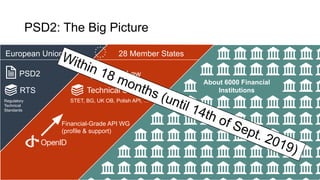
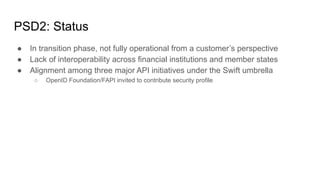
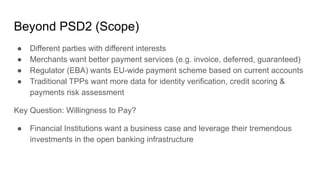
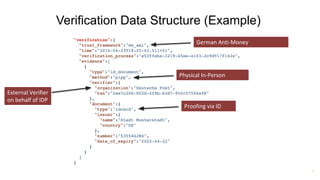
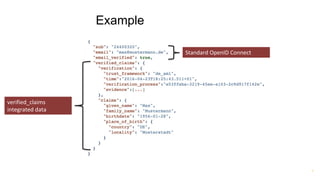
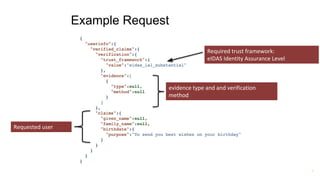
Torsten Lodderstedt is the CTO of yes.com, an open banking ecosystem. He discusses open banking prior to PSD2, including challenges like screen scraping. PSD2 obliges financial institutions to provide access to account information and payment initiation to authorized third parties. Beyond PSD2, different parties have differing interests. Identity is important for digital society. Financial institutions can leverage verified identity data as an identity provider and authentication service. OpenID Connect can represent verified identity claims with metadata for legal compliance and international interoperability. This representation allows for privacy-preserving inquiries.