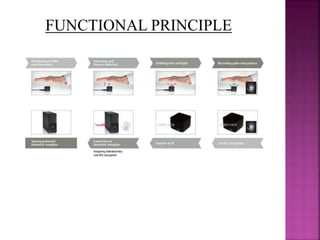
Fujitsu has developed a contactless palm vein pattern authentication technology called PalmSecure. It uses the unique vein pattern in a person's palm, which contains over 5 million reference points and remains the same throughout one's life, to identify individuals with a high level of precision. The PalmSecure sensor uses near-infrared light to extract the vein pattern without touching the palm. This technology offers stronger security than passwords or ID cards as vein patterns cannot be forged or shared, while being hygienic, accurate, and easy to use.





![When the palm is illuminated with near-infrared light, unlike the
image seen by the human eye [Figure 1(a)], the deoxidized
hemoglobin in the palm veins absorbs this light, which reduces the
reflection rate and causes the veins to appear as a black pattern
[Figure 1(b)]. In vein authentication based on this principle, the
region used for authentication is photographed with near-infrared
light and the vein pattern is extracted by image processing [Figure
1(c)] and registered.
EXTRACTION OF VEIN PATTERN](https://image.slidesharecdn.com/palmsecure-150609033406-lva1-app6892/85/Palmsecure-6-320.jpg)