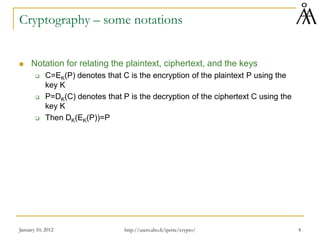
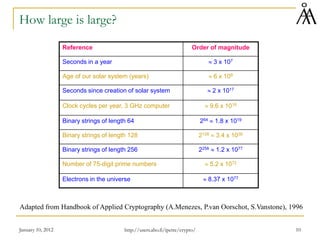
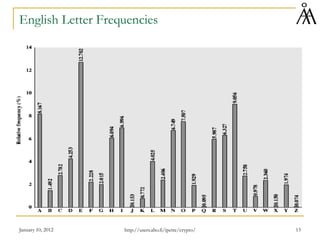
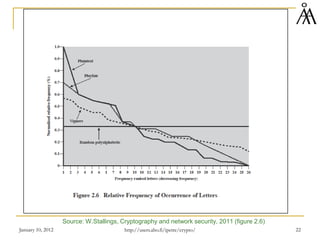
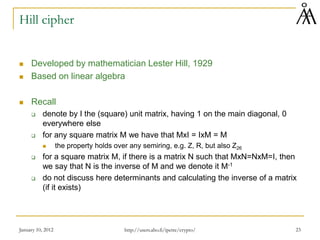
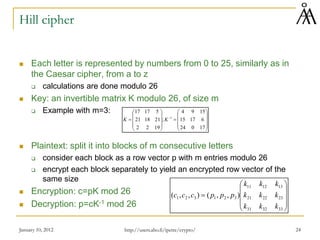
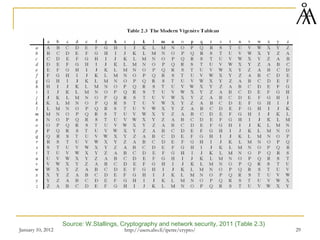
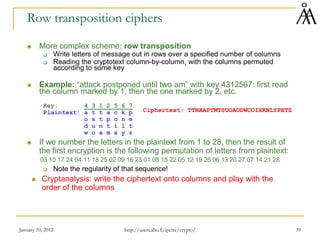
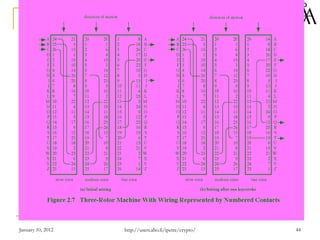
This document provides a summary of a lecture on classical encryption techniques. It discusses the Caesar cipher and its weaknesses, including how it can be broken with frequency analysis even with just the ciphertext. It then explains how monoalphabetic substitution ciphers are stronger but still vulnerable to frequency analysis with enough ciphertext. The document introduces the Playfair cipher as an example of a technique that encrypts digrams to strengthen security by hiding letter frequencies. It provides examples of how classical ciphers work and can be broken through cryptanalysis.