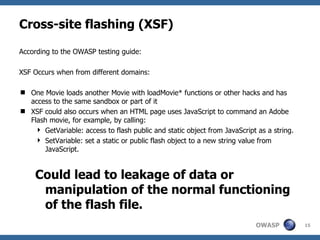
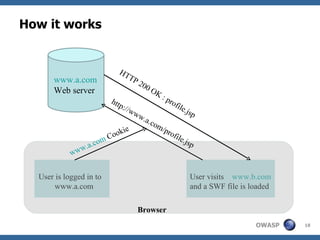
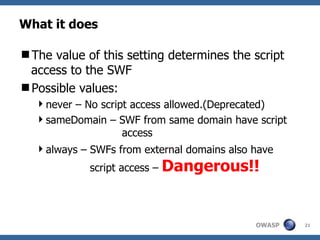
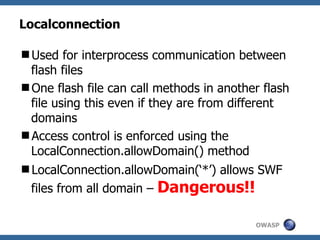
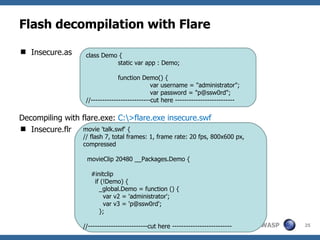
The document discusses security issues related to Flash applications. It introduces Flash and ActionScript, and outlines various vulnerabilities such as cross-site scripting, cross-site flashing, insecure crossdomain policies, and sensitive data storage in Flash. It provides examples of how these vulnerabilities can be exploited and recommendations for more secure development practices.
![Test.Security(Flash); Lavakumar K GISA, Royal Bank of Scotland Lavakumar[dot]in[at]gmail[dot]com 21 st March, 2009](https://image.slidesharecdn.com/flashsecurity-090615115202-phpapp02/75/Flash-Security-OWASP-Chennai-1-2048.jpg)







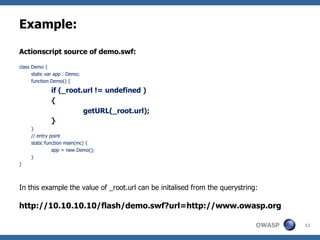

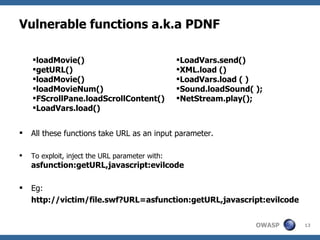
![Other means of Cross-site scripting Text fields in flash can be injected with HTML textfield.html = true textfield.htmlText = ’ <a href='javascript:alert(1)' >’ flash.external.ExternalInterface.call(); This function can call JavaScript methods. Method Description: public static call(methodName:String, [parameter1:Object]) : Object](https://image.slidesharecdn.com/flashsecurity-090615115202-phpapp02/85/Flash-Security-OWASP-Chennai-14-320.jpg)