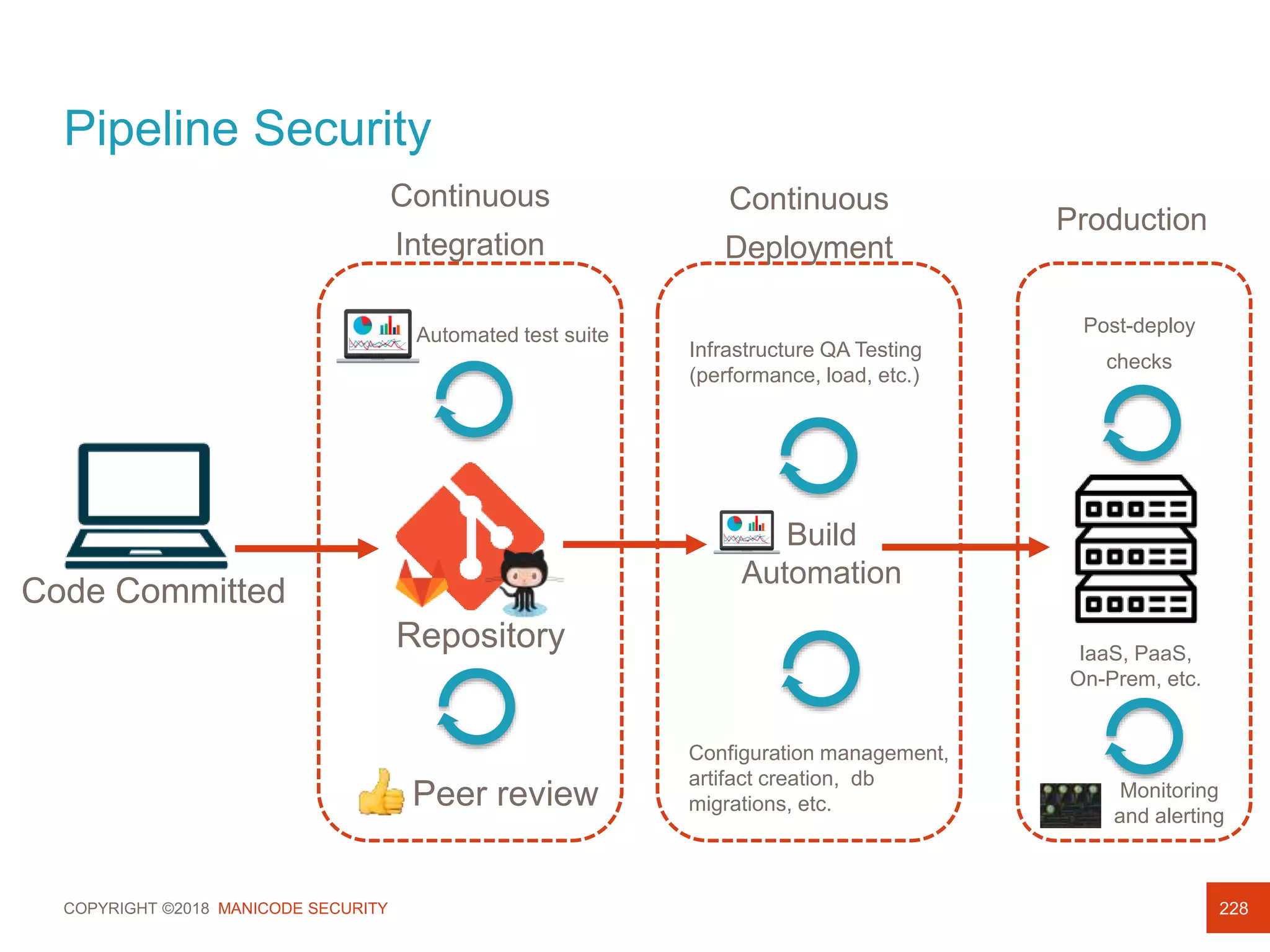
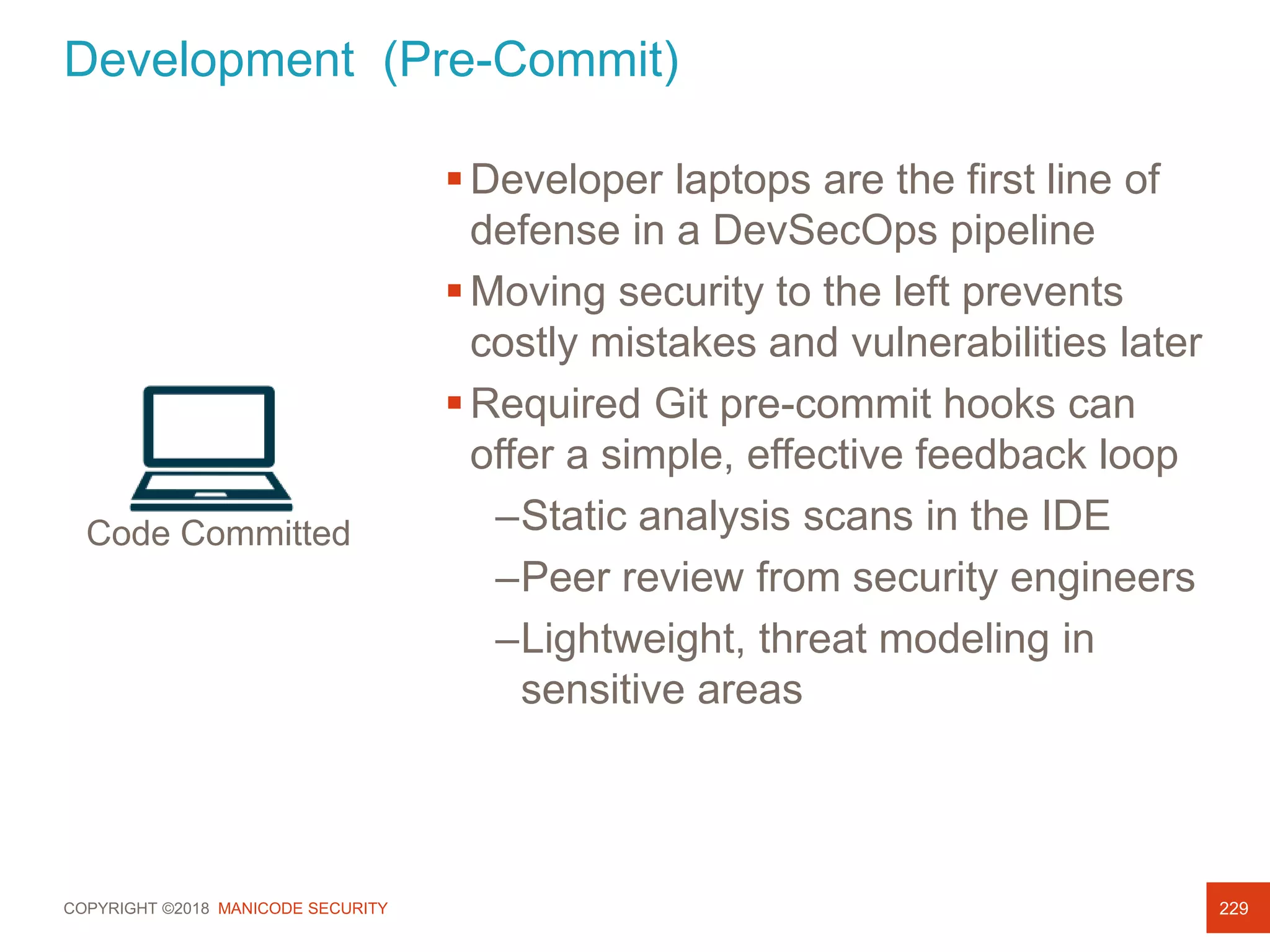
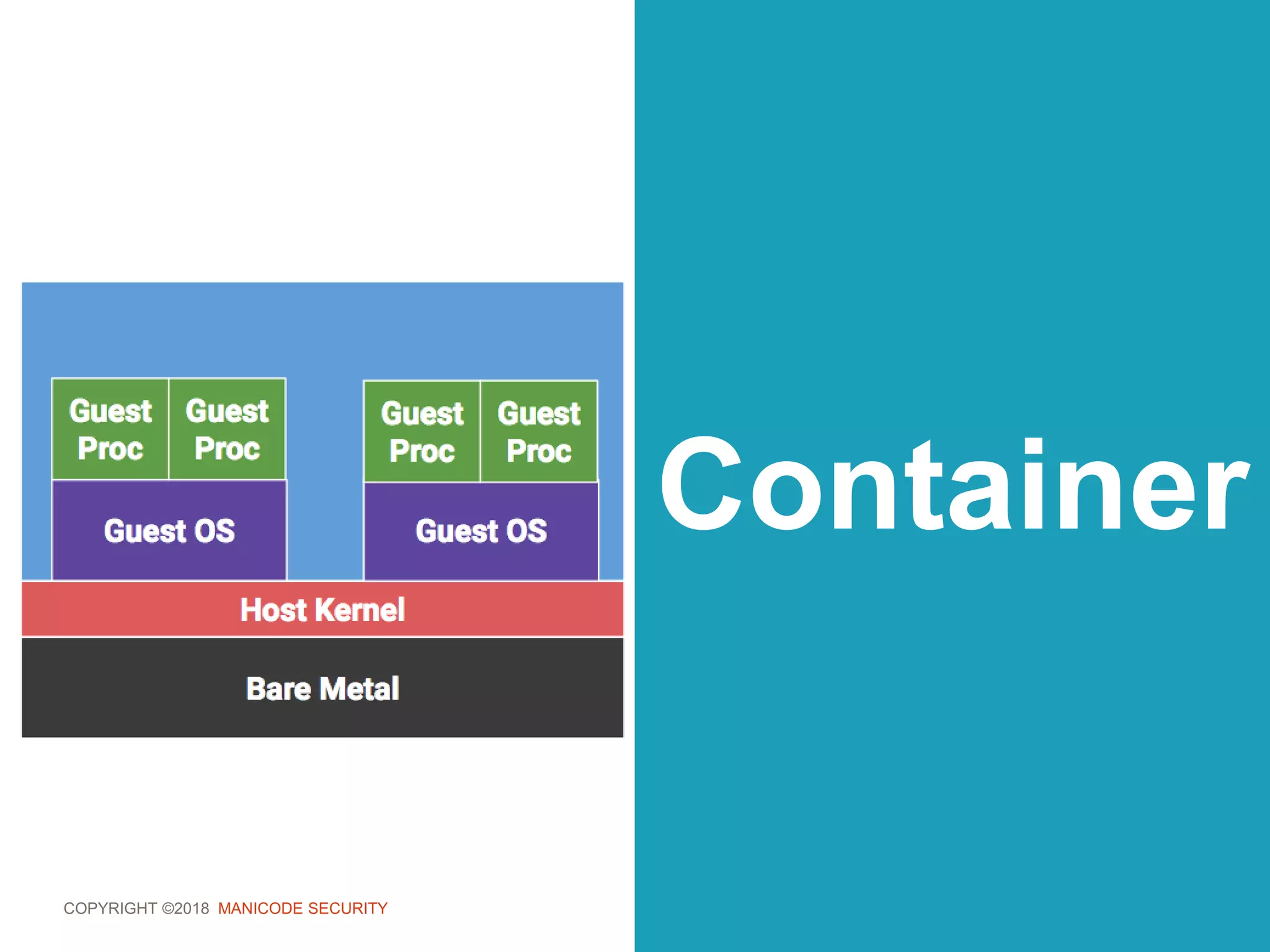
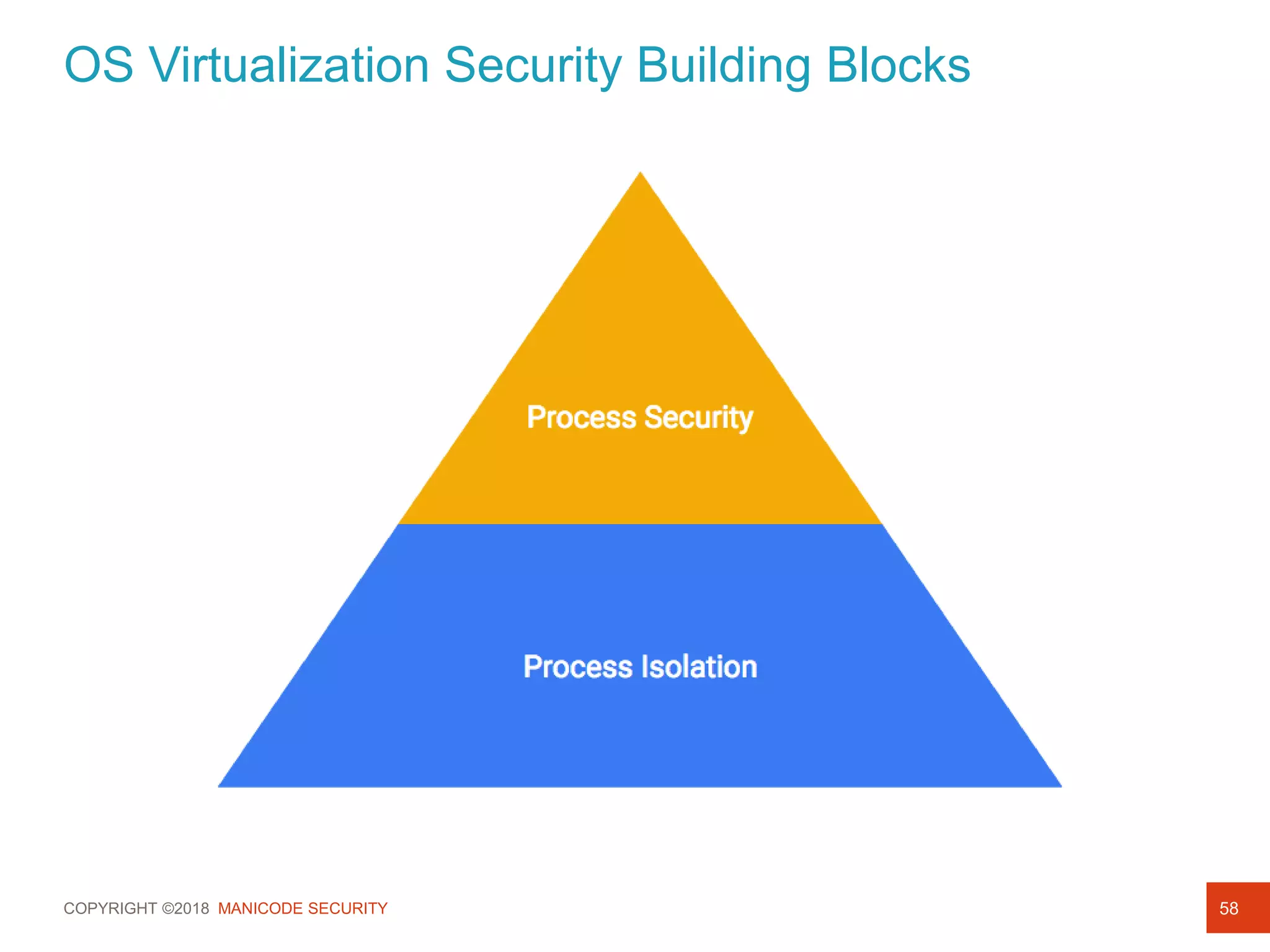
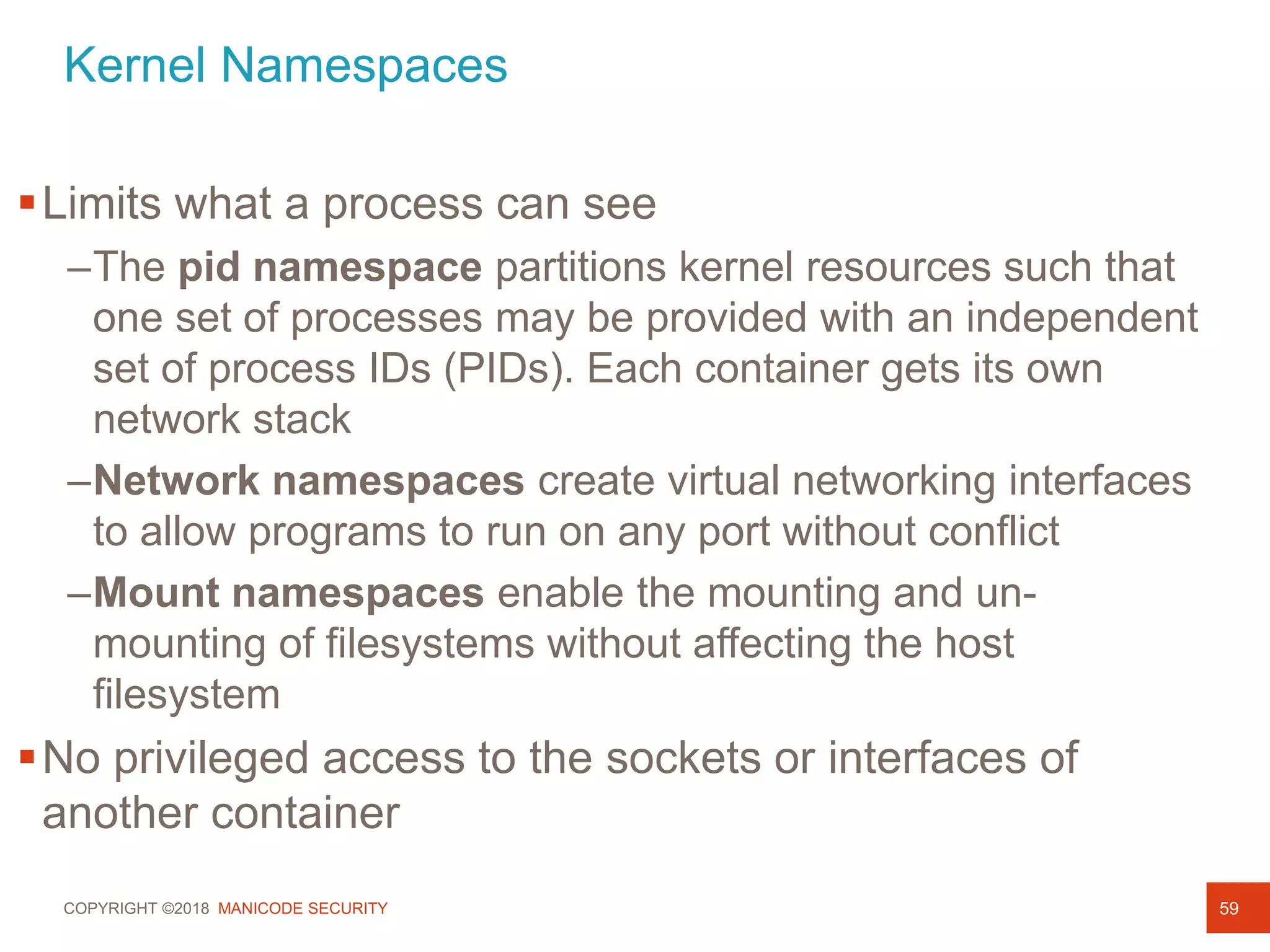
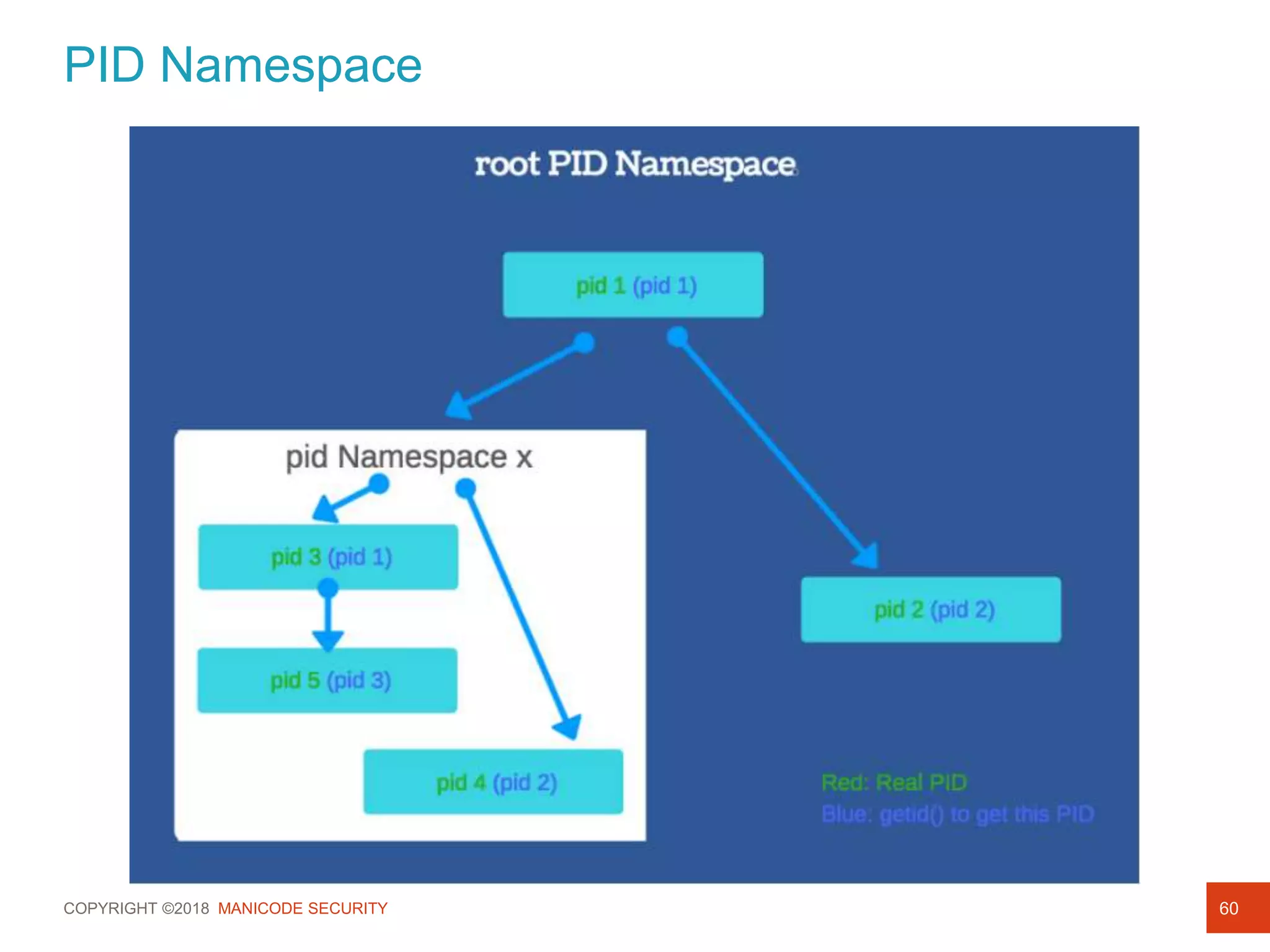
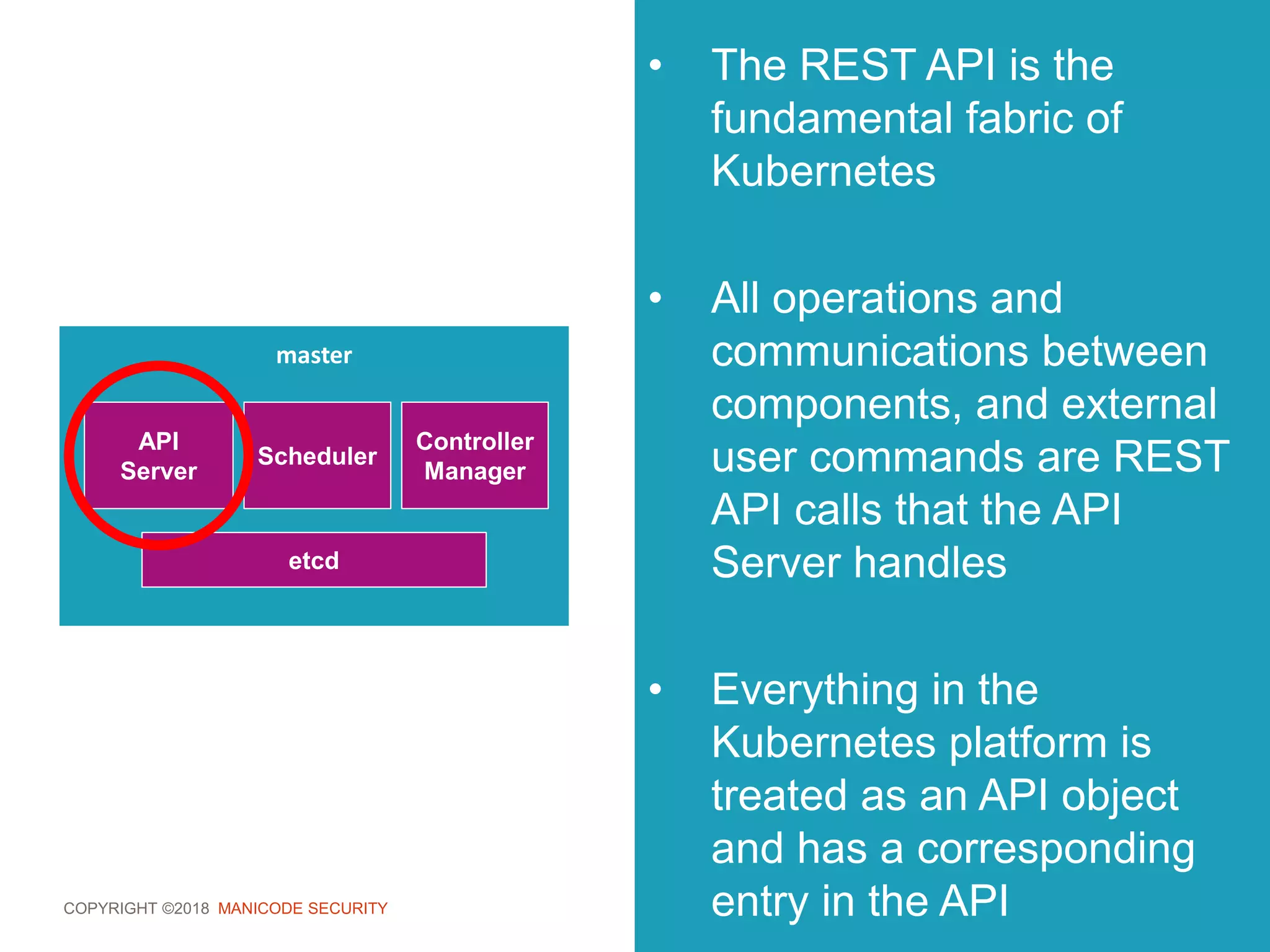
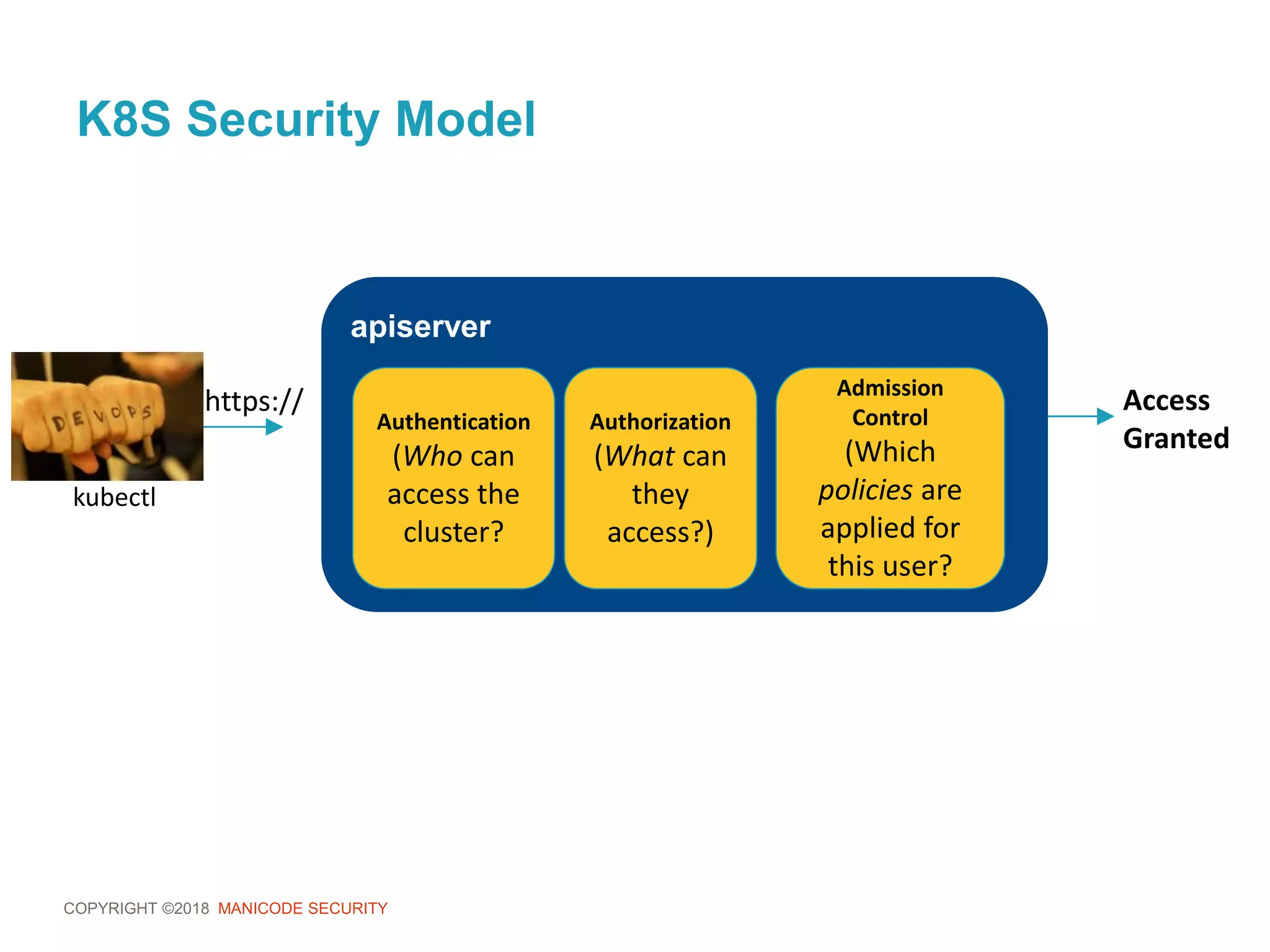
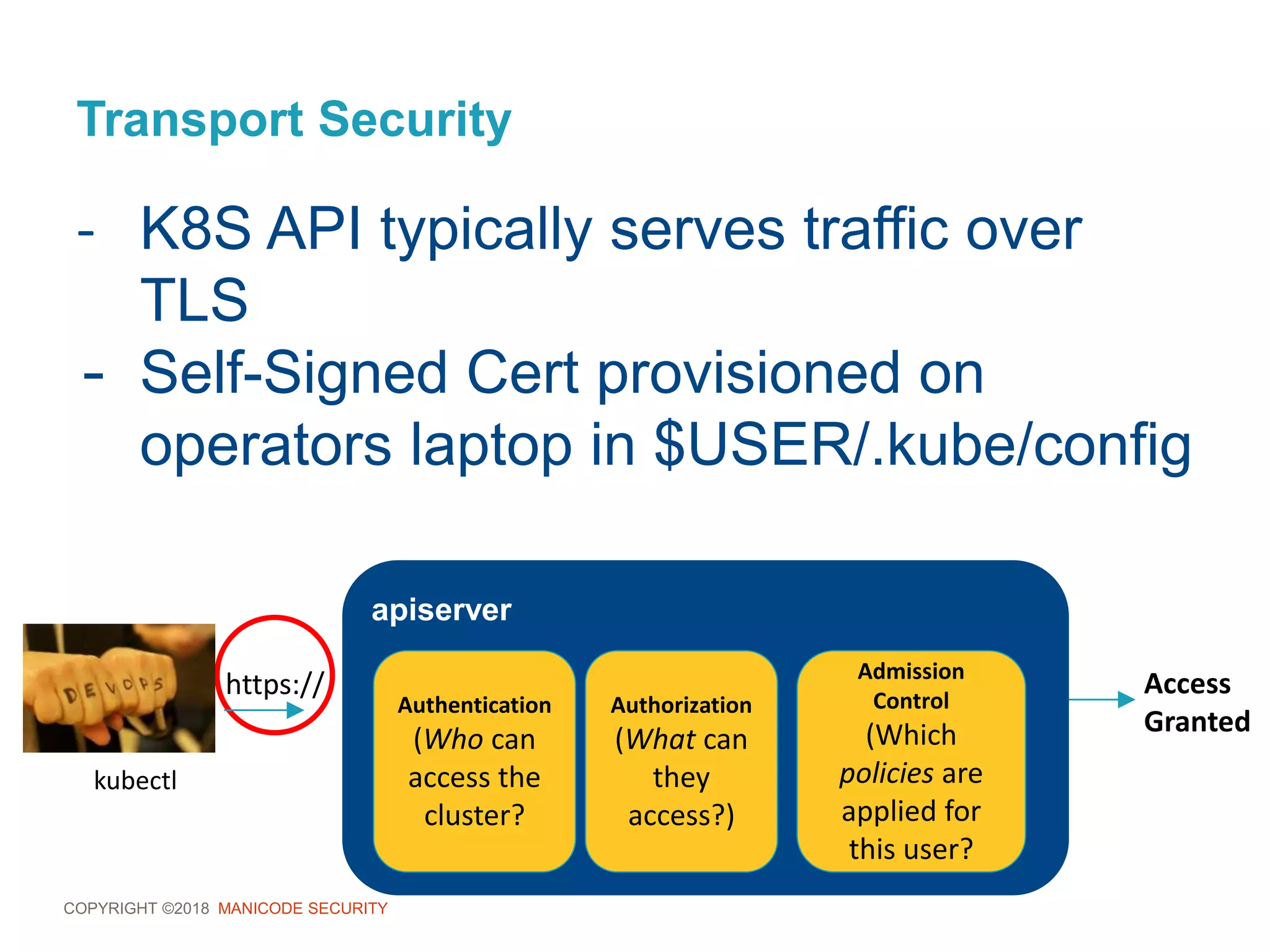
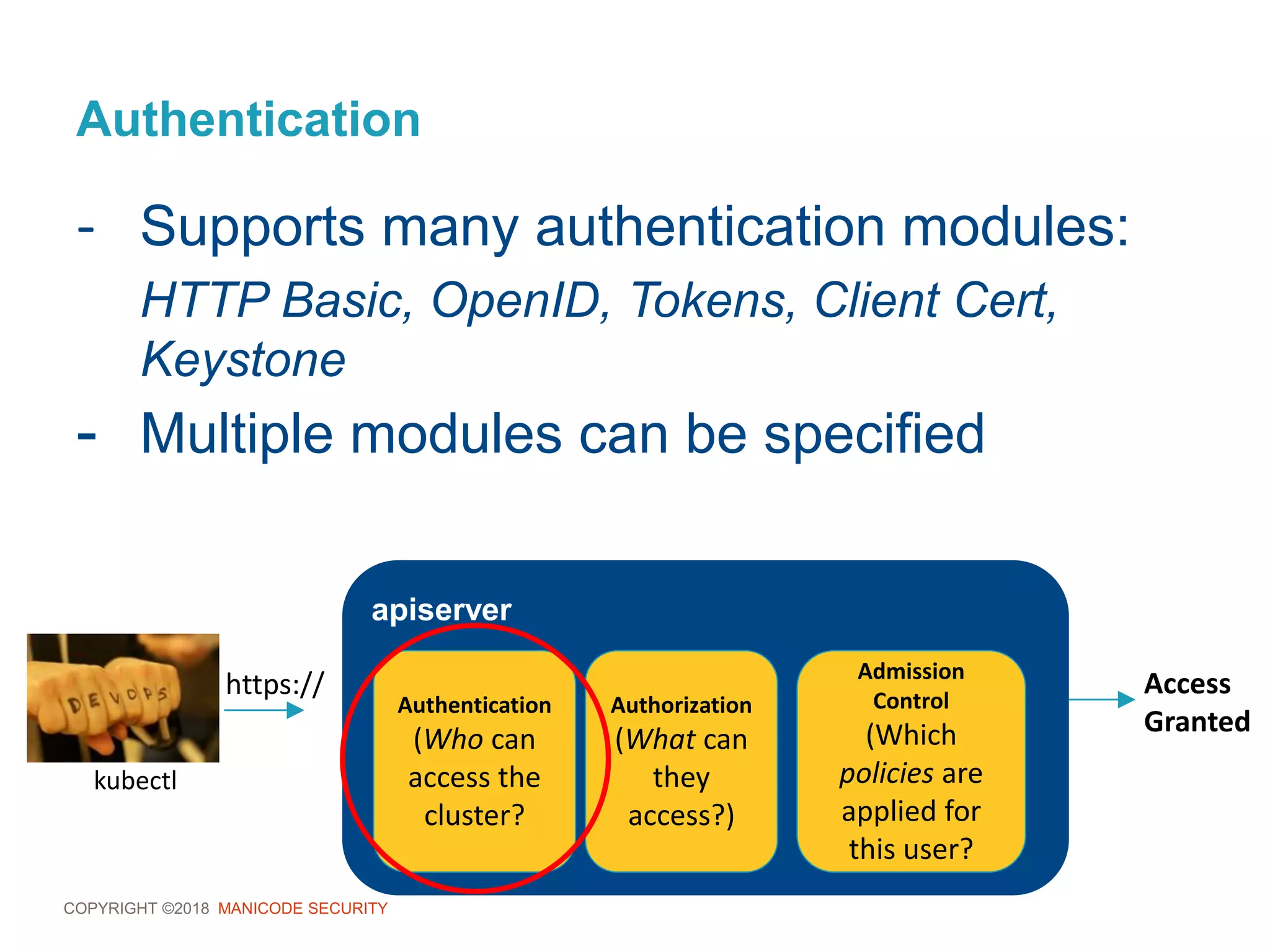
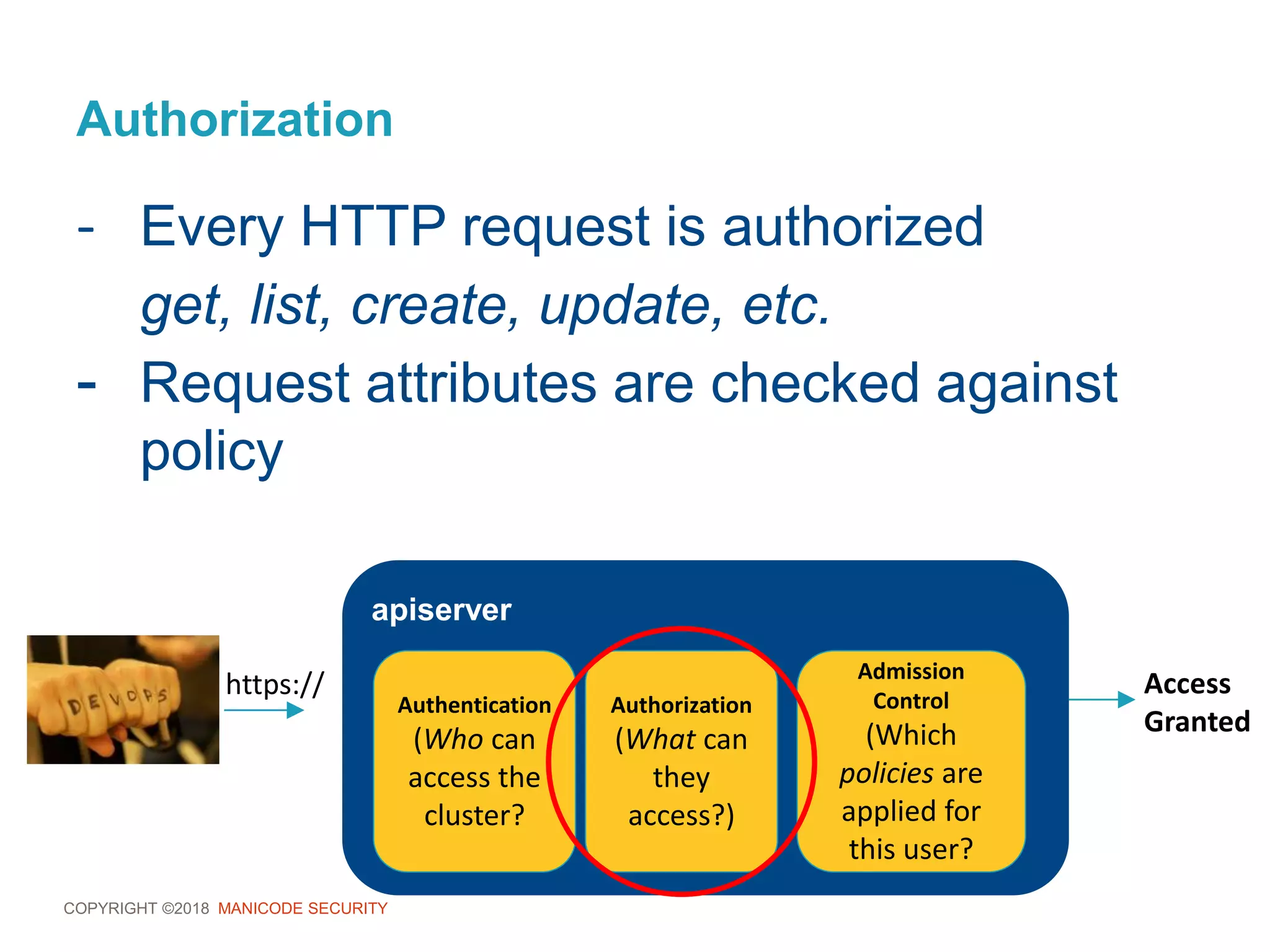
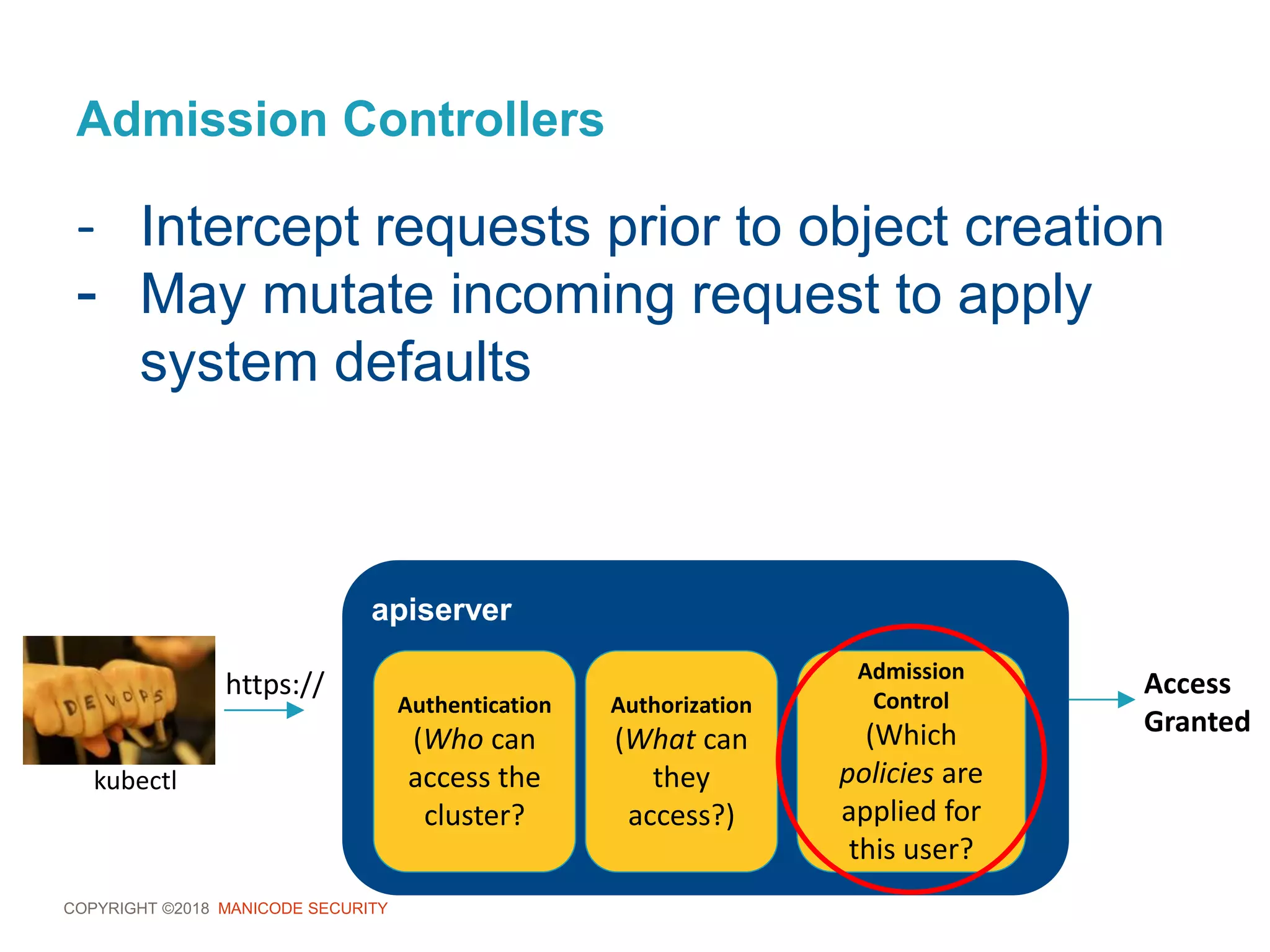
This document provides an overview of a training session on DevSecOps using Kubernetes. It includes background on the instructor and warnings about unauthorized hacking. The training covers topics like DevOps and DevSecOps processes and patterns, infrastructure as code, deploying containers securely, Kubernetes, and managing secrets and monitoring in Kubernetes. It encourages collaboration and discusses how to access lab materials through a GitHub repository.



























































![COPYRIGHT ©2018 MANICODE SECURITY
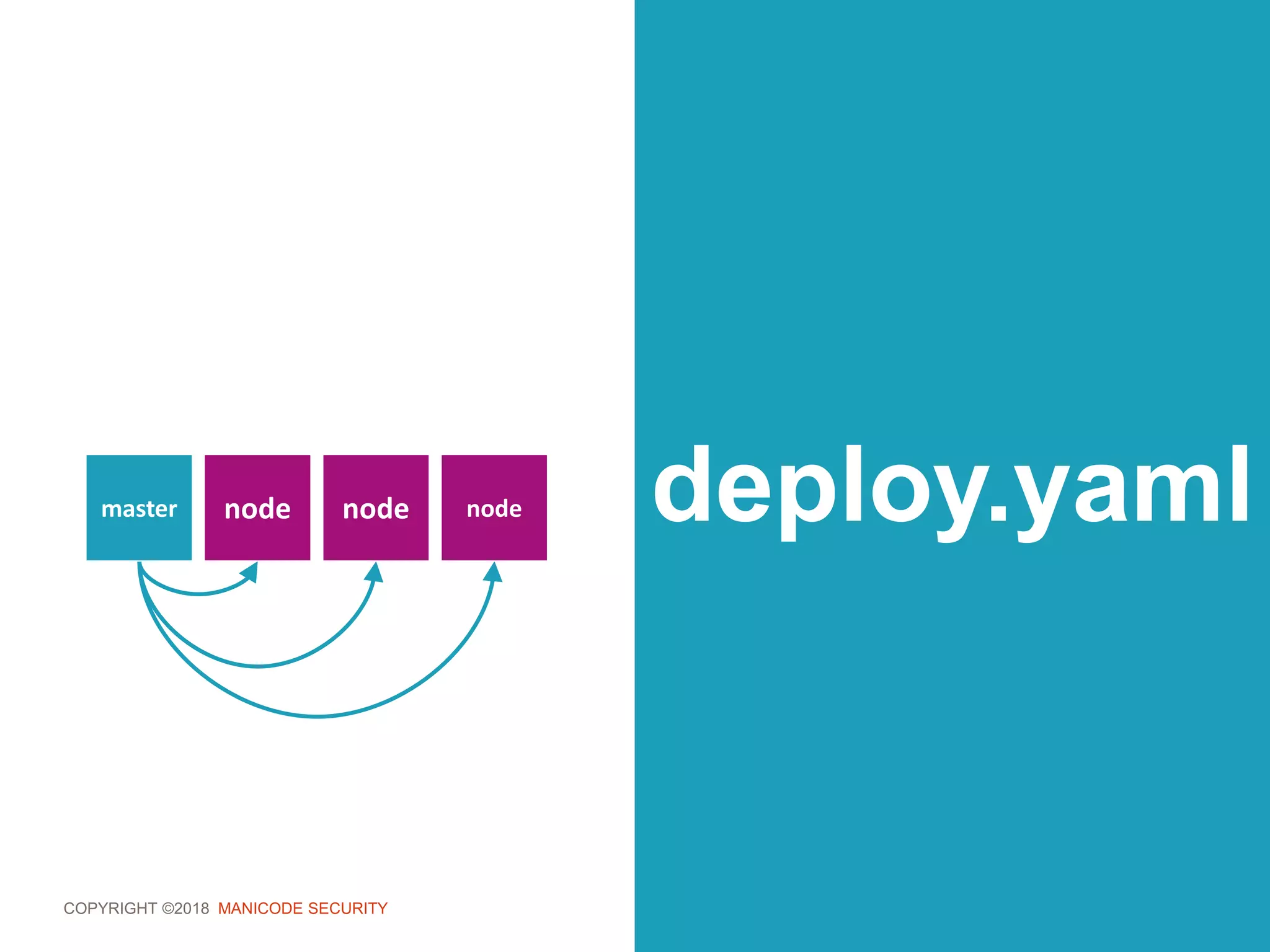
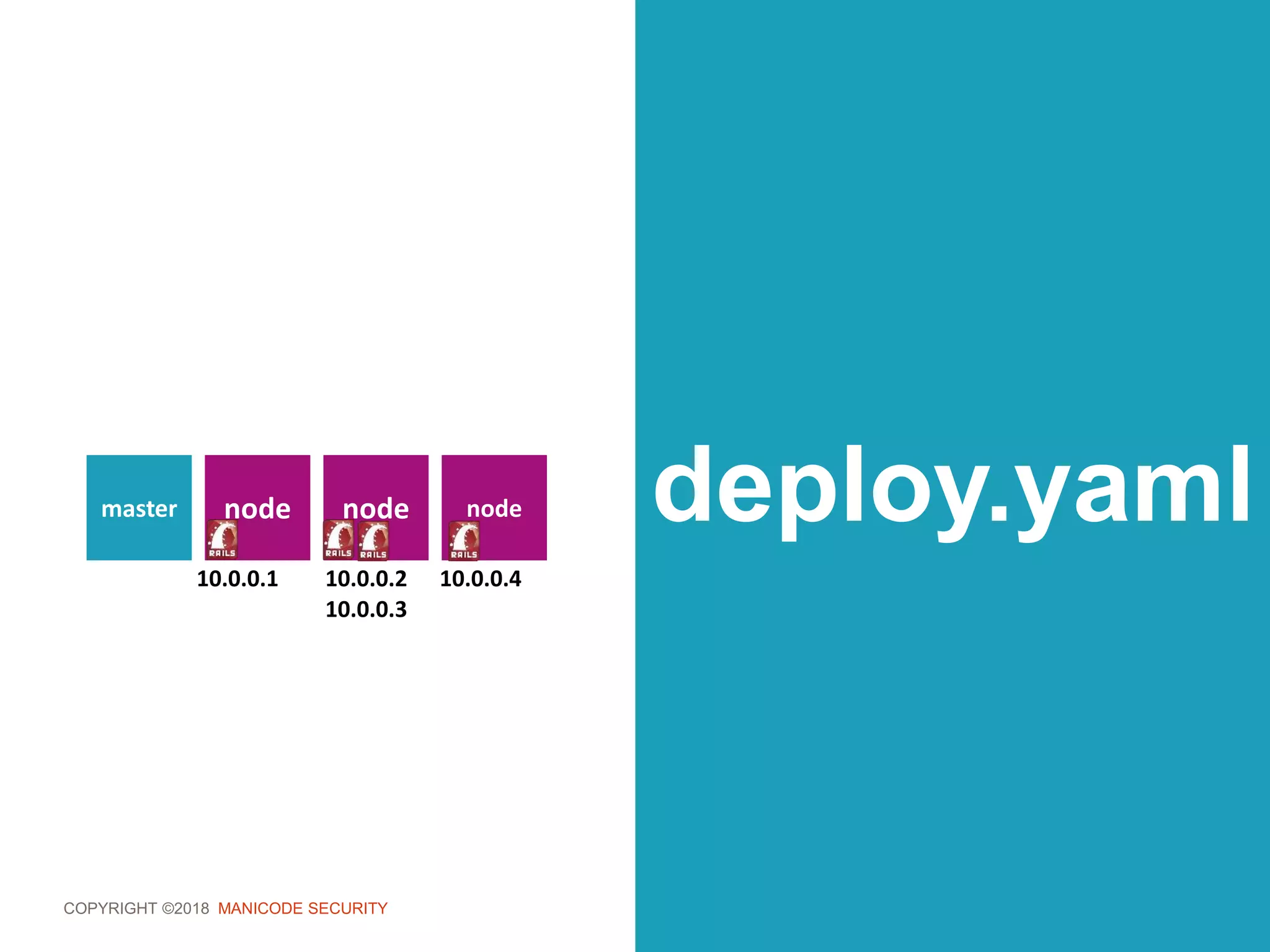
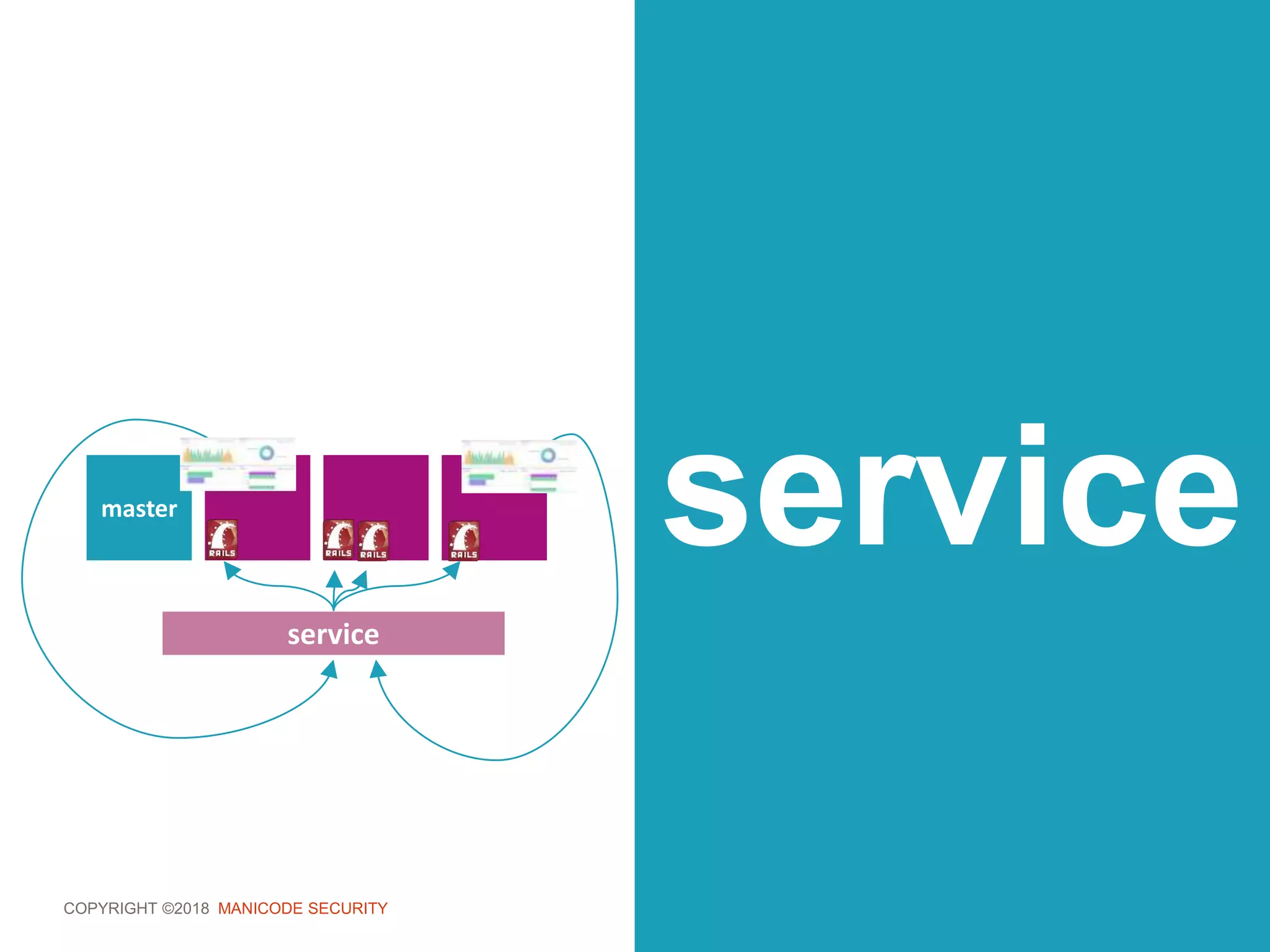
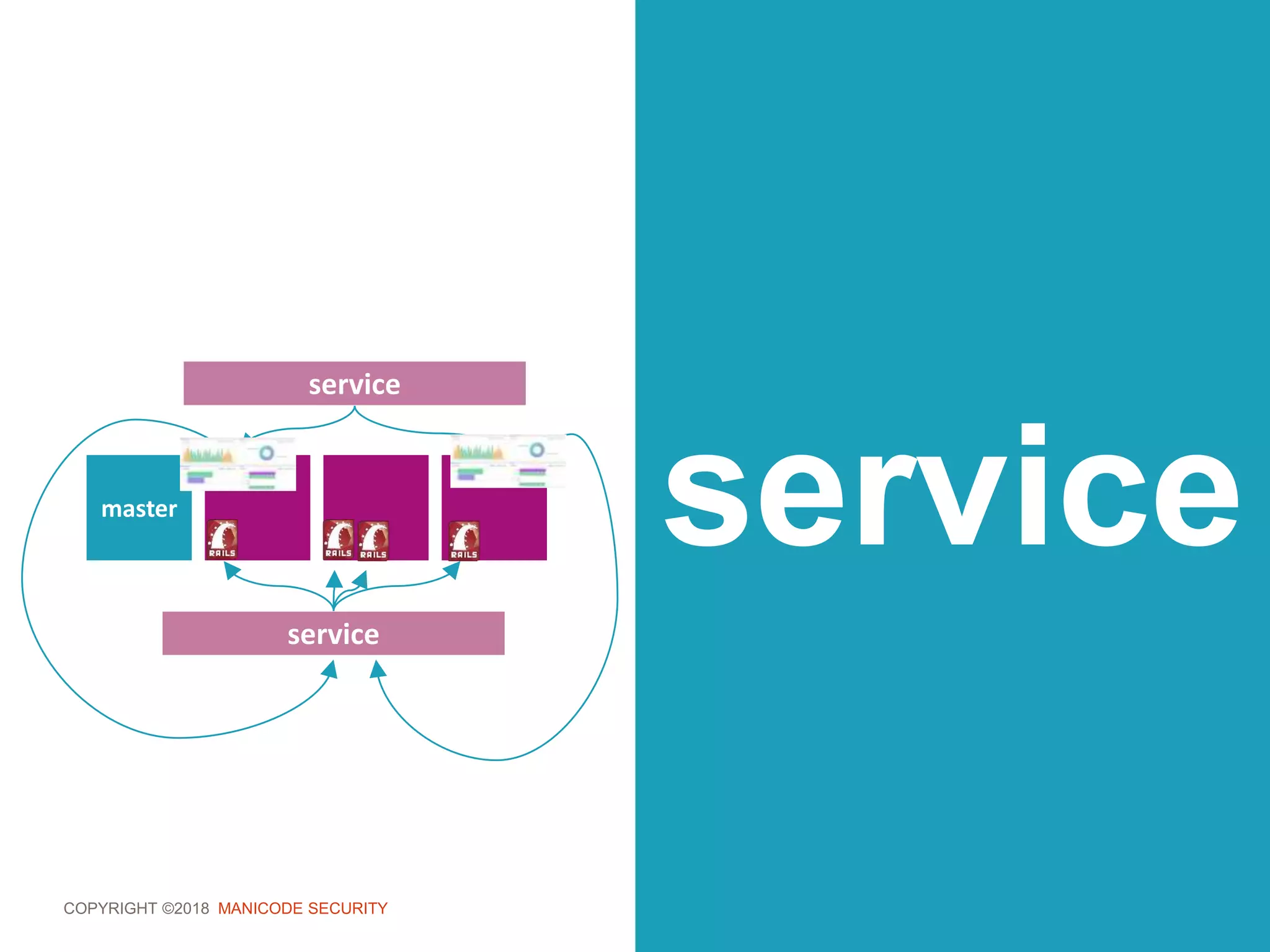
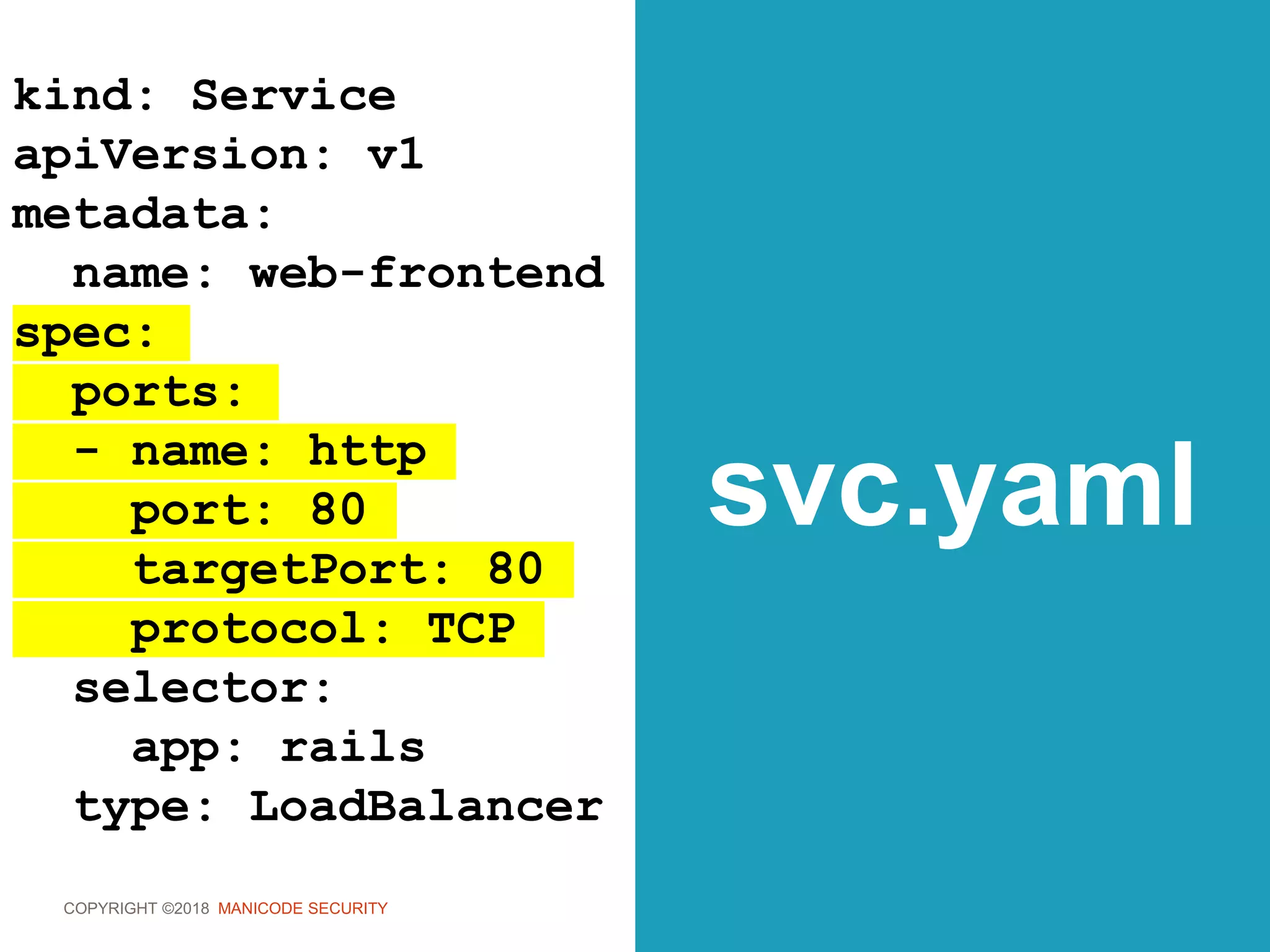
role.yaml
kind: Role
apiVersion:
rbac.authorization.k8s.io/v1
metadata:
namespace: development
name: pod-reader
rules:
- apiGroups: [""]
resources: [”pods"]
verbs: ["get", "list"]](https://image.slidesharecdn.com/owasp-sf-k8s-security-180904163521/75/OWASP-Bay-Area-Meetup-DevSecOps-the-Kubernetes-Way-166-2048.jpg)
![COPYRIGHT ©2018 MANICODE SECURITY
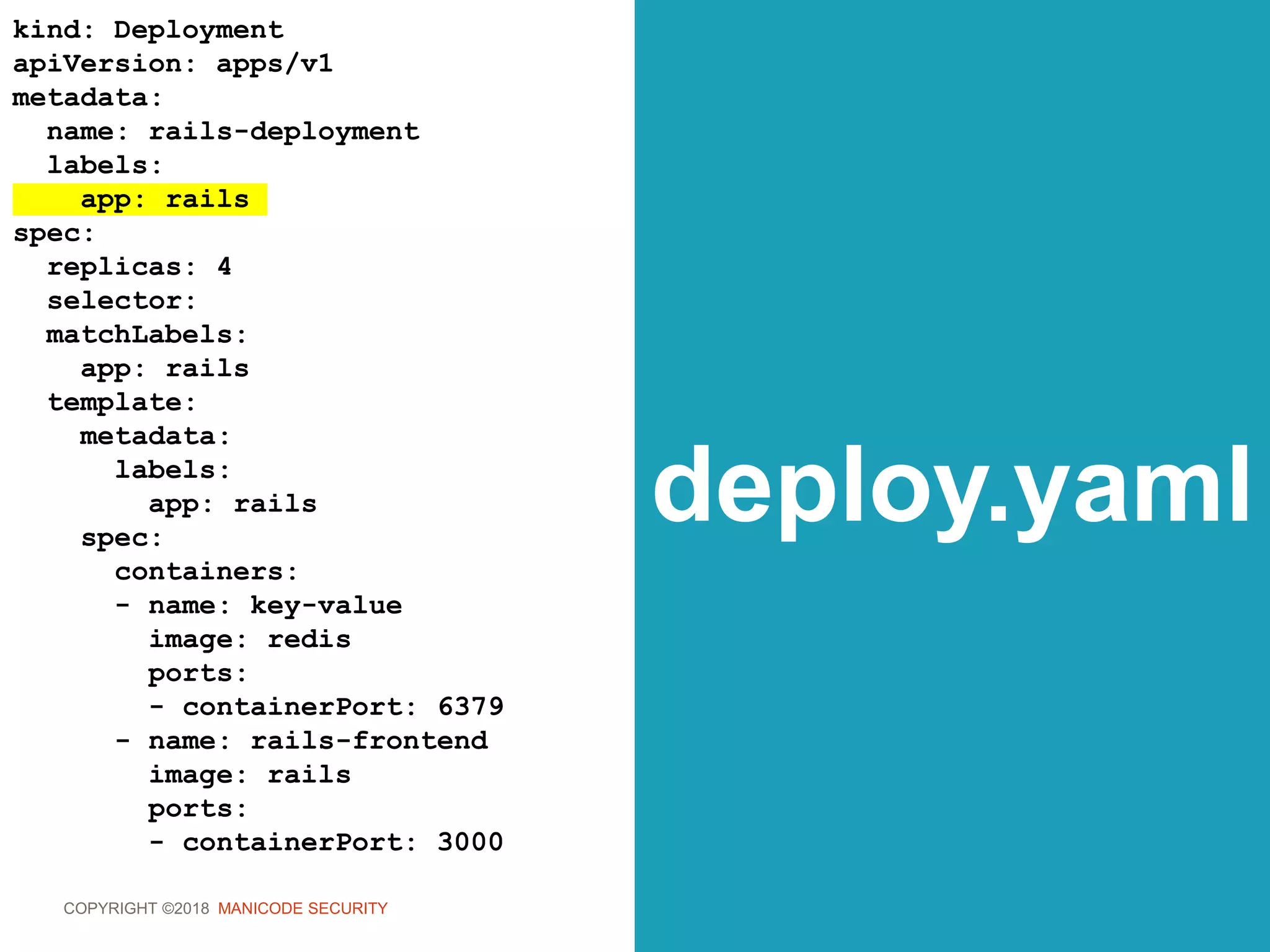
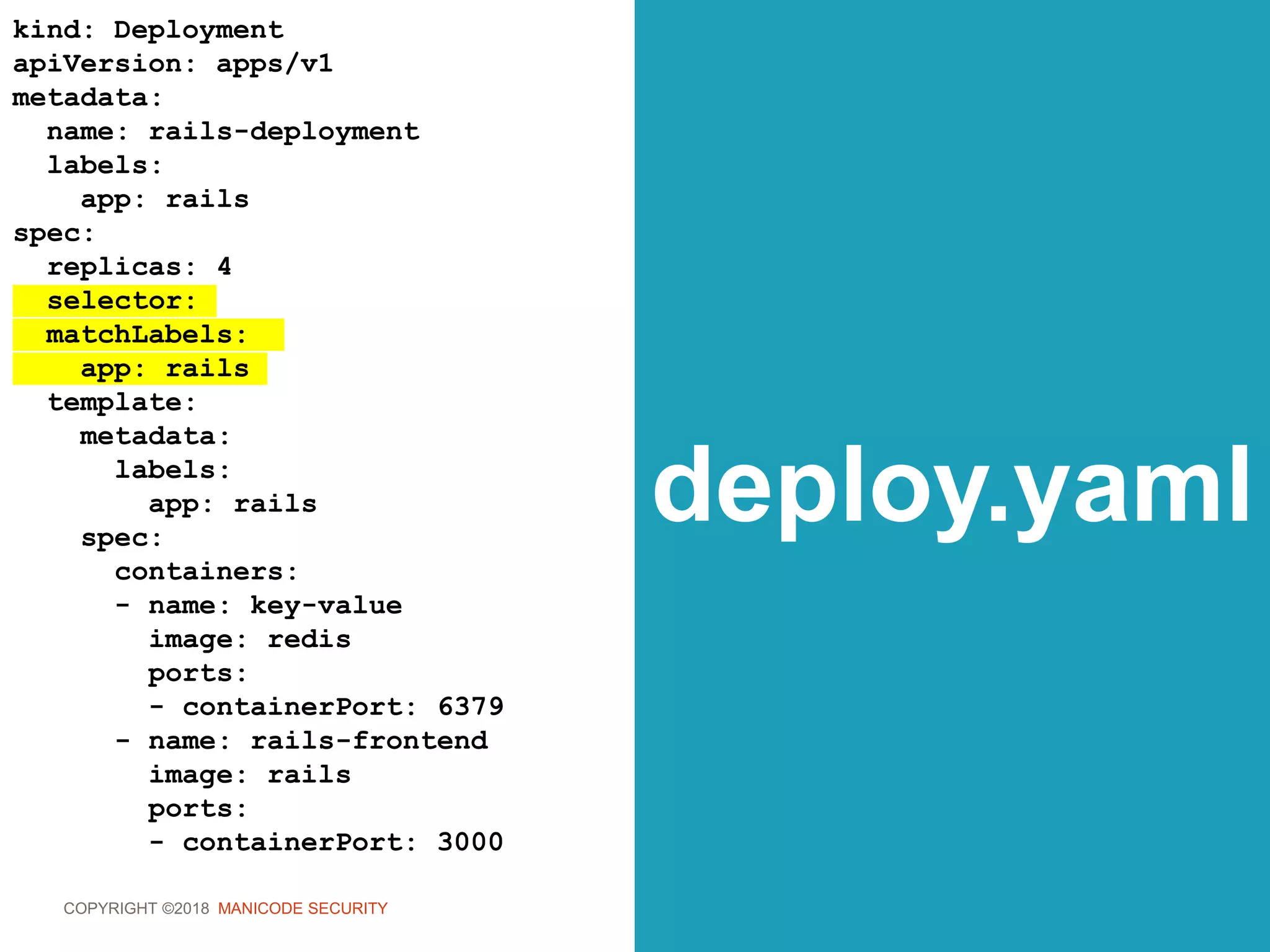
role.yaml
kind: Role
apiVersion:
rbac.authorization.k8s.io/v1
metadata:
namespace: development
name: dev-admin
rules:
- apiGroups: [”*"]
resources: [”*"]
verbs: [”*"]](https://image.slidesharecdn.com/owasp-sf-k8s-security-180904163521/75/OWASP-Bay-Area-Meetup-DevSecOps-the-Kubernetes-Way-168-2048.jpg)
![COPYRIGHT ©2018 MANICODE SECURITY
cr.yaml
kind: ClusterRole
apiVersion:
rbac.authorization.k8s.io/v1
metadata:
name: pod-reader
rules:
- apiGroups: [""]
resources: [”pods"]
verbs: ["get", "list"]](https://image.slidesharecdn.com/owasp-sf-k8s-security-180904163521/75/OWASP-Bay-Area-Meetup-DevSecOps-the-Kubernetes-Way-170-2048.jpg)







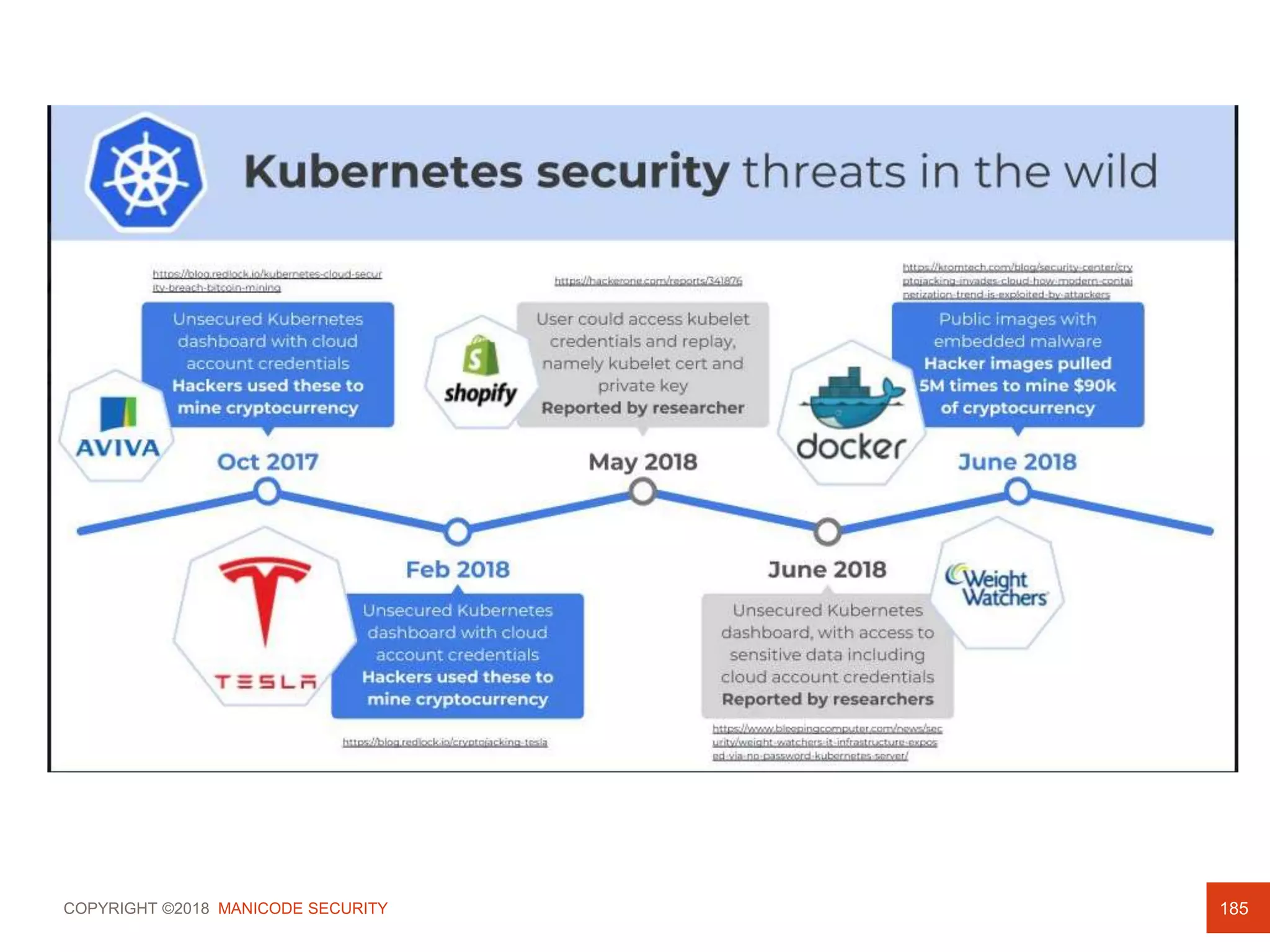
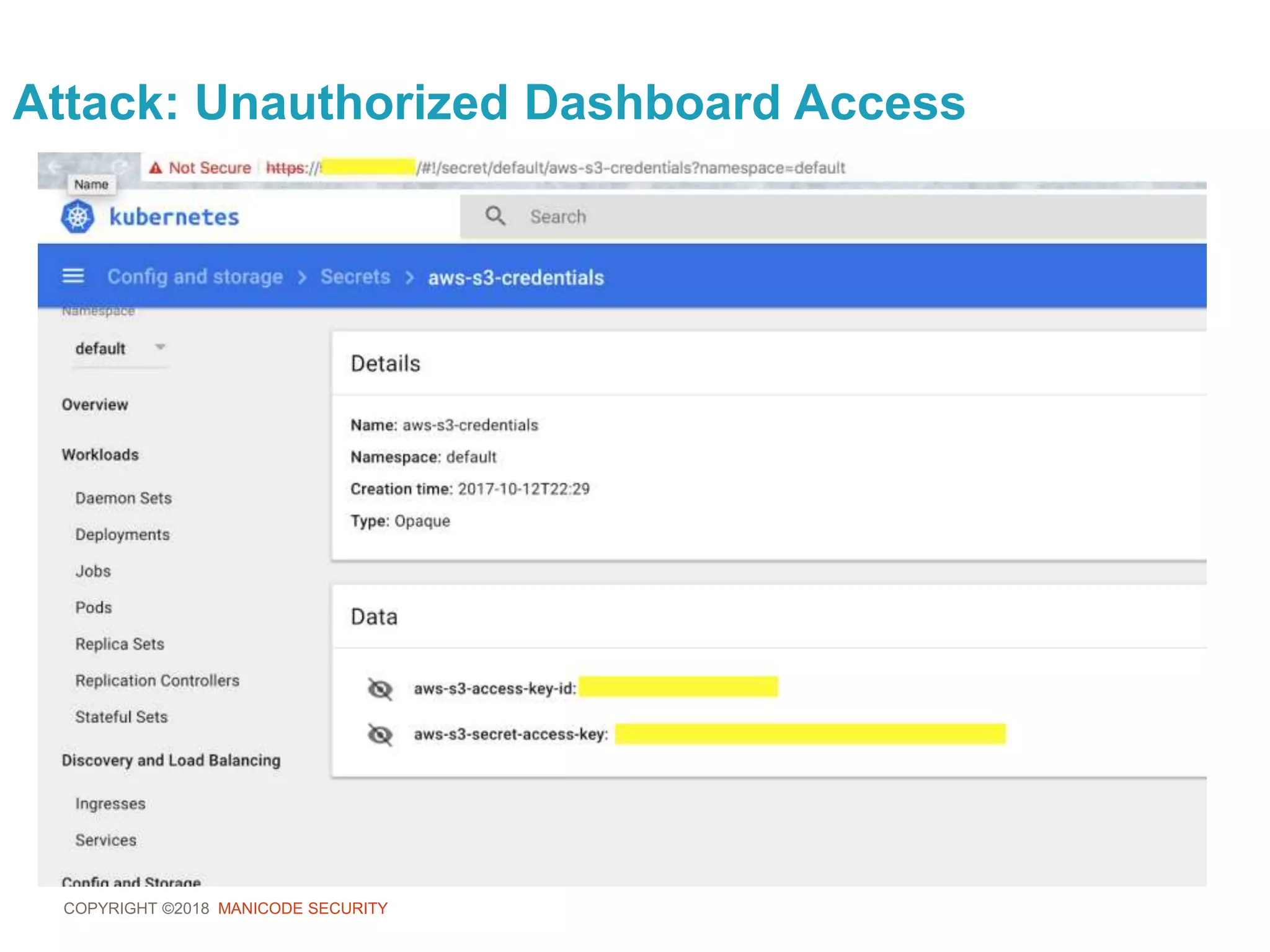

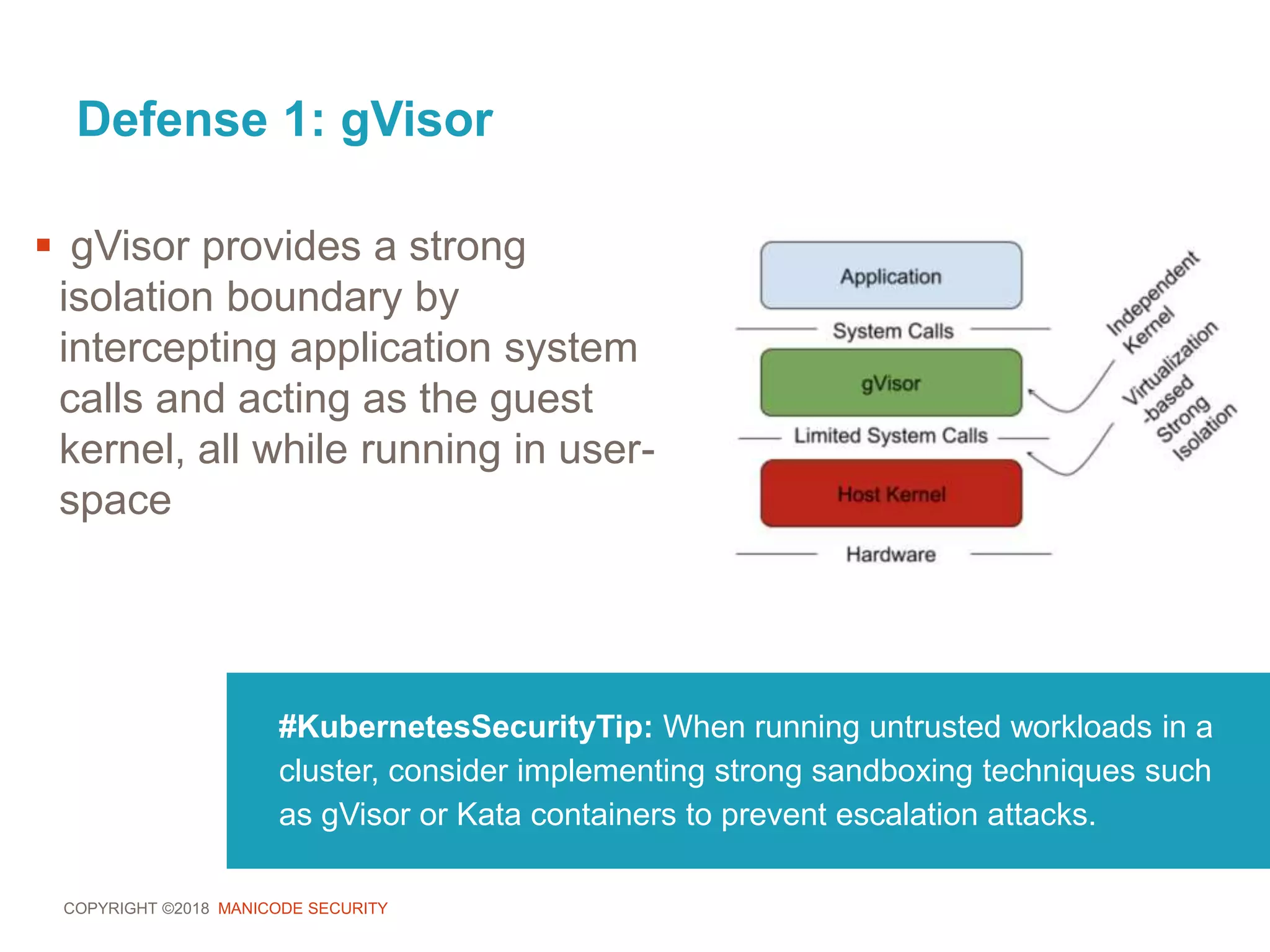
![COPYRIGHT ©2018 MANICODE SECURITY
priv-pod.yaml
apiVersion: v1
kind: Pod
metadata:
name: priv-pod
spec:
securityContext:
privileged: true
containers:
- name: pause
image: k8s.gcr.io/pause
securityContext:
capabilities:
add: ["NET_ADMIN", "SYS_TIME"]](https://image.slidesharecdn.com/owasp-sf-k8s-security-180904163521/75/OWASP-Bay-Area-Meetup-DevSecOps-the-Kubernetes-Way-192-2048.jpg)

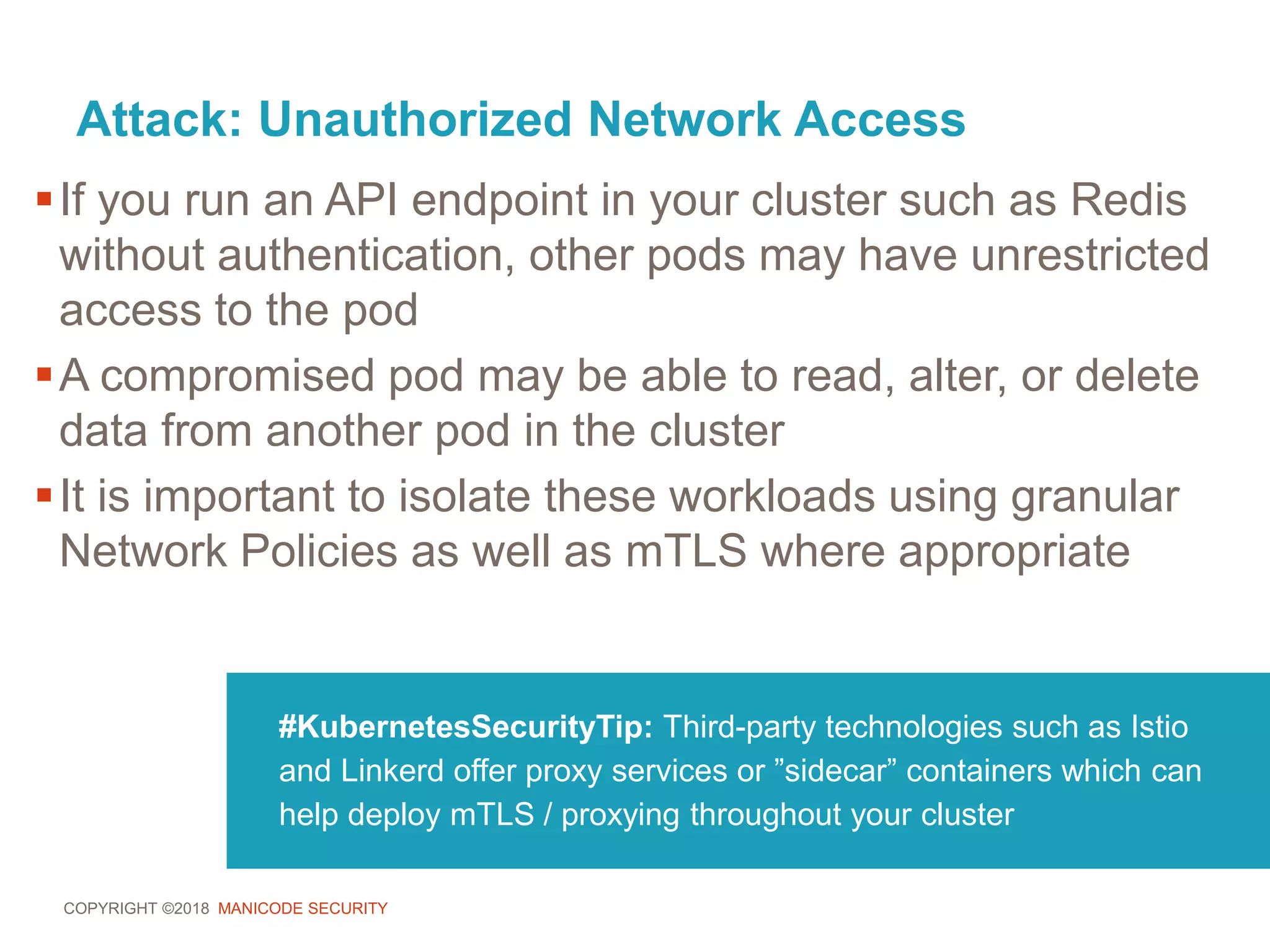
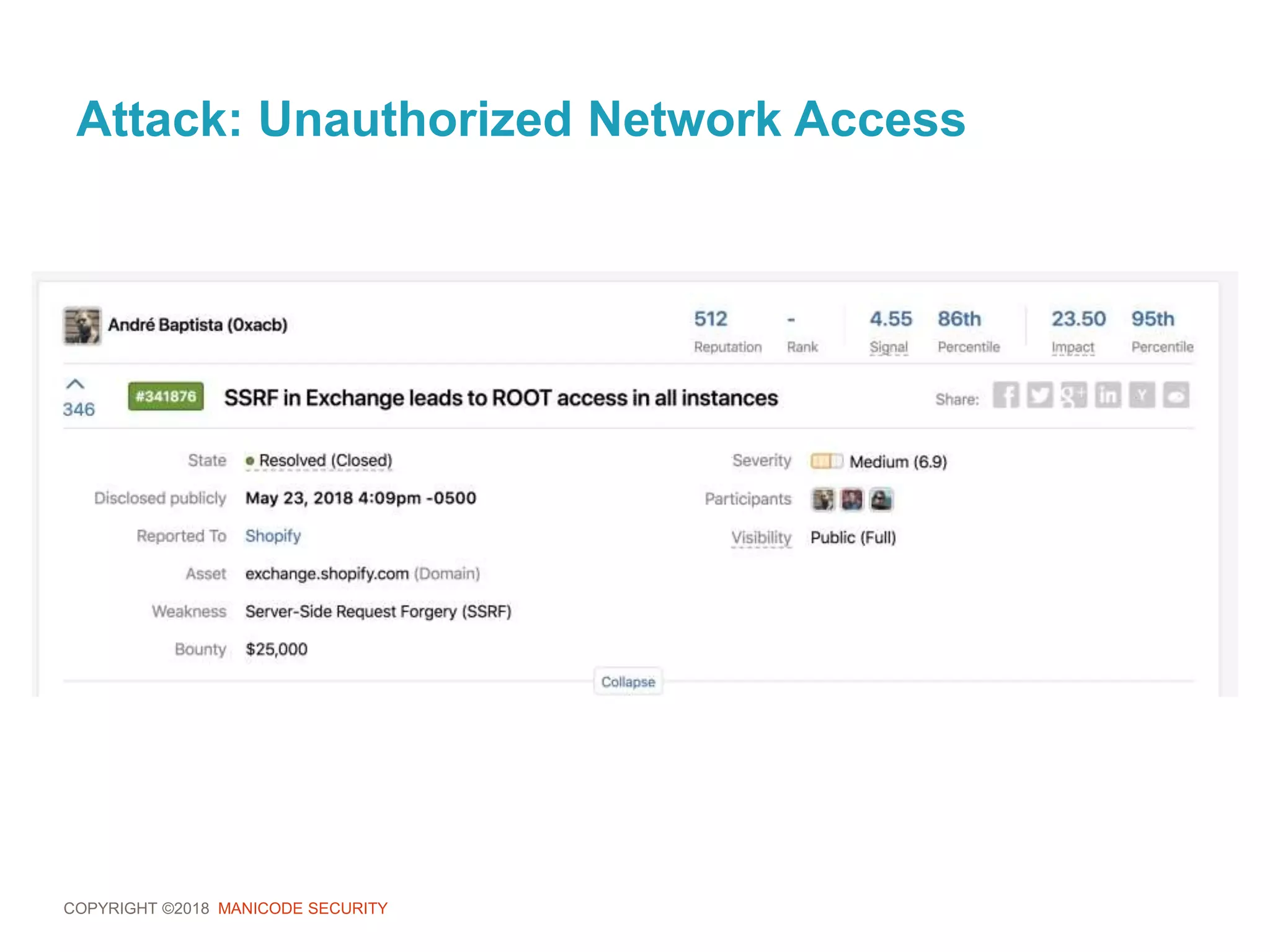

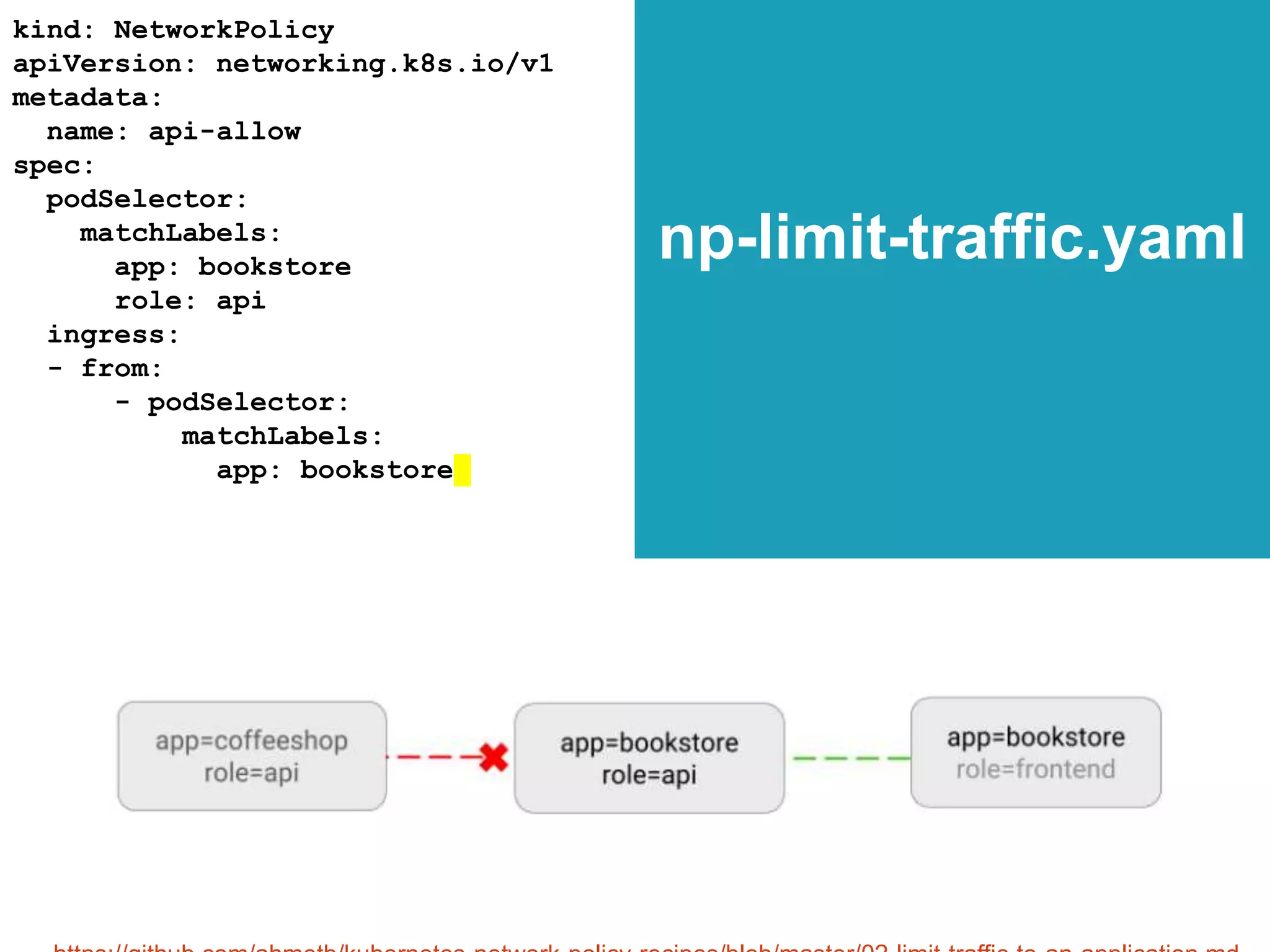
![COPYRIGHT ©2018 MANICODE SECURITY
np-deny-all.yaml
kind: NetworkPolicy
apiVersion: networking.k8s.io/v1
metadata:
name: web-deny-all
spec:
podSelector:
matchLabels:
app: web
ingress: []
https://github.com/ahmetb/kubernetes-network-policy-recipes/blob/master/01-deny-all-traffic-to-an-application.md](https://image.slidesharecdn.com/owasp-sf-k8s-security-180904163521/75/OWASP-Bay-Area-Meetup-DevSecOps-the-Kubernetes-Way-201-2048.jpg)
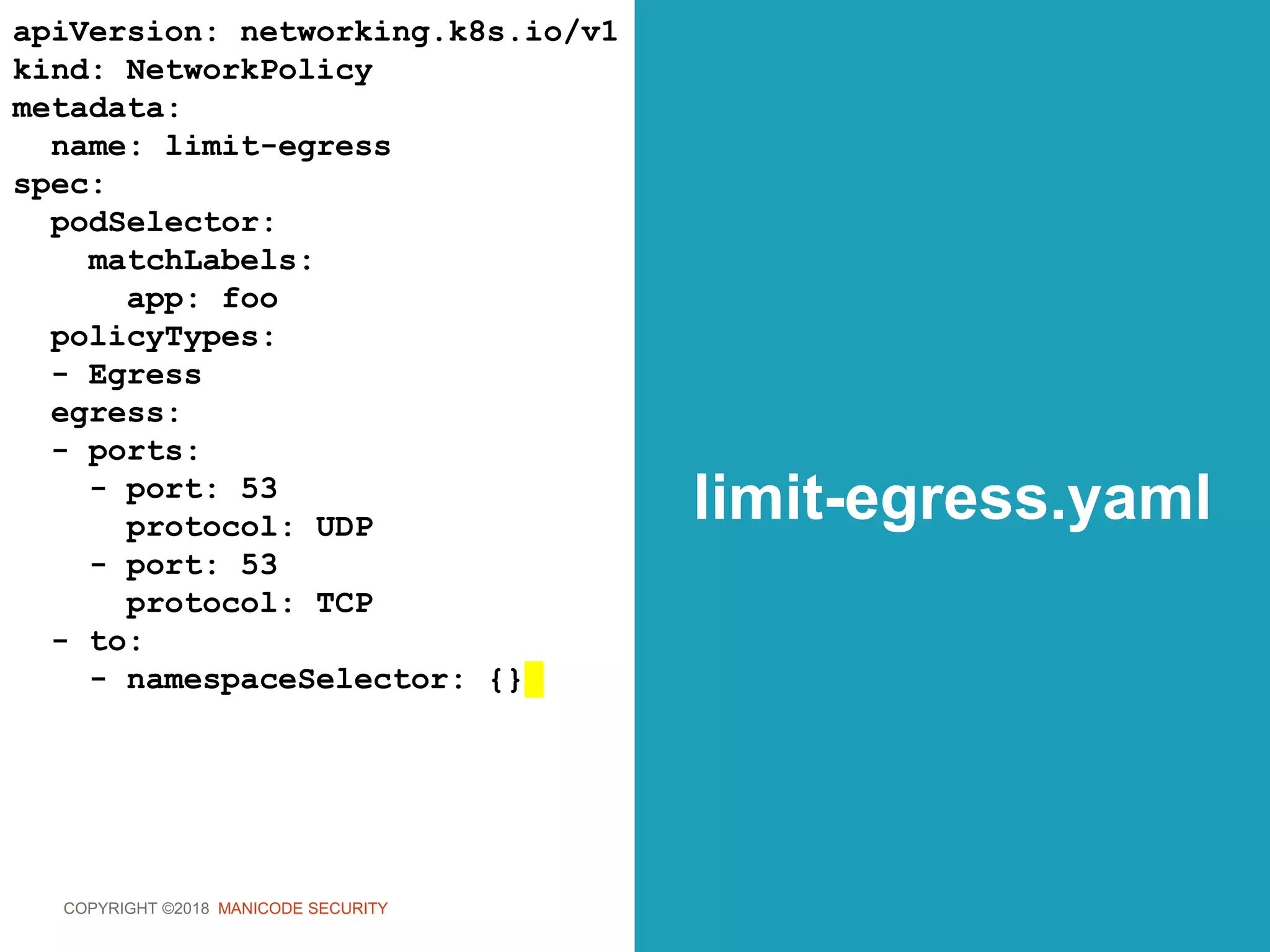







![COPYRIGHT ©2018 MANICODE SECURITY
audit.yaml
apiVersion: audit.k8s.io/v1beta1 #
kind: Policy
rules:
# Log configmap and secret changes in all
other namespaces at the Metadata level.
- level: Metadata
resources:
- group: "" # core API group
resources: ["secrets", "configmaps”]](https://image.slidesharecdn.com/owasp-sf-k8s-security-180904163521/75/OWASP-Bay-Area-Meetup-DevSecOps-the-Kubernetes-Way-223-2048.jpg)