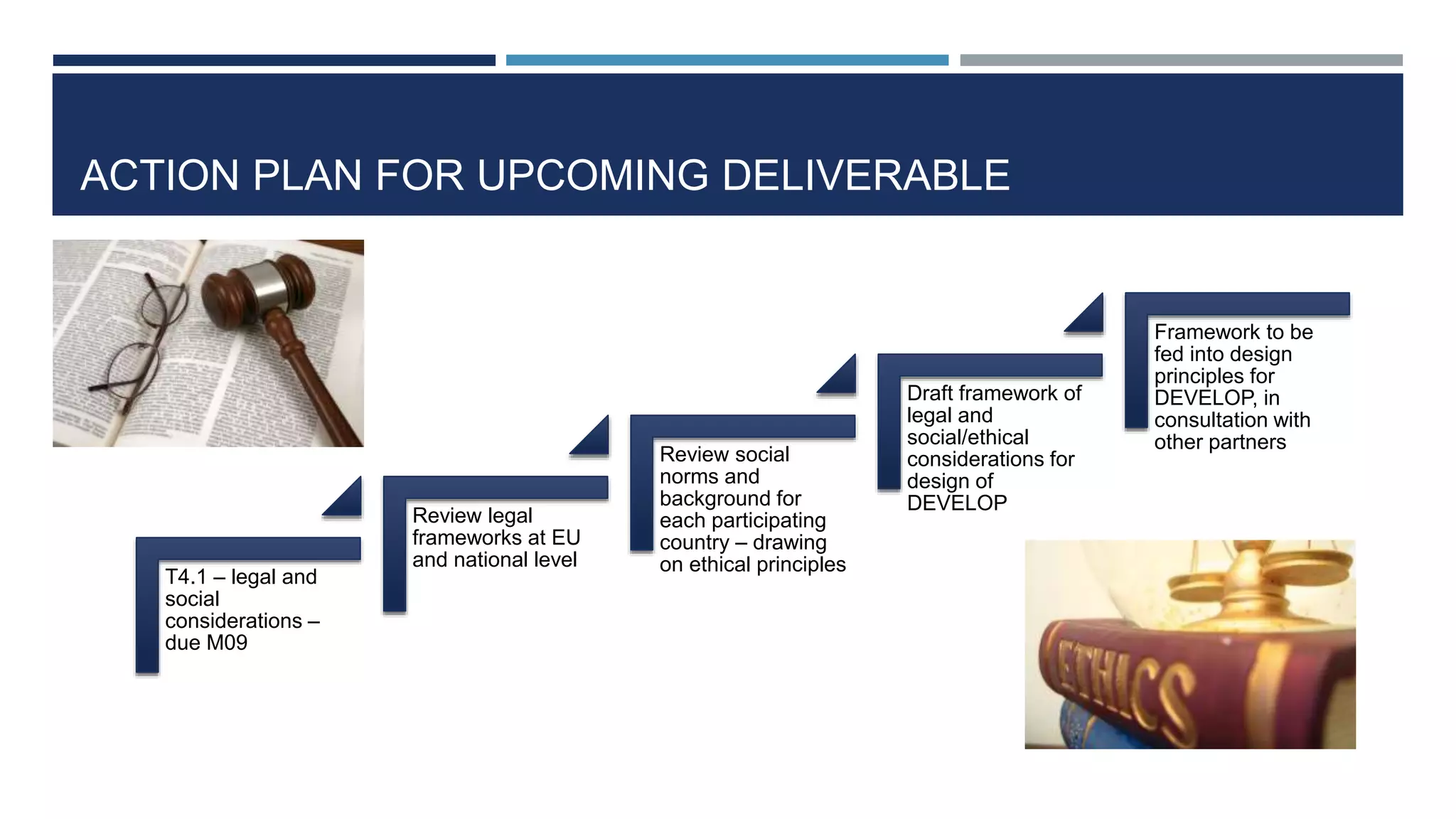
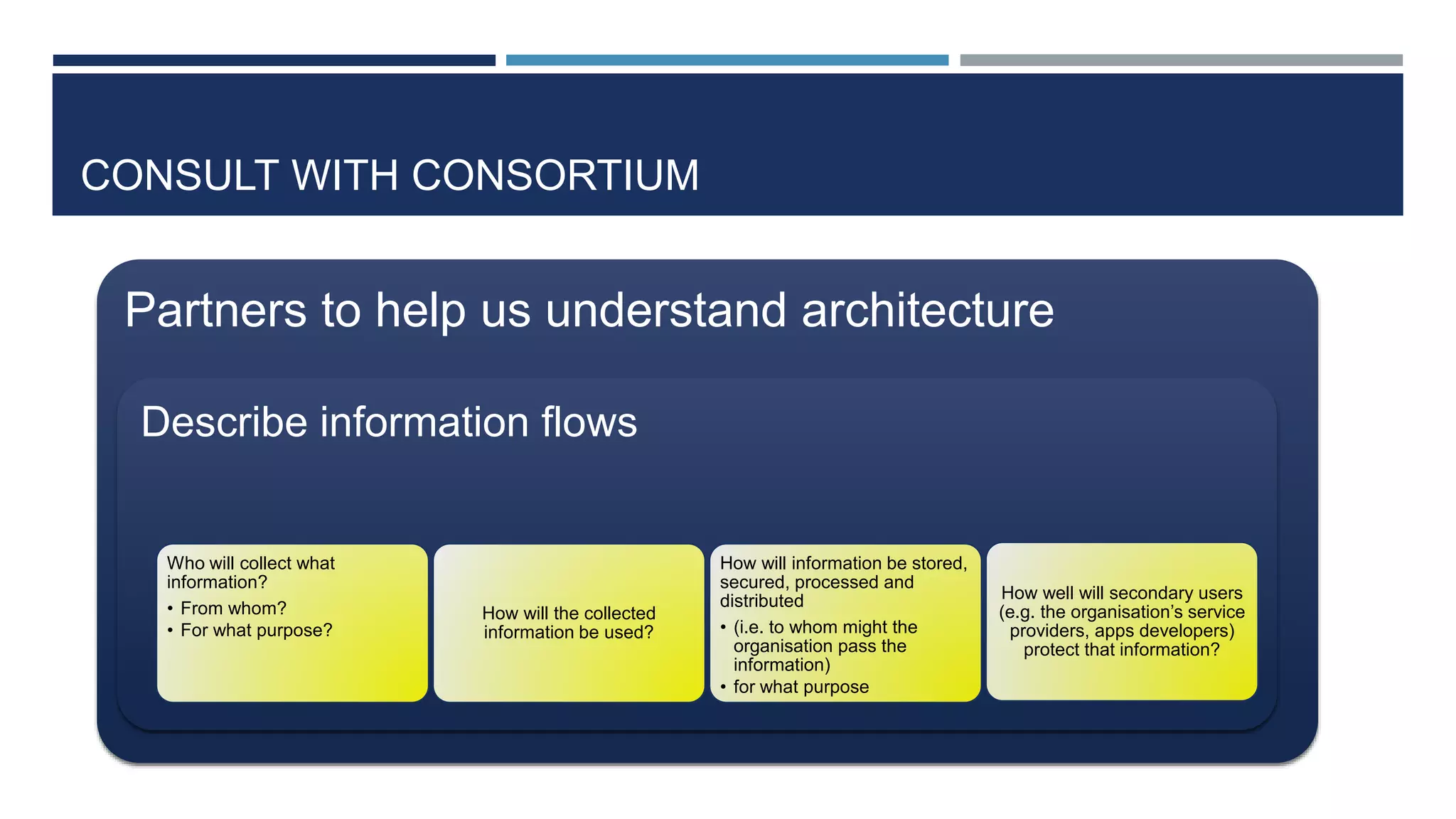
This document discusses ethical, privacy, and data protection considerations for a project called DEVELOP. It outlines relevant ethical values like autonomy, dignity, inclusion and beneficence. It also discusses the right to privacy under the European Convention on Human Rights and EU data protection law. The document provides an overview of the EU Data Protection Directive and the new General Data Protection Regulation. It raises specific privacy and data protection issues like informed consent, data minimization, and anonymity that DEVELOP should address.