Pattern recognition in ML.pdf
- 1. 1/11 Pattern recognition in ML leewayhertz.com/pattern-recognition Ever wondered how your incredible brain effortlessly navigates the vast sea of information that bombards you every day? Picture this: You are scrolling through a whirlwind of Facebook posts and photos, and amidst the chaos, your eyes lock onto a familiar face, completely ignoring the noise. It’s a remarkable ability called pattern recognition, a talent we humans possess without even realizing it. Our brains detect patterns and connect them with our stored memories. Interestingly, pattern recognition takes on a new dimension in the world of artificial intelligence. Pattern recognition, in the context of machine learning, refers to the process of matching incoming data with information stored in a database. It involves training a machine learning model to spot commonalities by exposing it to diverse examples. Like our brains, these models rely on their lessons to effectively identify similarities and make sense of the world. As per a report by Contrive Datum Insights, the valuation of the global Machine Learning (ML) market was USD 15.44 billion in 2021, and it is anticipated to witness substantial growth, reaching an estimated value of USD 209.91 billion by 2030. This impressive growth is projected to be driven by a CAGR of 38.8% during the forecast period. In machine learning, a pattern refers to a discernible regularity or structure observed in data. It can be as simple as a sequence of numbers or as complex as a multifaceted relationship between various data points. Patterns are the underlying framework that enables us to make sense of the vast amounts of information surrounding us. They allow us to decipher the complexities of our world, predict future outcomes, and create technologies that adapt to our needs. You can find applications of pattern recognition in ML everywhere: unlocking phones with facial recognition, voice assistants like Siri, personalized recommendations on Netflix and Spotify, and autonomous vehicles. By
- 2. 2/11 leveraging ML pattern recognition, we can unlock a world of possibilities, transforming how we interact with technology and shaping a future where intelligent systems seamlessly integrate into our lives. This article presents a comprehensive overview of pattern recognition in machine learning, encompassing its operational mechanics, techniques, and practical applications. What is pattern recognition in machine learning? How does pattern recognition work? Training the pattern recognition system Approaches to pattern recognition Pattern recognition using python Applications of pattern recognition What is pattern recognition in machine learning? Pattern recognition involves the identification of recurring trends or structures within a given dataset, enabling us to recognize similarities and make predictions. They provide insights into underlying concepts and facilitate informed decision-making based on observed regularities. In machine learning, pattern recognition employs advanced algorithms to detect and analyze regularities within data. This field has wide-ranging applications, particularly in technical domains such as computer vision, speech recognition, and face recognition. Pattern recognition utilizes statistical information, historical data, and the system’s memory to recognize and classify events or entities. One key attribute of pattern recognition is the ability to learn from data. It leverages available data to improve its performance continually. ML adapts and refines its algorithms through training and iterative processes, enhancing the accuracy and efficiency of pattern recognition. For instance, in the context of recommending books or movies, if a user consistently prefers black comedies, machine learning algorithms can recognize this pattern and suggest similar genre preferences, avoiding suggestions that do not align with the established pattern. How does pattern recognition work? Pattern recognition is a complex process that consists of two main parts: explorative and descriptive. Explorative: In the explorative part, pattern recognition involves identifying and discovering data patterns in a more general sense. It aims to uncover underlying regularities or structures within the data without specific pre-defined categories or labels. This approach is often used when the patterns or relationships in the data are not well- known or when there is a need for exploratory analysis. Descriptive: Descriptive pattern recognition focuses on categorizing and organizing the detected patterns into predefined categories or classes. It starts with the assumption that there are distinct groups or classes to which the patterns can be assigned. This approach
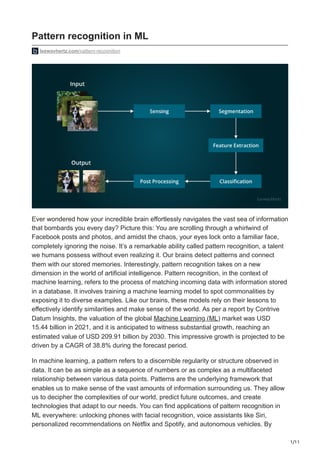
- 3. 3/11 is commonly employed when the goal is to classify or label the data based on known patterns or categories. For example, descriptive pattern recognition might categorize documents into topics or themes based on the identified patterns. Sentiment analysis leverages pattern recognition to categorize texts based on their emotional tone, distinguishing between positive, negative, or neutral sentiments by identifying patterns associated with specific emotions. Similarly, in audio data, pattern recognition algorithms can classify various sounds, such as speech, music, or environmental noise, by detecting distinctive patterns and features unique to each sound category. Using pattern recognition techniques, data analytics systems can process large volumes of diverse data, uncover hidden relationships and provide valuable information to support decision-making processes in various fields. The above-mentioned working pattern recognition system can be divided into different phases. Let us discuss the phases that pattern recognition in ML goes through. Phases of pattern recognition The phases associated with pattern recognition systems are as follows: Sensing In this initial phase, the pattern recognition system receives input data (which could be in different formats, such as images, sounds, or text) from various sources, such as sensors or data streams. The system converts this input data into a suitable format for further processing. For example, in image recognition, the system may convert the raw pixel data into a digital representation that can be analyzed. Segmentation In this phase, the pattern recognition system identifies and isolates individual objects or regions of interest within the sensed data. This step is crucial when dealing with complex data containing multiple objects or distinguishing between foreground and background elements. In image analysis, segmentation involves partitioning an image into distinct regions or objects. Feature extraction The system extracts relevant features or properties once the objects or regions of interest are identified. Features are distinctive characteristics that help distinguish one object from another. These features can be numerical values or descriptors that capture important information about the objects. Feature extraction techniques vary depending on the nature of the data and the specific problem at hand. For instance, in text analysis, features could include word frequencies or syntactic patterns. Once the features have been extracted from the pre-processed data, the pattern recognition system proceeds with the classification, clustering or regression phase (though these 3 phases may or may not be implemented together depending on the use
- 4. 4/11 case). Classification The system assigns a label or class to each input based on the extracted features. This involves training a classification model using labeled data, where the features serve as input variables, and the corresponding labels define the target classes. Popular classification algorithms include Support Vector Machines (SVM), decision trees, random forests, and neural networks. The trained model can then predict the class labels for new, unseen data. Clustering The system groups similar data points based on their extracted features without predefined class labels. Clustering algorithms aim to identify inherent patterns and structures within the data. Common clustering algorithms include k-means clustering, hierarchical clustering, and density-based clustering. The output is a set of clusters where data points within the same cluster are similar to those in other clusters. Regression The pattern recognition system may sometimes involve predicting numerical values rather than assigning class labels. Regression models establish relationships between the extracted features and the target variable, allowing the system to make predictions on new data. Linear, polynomial, and support vector regression are examples of regression algorithms. Post-processing After the classificationclusteringregression phase, additional steps may be performed to refine the results or make further decisions. Post-processing involves applying additional rules or criteria to the classified objects or using techniques such as filtering, smoothing, or outlier detection. The goal is to improve the accuracy or reliability of the classification results before taking any further action or making a final decision based on the recognized patterns. It’s important to note that these phases are not always strictly sequential or independent. They can be iterative, with feedback loops between different stages to improve the overall performance of the pattern recognition system. Additionally, the specific techniques and algorithms employed in each phase may vary depending on the application and the type of data being analyzed.
- 5. 5/11 Feedback and Adaptation Feature Extraction Classification Regression Implement on the Problems LeewayHertz Segmentation Sensing Real World Clustering Training the pattern recognition system Data selection and preparation are fundamental steps in constructing a pattern recognition system. They involve carefully curating and transforming the data to ensure its quality, relevance, and compatibility with the system. After data selection and preparation, the next step is to divide the data into three sets: Training set The training data set plays a crucial role in building a pattern recognition system as it is used to train the model. For a security system based on face recognition, various photos of employees’ faces in different lighting conditions, angles, and expressions should be gathered. These images serve as the foundation for extracting relevant information. The faces from the images are first detected and extracted to prepare face images for analysis. Then, the images are normalized to adjust for variations in lighting and scale, ensuring accurate and consistent results. Once the data is prepared, the training rules come into play. The model is trained using preprocessed face images, enabling it to associate facial features, patterns, and unique characteristics with the corresponding identities of the employees. It is generally recommended to allocate about 80% of the data for the training set, ensuring there is sufficient data to capture the variability in employees’ faces and enable accurate recognition. Through this process, the pattern recognition system can effectively learn and generalize from the training set, enabling accurate identification and recognition of individuals. Validation set The validation set ensures the model performs well on new data. It helps prevent the model from becoming too specialized and ensures its accuracy extends beyond the training data. We can detect signs of overfitting by evaluating the model’s performance on the validation set. Overfitting occurs when the model becomes overly specialized to the
- 6. 6/11 training data, resulting in high accuracy on the training set but poor performance on new, unseen data. When such a scenario is observed, the model’s performance may not generalize well to real-world situations. In such cases, it is recommended to stop training the model to prevent overfitting and explore strategies to improve its generalization capabilities. The validation set is a valuable checkpoint in the model development process, ensuring the trained model performs well on unseen data. Testing set The testing set serves as a final evaluation step to assess the accuracy and effectiveness of the pattern recognition system. Approximately 20% of the available data is reserved for this purpose. The testing set consists of data not used during the model training or fine- tuning stages, representing unseen samples that simulate real-world scenarios. The system’s outputs, such as predicted class labels or regression values, are compared against the actual ground truth labels or values in the testing set. This evaluation helps determine the system’s accuracy and performance on new, unseen data. Using a separate testing set, we can validate whether the pattern recognition system can generalize well and provide accurate outputs beyond the data it has been exposed to during training and validation. The testing set is an essential measure of the system’s overall performance and ability to handle real-world patterns effectively. Do not confuse the validation set with the testing set. The validation set is used to tune the parameters of the model, while a testing set assesses its performance as a whole. Approaches to pattern recognition One of the more challenging parts of pattern recognition is deciding on the approach you plan to follow. Here, we discuss a few pattern recognition approaches. Statistical In the statistical approach to pattern recognition, patterns are represented by features or measurements, forming points in a d-dimensional space. The goal is to choose features that ensure patterns from different categories occupy separate and well-defined regions in this feature space. The effectiveness of the feature set is determined by how well patterns from different classes can be separated. A set of training patterns from each class is used to establish decision boundaries in the feature space. The decision boundaries are determined based on the probability distributions of patterns belonging to each class, which can be either specified or learned. The goal is to find boundaries that effectively separate patterns from different classes. Another approach to classification is discriminant analysis, where a parametric form of the decision boundary (e.g., linear or quadratic) is specified. The “best” decision boundary of the specified form is then determined based on the classification of training patterns. Techniques such as the mean squared error criterion can be employed to construct these
- 7. 7/11 boundaries. Vapnik’s philosophy advocates the approach of constructing decision boundaries directly, which suggests solving the problem directly instead of attempting to solve a more general intermediate problem. Syntactic In complex pattern recognition problems, adopting a hierarchical perspective is often more suitable as it involves viewing patterns as compositions of simpler subpatterns. The elementary subpatterns, called primitives, are the basic units of recognition, and the complex pattern is represented based on the relationships between these primitives. This approach allows for a deeper understanding and recognition of complex patterns by breaking them into constituent elements. Syntactic pattern recognition draws a formal analogy between pattern structure and language syntax. Patterns are treated as sentences in a language, primitives serve as the language’s alphabet, and sentences are generated following grammar. By using a small set of primitives and grammatical rules, a large collection of complex patterns can be described. The grammar for each pattern class needs to be inferred from the available training samples. Structural pattern recognition is appealing because it enables classification and provides insights into how the given pattern is constructed from primitives. This approach has been applied in scenarios where patterns exhibit a definite structure, such as EKG waveforms, textured images, and shape analysis of contours. However, implementing a syntactic approach comes with challenges related to segmenting noisy patterns (to detect primitives) and inferring the grammar from training data. Neural network Neural networks are powerful computing systems comprised of numerous interconnected processors. They use learning, adaptivity, and fault-tolerance principles to process information. A neural network consists of artificial neurons connected by weighted edges, enabling them to learn complex relationships and adapt to data. Neural networks, particularly feed-forward networks like multilayer perceptrons and radial-basis function networks, are commonly used for pattern classification. These networks operate in a one- directional manner without feedback. However, the development of auto-associative neural networks has allowed feedback-based learning resembling human learning processes. Auto-associative neural networks are designed to reconstruct input patterns and minimize errors through the utilization of feedback connections. Constructing such networks can be challenging due to the requirement of accurately defining the feedback connections. Backpropagation algorithms simplify this process by adjusting connection weights backward, starting from the output unit and propagating adjustments to the input units. The iterative learning continues until the network minimizes the error between the actual
- 8. 8/11 and desired outputs. Neural networks offer efficient implementations of nonlinear feature extraction and classification algorithms, sharing similarities with classical statistical pattern recognition methods. Template matching Template matching is a simple and early technique used in pattern recognition. It involves comparing the similarity between entities of the same type, such as points, curves, or shapes. A prototype or template of the pattern to be recognized is provided in template matching. The pattern is then compared to the stored template, considering different allowable translation, rotation, and scale changes. The similarity between the pattern and template is usually measured using correlation, which can be optimized based on the training set available. In some cases, the template itself is learned from the training set. Template matching can be computationally intensive, but this approach has become more feasible with the advancement of faster processors. Pattern recognition using python Let’s consider a dataset consisting of information about apples and oranges. Each fruit is characterized by its color (red or yellow) and shape (round or oval), represented as a list of strings, such as [‘red’, ’round’] for a red, round fruit. We aim to create a function to predict whether a fruit is an apple or an orange. To accomplish this, we will utilize a basic pattern recognition algorithm known as k-nearest neighbors (k-NN). Here is the Python implementation of the function: Step-1: Import sqrt Below is the code for this step: from math import sqrt from collections import Counter These are import statements. They import the sqrt function from the math module and the Counter class from the collections module. We need sqrt to calculate the Euclidean distance and Counter to count the occurrences of each label. Step-2: Calculate Euclidean distance This step calculates the Euclidean distance between two points. In this case, the points are represented as lists. It iterates over the indices of the lists and calculates the squared difference between the corresponding elements. The sum of these squared differences is then square rooted to obtain the Euclidean distance. def euclidean_distance(point1, point2): distance = sqrt(sum((point1[i] != point2[i]) ** 2 for i in range(len(point1)))) return distance
- 9. 9/11 Step-3: Implement the k-nearest neighbors algorithm Here we will implement the k-nearest neighbors algorithm. It takes in the training_data, new_sample (the fruit to classify), and k (the number of nearest neighbors to consider). It initializes an empty list called distances to store the distances between new_sample and each point in the training_data. It then iterates over each fruit in the training_data, calculates the Euclidean distance between the features of the fruit and new_sample, and appends the distance along with the corresponding label to the distances list. def k_nearest_neighbors(training_data, new_sample, k): distances = [] # Calculate distances between new_sample and each training_data point for fruit in training_data: distance = euclidean_distance(fruit[0], new_sample) distances.append((distance, fruit[1])) Step-4: Extract the labels of the k nearest neighbors After calculating the distances, the distances list is sorted in ascending order. The next step is to extract the labels of the k nearest neighbors. This is done by iterating over the first k elements of the distances list and extracting the labels (fruit[1]) into a new list called neighbors. # Sort distances in ascending order distances.sort() # Get the labels of the k nearest neighbors neighbors = [fruit[1] for fruit in distances[:k]] Step-5: Find the most common label Using the Counter class, the code counts the occurrences of each label in the neighbors list, which gives a dictionary-like object with labels as keys and their counts as values. The most_common method is then used to find the label that appears most frequently. The function returns this most common label. # Count the occurrences of each label label_counts = Counter(neighbors) # Find the most common label most_common_label = label_counts.most_common(1)[0][0] return most_common_label Step-6: Output Finally, the code defines the training_data list, which contains tuples of features and labels for each fruit. It defines new_fruit as the sample fruit to classify and sets the value of k to 3, indicating that we want to consider the 3 nearest neighbors. The function k_nearest_neighbors is called with these inputs, and the predicted label is printed.
- 10. 10/11 training_data = [ (['red', 'round'], 'apple'), (['yellow', 'round'], 'apple'), (['red', 'oval'], 'orange'), (['yellow', 'oval'], 'orange') ] new_fruit = ['red', 'round'] # Sample fruit to classify k = 3 # Number of nearest neighbors to consider predicted_label = k_nearest_neighbors(training_data, new_fruit, k) print("Predicted label:", predicted_label) Output is: Predicted label: apple Applications of pattern recognition The applications of pattern recognition include: Image processing: Pattern recognition is leveraged in image processing, where machine learning algorithms can outperform humans. For example, recognizing various bird species, even in challenging conditions such as low lighting or noisy images. This capability allows for accurate and efficient classification and identification of objects within images, leading to advancements in areas like wildlife monitoring, species conservation, and biodiversity research. Computer vision: Pattern recognition techniques are utilized to extract significant features from image and video samples, enabling advanced analysis in computer vision. In biological and biomedical imaging, pattern recognition plays a crucial role in tasks like disease diagnosis, cell classification, and image-based research, aiding in understanding and advancing medical sciences. Seismic analysis: Pattern recognition is applied in seismology to detect, image, and interpret temporal patterns in seismic array recordings. Various seismic analysis models can be developed and employed using statistical pattern recognition techniques to identify seismic events, characterize their properties, and gain insights into Earth’s subsurface processes. These approaches enhance our understanding of earthquakes, volcanic activity, and other geophysical phenomena. Speech recognition: Pattern recognition paradigms have proven to be highly successful in speech recognition. Various speech recognition algorithms leverage these paradigms to overcome challenges associated with phoneme-level descriptions by treating larger units such as words as patterns, leading to improved accuracy and performance in speech recognition systems. Fingerprint identification: Various recognition methods are utilized for fingerprint matching, with pattern recognition playing a key role in accurately identifying and matching fingerprints. These approaches enable robust and reliable fingerprint
- 11. 11/11 recognition, contributing to applications such as secure access control, identity verification, and forensic investigations. Character recognition: Pattern recognition plays a crucial role in character recognition, enabling the identification and interpretation of letters and numbers. This application utilizes pattern recognition algorithms to process optically scanned images and generate alphanumeric characters as output. By analyzing the patterns and features within the input data, pattern recognition techniques enable automation and information handling systems to recognize and extract meaningful characters accurately. Character recognition finds wide-ranging applications such as document processing, Optical Character Recognition (OCR), postal services, and vehicle identification systems, facilitating efficient and reliable data processing and analysis. Endnote Pattern recognition in ML involves the analysis of input data to identify underlying patterns. These patterns can then be used for prediction, categorization, and decision- making. There are two main approaches to pattern recognition: explorative, which aims to identify general data patterns, and descriptive, which categorizes specific detected patterns. Pattern recognition is not limited to a single technique but rather a collection of closely related approaches that are constantly evolving. It is a prerequisite for developing intelligent systems and relies on computer algorithms to analyze and interpret data from various sources, such as text, images, and audio. As technology advances, pattern recognition will remain vital for understanding and making sense of complex data, driving innovation and advancements across multiple disciplines such as biology, psychology, medicine, marketing, computer vision, etc. Maximize your business potential with our ML-based solutions. Contact LeewayHertz’s experts to get started!