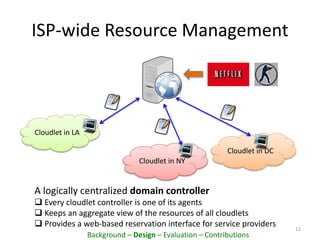
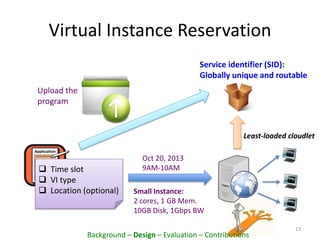
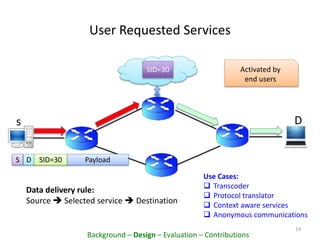
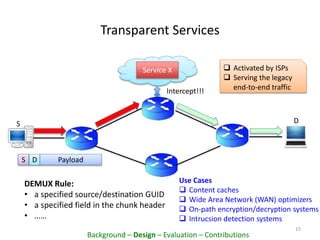
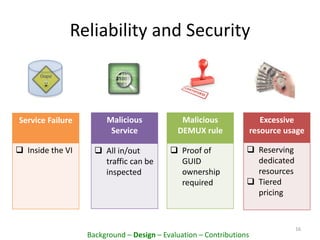
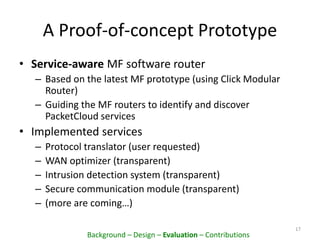
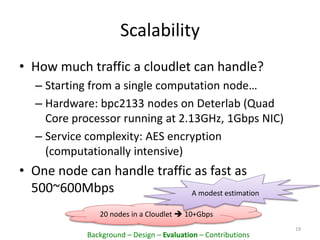
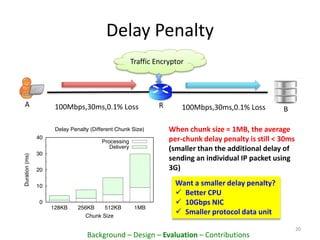
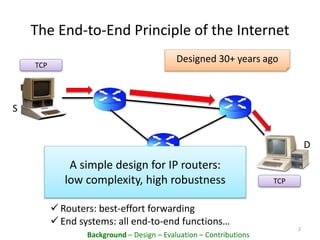
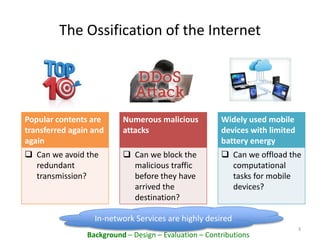
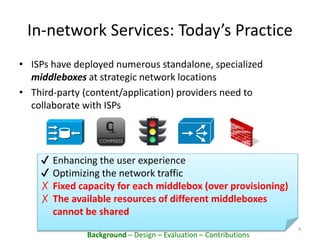
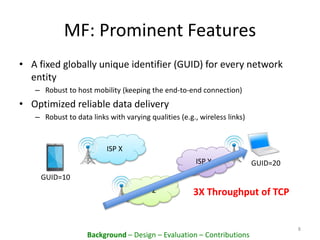
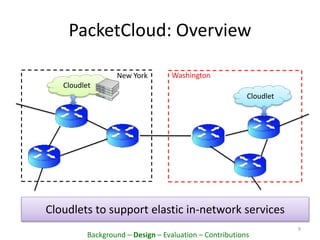
This document proposes PacketCloud, an open platform for hosting elastic in-network services. PacketCloud uses cloudlets located at ISP network edges to provide virtual instances for third-party services. These services can be user-requested or transparently intercept traffic. A prototype demonstrates services like encryption achieving over 500Mbps on one node and over 10Gbps across 20 nodes in a cloudlet with minimal delay. The platform aims to efficiently share network resources while providing economic rewards for ISPs and third parties.
![Related Work
• CoMb: consolidation of middleboxes [Sekar et al.,
NSDI’12]
– Supporting only trusted/reliable services
– Not open to third-party providers
– Vulnerable to unexpected service crash and malicious
attacks
• APLOMB: outsourcing to public clouds [Sherry et
al., SIGCOMM’12]
– Unwanted interdomain traffic
– Data ownership problems
6
Background – Design – Evaluation – Contributions](https://image.slidesharecdn.com/packetcloudmobiarch13final-131011095315-phpapp01/85/PacketCloud-an-Open-Platform-for-Elastic-In-network-Services-6-320.jpg)
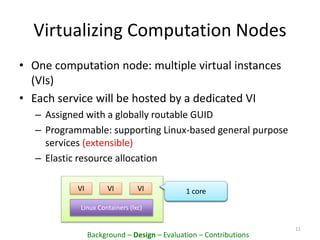
![Inside a Cloudlet
CPU (cores) Mem (GB) Disk (GB) BW (Gbps)
N1 7/1 1/1 250/50 5/5
N2 4/4 0/2 50/200 9/1
… … … … …
10
Reserved / Available
Resource Table (time slot: [t0, t1])
……
Serv 2
Serv 1
Cloudlet
Controller
DEMUX Rules
Background – Design – Evaluation – Contributions](https://image.slidesharecdn.com/packetcloudmobiarch13final-131011095315-phpapp01/85/PacketCloud-an-Open-Platform-for-Elastic-In-network-Services-10-320.jpg)