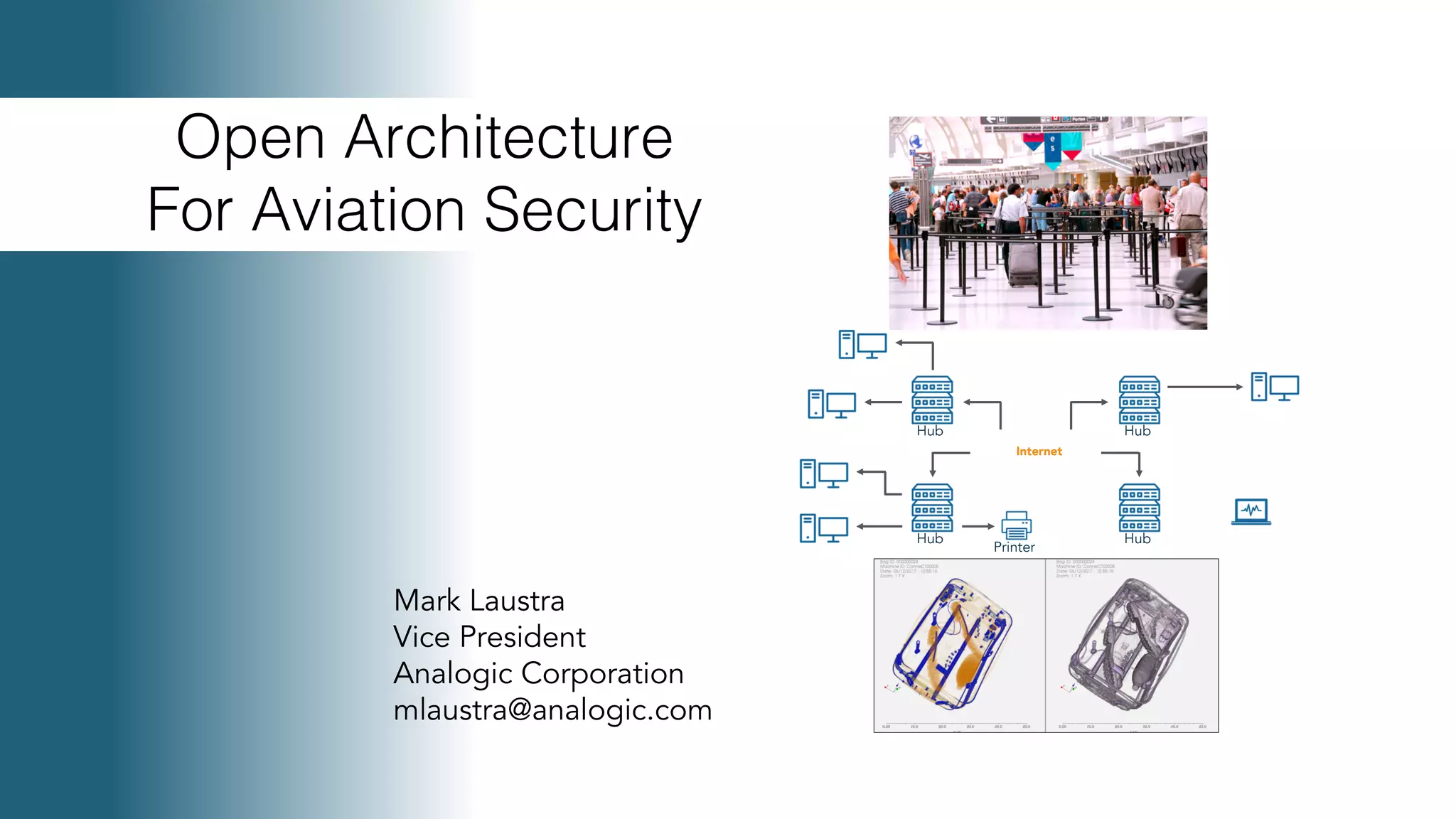
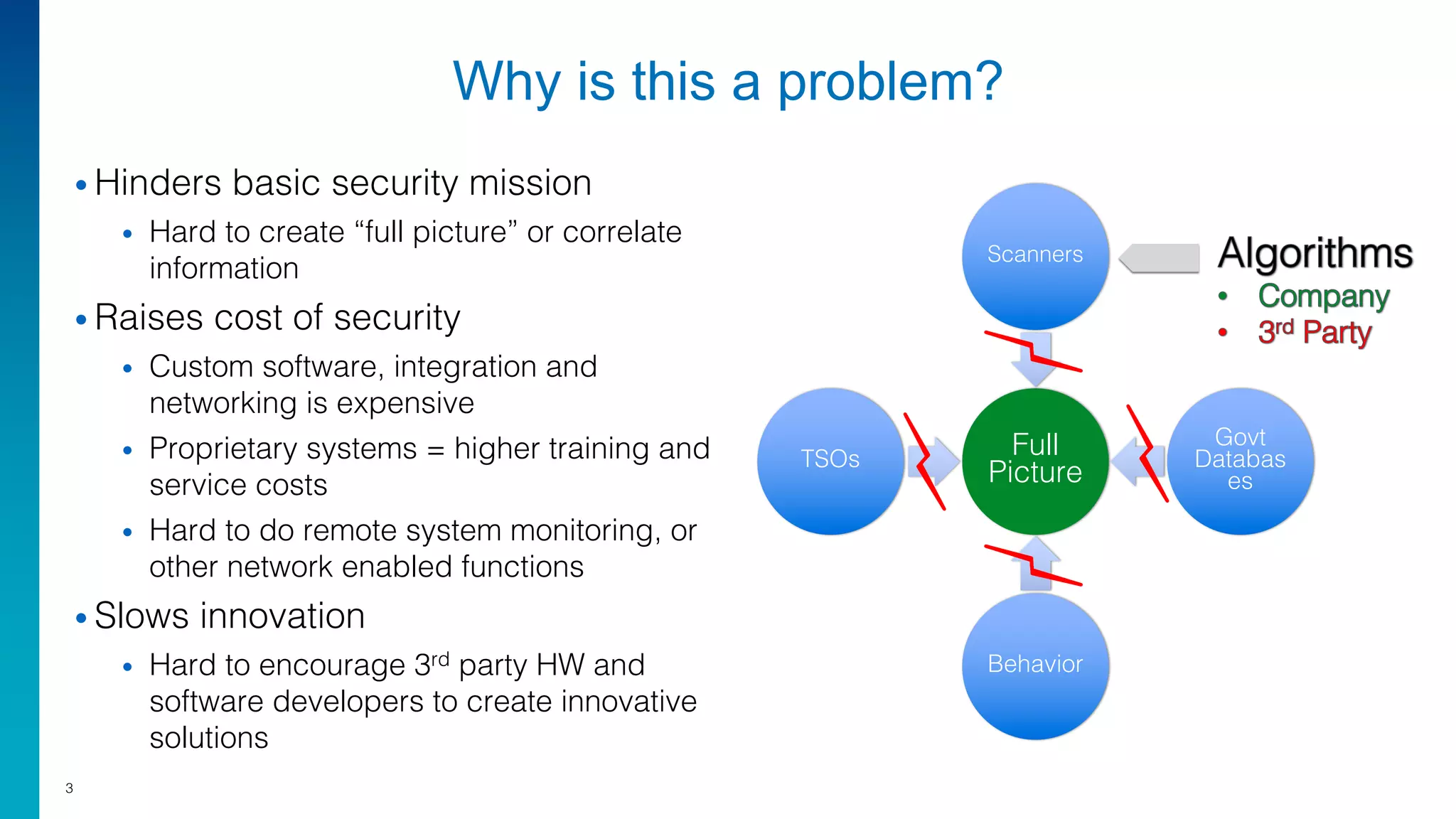
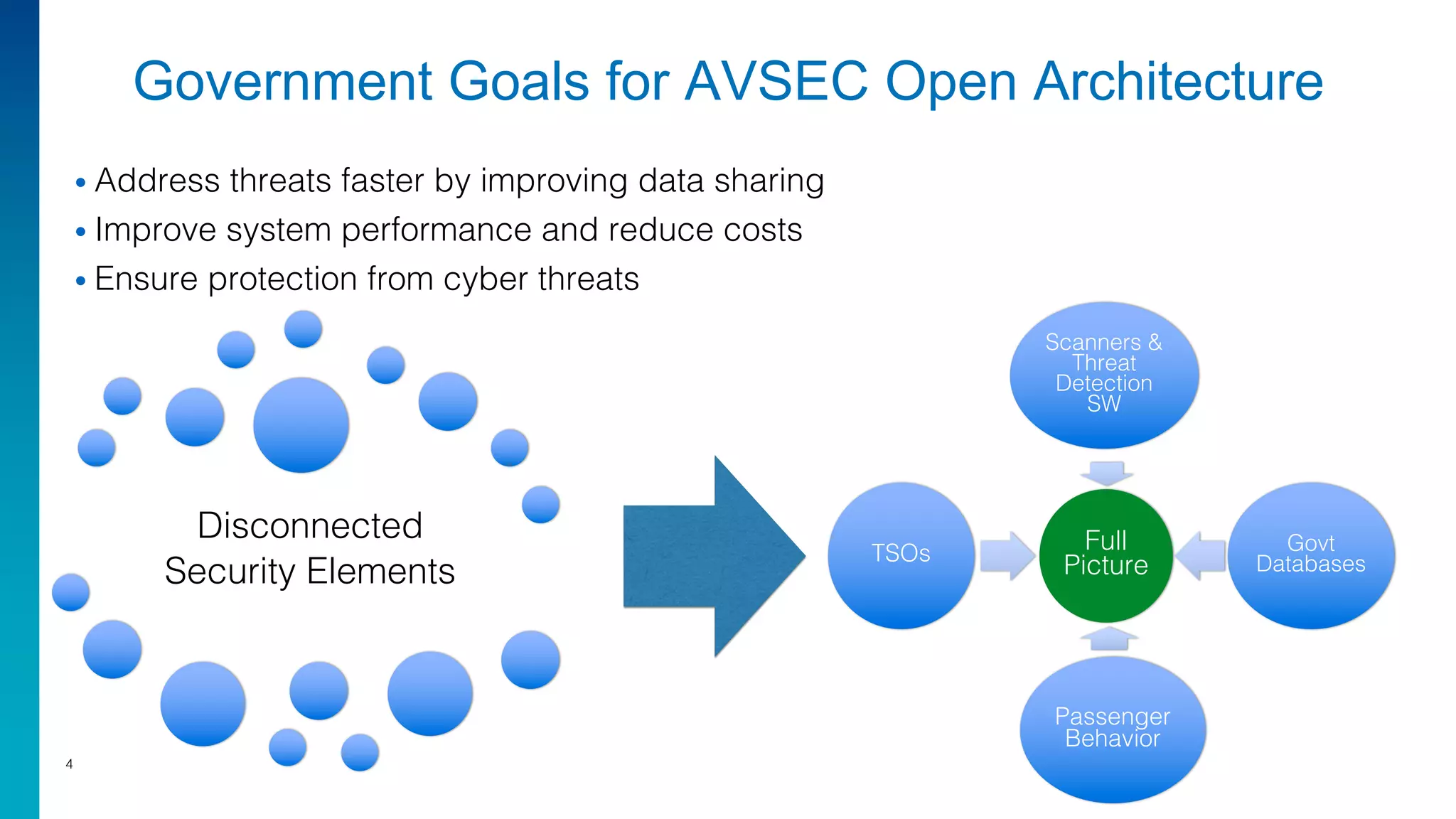
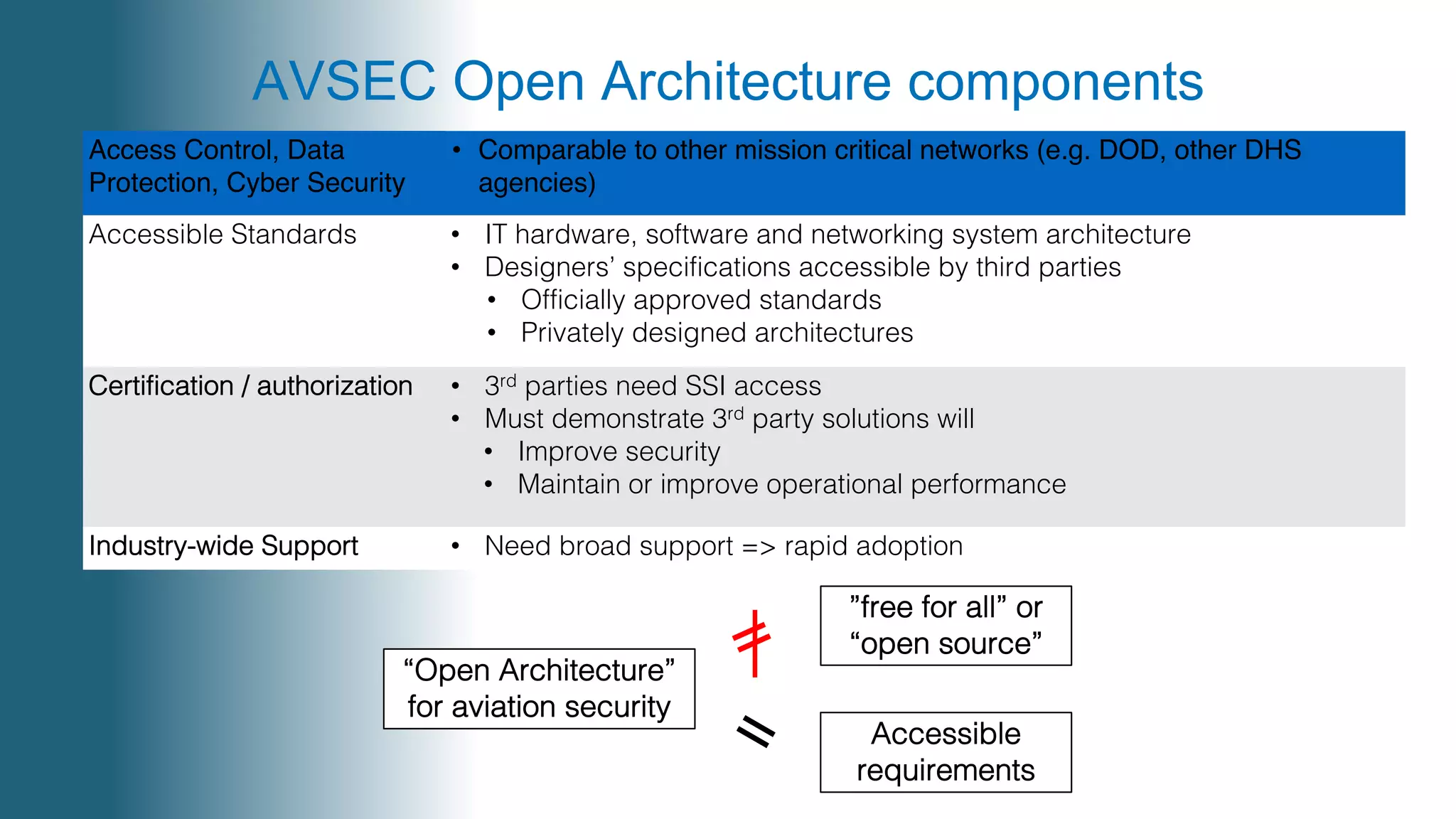
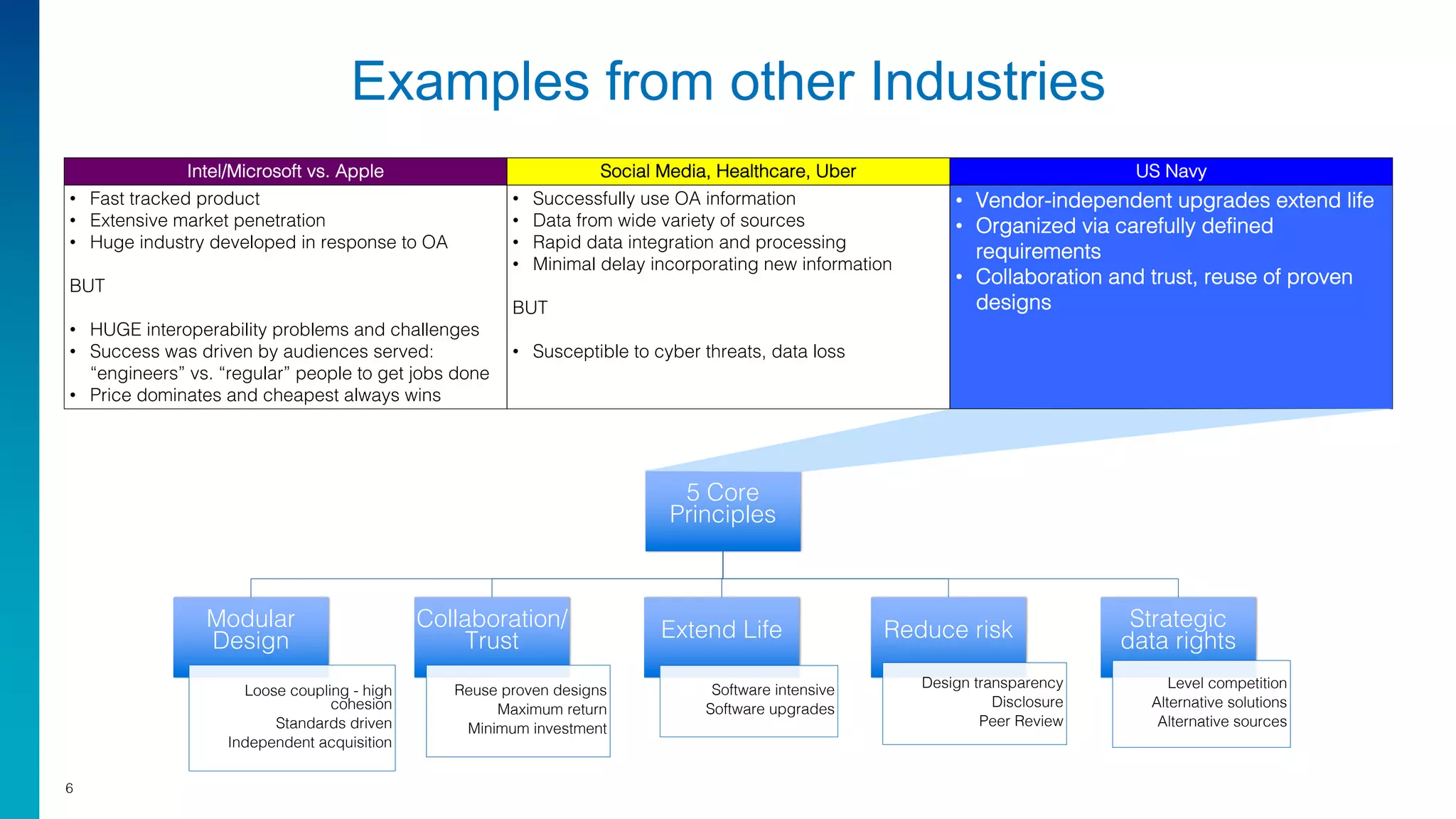
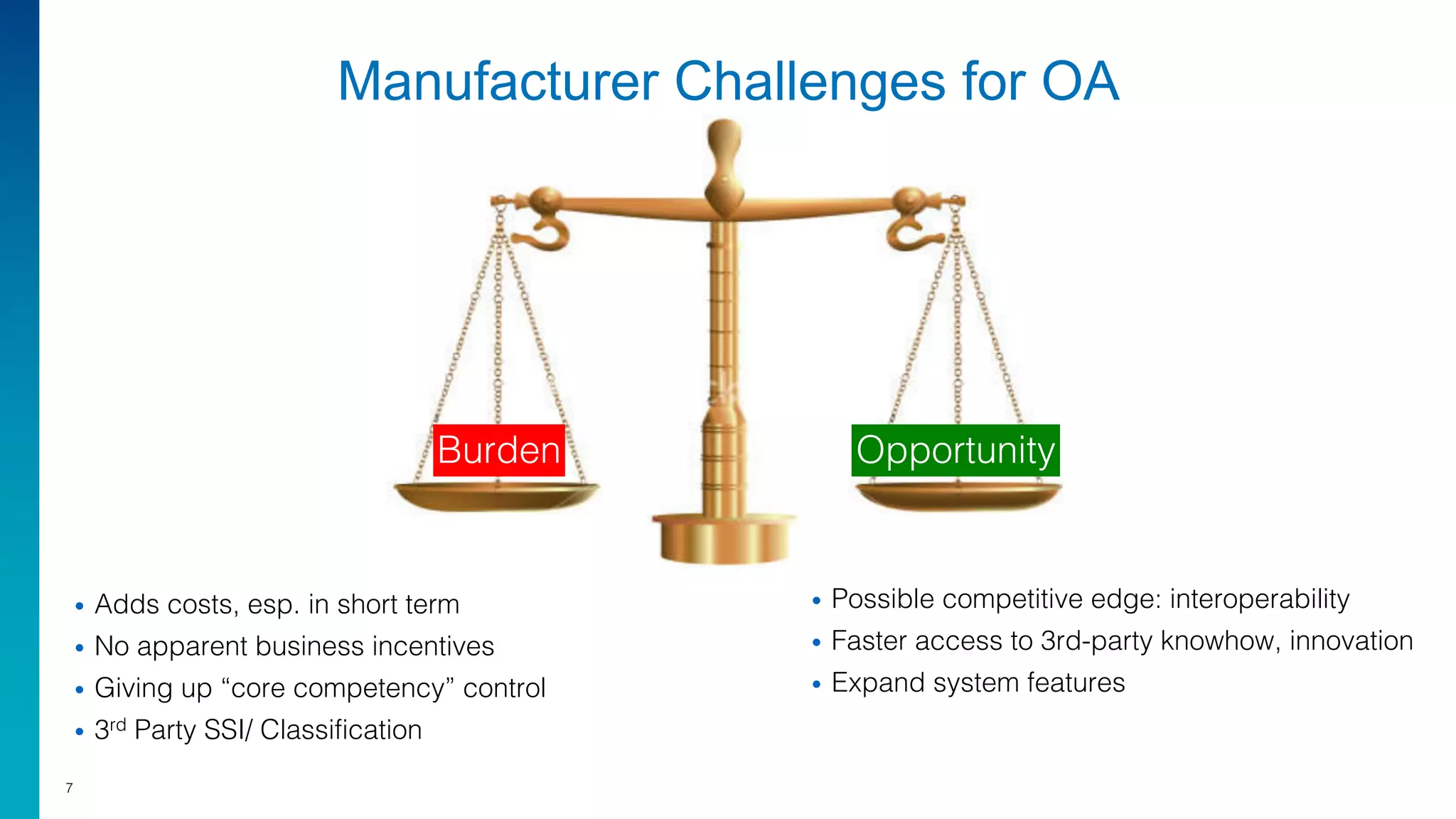
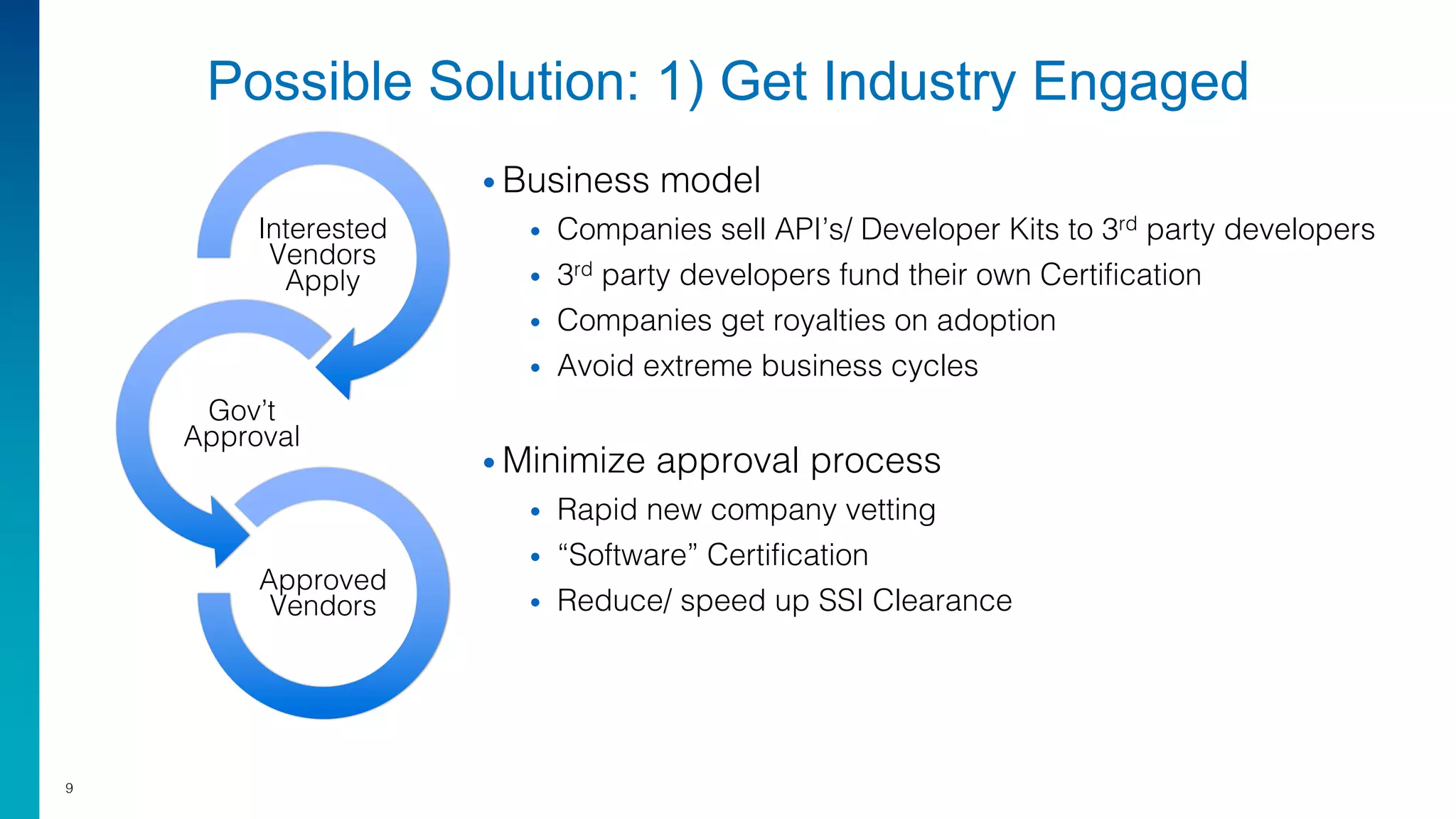
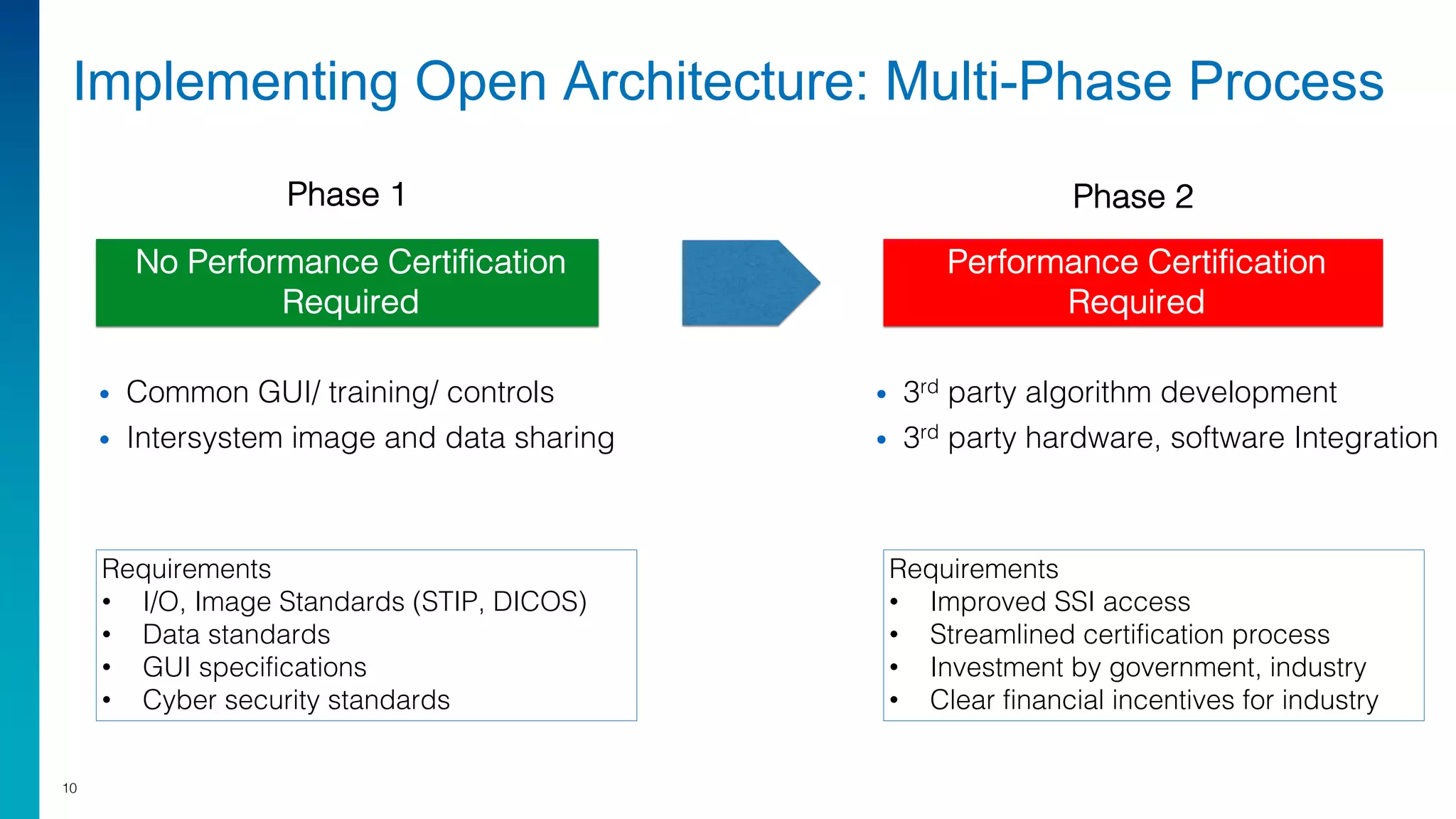
Mark Laustra discusses the need for open architecture in aviation security to enhance interoperability, reduce costs, and improve cybersecurity. The document outlines challenges with current proprietary systems, emphasizing the importance of third-party integration and collaboration across the industry. It proposes a phased approach to implement open architecture, requiring engagement from all stakeholders and streamlined certification processes.