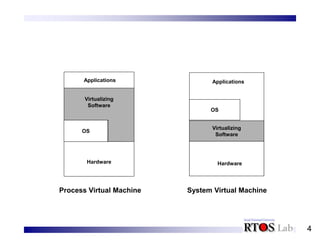
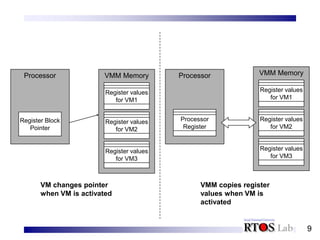
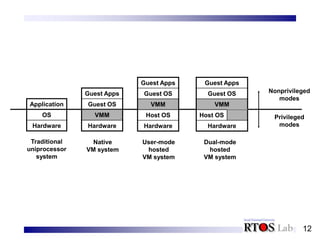
This document discusses system virtual machines. It introduces key concepts of system virtual machines including outward appearance, state management, and resource control. It explains how system virtual machines virtualize hardware resources like processors and memory to provide an illusion of multiple isolated computer systems running simultaneously on a single physical machine. It also distinguishes between native virtual machine systems where the virtual machine monitor runs in the highest privilege level, and hosted virtual machine systems where the virtual machine monitor utilizes functions of an underlying host operating system.