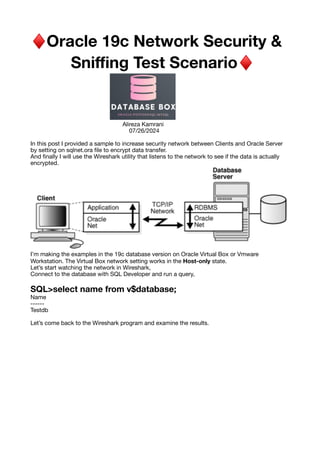
This document discusses a method to secure network communication between clients and Oracle 19c databases by configuring the sqlnet.ora file for data encryption. It details a step-by-step process to test and confirm that data is encrypted during transmission using the Wireshark utility. The document also explains the parameters required for encryption settings on both client and server sides, emphasizing that configuration can be done on either side to enable secure connections.

![As shown in the picture, the query appears encrypted after the query we run. When we look at
the tra
ffi
c in the Wireshark program as before, the query executed on the client side became
encrypted.
After you close the connection, let’s search all .trc
fi
les on the client. The trace
fi
le created at the
time of the connection will tell us whether the connection is encrypted.
Look for the word “encryption” in these
fi
le.
This result indicates that the data is encrypted over the network with the AES128 algorithm and
data integrity is ensured by the SHA1 algorithm.
Here I present some information about encryption settings:
Con
fi
guring for Network Encryption
The con
fi
guration for Network Encryption is de
fi
ned in the “sqlnet.ora”
fi
le on the client and server
side. Before con
fi
guring, Oracle Net installation must be done on both the server and client side.
Con
fi
guration can be done by replacing the
fi
le “sqlnet.ora” with the text editor or with the
netmgr program.
Two separate parameters are used on the server side.
SQLNET.ENCRYPTION_SERVER = [accepted | rejected | requested | required ]
SQLNET.ENCYRPTION_TYPES_SERVER = (algorithm name)
The parameters used by the client side,
SQLNET.ENCRYPTION_CLIENT = [ accepted | rejected | requested | required ]
SQLNET.ENCYRPTION_TYPES_CLIENT = ( algorithm name )
The SQLNET.ENCRYPTION_SERVER and SQLNET.ENCRYPTION_CLIENT parameters are
parameters that determine whether to encrypt the client and the server.
This parameter can take the following values,
• REJECTED
• ACCEPTED
• REQUESTED
• REQUIRED
The default value is ACCEPTED.](https://image.slidesharecdn.com/oracle19cnetworksecuritysniffingtestscenario-240726132226-18bb5b44/85/Oracle-19c-Network-Security-Sniffing-Test-Scenario-3-320.jpg)
