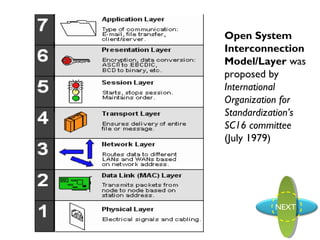
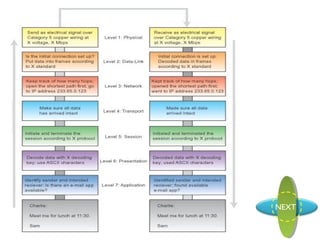
The document proposes the Open System Interconnection Model/Layer, which was proposed by the International Organization for Standardization’s SC16 committee in July 1979. The OSI model defines 7 layers for network communication: Physical, Data Link, Network, Transport, Session, Presentation, and Application layer. Each layer has a specific function and provides services to the layer above it.