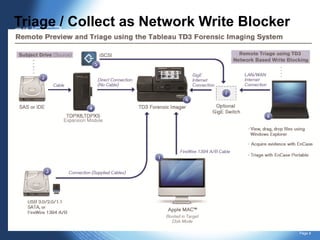
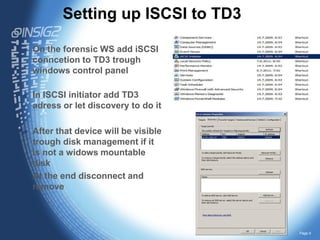
The document discusses using forensic preview, triage, and collection techniques with the TD3 device. It explores using these processes to complement full drive collection. Preview allows determining if a volume contains evidence, triage prioritizes investigation by reviewing data quickly, and collection fully images storage if enough evidence is found. The document outlines using the TD3 over iSCSI to remotely access storage in a forensically sound way for these processes. This enables fast review and triage to reduce data volume and close cases more efficiently. Hands-on with these techniques will be demonstrated using EnCase tools connected remotely to the TD3 during the training.