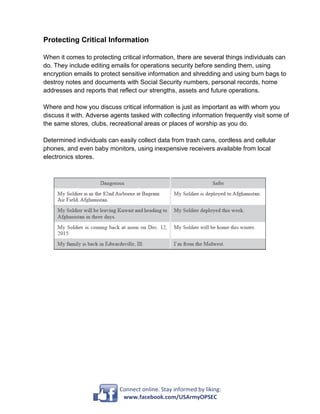
Service members, government employees, and their families should be mindful of sharing "critical information" such as details about military capabilities, activities, limitations, and intentions. Critical information includes details about unit missions and deployments, personnel transactions like pay information, and references to unit morale issues. While this information may seem insignificant, adversaries can piece together critical details to understand what a military unit is doing and planning. Individuals should protect critical information by editing emails for security, using encrypted emails, and properly destroying documents with sensitive details through shredding or burn bags. Where and with whom critical information is discussed is important, as adversaries can collect data even from public places, phones, and devices using basic receivers.