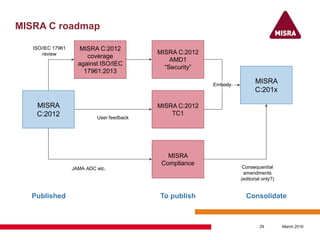
MISRA C is a coding standard for the C programming language developed to enable safe and secure embedded systems. It defines a subset of the C language that removes opportunities for mistakes. The standard has evolved from focusing on the automotive industry to being applicable for any industry requiring high integrity or reliability software. Recent updates to MISRA C include improved compliance guidance, additional security rules, and assessments of coverage against other standards like ISO/IEC TS 17961 for secure coding rules and CERT-C. Future work plans to consider rules addressing C11 features and operating environment access.

































![ISO/IEC TS 17961 – The Gaps
The gaps (partial or not covered) can be grouped as follows:
- Taintedness as a concept
- The use of getenv(), localeconv(), setlocale() and strerror() 2 rules
[or indeed other library functions relating to a hosted environment]
- Use of sizeof() on a pointer function parameter 1 rule
- Comparisons of padding data 1 rule
Proposal
- MISRA C:2012 be enhanced to address these gaps
April 27, 201640](https://image.slidesharecdn.com/d05db5ac-59c6-4fe9-992d-607c34870ebe-160427091818/85/MISRA-C-Chairman-Device-Developer-Conference-2016-40-320.jpg)