A 2014 Wisegate report reveals that many IT security teams lack effective metrics to track their security risks, leading to a significant disconnect between security efforts and business communication. The survey noted that over 50% of participants do not have metrics to measure their top security risks, resulting in poor communication with executives about increasing risks like malware and data breaches. The document emphasizes the need for IT security to adopt a more risk-centric approach to provide actionable metrics that resonate with business leaders and improve overall security effectiveness.


![a Failure in Communication 3
In June of 2014, Wisegate conducted a member-driven research initiative designed to
assess the current state of security risks and controls in business today. Assessing IT
Security Risks addresses many of the top takeaways from this survey. This document is the
first in a series of reports designed to look more closely at four specific issues highlighted
by that survey.
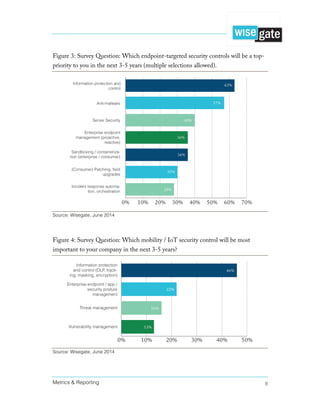
» Metrics and reporting
» Malware and data breaches
» Data-centric security
» Automation and orchestration
Metrics and Reporting
This document might have just as easily been titled, ‘The Lack of Metrics’. It is highlighted
in a simple conclusion reached in Assessing IT Security Risks:
“Overall, [security] teams were optimistic but not overwhelmingly confident.”](https://image.slidesharecdn.com/wisegate-metrics-reporting-150813225033-lva1-app6892/85/Metrics-Reporting-A-Failure-in-Communication-3-320.jpg)

![a Failure in Communication 5
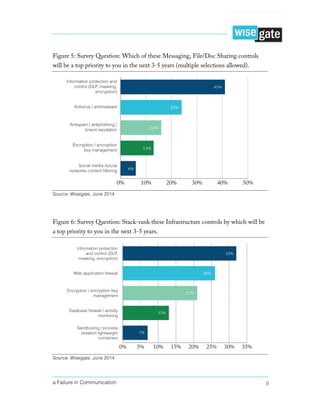
The problem is that there is a general acceptance that all three top risks are growing—more
than 80% of participants believe that major risks are increasing in their industry (see Figure
2).
[Note: These three ‘top risks’ are non-specific—they are whatever the participant
considered to be his or her personal top three risks. Overall, the top three risks are
malware, data breaches and outsider threat.]
Figure 2: Survey Question: Which risks are growing for your specific company and
industry?
Source: Wisegate June 2014
What this means, in effect, is that IT cannot accurately communicate an increasing security
risk to Business; and Business cannot accurately understand that security risk and its
possible impact on the business.
Is This Important?
This lack of communication is very important, for three particular reasons:
» Real security cannot be achieved without full Business buy-in.
» Business is likely to become suddenly very keen on understanding security
following the recent prosecution of FedEx in what can be seen as an extension of
the ‘failure to prevent’ theory. “This bodes ill not only for corporations that fail to
prevent criminal activity, but for corporate compliance officers whose programs,](https://image.slidesharecdn.com/wisegate-metrics-reporting-150813225033-lva1-app6892/85/Metrics-Reporting-A-Failure-in-Communication-5-320.jpg)