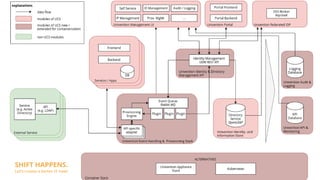
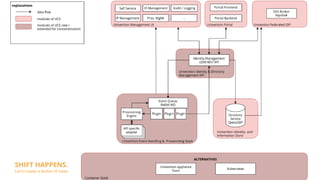
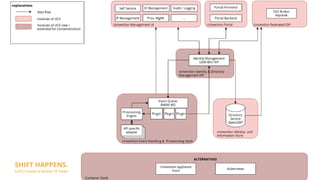
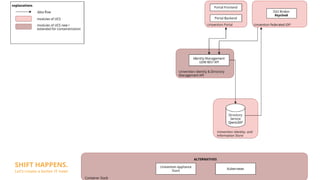
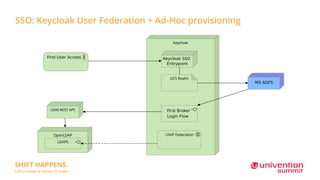
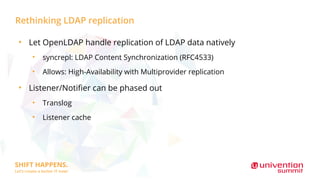
Modularity and IAM Stack focuses on containerizing the Univention Management Stack for deployment in modern data centers and clouds. The goals are to deploy each module in multiple instances for scalability and high availability, use a service-oriented API-first architecture, and deploy on platforms like Kubernetes and Sovereign Cloud Stack. Key aspects include containerizing IAM services like OpenLDAP, UDM, and Keycloak for SSO and federation; using the UDM REST API as the primary access point; and rethinking service provisioning to use an event queue instead of LDAP listeners. Challenges include orchestrating services in Kubernetes and ensuring high availability and scalability of the containerized LDAP database.