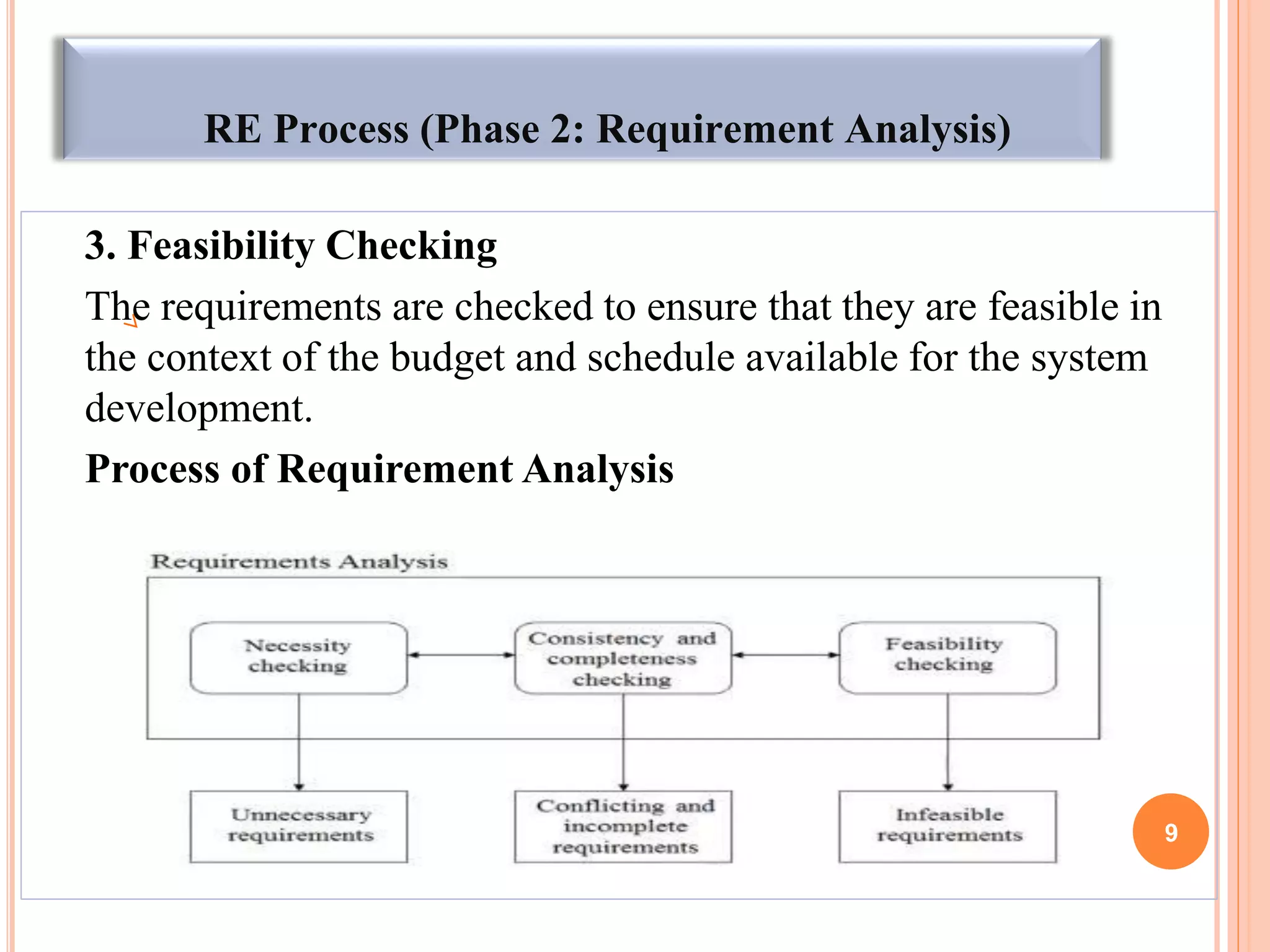
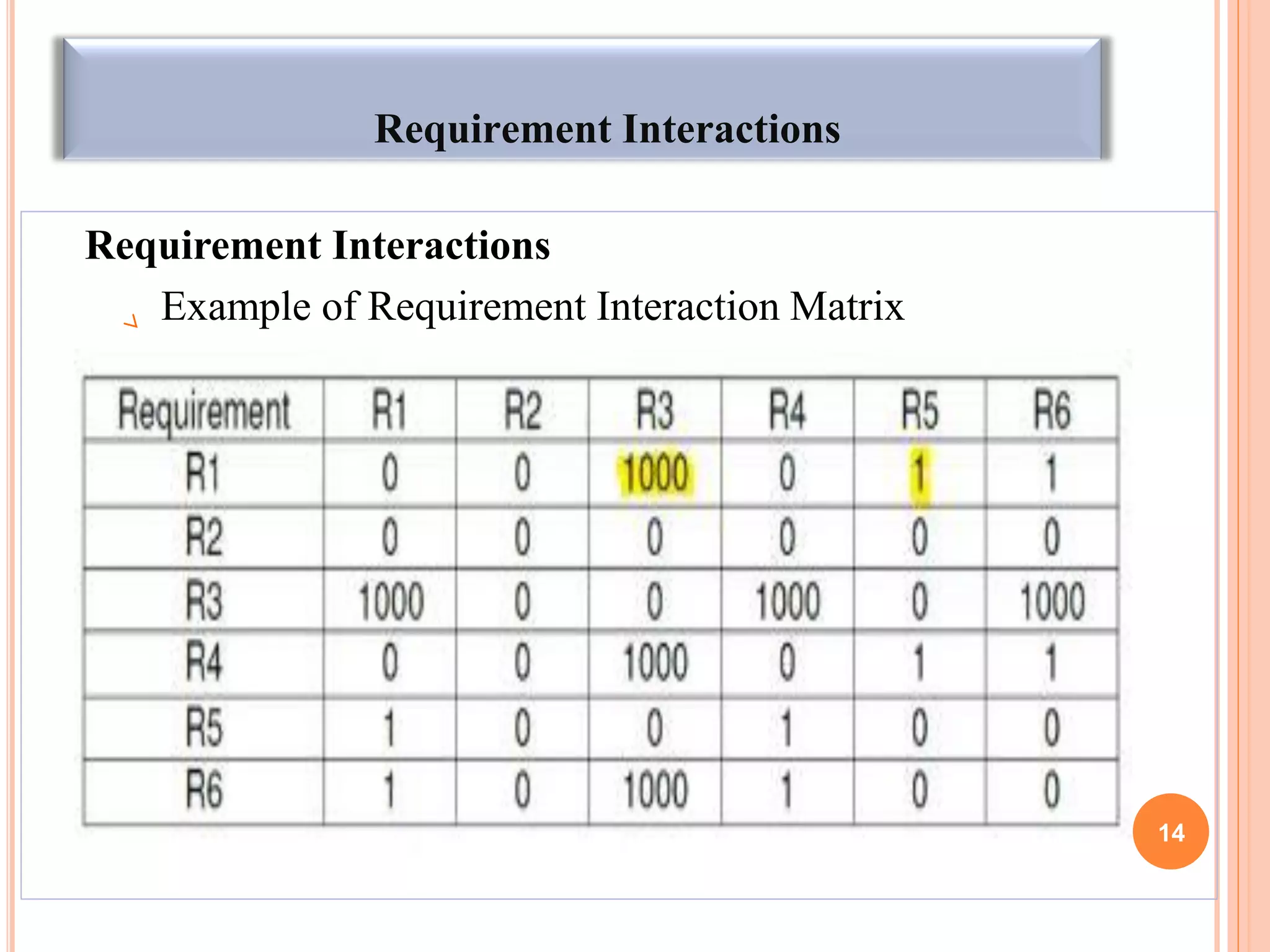
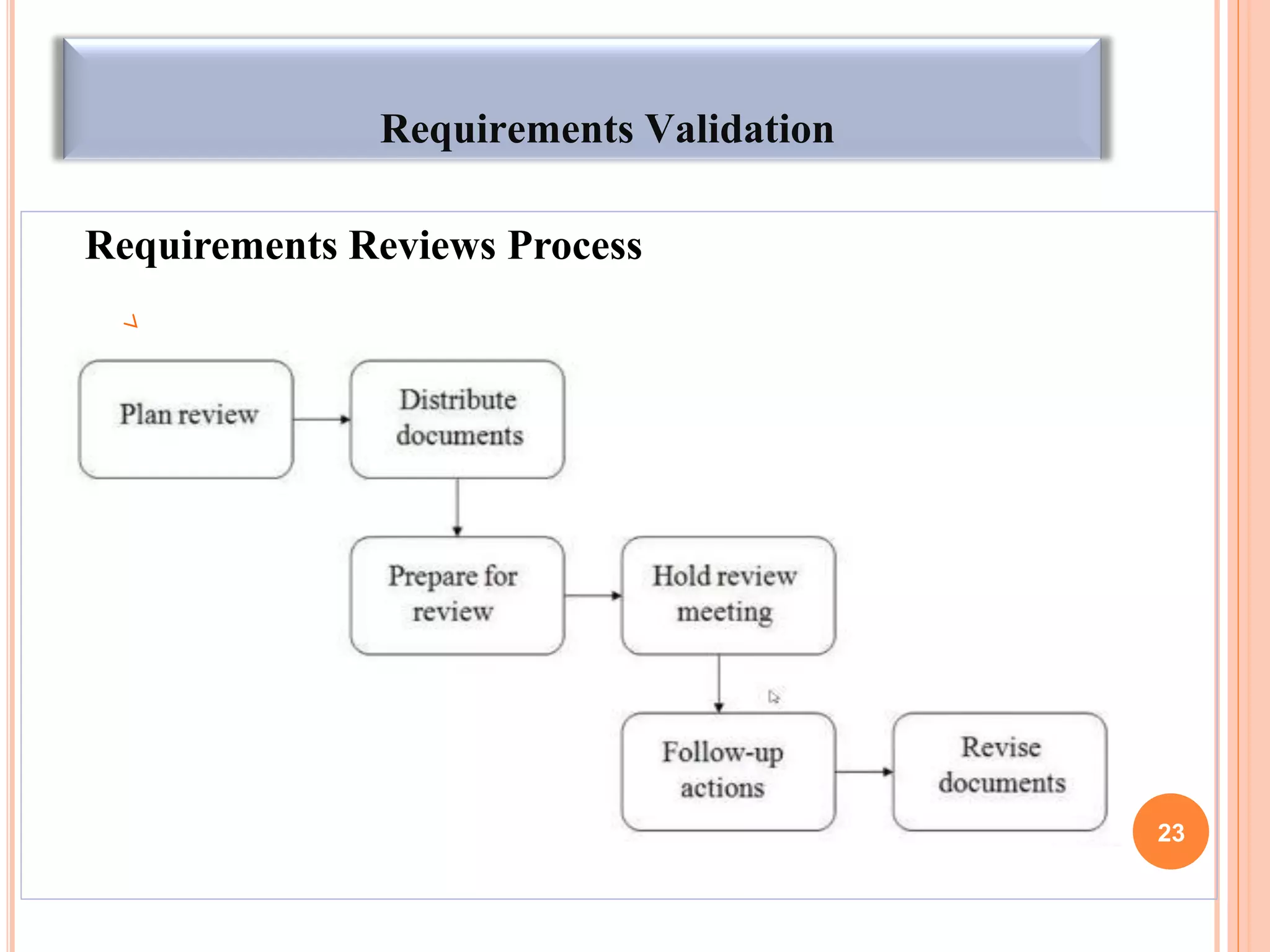
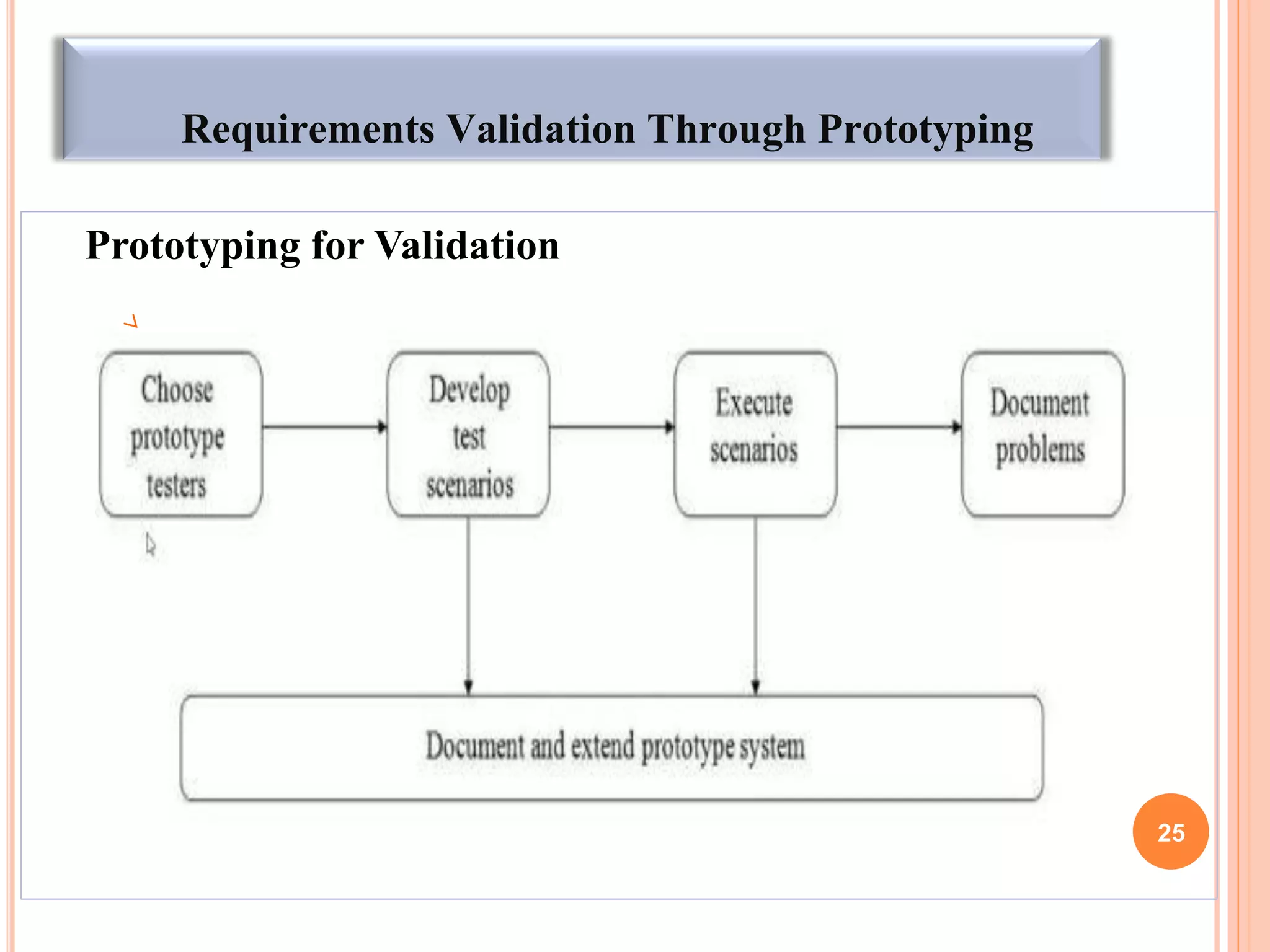
The document discusses techniques for requirements elicitation and analysis in software engineering. It describes observing users to understand processes, reusing requirements from other similar systems, analyzing requirements for necessity, consistency and feasibility, and resolving conflicts through negotiation. Validation techniques include reviews involving stakeholders and prototyping to demonstrate requirements. Managing changing requirements is also discussed.