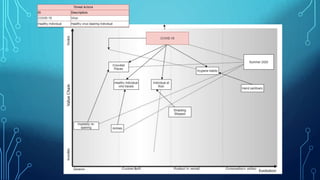
1. The document discusses the importance of understanding context in cybersecurity, similar to how context is important in other fields like aviation and medicine.
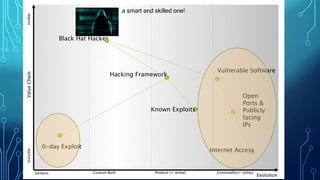
2. It encourages applying a "reverse Wardley map" approach to think like an attacker and understand their needs and goals in order to make systems less vulnerable.
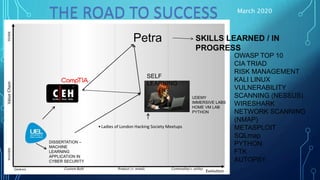
3. The author is both a doctor and cybersecurity engineer who shares their journey learning cybersecurity skills through conferences, online courses, and building a home lab to gain experience in topics like networking, vulnerability scanning, and Python programming.