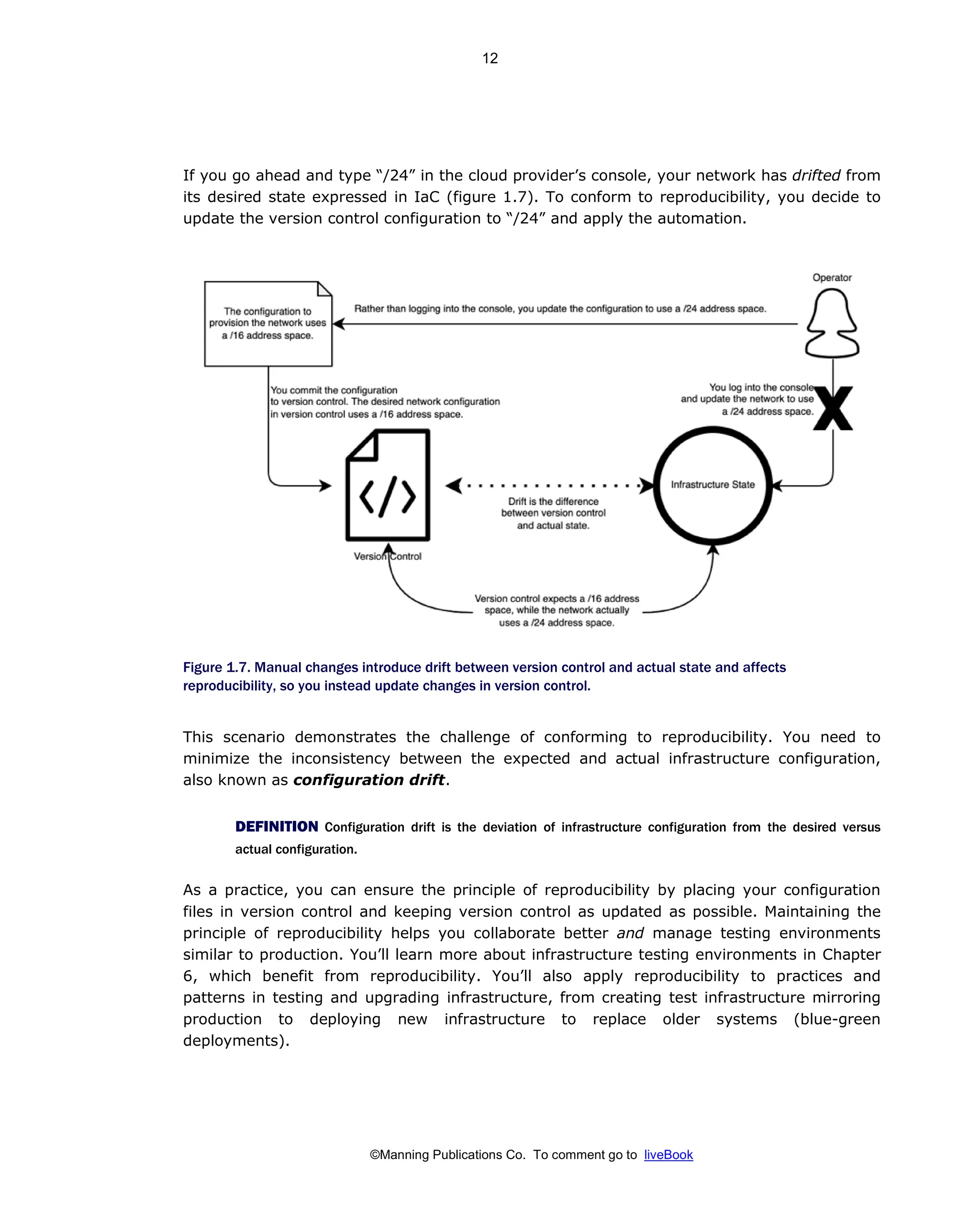
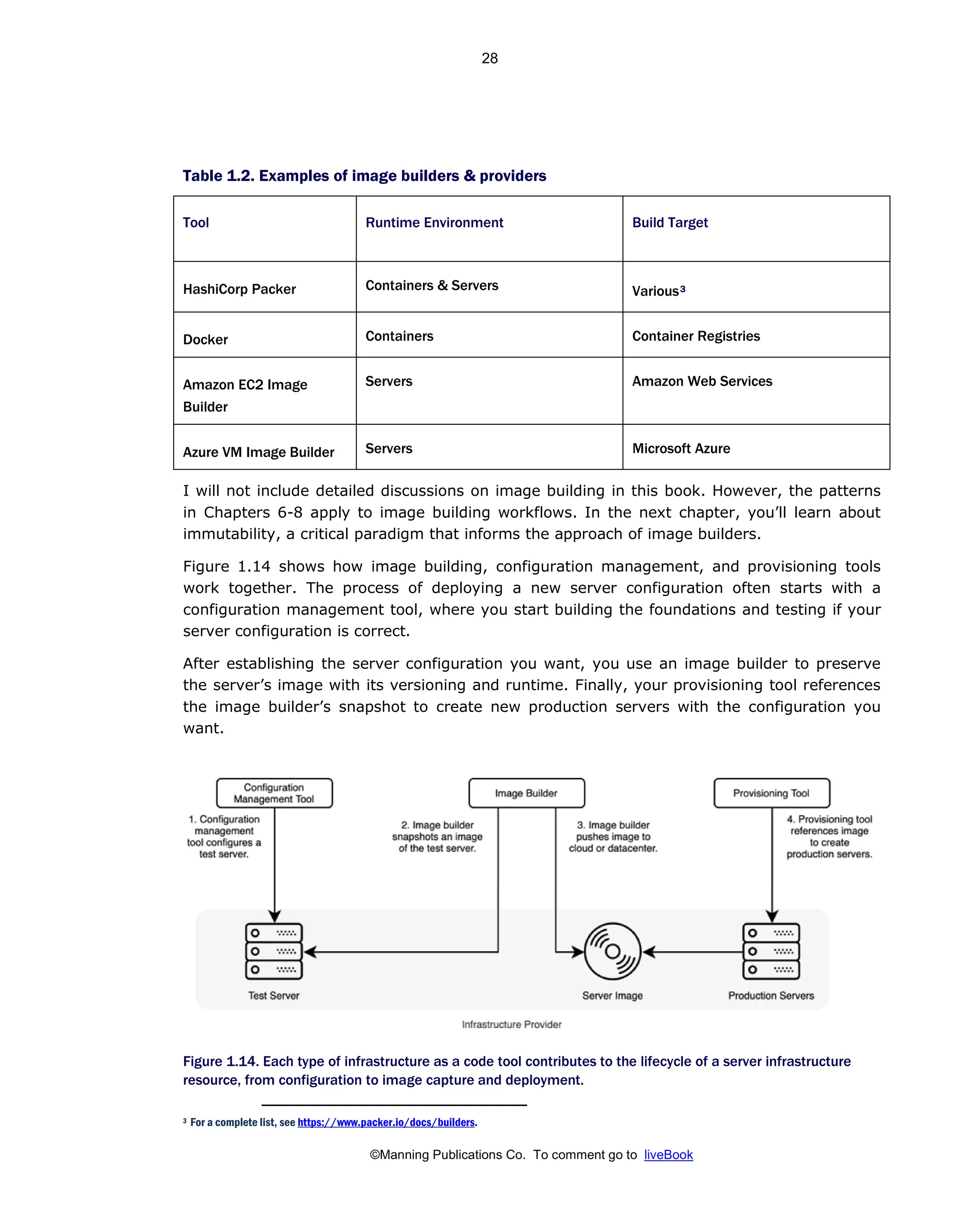
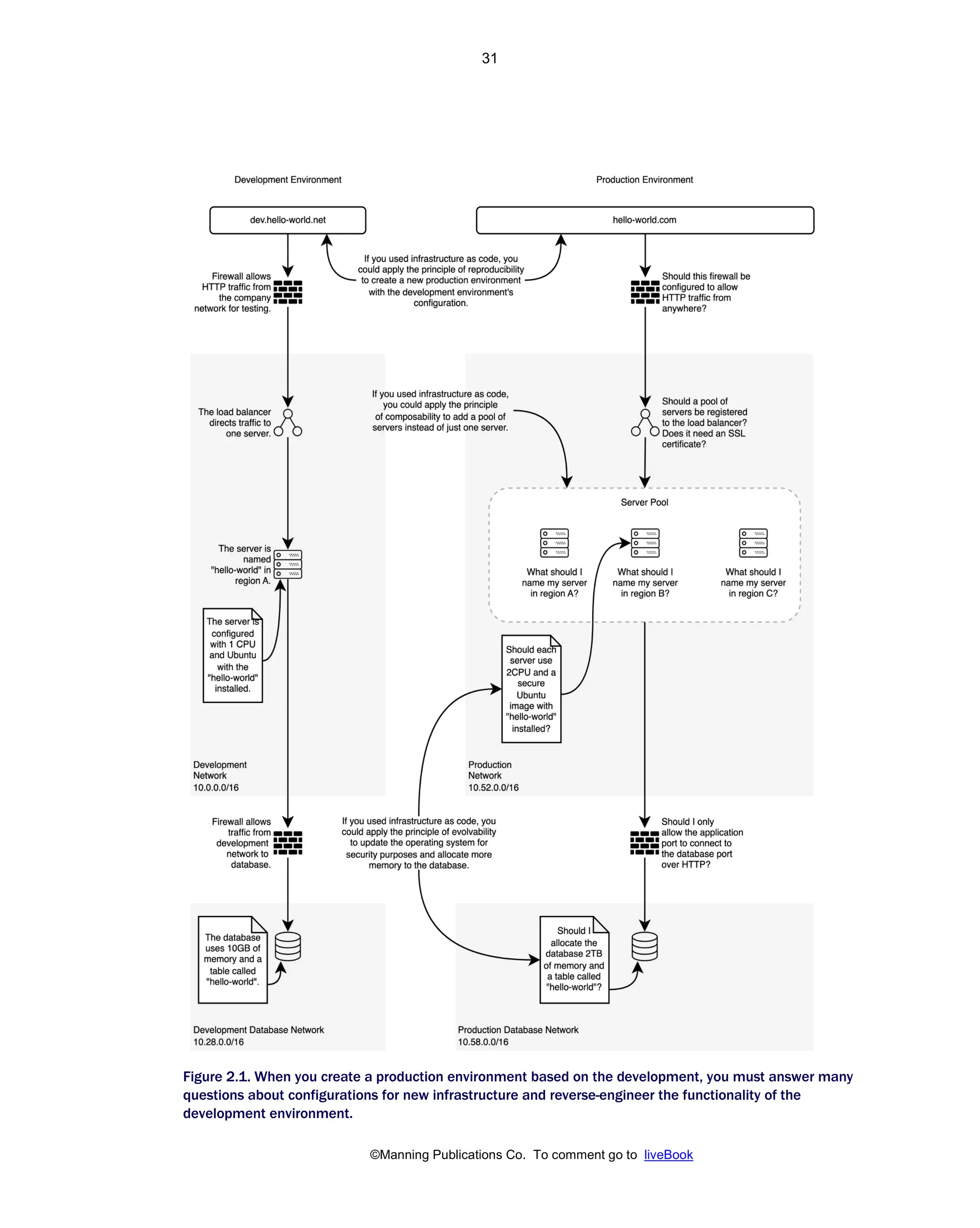
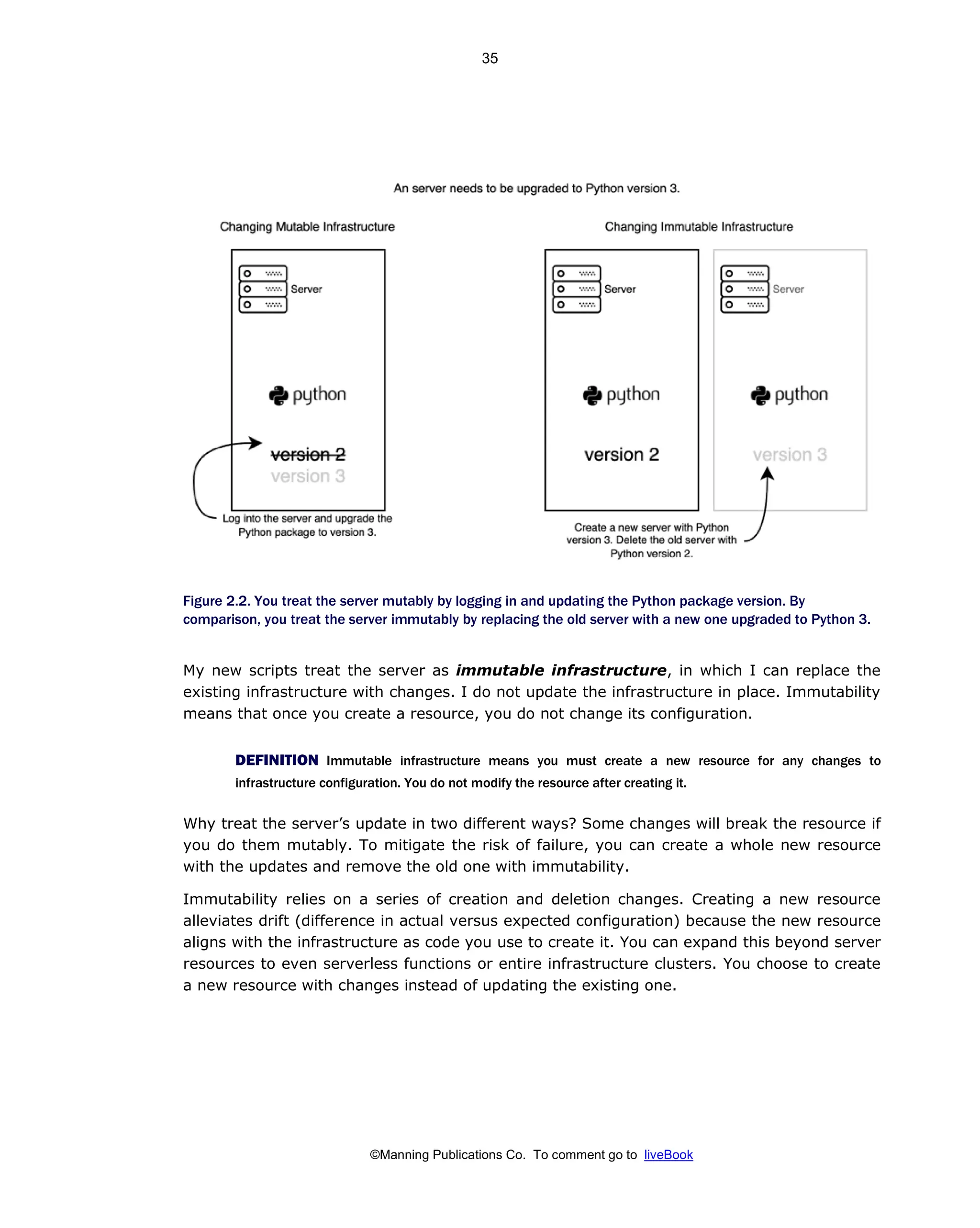
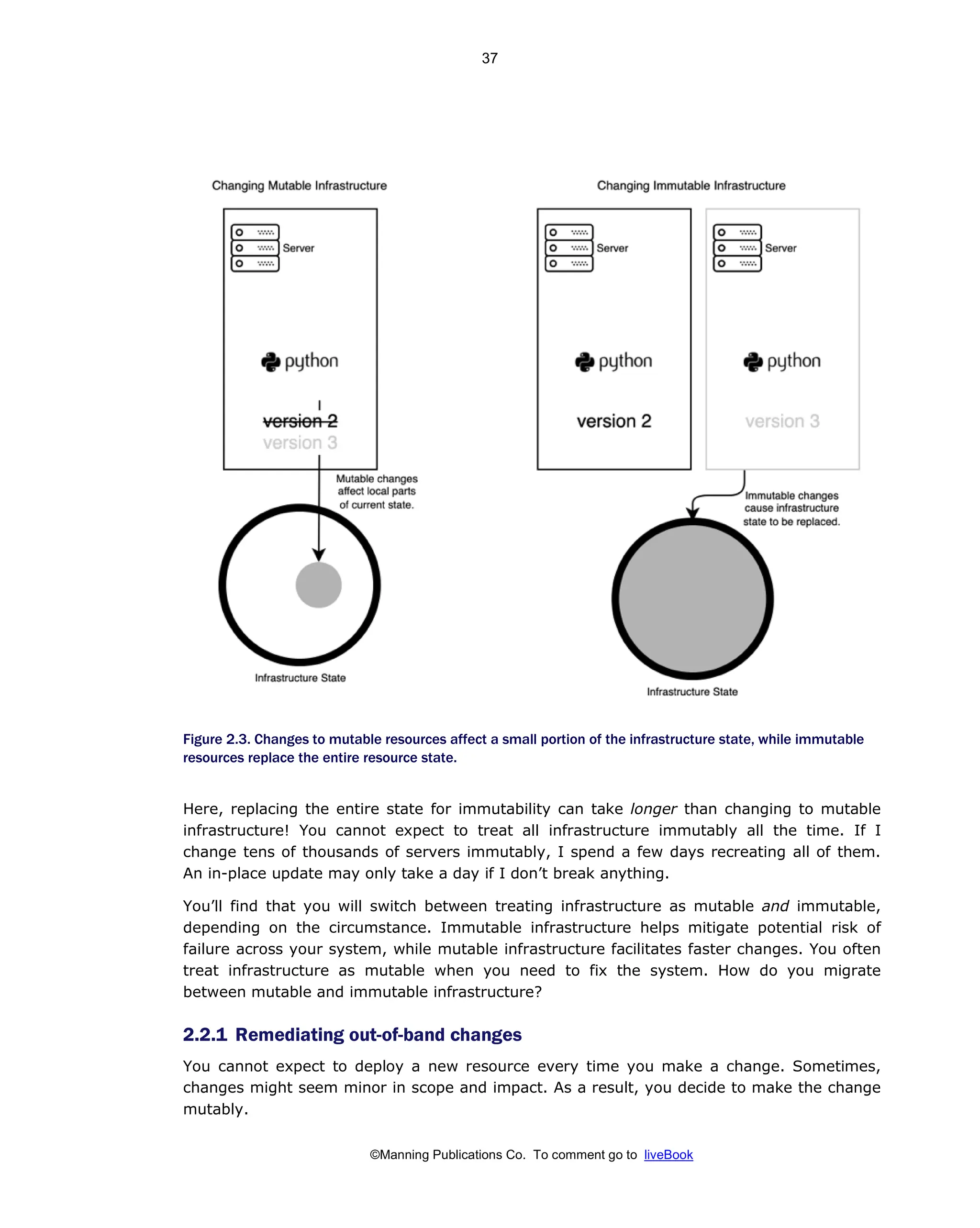
Patterns And Practices For Infrastructure As Code With Examples In Python And Terraform Meap V08 Meap V08 Rosemary Wang
Patterns And Practices For Infrastructure As Code With Examples In Python And Terraform Meap V08 Meap V08 Rosemary Wang
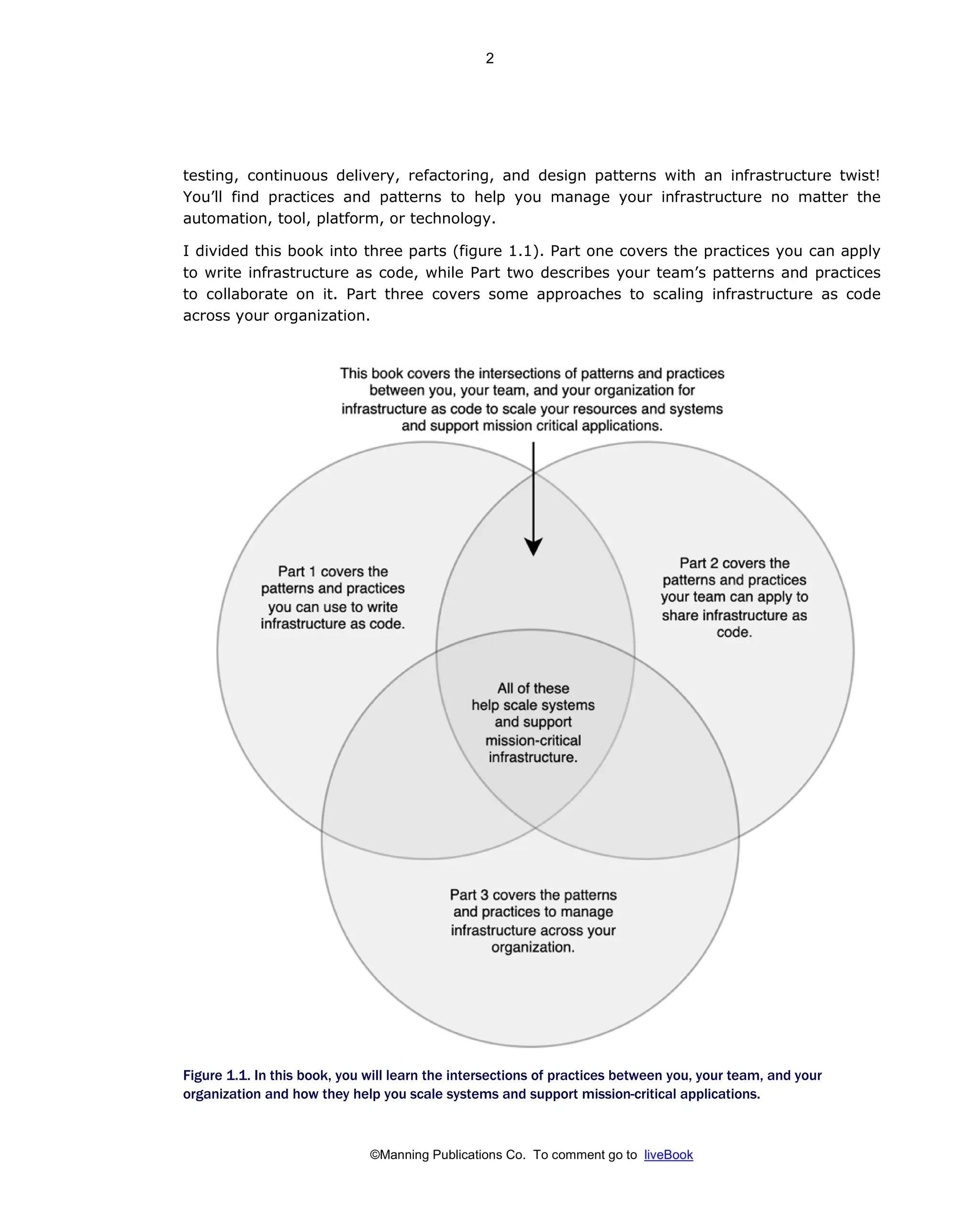
Patterns And Practices For Infrastructure As Code With Examples In Python And Terraform Meap V08 Meap V08 Rosemary Wang









































![Direct. II. Be very careful what persons you commit either trusts
or secrets to; and be sure they be trusty by their wisdom, ability,
and fidelity.
Direct. III. Be not too forward in revealing your own secrets to
another's trust: for, 1. You cannot be certain of any one's secrecy,
where you are most confident. 2. You oblige yourself too much to
please that person, who by revealing your secrets may do you hurt;
and are in fear lest carelessness, or unfaithfulness, or any accident
should disclose it. 3. You burden your friend with the charge and
care of secrecy.[168]
Direct. IV. Be faithful to your friend that doth intrust you;
remembering that perfidiousness or falseness to a friend, is a crime
against humanity, and all society, as well as against christianity; and
stigmatizeth the guilty in the eyes of all men, with the brand of an
odious, unsociable person.
Direct. V. Be not intimate with too many, nor confident in too
many; for he that hath too many intimates, will be opening the
secrets of one to another.
Direct. VI. Abhor covetousness and ambition; or else a bribe or
the promise of preferment, will tempt you to perfidiousness. There is
no trusting a selfish, worldly man.
Direct. VII. Remember that God is the avenger of perfidiousness,
who will do it severely: and that even they that are pleased and
served by it, do yet secretly disdain and detest the person that doth
it; because they would not be so used themselves.
Direct. VIII. Yet take not friendship or fidelity to be an obligation
to perfidiousness to God, or the king, or commonwealth, or to
another, or to any sin whatsoever.](https://image.slidesharecdn.com/21261401-250520132040-0fc4e595/75/Patterns-And-Practices-For-Infrastructure-As-Code-With-Examples-In-Python-And-Terraform-Meap-V08-Meap-V08-Rosemary-Wang-62-2048.jpg)
![[168] Quod tacitum esse velis nemini dixeris. Si tibi non
imperasti, quomodo ab alio silentium speras? Martin. Dumiens,
de morib.](https://image.slidesharecdn.com/21261401-250520132040-0fc4e595/75/Patterns-And-Practices-For-Infrastructure-As-Code-With-Examples-In-Python-And-Terraform-Meap-V08-Meap-V08-Rosemary-Wang-63-2048.jpg)








![he was not; therefore he was not an object of love (but in esse
cognito.) The same we say of God's loving us when we were
enemies: he really loved us with complacency so far as our physical
goodness made us lovely; and as morally lovely he did not love us,
otherwise than in esse cognito. But he purposed to make us morally
lovely, and gave us his mercies to that end; and so loved us with a
love of benevolence, as it is called; which signifieth no more than
out of a complacence (or love) to himself, and to us, as physically
good, to purpose to make us morally good and happy. As to the
incident difficulty of love beginning de novo in God, I have fully
resolved it elsewhere.[169]
2. So also we must love a wicked man with a love of benevolence:
which properly is but to love him in his physical worth, and his
capacity of moral goodness and happiness, and thereupon (but
especially through the love of God) to desire his happiness.
3. And as to the loving of ourselves, (besides the sensitive love
before mentioned which respecteth self as self, and not as good,) a
wicked man may rationally love himself according to his physical
goodness as a man, which containeth his capacity of moral
goodness, and so of being holy and serviceable to God and to good
men, and happy in the fruition of God. But beyond all such goodness
(which only is amiableness) no man may rationally love himself or
any other, with the true formal act of love, which is complacence;
though he may wish good to himself or another beyond the present
goodness which is in them; nay, he wisheth them good, not because
they are good, but because they want good.
And though some define loving to be bene velle alicui ut illi bene
sit, to desire another's welfare, yet indeed this may be without any
true formal love at all. As I may desire the welfare of my horse,
without any proper love to him, even for myself and use. When God
from eternity willeth to make Paul, and to convert and save him, ut
illi bene sit, it is called love of benevolence; but properly it is only to
be called, a will to make Paul good and lovely;[170] it being only God
himself who is the original and ultimate end of that will and purpose;](https://image.slidesharecdn.com/21261401-250520132040-0fc4e595/75/Patterns-And-Practices-For-Infrastructure-As-Code-With-Examples-In-Python-And-Terraform-Meap-V08-Meap-V08-Rosemary-Wang-72-2048.jpg)