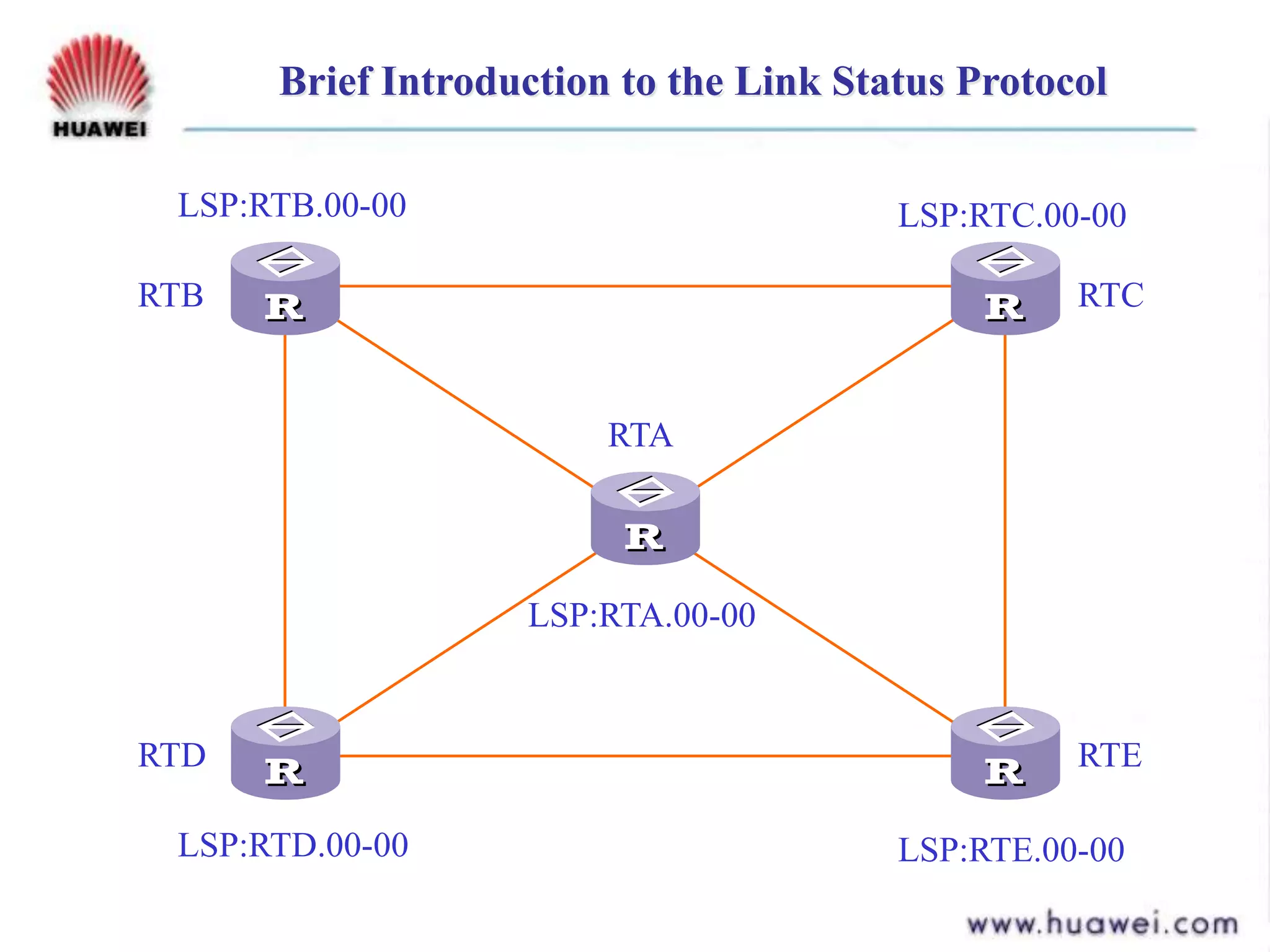
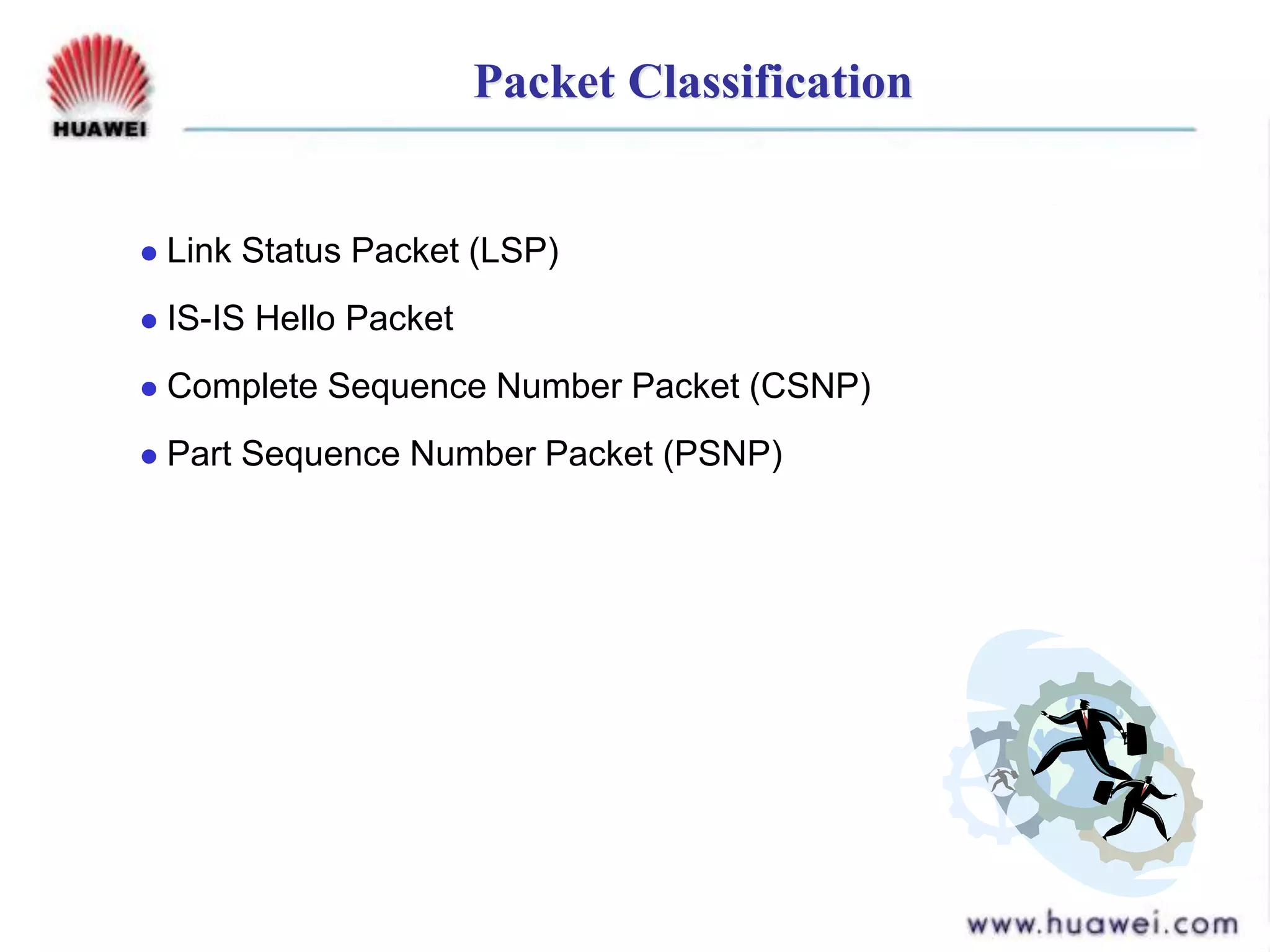
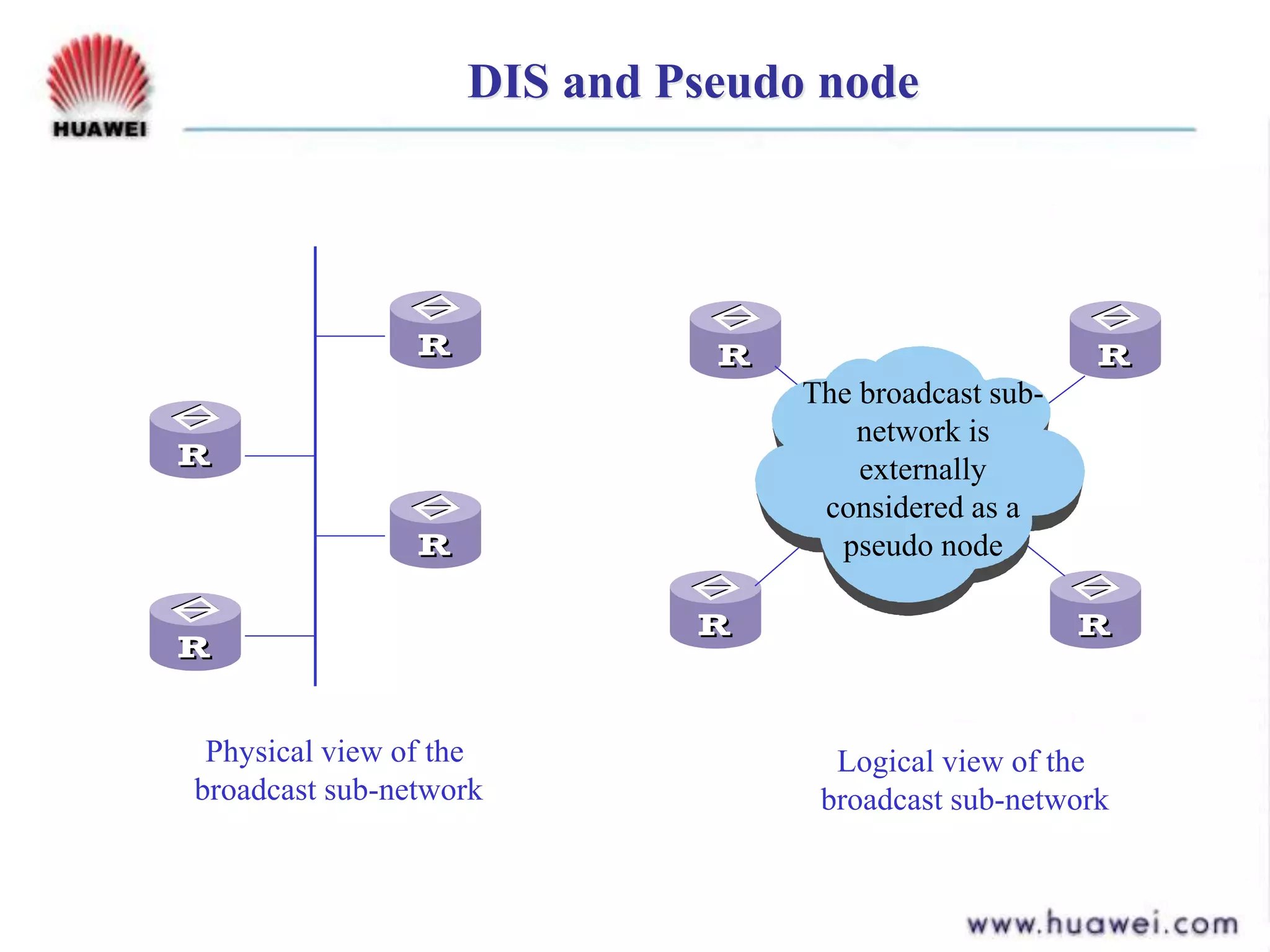
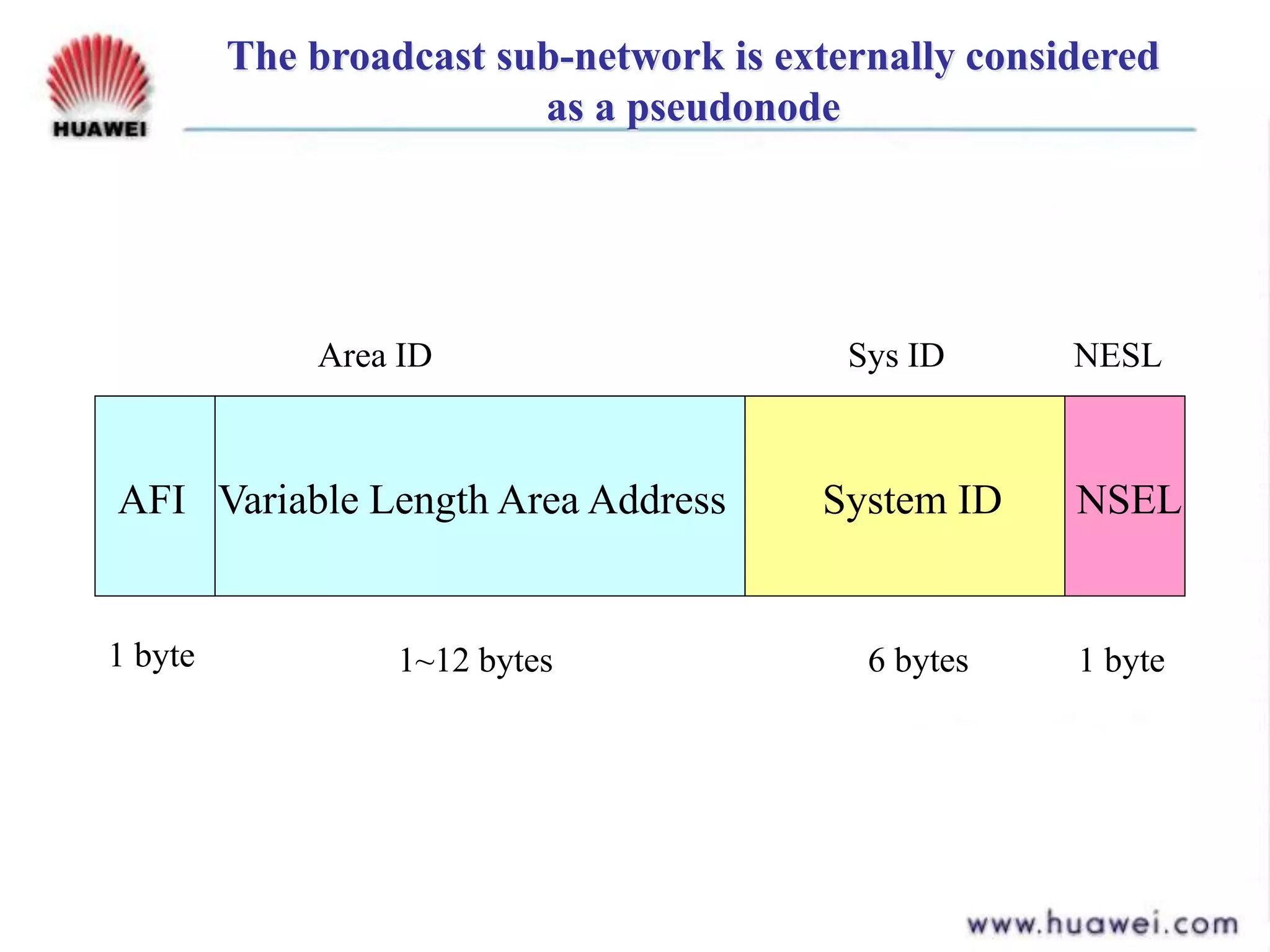
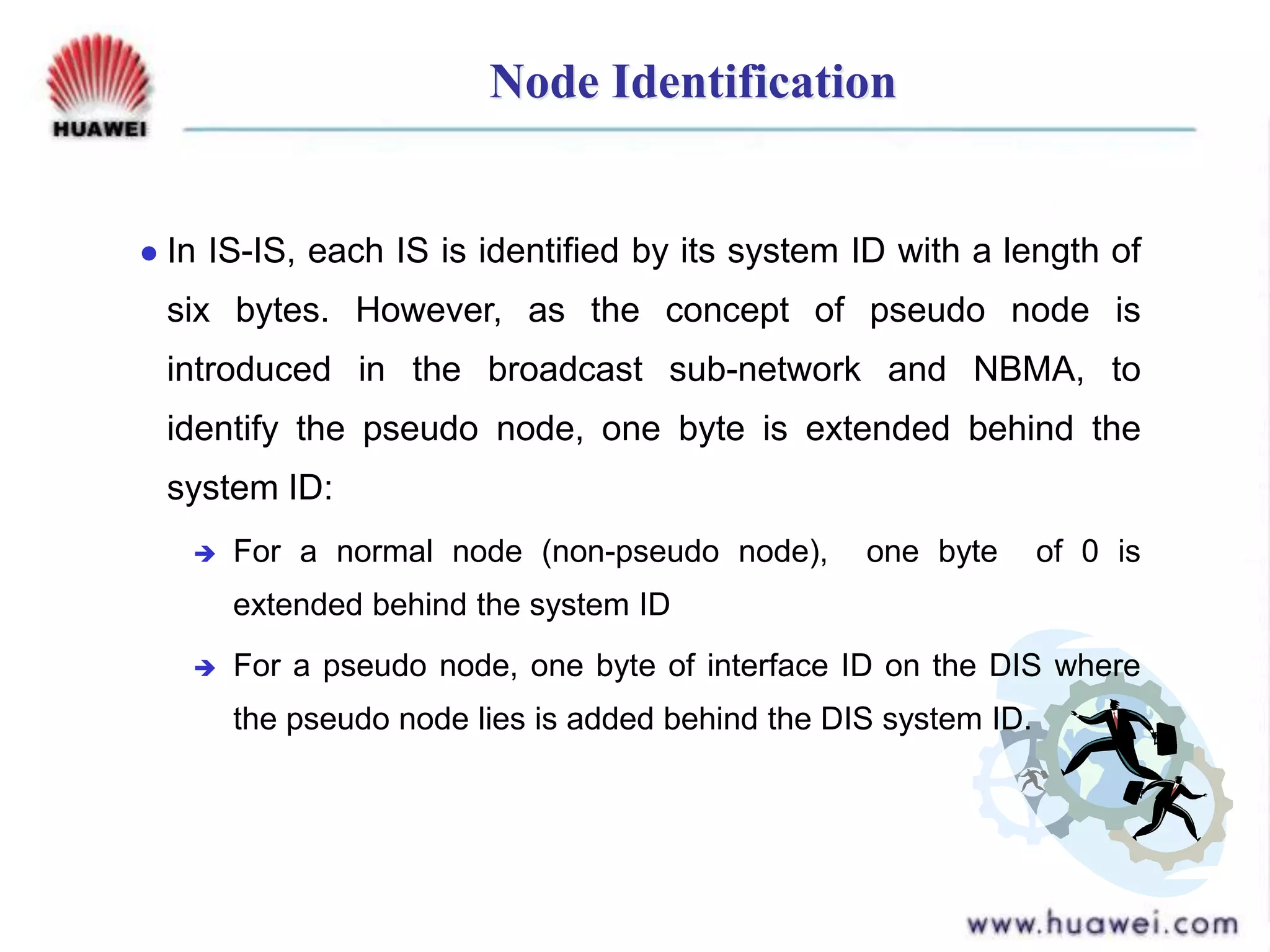
- IS-IS is an intermediate system to intermediate system (IS-IS) routing protocol that uses link state packets (LSPs) to advertise routing information within an autonomous system.
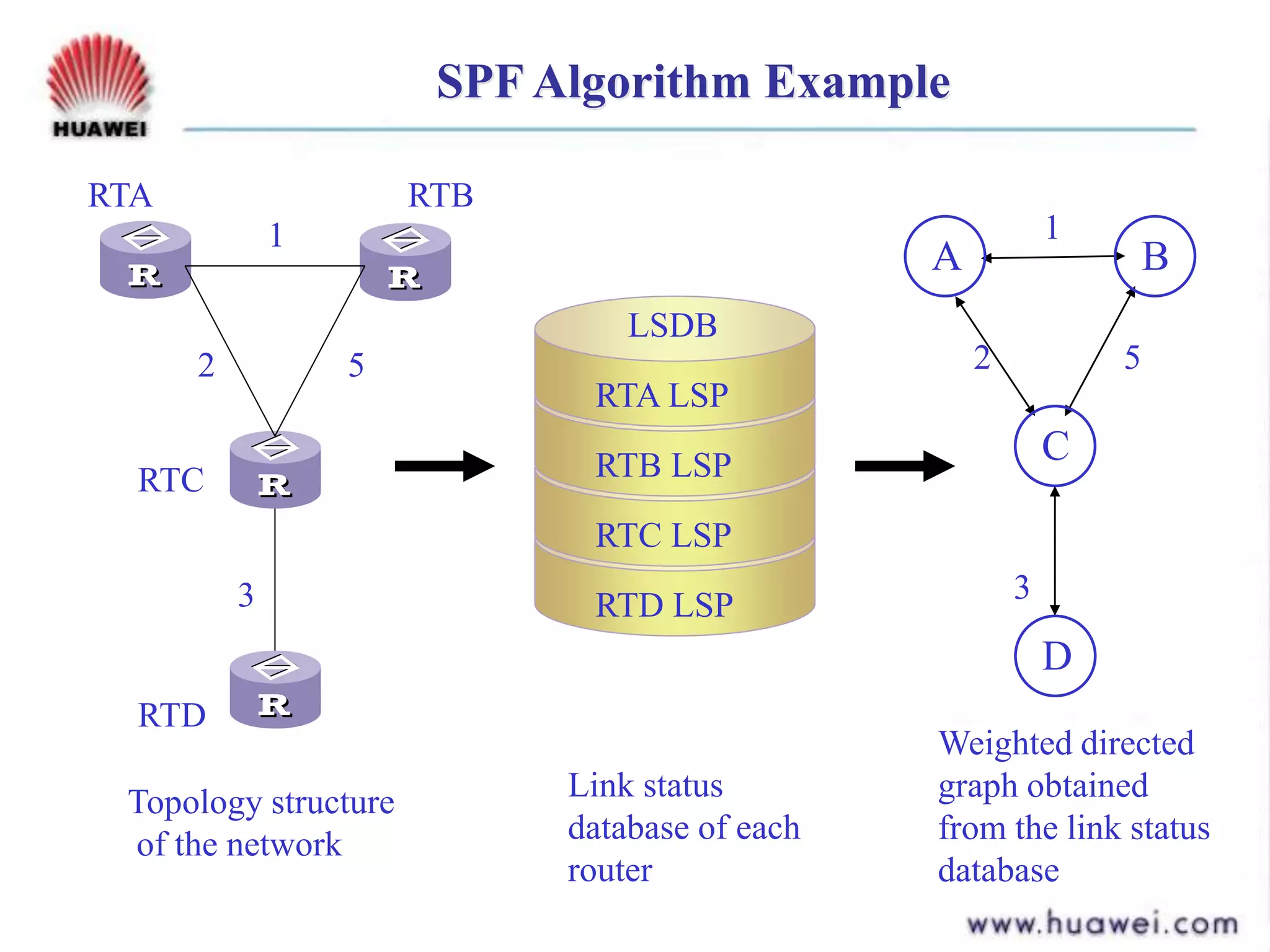
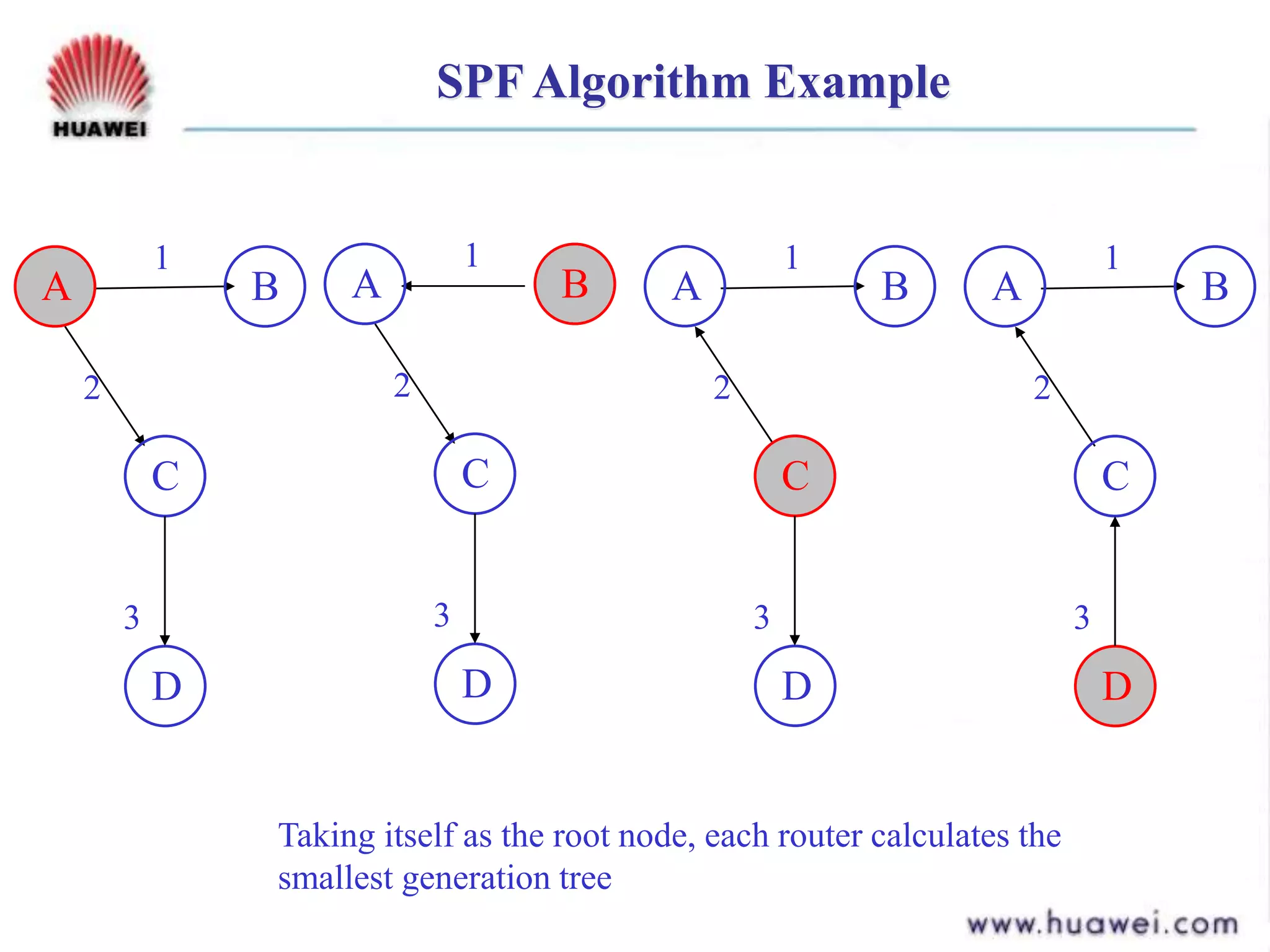
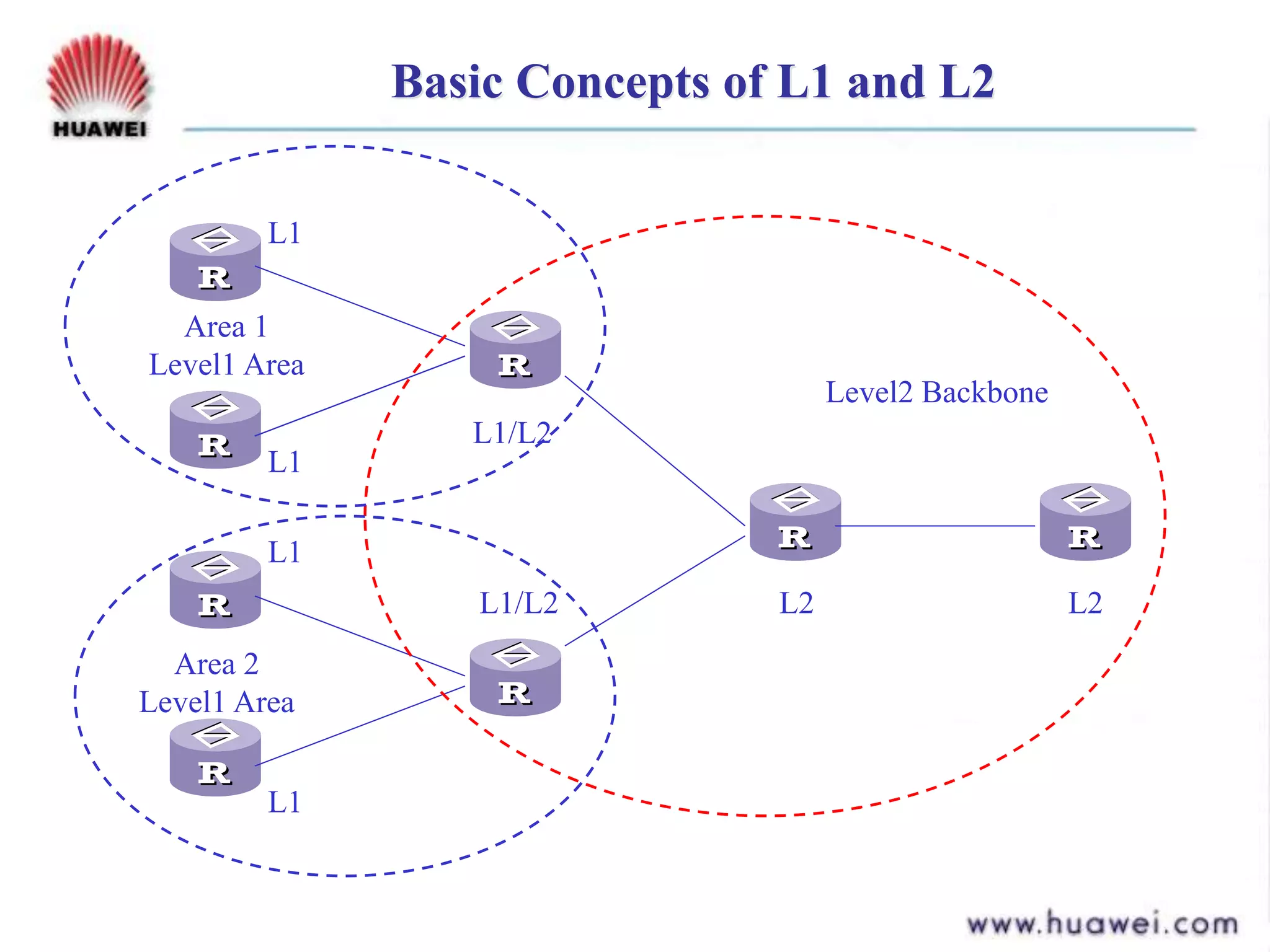
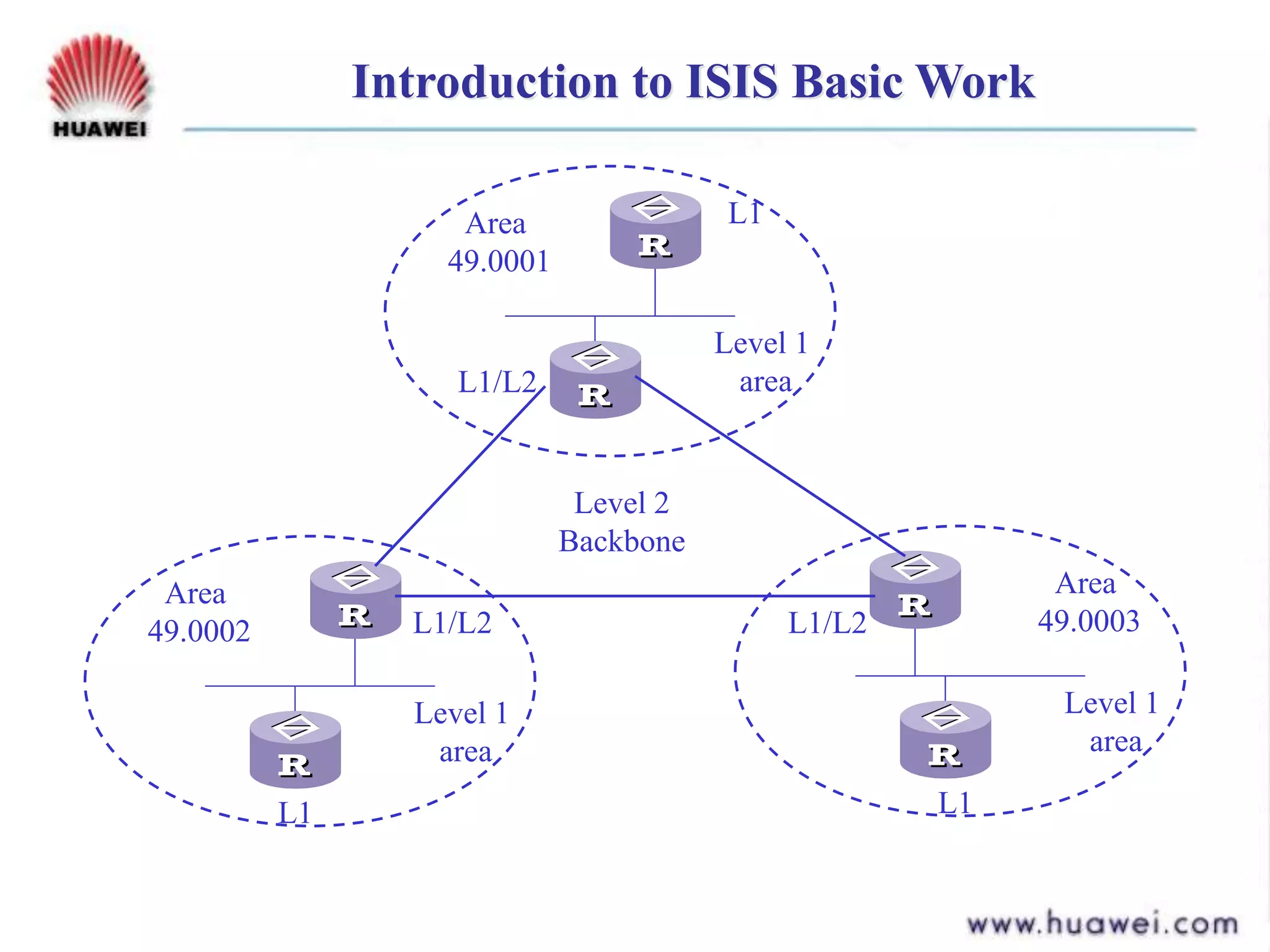
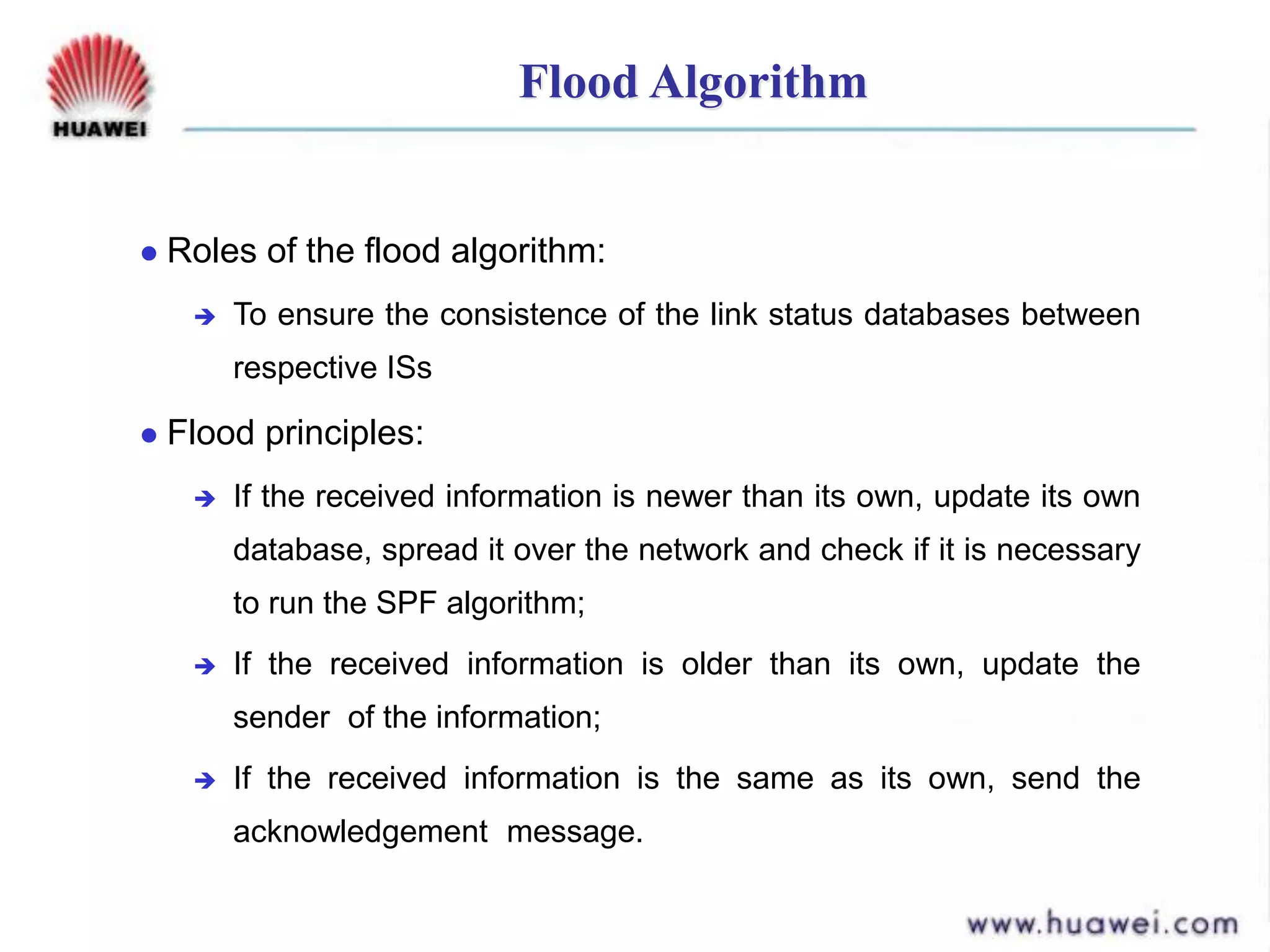
- It runs the shortest path first (SPF) algorithm on the link state database to determine the best paths to destinations. Areas and levels are used to structure large IS-IS networks hierarchically.
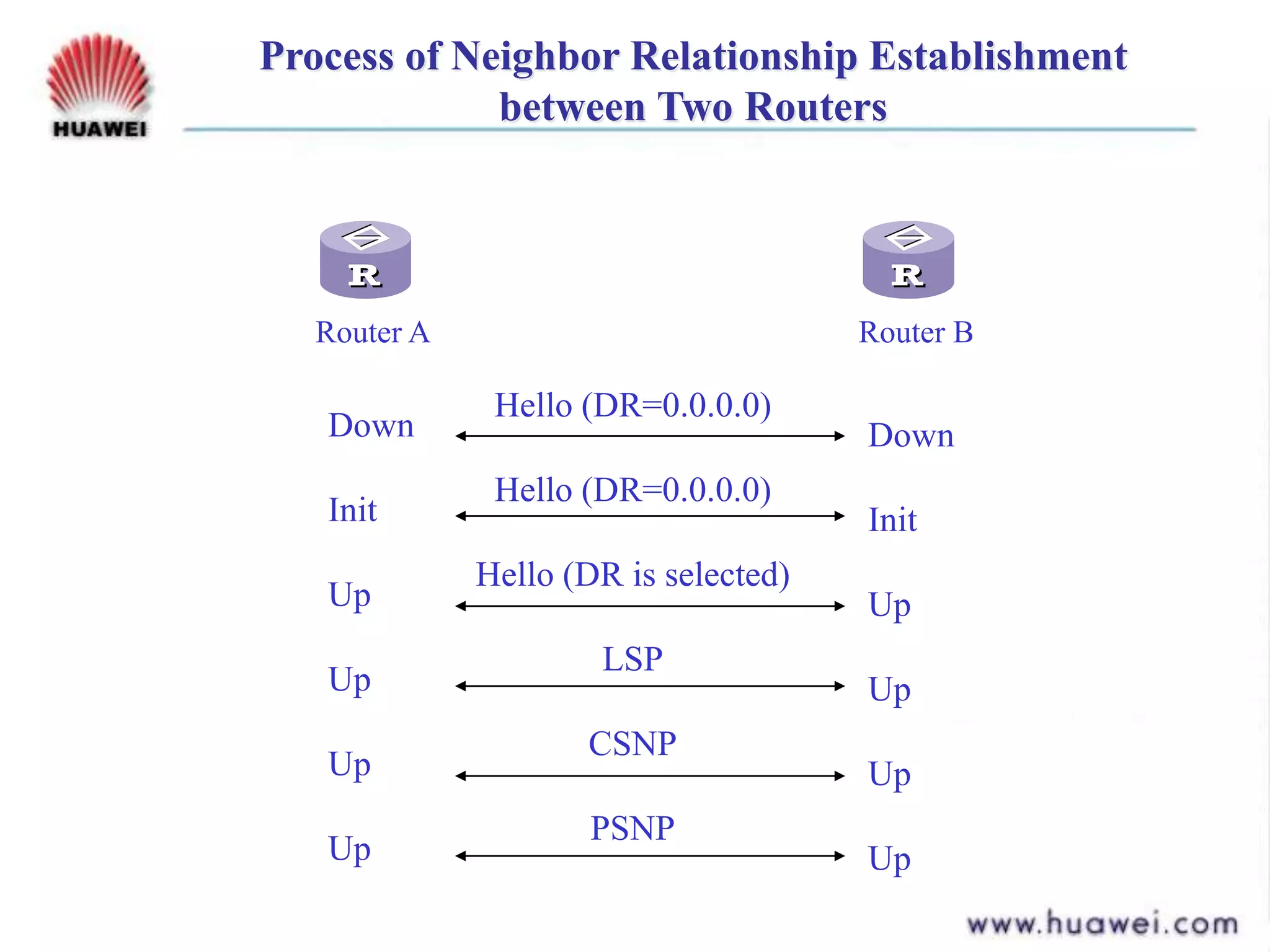
- IS-IS is similar to OSPF in using areas, SPF algorithm, and link state flooding but differs in packet formats, database structures, backbone definitions, and neighbor establishment.