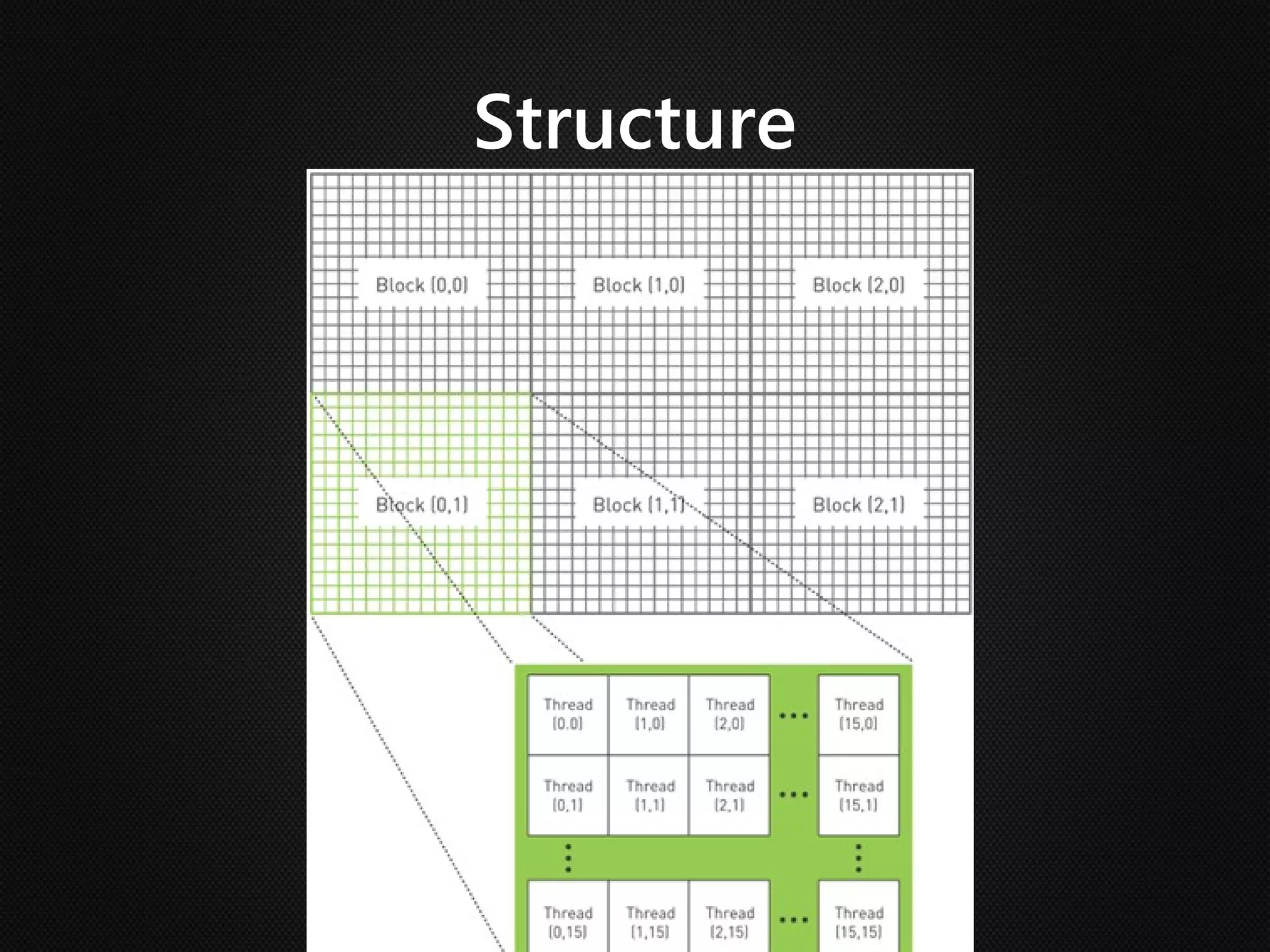
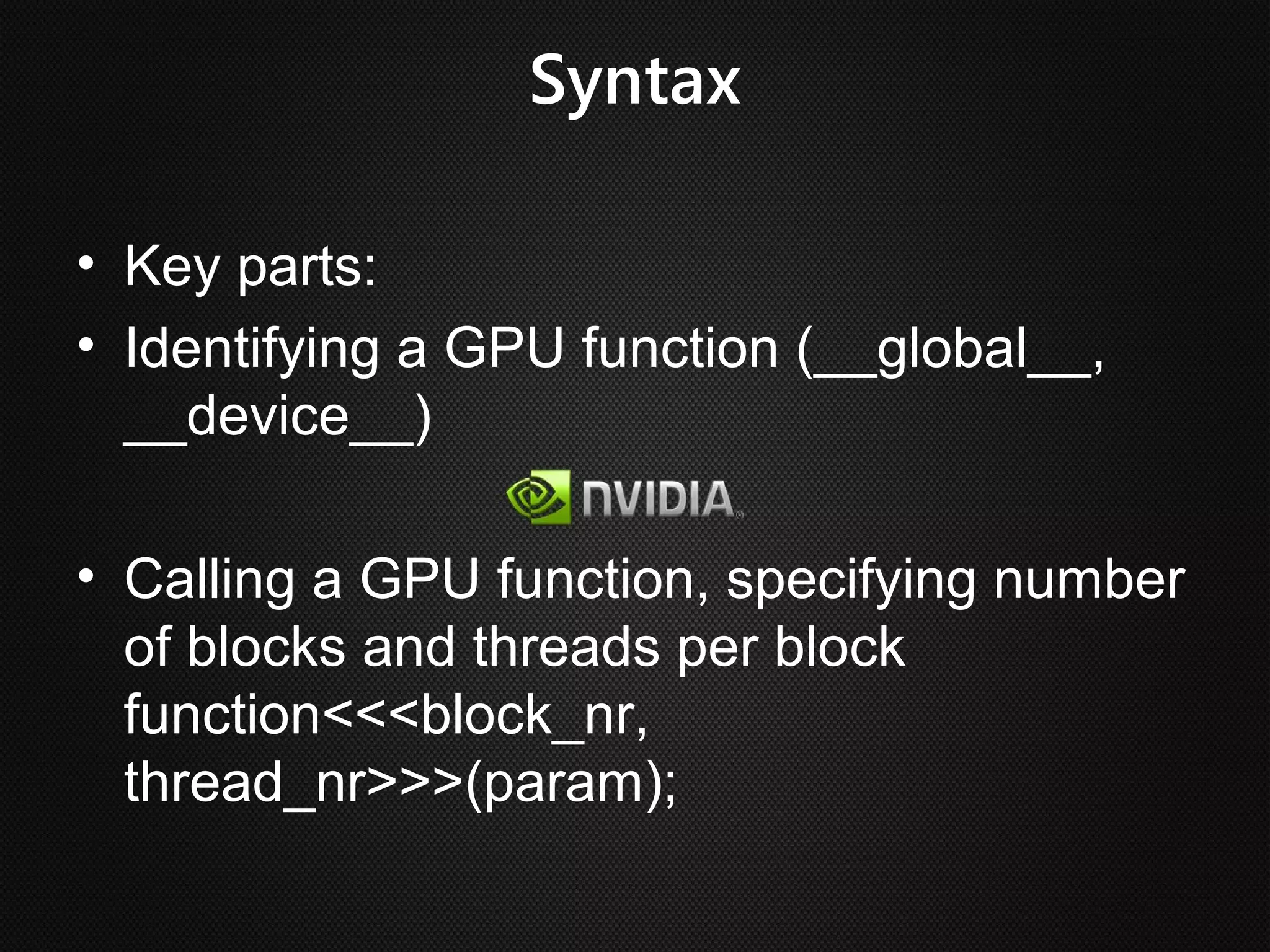
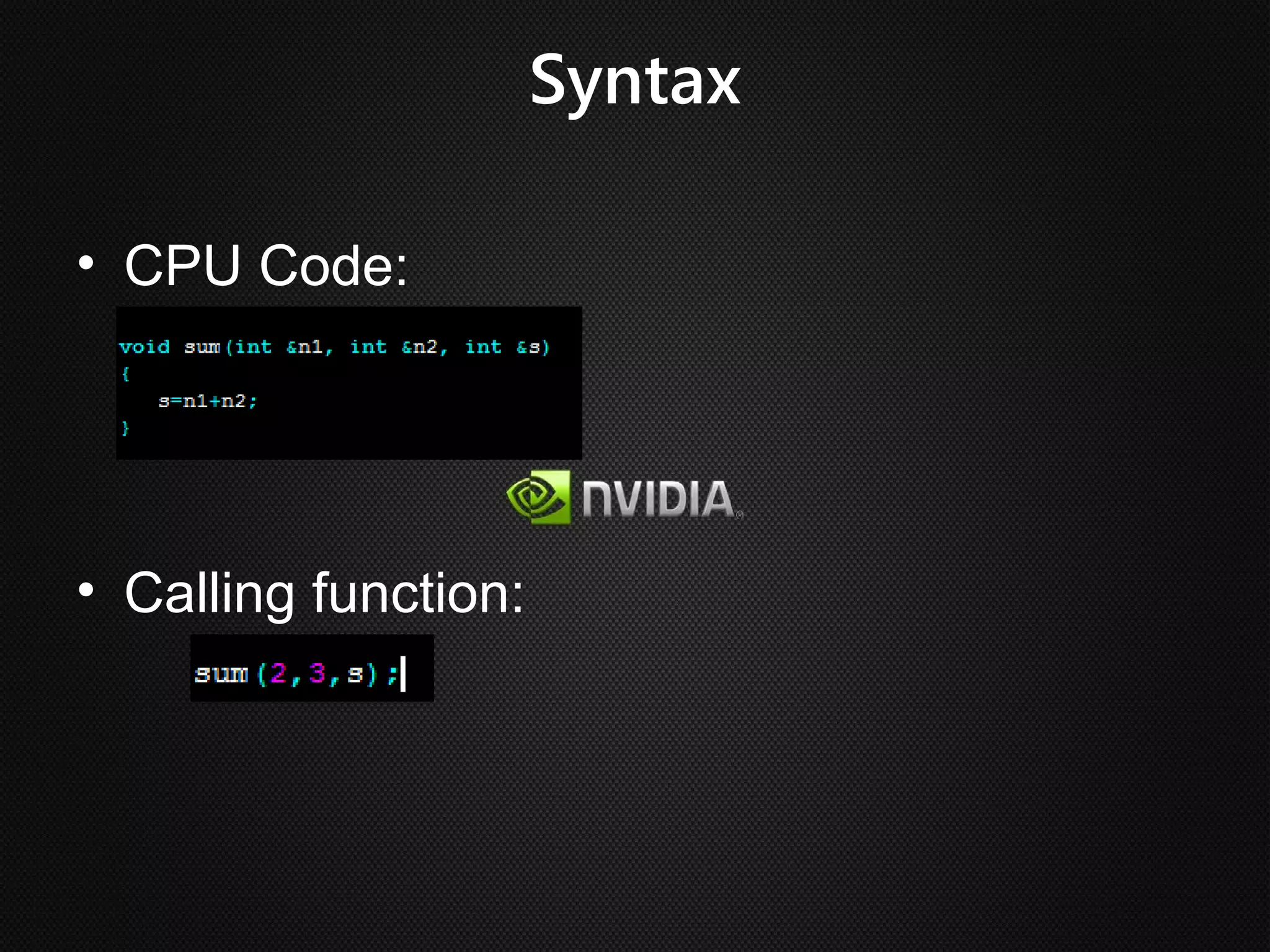
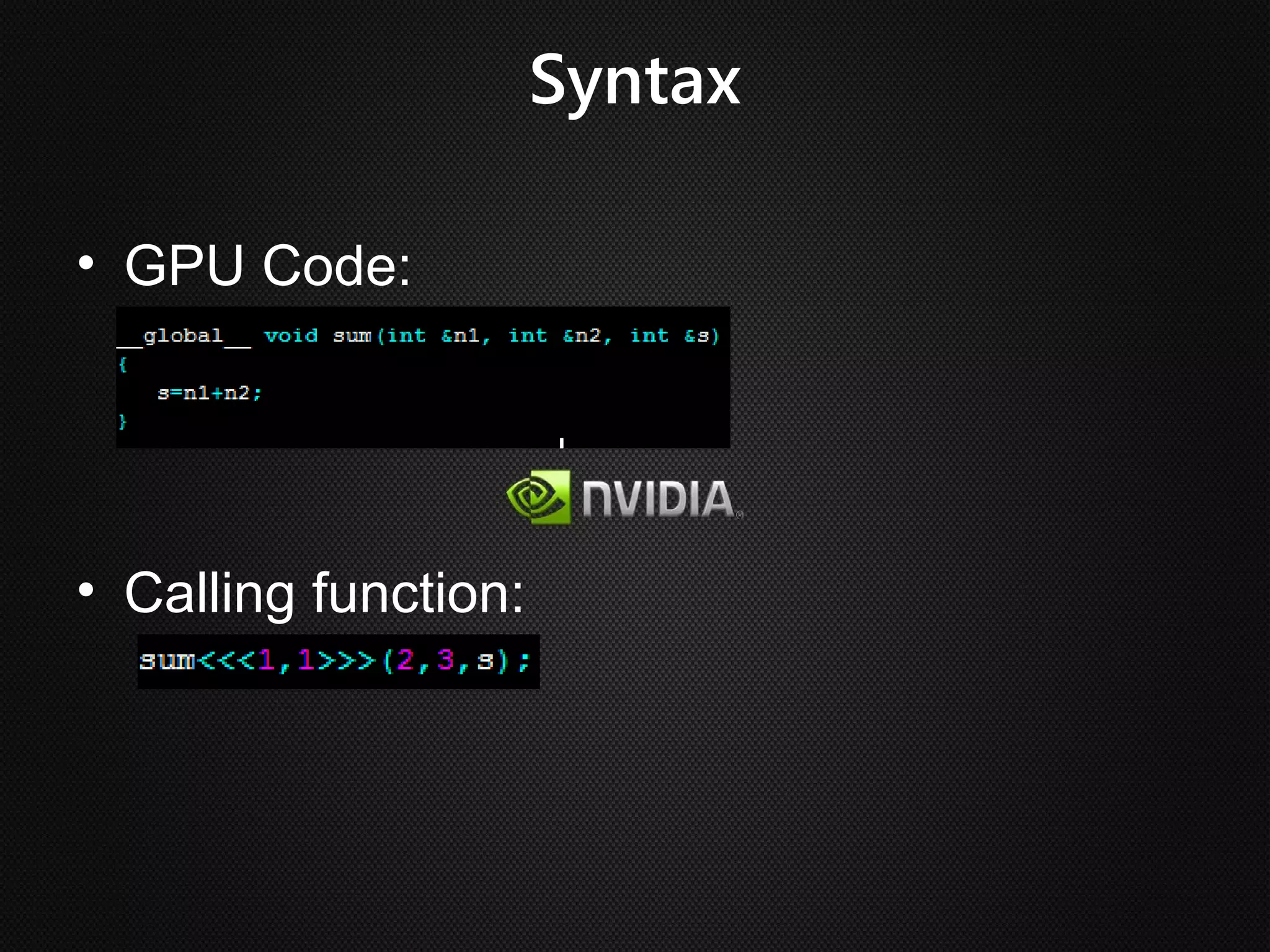
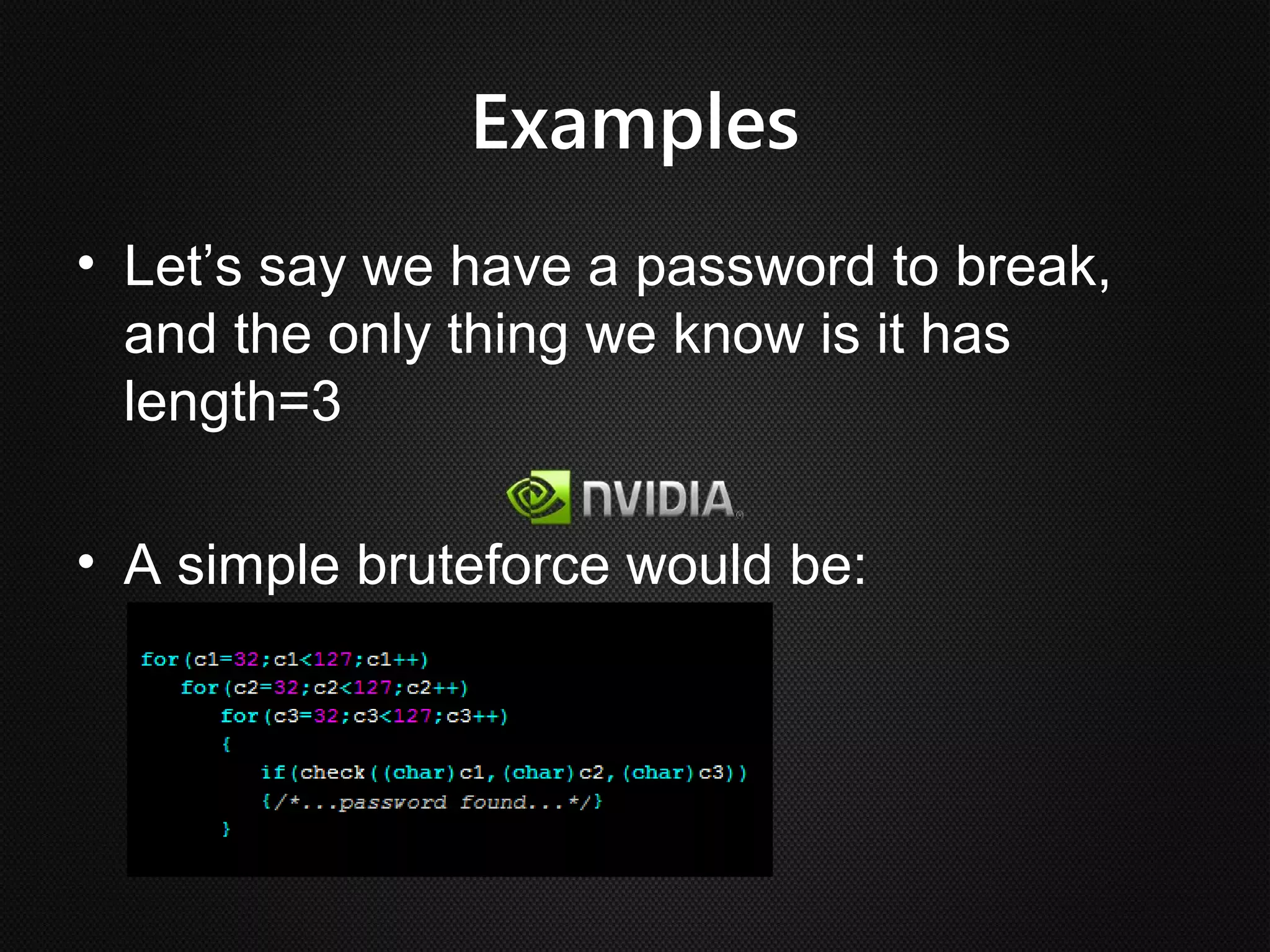
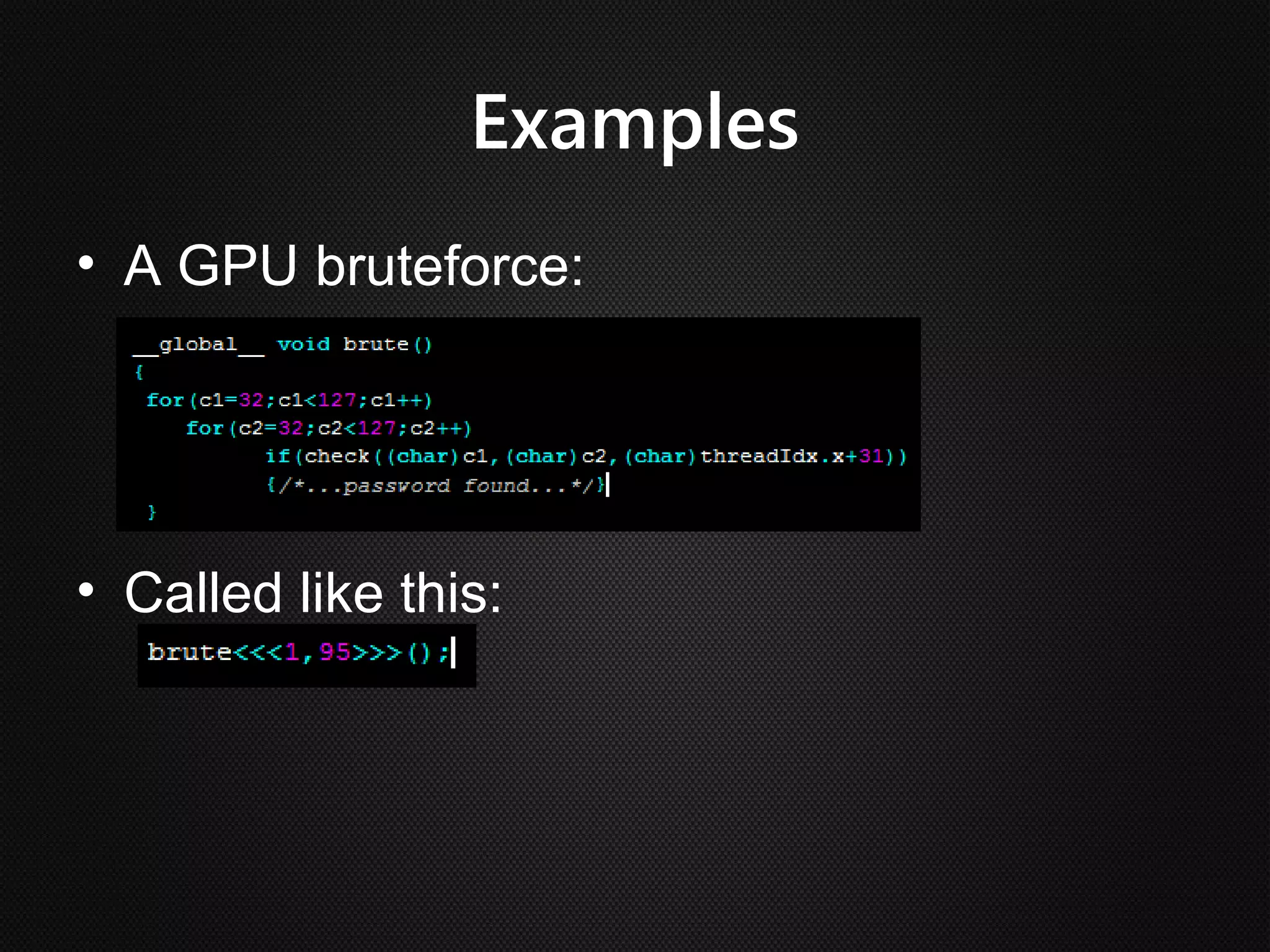
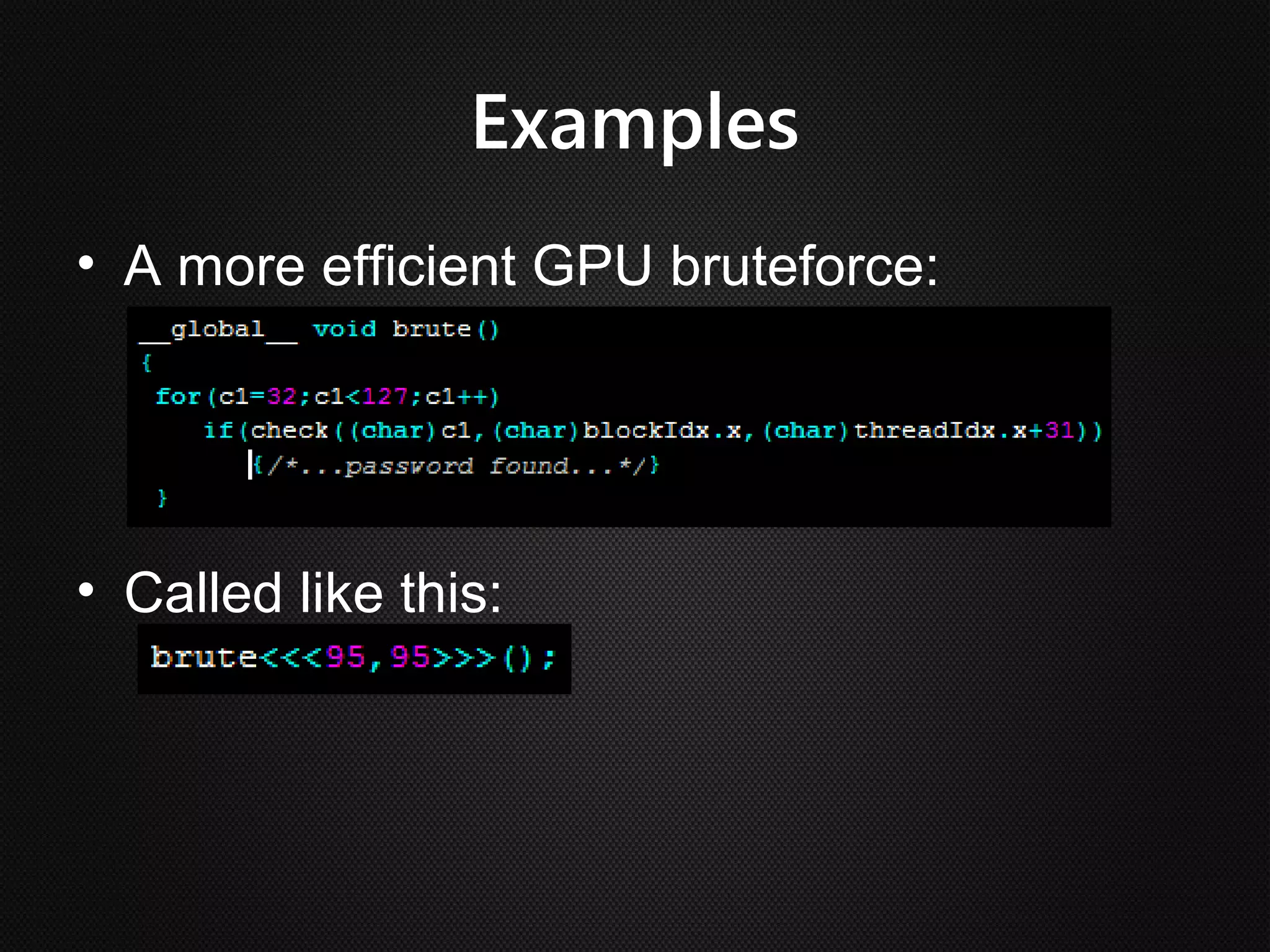
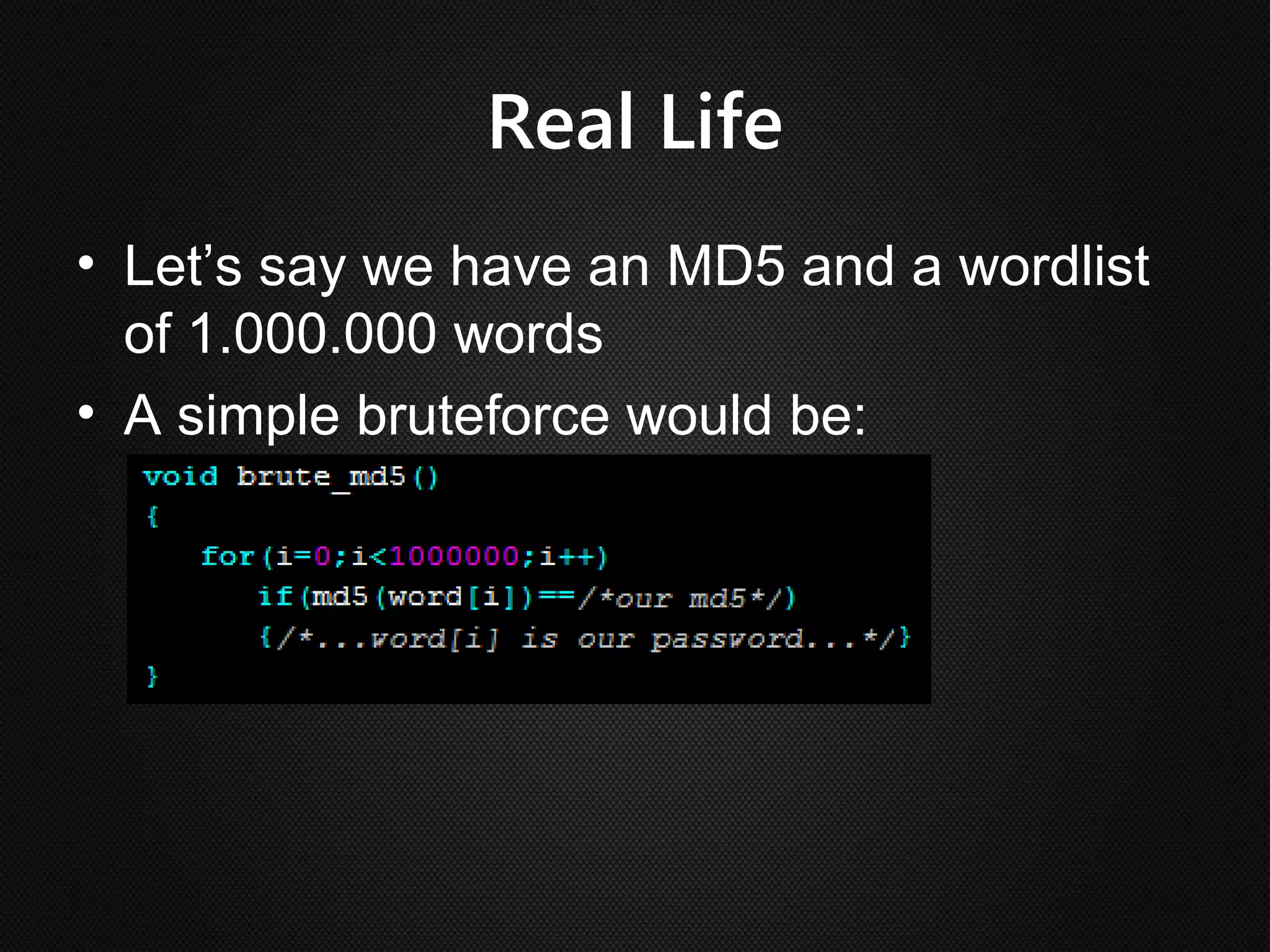
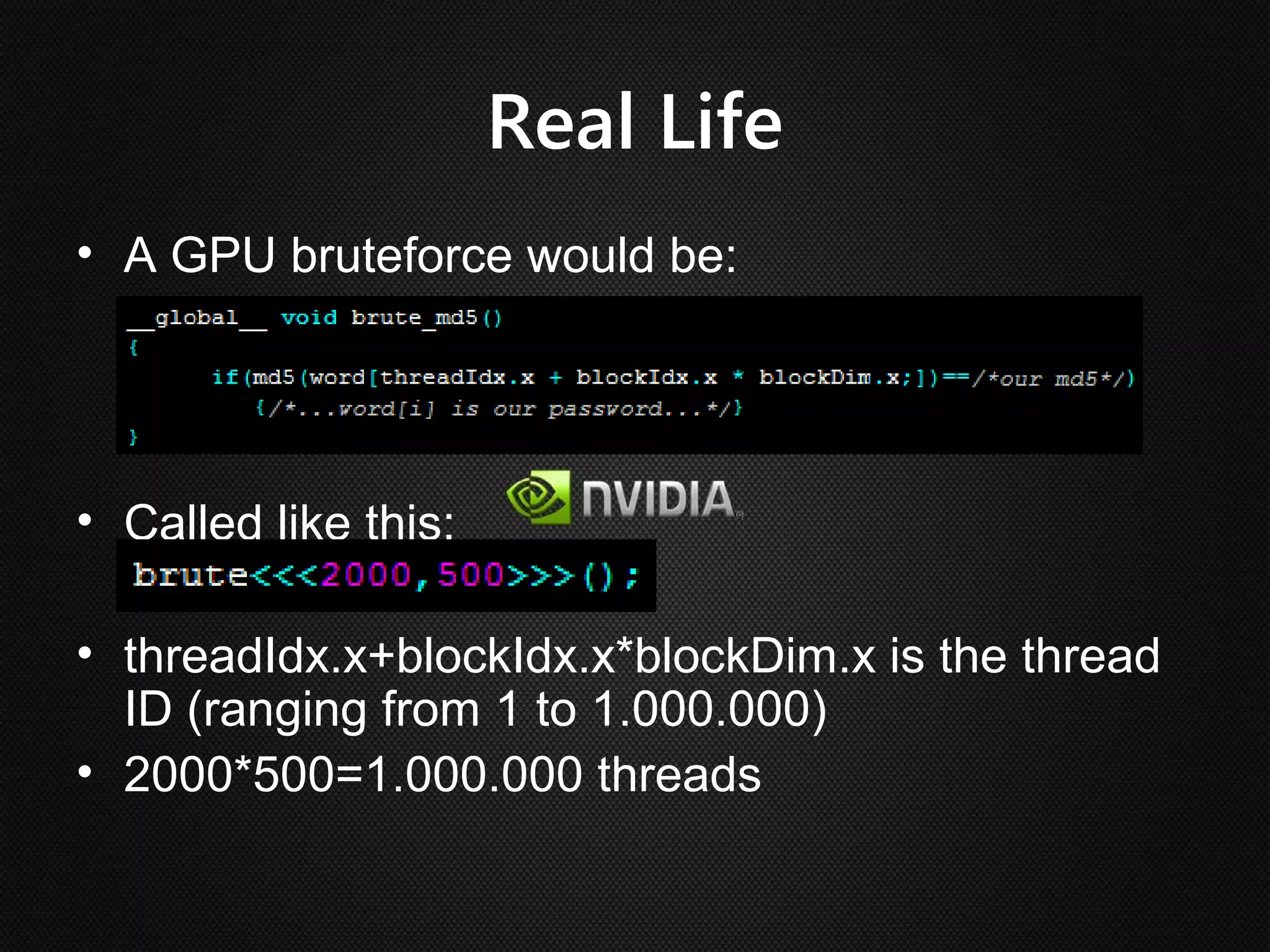
Ian Buck developed GPU computing at Nvidia. CUDA 1.0 was released in 2006, allowing normal applications to utilize GPU processing for higher performance without low-level programming. A GPU can execute many more instructions per clock than a CPU due to its large number of arithmetic logic units. In CUDA, programs specify blocks and threads to distribute work across a GPU. Calling a GPU function launches the specified number of blocks with threads. This massive parallelism allows GPUs to greatly accelerate brute force searches.