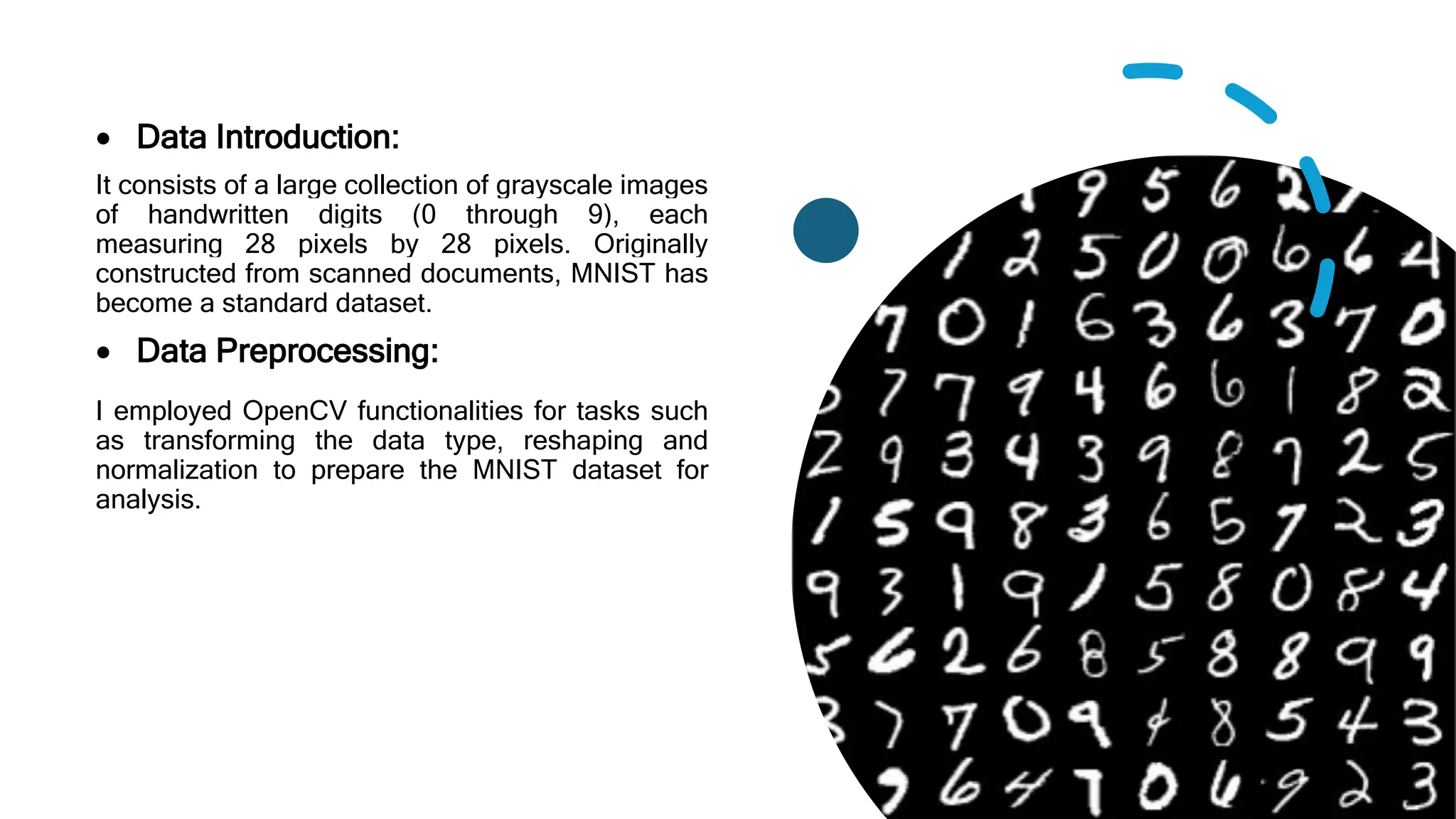
The project focuses on developing an accurate image classification system for categorizing handwritten digits using the MNIST dataset and OpenCV. Data preprocessing steps included reshaping and normalization, and the model achieved an approximate accuracy of 98% with high recall and precision. The evaluation showed that the model correctly classified 9,833 out of 10,000 test images.